
Research Topics & Ideas: Cybersecurity
50 Topic Ideas To Kickstart Your Research

If you’re just starting out exploring cybersecurity-related topics for your dissertation, thesis or research project, you’ve come to the right place. In this post, we’ll help kickstart your research by providing a hearty list of cybersecurity-related research topics and ideas , including examples from recent studies.
PS – This is just the start…
We know it’s exciting to run through a list of research topics, but please keep in mind that this list is just a starting point . These topic ideas provided here are intentionally broad and generic , so keep in mind that you will need to develop them further. Nevertheless, they should inspire some ideas for your project.
To develop a suitable research topic, you’ll need to identify a clear and convincing research gap , and a viable plan to fill that gap. If this sounds foreign to you, check out our free research topic webinar that explores how to find and refine a high-quality research topic, from scratch. Alternatively, consider our 1-on-1 coaching service .

Cybersecurity-Related Research Topics
- Developing machine learning algorithms for early detection of cybersecurity threats.
- The use of artificial intelligence in optimizing network traffic for telecommunication companies.
- Investigating the impact of quantum computing on existing encryption methods.
- The application of blockchain technology in securing Internet of Things (IoT) devices.
- Developing efficient data mining techniques for large-scale social media analytics.
- The role of virtual reality in enhancing online education platforms.
- Investigating the effectiveness of various algorithms in reducing energy consumption in data centers.
- The impact of edge computing on the performance of mobile applications in remote areas.
- The application of computer vision techniques in automated medical diagnostics.
- Developing natural language processing tools for sentiment analysis in customer service.
- The use of augmented reality for training in high-risk industries like oil and gas.
- Investigating the challenges of integrating AI into legacy enterprise systems.
- The role of IT in managing supply chain disruptions during global crises.
- Developing adaptive cybersecurity strategies for small and medium-sized enterprises.
- The impact of 5G technology on the development of smart city solutions.
- The application of machine learning in personalized e-commerce recommendations.
- Investigating the use of cloud computing in improving government service delivery.
- The role of IT in enhancing sustainability in the manufacturing sector.
- Developing advanced algorithms for autonomous vehicle navigation.
- The application of biometrics in enhancing banking security systems.
- Investigating the ethical implications of facial recognition technology.
- The role of data analytics in optimizing healthcare delivery systems.
- Developing IoT solutions for efficient energy management in smart homes.
- The impact of mobile computing on the evolution of e-health services.
- The application of IT in disaster response and management.
Cybersecurity Research Ideas (Continued)
- Assessing the security implications of quantum computing on modern encryption methods.
- The role of artificial intelligence in detecting and preventing phishing attacks.
- Blockchain technology in secure voting systems: opportunities and challenges.
- Cybersecurity strategies for protecting smart grids from targeted attacks.
- Developing a cyber incident response framework for small to medium-sized enterprises.
- The effectiveness of behavioural biometrics in preventing identity theft.
- Securing Internet of Things (IoT) devices in healthcare: risks and solutions.
- Analysis of cyber warfare tactics and their implications on national security.
- Exploring the ethical boundaries of offensive cybersecurity measures.
- Machine learning algorithms for predicting and mitigating DDoS attacks.
- Study of cryptocurrency-related cybercrimes: patterns and prevention strategies.
- Evaluating the impact of GDPR on data breach response strategies in the EU.
- Developing enhanced security protocols for mobile banking applications.
- An examination of cyber espionage tactics and countermeasures.
- The role of human error in cybersecurity breaches: a behavioural analysis.
- Investigating the use of deep fakes in cyber fraud: detection and prevention.
- Cloud computing security: managing risks in multi-tenant environments.
- Next-generation firewalls: evaluating performance and security features.
- The impact of 5G technology on cybersecurity strategies and policies.
- Secure coding practices: reducing vulnerabilities in software development.
- Assessing the role of cyber insurance in mitigating financial losses from cyber attacks.
- Implementing zero trust architecture in corporate networks: challenges and benefits.
- Ransomware attacks on critical infrastructure: case studies and defence strategies.
- Using big data analytics for proactive cyber threat intelligence.
- Evaluating the effectiveness of cybersecurity awareness training in organisations.
Recent Cybersecurity-Related Studies
While the ideas we’ve presented above are a decent starting point for finding a research topic, they are fairly generic and non-specific. So, it helps to look at actual studies in the cybersecurity space to see how this all comes together in practice.
Below, we’ve included a selection of recent studies to help refine your thinking. These are actual studies, so they can provide some useful insight as to what a research topic looks like in practice.
- Cyber Security Vulnerability Detection Using Natural Language Processing (Singh et al., 2022)
- Security for Cloud-Native Systems with an AI-Ops Engine (Ck et al., 2022)
- Overview of Cyber Security (Yadav, 2022)
- Exploring the Top Five Evolving Threats in Cybersecurity: An In-Depth Overview (Mijwil et al., 2023)
- Cyber Security: Strategy to Security Challenges A Review (Nistane & Sharma, 2022)
- A Review Paper on Cyber Security (K & Venkatesh, 2022)
- The Significance of Machine Learning and Deep Learning Techniques in Cybersecurity: A Comprehensive Review (Mijwil, 2023)
- Towards Artificial Intelligence-Based Cybersecurity: The Practices and ChatGPT Generated Ways to Combat Cybercrime (Mijwil et al., 2023)
- ESTABLISHING CYBERSECURITY AWARENESS OF TECHNICAL SECURITY MEASURES THROUGH A SERIOUS GAME (Harding et al., 2022)
- Efficiency Evaluation of Cyber Security Based on EBM-DEA Model (Nguyen et al., 2022)
- An Overview of the Present and Future of User Authentication (Al Kabir & Elmedany, 2022)
- Cybersecurity Enterprises Policies: A Comparative Study (Mishra et al., 2022)
- The Rise of Ransomware: A Review of Attacks, Detection Techniques, and Future Challenges (Kamil et al., 2022)
- On the scale of Cyberspace and Cybersecurity (Pathan, 2022)
- Analysis of techniques and attacking pattern in cyber security approach (Sharma et al., 2022)
- Impact of Artificial Intelligence on Information Security in Business (Alawadhi et al., 2022)
- Deployment of Artificial Intelligence with Bootstrapped Meta-Learning in Cyber Security (Sasikala & Sharma, 2022)
- Optimization of Secure Coding Practices in SDLC as Part of Cybersecurity Framework (Jakimoski et al., 2022)
- CySSS ’22: 1st International Workshop on Cybersecurity and Social Sciences (Chan-Tin & Kennison, 2022)
As you can see, these research topics are a lot more focused than the generic topic ideas we presented earlier. So, for you to develop a high-quality research topic, you’ll need to get specific and laser-focused on a specific context with specific variables of interest. In the video below, we explore some other important things you’ll need to consider when crafting your research topic.
Get 1-On-1 Help
If you’re still unsure about how to find a quality research topic, check out our Research Topic Kickstarter service, which is the perfect starting point for developing a unique, well-justified research topic.

You Might Also Like:

Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly
- Privacy Policy

Home » 500+ Cyber Security Research Topics
500+ Cyber Security Research Topics

Cybersecurity has become an increasingly important topic in recent years as more and more of our lives are spent online. With the rise of the digital age, there has been a corresponding increase in the number and severity of cyber attacks. As such, research into cybersecurity has become critical in order to protect individuals, businesses, and governments from these threats. In this blog post, we will explore some of the most pressing cybersecurity research topics, from the latest trends in cyber attacks to emerging technologies that can help prevent them. Whether you are a cybersecurity professional, a Master’s or Ph.D. student, or simply interested in the field, this post will provide valuable insights into the challenges and opportunities in this rapidly evolving area of study.
Cyber Security Research Topics
Cyber Security Research Topics are as follows:
- The role of machine learning in detecting cyber threats
- The impact of cloud computing on cyber security
- Cyber warfare and its effects on national security
- The rise of ransomware attacks and their prevention methods
- Evaluating the effectiveness of network intrusion detection systems
- The use of blockchain technology in enhancing cyber security
- Investigating the role of cyber security in protecting critical infrastructure
- The ethics of hacking and its implications for cyber security professionals
- Developing a secure software development lifecycle (SSDLC)
- The role of artificial intelligence in cyber security
- Evaluating the effectiveness of multi-factor authentication
- Investigating the impact of social engineering on cyber security
- The role of cyber insurance in mitigating cyber risks
- Developing secure IoT (Internet of Things) systems
- Investigating the challenges of cyber security in the healthcare industry
- Evaluating the effectiveness of penetration testing
- Investigating the impact of big data on cyber security
- The role of quantum computing in breaking current encryption methods
- Developing a secure BYOD (Bring Your Own Device) policy
- The impact of cyber security breaches on a company’s reputation
- The role of cyber security in protecting financial transactions
- Evaluating the effectiveness of anti-virus software
- The use of biometrics in enhancing cyber security
- Investigating the impact of cyber security on the supply chain
- The role of cyber security in protecting personal privacy
- Developing a secure cloud storage system
- Evaluating the effectiveness of firewall technologies
- Investigating the impact of cyber security on e-commerce
- The role of cyber security in protecting intellectual property
- Developing a secure remote access policy
- Investigating the challenges of securing mobile devices
- The role of cyber security in protecting government agencies
- Evaluating the effectiveness of cyber security training programs
- Investigating the impact of cyber security on the aviation industry
- The role of cyber security in protecting online gaming platforms
- Developing a secure password management system
- Investigating the challenges of securing smart homes
- The impact of cyber security on the automotive industry
- The role of cyber security in protecting social media platforms
- Developing a secure email system
- Evaluating the effectiveness of encryption methods
- Investigating the impact of cyber security on the hospitality industry
- The role of cyber security in protecting online education platforms
- Developing a secure backup and recovery strategy
- Investigating the challenges of securing virtual environments
- The impact of cyber security on the energy sector
- The role of cyber security in protecting online voting systems
- Developing a secure chat platform
- Investigating the impact of cyber security on the entertainment industry
- The role of cyber security in protecting online dating platforms
- Artificial Intelligence and Machine Learning in Cybersecurity
- Quantum Cryptography and Post-Quantum Cryptography
- Internet of Things (IoT) Security
- Developing a framework for cyber resilience in critical infrastructure
- Understanding the fundamentals of encryption algorithms
- Cyber security challenges for small and medium-sized businesses
- Developing secure coding practices for web applications
- Investigating the role of cyber security in protecting online privacy
- Network security protocols and their importance
- Social engineering attacks and how to prevent them
- Investigating the challenges of securing personal devices and home networks
- Developing a basic incident response plan for cyber attacks
- The impact of cyber security on the financial sector
- Understanding the role of cyber security in protecting critical infrastructure
- Mobile device security and common vulnerabilities
- Investigating the challenges of securing cloud-based systems
- Cyber security and the Internet of Things (IoT)
- Biometric authentication and its role in cyber security
- Developing secure communication protocols for online messaging platforms
- The importance of cyber security in e-commerce
- Understanding the threats and vulnerabilities associated with social media platforms
- Investigating the role of cyber security in protecting intellectual property
- The basics of malware analysis and detection
- Developing a basic cyber security awareness training program
- Understanding the threats and vulnerabilities associated with public Wi-Fi networks
- Investigating the challenges of securing online banking systems
- The importance of password management and best practices
- Cyber security and cloud computing
- Understanding the role of cyber security in protecting national security
- Investigating the challenges of securing online gaming platforms
- The basics of cyber threat intelligence
- Developing secure authentication mechanisms for online services
- The impact of cyber security on the healthcare sector
- Understanding the basics of digital forensics
- Investigating the challenges of securing smart home devices
- The role of cyber security in protecting against cyberbullying
- Developing secure file transfer protocols for sensitive information
- Understanding the challenges of securing remote work environments
- Investigating the role of cyber security in protecting against identity theft
- The basics of network intrusion detection and prevention systems
- Developing secure payment processing systems
- Understanding the role of cyber security in protecting against ransomware attacks
- Investigating the challenges of securing public transportation systems
- The basics of network segmentation and its importance in cyber security
- Developing secure user access management systems
- Understanding the challenges of securing supply chain networks
- The role of cyber security in protecting against cyber espionage
- Investigating the challenges of securing online educational platforms
- The importance of data backup and disaster recovery planning
- Developing secure email communication protocols
- Understanding the basics of threat modeling and risk assessment
- Investigating the challenges of securing online voting systems
- The role of cyber security in protecting against cyber terrorism
- Developing secure remote access protocols for corporate networks.
- Investigating the challenges of securing artificial intelligence systems
- The role of machine learning in enhancing cyber threat intelligence
- Evaluating the effectiveness of deception technologies in cyber security
- Investigating the impact of cyber security on the adoption of emerging technologies
- The role of cyber security in protecting smart cities
- Developing a risk-based approach to cyber security governance
- Investigating the impact of cyber security on economic growth and innovation
- The role of cyber security in protecting human rights in the digital age
- Developing a secure digital identity system
- Investigating the impact of cyber security on global political stability
- The role of cyber security in protecting the Internet of Things (IoT)
- Developing a secure supply chain management system
- Investigating the challenges of securing cloud-native applications
- The role of cyber security in protecting against insider threats
- Developing a secure software-defined network (SDN)
- Investigating the impact of cyber security on the adoption of mobile payments
- The role of cyber security in protecting against cyber warfare
- Developing a secure distributed ledger technology (DLT) system
- Investigating the impact of cyber security on the digital divide
- The role of cyber security in protecting against state-sponsored attacks
- Developing a secure Internet infrastructure
- Investigating the challenges of securing industrial control systems (ICS)
- Developing a secure quantum communication system
- Investigating the impact of cyber security on global trade and commerce
- Developing a secure decentralized authentication system
- Investigating the challenges of securing edge computing systems
- Developing a secure hybrid cloud system
- Investigating the impact of cyber security on the adoption of smart cities
- The role of cyber security in protecting against cyber propaganda
- Developing a secure blockchain-based voting system
- Investigating the challenges of securing cyber-physical systems (CPS)
- The role of cyber security in protecting against cyber hate speech
- Developing a secure machine learning system
- Investigating the impact of cyber security on the adoption of autonomous vehicles
- The role of cyber security in protecting against cyber stalking
- Developing a secure data-driven decision-making system
- Investigating the challenges of securing social media platforms
- The role of cyber security in protecting against cyberbullying in schools
- Developing a secure open source software ecosystem
- Investigating the impact of cyber security on the adoption of smart homes
- The role of cyber security in protecting against cyber fraud
- Developing a secure software supply chain
- Investigating the challenges of securing cloud-based healthcare systems
- The role of cyber security in protecting against cyber harassment
- Developing a secure multi-party computation system
- Investigating the impact of cyber security on the adoption of virtual and augmented reality technologies.
- Cybersecurity in Cloud Computing Environments
- Cyber Threat Intelligence and Analysis
- Blockchain Security
- Data Privacy and Protection
- Cybersecurity in Industrial Control Systems
- Mobile Device Security
- The importance of cyber security in the digital age
- The ethics of cyber security and privacy
- The role of government in regulating cyber security
- Cyber security threats and vulnerabilities in the healthcare sector
- Understanding the risks associated with social media and cyber security
- The impact of cyber security on e-commerce
- The effectiveness of cyber security awareness training programs
- The role of biometric authentication in cyber security
- The importance of password management in cyber security
- The basics of network security protocols and their importance
- The challenges of securing online gaming platforms
- The role of cyber security in protecting national security
- The impact of cyber security on the legal sector
- The ethics of cyber warfare
- The challenges of securing the Internet of Things (IoT)
- Understanding the basics of malware analysis and detection
- The challenges of securing public transportation systems
- The impact of cyber security on the insurance industry
- The role of cyber security in protecting against ransomware attacks
- The challenges of securing remote work environments
- Understanding the threats and vulnerabilities associated with social engineering attacks
- The impact of cyber security on the education sector
- Investigating the challenges of securing supply chain networks
- The challenges of securing personal devices and home networks
- The importance of secure coding practices for web applications
- The impact of cyber security on the hospitality industry
- The role of cyber security in protecting against identity theft
- The challenges of securing public Wi-Fi networks
- The importance of cyber security in protecting critical infrastructure
- The challenges of securing cloud-based storage systems
- The effectiveness of antivirus software in cyber security
- Developing secure payment processing systems.
- Cybersecurity in Healthcare
- Social Engineering and Phishing Attacks
- Cybersecurity in Autonomous Vehicles
- Cybersecurity in Smart Cities
- Cybersecurity Risk Assessment and Management
- Malware Analysis and Detection Techniques
- Cybersecurity in the Financial Sector
- Cybersecurity in Government Agencies
- Cybersecurity and Artificial Life
- Cybersecurity for Critical Infrastructure Protection
- Cybersecurity in the Education Sector
- Cybersecurity in Virtual Reality and Augmented Reality
- Cybersecurity in the Retail Industry
- Cryptocurrency Security
- Cybersecurity in Supply Chain Management
- Cybersecurity and Human Factors
- Cybersecurity in the Transportation Industry
- Cybersecurity in Gaming Environments
- Cybersecurity in Social Media Platforms
- Cybersecurity and Biometrics
- Cybersecurity and Quantum Computing
- Cybersecurity in 5G Networks
- Cybersecurity in Aviation and Aerospace Industry
- Cybersecurity in Agriculture Industry
- Cybersecurity in Space Exploration
- Cybersecurity in Military Operations
- Cybersecurity and Cloud Storage
- Cybersecurity in Software-Defined Networks
- Cybersecurity and Artificial Intelligence Ethics
- Cybersecurity and Cyber Insurance
- Cybersecurity in the Legal Industry
- Cybersecurity and Data Science
- Cybersecurity in Energy Systems
- Cybersecurity in E-commerce
- Cybersecurity in Identity Management
- Cybersecurity in Small and Medium Enterprises
- Cybersecurity in the Entertainment Industry
- Cybersecurity and the Internet of Medical Things
- Cybersecurity and the Dark Web
- Cybersecurity and Wearable Technology
- Cybersecurity in Public Safety Systems.
- Threat Intelligence for Industrial Control Systems
- Privacy Preservation in Cloud Computing
- Network Security for Critical Infrastructure
- Cryptographic Techniques for Blockchain Security
- Malware Detection and Analysis
- Cyber Threat Hunting Techniques
- Cybersecurity Risk Assessment
- Machine Learning for Cybersecurity
- Cybersecurity in Financial Institutions
- Cybersecurity for Smart Cities
- Cybersecurity in Aviation
- Cybersecurity in the Automotive Industry
- Cybersecurity in the Energy Sector
- Cybersecurity in Telecommunications
- Cybersecurity for Mobile Devices
- Biometric Authentication for Cybersecurity
- Cybersecurity for Artificial Intelligence
- Cybersecurity for Social Media Platforms
- Cybersecurity in the Gaming Industry
- Cybersecurity in the Defense Industry
- Cybersecurity for Autonomous Systems
- Cybersecurity for Quantum Computing
- Cybersecurity for Augmented Reality and Virtual Reality
- Cybersecurity in Cloud-Native Applications
- Cybersecurity for Smart Grids
- Cybersecurity in Distributed Ledger Technology
- Cybersecurity for Next-Generation Wireless Networks
- Cybersecurity for Digital Identity Management
- Cybersecurity for Open Source Software
- Cybersecurity for Smart Homes
- Cybersecurity for Smart Transportation Systems
- Cybersecurity for Cyber Physical Systems
- Cybersecurity for Critical National Infrastructure
- Cybersecurity for Smart Agriculture
- Cybersecurity for Retail Industry
- Cybersecurity for Digital Twins
- Cybersecurity for Quantum Key Distribution
- Cybersecurity for Digital Healthcare
- Cybersecurity for Smart Logistics
- Cybersecurity for Wearable Devices
- Cybersecurity for Edge Computing
- Cybersecurity for Cognitive Computing
- Cybersecurity for Industrial IoT
- Cybersecurity for Intelligent Transportation Systems
- Cybersecurity for Smart Water Management Systems
- The rise of cyber terrorism and its impact on national security
- The impact of artificial intelligence on cyber security
- Analyzing the effectiveness of biometric authentication for securing data
- The impact of social media on cyber security and privacy
- The future of cyber security in the Internet of Things (IoT) era
- The role of machine learning in detecting and preventing cyber attacks
- The effectiveness of encryption in securing sensitive data
- The impact of quantum computing on cyber security
- The rise of cyber bullying and its effects on mental health
- Investigating cyber espionage and its impact on national security
- The effectiveness of cyber insurance in mitigating cyber risks
- The role of blockchain technology in cyber security
- Investigating the effectiveness of cyber security awareness training programs
- The impact of cyber attacks on critical infrastructure
- Analyzing the effectiveness of firewalls in protecting against cyber attacks
- The impact of cyber crime on the economy
- Investigating the effectiveness of multi-factor authentication in securing data
- The future of cyber security in the age of quantum internet
- The impact of big data on cyber security
- The role of cybersecurity in the education system
- Investigating the use of deception techniques in cyber security
- The impact of cyber attacks on the healthcare industry
- The effectiveness of cyber threat intelligence in mitigating cyber risks
- The role of cyber security in protecting financial institutions
- Investigating the use of machine learning in cyber security risk assessment
- The impact of cyber attacks on the transportation industry
- The effectiveness of network segmentation in protecting against cyber attacks
- Investigating the effectiveness of biometric identification in cyber security
- The impact of cyber attacks on the hospitality industry
- The future of cyber security in the era of autonomous vehicles
- The effectiveness of intrusion detection systems in protecting against cyber attacks
- The role of cyber security in protecting small businesses
- Investigating the effectiveness of virtual private networks (VPNs) in securing data
- The impact of cyber attacks on the energy sector
- The effectiveness of cyber security regulations in mitigating cyber risks
- Investigating the use of deception technology in cyber security
- The impact of cyber attacks on the retail industry
- The effectiveness of cyber security in protecting critical infrastructure
- The role of cyber security in protecting intellectual property in the entertainment industry
- Investigating the effectiveness of intrusion prevention systems in protecting against cyber attacks
- The impact of cyber attacks on the aerospace industry
- The future of cyber security in the era of quantum computing
- The effectiveness of cyber security in protecting against ransomware attacks
- The role of cyber security in protecting personal and sensitive data
- Investigating the effectiveness of cloud security solutions in protecting against cyber attacks
- The impact of cyber attacks on the manufacturing industry
- The effective cyber security and the future of e-votingness of cyber security in protecting against social engineering attacks
- Investigating the effectiveness of end-to-end encryption in securing data
- The impact of cyber attacks on the insurance industry
- The future of cyber security in the era of artificial intelligence
- The effectiveness of cyber security in protecting against distributed denial-of-service (DDoS) attacks
- The role of cyber security in protecting against phishing attacks
- Investigating the effectiveness of user behavior analytics
- The impact of emerging technologies on cyber security
- Developing a framework for cyber threat intelligence
- The effectiveness of current cyber security measures
- Cyber security and data privacy in the age of big data
- Cloud security and virtualization technologies
- Cryptography and its role in cyber security
- Cyber security in critical infrastructure protection
- Cyber security in the Internet of Things (IoT)
- Cyber security in e-commerce and online payment systems
- Cyber security and the future of digital currencies
- The impact of social engineering on cyber security
- Cyber security and ethical hacking
- Cyber security challenges in the healthcare industry
- Cyber security and digital forensics
- Cyber security in the financial sector
- Cyber security in the transportation industry
- The impact of artificial intelligence on cyber security risks
- Cyber security and mobile devices
- Cyber security in the energy sector
- Cyber security and supply chain management
- The role of machine learning in cyber security
- Cyber security in the defense sector
- The impact of the Dark Web on cyber security
- Cyber security in social media and online communities
- Cyber security challenges in the gaming industry
- Cyber security and cloud-based applications
- The role of blockchain in cyber security
- Cyber security and the future of autonomous vehicles
- Cyber security in the education sector
- Cyber security in the aviation industry
- The impact of 5G on cyber security
- Cyber security and insider threats
- Cyber security and the legal system
- The impact of cyber security on business operations
- Cyber security and the role of human behavior
- Cyber security in the hospitality industry
- The impact of cyber security on national security
- Cyber security and the use of biometrics
- Cyber security and the role of social media influencers
- The impact of cyber security on small and medium-sized enterprises
- Cyber security and cyber insurance
- The impact of cyber security on the job market
- Cyber security and international relations
- Cyber security and the role of government policies
- The impact of cyber security on privacy laws
- Cyber security in the media and entertainment industry
- The role of cyber security in digital marketing
- Cyber security and the role of cybersecurity professionals
- Cyber security in the retail industry
- The impact of cyber security on the stock market
- Cyber security and intellectual property protection
- Cyber security and online dating
- The impact of cyber security on healthcare innovation
- Cyber security and the future of e-voting
- Cyber security and the role of open source software
- Cyber security and the use of social engineering in cyber attacks
- The impact of cyber security on the aviation industry
- Cyber security and the role of cyber security awareness training
- Cyber security and the role of cybersecurity standards and best practices
- Cyber security in the legal industry
- The impact of cyber security on human rights
- Cyber security and the role of public-private partnerships
- Cyber security and the future of e-learning
- Cyber security and the role of mobile applications
- The impact of cyber security on environmental sustainability
- Cyber security and the role of threat intelligence sharing
- Cyber security and the future of smart homes
- Cyber security and the role of cybersecurity certifications
- The impact of cyber security on international trade
- Cyber security and the role of cyber security auditing
About the author
Muhammad Hassan
Researcher, Academic Writer, Web developer
You may also like

200+ Funny Research Topics

500+ Sports Research Topics

500+ Environmental Research Topics

500+ Economics Research Topics

500+ Physics Research Topics

500+ Google Scholar Research Topics
Cybersecurity

Most Cited Paper
We are pleased to announce the top 5 cited papers of Cybersecurity.
This list is based on the cites received from 2018 to 2023. You can find the top five articles here .
Cybersecurity Award 2024
Call for Nomination - Deadline Extension
The Cybersecurity Award is held annually and presented to authors whose work represents outstanding and groundbreaking research in all essential aspects of cybersecurity from the previous year.
- Most accessed
Polar code-based secure transmission with higher message rate combining channel entropy and computational entropy
Authors: Chen An, Mengjie Huang, Xianhui Lu, Lei Bi and Weijie Li
Dissecting zero trust: research landscape and its implementation in IoT
Authors: Chunwen Liu, Ru Tan, Yang Wu, Yun Feng, Ze Jin, Fangjiao Zhang, Yuling Liu and Qixu Liu
Study of smart grid cyber-security, examining architectures, communication networks, cyber-attacks, countermeasure techniques, and challenges
Authors: Batoul Achaal, Mehdi Adda, Maxime Berger, Hussein Ibrahim and Ali Awde
A multi-agent adaptive deep learning framework for online intrusion detection
Authors: Mahdi Soltani, Khashayar Khajavi, Mahdi Jafari Siavoshani and Amir Hossein Jahangir
Iterative and mixed-spaces image gradient inversion attack in federated learning
Authors: Linwei Fang, Liming Wang and Hongjia Li
Most recent articles RSS
View all articles
Survey of intrusion detection systems: techniques, datasets and challenges
Authors: Ansam Khraisat, Iqbal Gondal, Peter Vamplew and Joarder Kamruzzaman
Review and insight on the behavioral aspects of cybersecurity
Authors: Rachid Ait Maalem Lahcen, Bruce Caulkins, Ram Mohapatra and Manish Kumar
Fuzzing: a survey
Authors: Jun Li, Bodong Zhao and Chao Zhang
A critical review of intrusion detection systems in the internet of things: techniques, deployment strategy, validation strategy, attacks, public datasets and challenges
Authors: Ansam Khraisat and Ammar Alazab
Detecting telecommunication fraud by understanding the contents of a call
Authors: Qianqian Zhao, Kai Chen, Tongxin Li, Yi Yang and XiaoFeng Wang
Most accessed articles RSS
Thematic Series
2020 Data-Driven Security Edited by: Yang Liu, Xinming Ou, Xinyu Xing, Guozhu Meng
2019 Data Security and Privacy Edited by: Dan Lin, Jingqiang Lin and Bo Luo
Information Abuse Prevention Edited by: Gang Li and Jianlong Tan
2018 System Security Edited by: Peng Liu
AI and Security Edited by: Xiaofeng Wang
Aims and scope
This journal is aimed to systematically cover all essential aspects of cybersecurity, with a focus on reporting on cyberspace security issues, the latest research results, and real-world deployment of security technologies.
The journal publishes research articles and reviews in the areas including, but not limited to:
• Cryptography and its applications • Network and critical infrastructure security • Hardware security • Software and system security • Cybersecurity data analytics • Data-driven security and measurement studies • Adversarial reasoning • Malware analysis • Privacy-enhancing technologies and anonymity • IoT Security • AI Security
Why submit to us
• 1 st open access journal on Cybersecurity • APC fully covered by IIE, CAS • Served by a dedicated international editorial board to give thorough swift editorial response
Editor-in-Chief: MENG Dan

Full Professor in Institute of Information Engineering (IIE), Chinese Academy of Sciences (CAS). His work focuses on network and system security, parallel distributed processing. He has lead important research projects including Dawning supercomputers, National Science and Technology Major Project, National High Technology Research and Development Program of China, and strategic priority research program of CAS. He has published over one hundred peer-reviewed papers. He is the director of IIE, after serving as the deputy director of IIE, the deputy director of the High Technology Research and Development Bureau of CAS.
Executive Editor-in-Chief: LIU Peng

LIU Peng received his BS and MS degrees from the University of Science and Technology of China, and his PhD from George Mason University in 1999. Dr. Liu is a Professor of Information Sciences and Technology, founding Director of the Center for Cyber-Security, Information Privacy, and Trust, and founding Director of the Cyber Security Lab at Penn State University. His research interests are in all areas of computer and network security. He has published a monograph and over 260 refereed technical papers. His research has been sponsored by NSF, ARO, AFOSR, DARPA, DHS, DOE, AFRL, NSA, TTC, CISCO, and HP. He has served as a program (co-)chair or general (co-)chair for over 10 international conferences (e.g., Asia CCS 2010) and workshops (e.g., MTD 2016). He chaired the Steering Committee of SECURECOMM during 2008-14. He has served on over 100 program committees and reviewed papers for numerous journals. He is an associate editor for IEEE TDSC. He is a recipient of the DOE Early Career Principle Investigator Award. He has co-led the effort to make Penn State a NSA-certified National Center of Excellence in Information Assurance Education and Research. He has advised or co-advised over 30 PhD dissertations to completion.
- Editorial Board
- Sign up for article alerts and news from this journal
Affiliated with

The Institute of Information Engineering (IIE) is a national research institute in Beijing that specializes in comprehensive research on theories and applications related to information technology.
IIE strives to be a leading global academic institution by creating first-class research platforms and attracting top researchers. It also seeks to become an important national strategic power in the field of information technology.
IIE’s mission is to promote China’s innovation and industrial competitiveness by advancing information science, standards, and technology in ways that enhance economic security and public safety as well as improve our quality of life.
Read more..
The journal is indexed by
- EI Compendex
- Emerging Sources Citation Index
- EBSCO Discovery Service
- Institute of Scientific and Technical Information of China
- Google Scholar
- Norwegian Register for Scientific Journals and Series
- OCLC WorldCat Discovery Service
- ProQuest-ExLibris Primo
- ProQuest-ExLibris Summon
- TD Net Discovery Service
- UGC-CARE List (India)
Annual Journal Metrics
2022 Citation Impact 3.1 - 2-year Impact Factor 4.8 - 5-year Impact Factor 2.071 - SNIP (Source Normalized Impact per Paper) 1.266 - SJR (SCImago Journal Rank)
2023 Speed 8 days submission to first editorial decision for all manuscripts (Median) 95 days submission to accept (Median)
2023 Usage 408,523 downloads 15 Altmetric mentions
- ISSN: 2523-3246 (electronic)
- Search Menu
- Editor's Choice
- Author Guidelines
- Submission Site
- Open Access
- About Journal of Cybersecurity
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Journals on Oxford Academic
- Books on Oxford Academic

Editors-in-Chief
Tyler Moore
About the journal
Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …
Latest articles

Call for Papers: Workshop on the Economics of Information Security
Journal of Cybersecurity is inviting submissions to a new special issue from the workshop on the economics of information security. Authors whose papers appeared at the workshop are invited to submit a revised version to the journal.

Call for Papers
Journal of Cybersecurity is soliciting papers for a special collection on the philosophy of information security. This collection will explore research at the intersection of philosophy, information security, and philosophy of science.
Find out more

Submit your paper
Join the conversation moving the science of security forward. Visit our Instructions to Authors for more information about how to submit your manuscript.

High-Impact Research Collection
Explore a collection of recently published high-impact research in the Journal of Cybersecurity .
Browse the collection here

Email alerts
Register to receive table of contents email alerts as soon as new issues of Journal of Cybersecurity are published online.

Read and Publish deals
Authors interested in publishing in Journal of Cybersecurity may be able to publish their paper Open Access using funds available through their institution’s agreement with OUP.
Find out if your institution is participating
Related Titles

Affiliations
- Online ISSN 2057-2093
- Print ISSN 2057-2085
- Copyright © 2024 Oxford University Press
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
- Survey Paper
- Open access
- Published: 01 July 2020
Cybersecurity data science: an overview from machine learning perspective
- Iqbal H. Sarker ORCID: orcid.org/0000-0003-1740-5517 1 , 2 ,
- A. S. M. Kayes 3 ,
- Shahriar Badsha 4 ,
- Hamed Alqahtani 5 ,
- Paul Watters 3 &
- Alex Ng 3
Journal of Big Data volume 7 , Article number: 41 ( 2020 ) Cite this article
145k Accesses
244 Citations
51 Altmetric
Metrics details
In a computing context, cybersecurity is undergoing massive shifts in technology and its operations in recent days, and data science is driving the change. Extracting security incident patterns or insights from cybersecurity data and building corresponding data-driven model , is the key to make a security system automated and intelligent. To understand and analyze the actual phenomena with data, various scientific methods, machine learning techniques, processes, and systems are used, which is commonly known as data science. In this paper, we focus and briefly discuss on cybersecurity data science , where the data is being gathered from relevant cybersecurity sources, and the analytics complement the latest data-driven patterns for providing more effective security solutions. The concept of cybersecurity data science allows making the computing process more actionable and intelligent as compared to traditional ones in the domain of cybersecurity. We then discuss and summarize a number of associated research issues and future directions . Furthermore, we provide a machine learning based multi-layered framework for the purpose of cybersecurity modeling. Overall, our goal is not only to discuss cybersecurity data science and relevant methods but also to focus the applicability towards data-driven intelligent decision making for protecting the systems from cyber-attacks.
Introduction
Due to the increasing dependency on digitalization and Internet-of-Things (IoT) [ 1 ], various security incidents such as unauthorized access [ 2 ], malware attack [ 3 ], zero-day attack [ 4 ], data breach [ 5 ], denial of service (DoS) [ 2 ], social engineering or phishing [ 6 ] etc. have grown at an exponential rate in recent years. For instance, in 2010, there were less than 50 million unique malware executables known to the security community. By 2012, they were double around 100 million, and in 2019, there are more than 900 million malicious executables known to the security community, and this number is likely to grow, according to the statistics of AV-TEST institute in Germany [ 7 ]. Cybercrime and attacks can cause devastating financial losses and affect organizations and individuals as well. It’s estimated that, a data breach costs 8.19 million USD for the United States and 3.9 million USD on an average [ 8 ], and the annual cost to the global economy from cybercrime is 400 billion USD [ 9 ]. According to Juniper Research [ 10 ], the number of records breached each year to nearly triple over the next 5 years. Thus, it’s essential that organizations need to adopt and implement a strong cybersecurity approach to mitigate the loss. According to [ 11 ], the national security of a country depends on the business, government, and individual citizens having access to applications and tools which are highly secure, and the capability on detecting and eliminating such cyber-threats in a timely way. Therefore, to effectively identify various cyber incidents either previously seen or unseen, and intelligently protect the relevant systems from such cyber-attacks, is a key issue to be solved urgently.
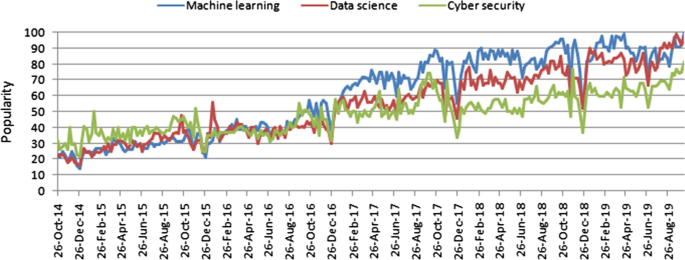
Popularity trends of data science, machine learning and cybersecurity over time, where x-axis represents the timestamp information and y axis represents the corresponding popularity values
Cybersecurity is a set of technologies and processes designed to protect computers, networks, programs and data from attack, damage, or unauthorized access [ 12 ]. In recent days, cybersecurity is undergoing massive shifts in technology and its operations in the context of computing, and data science (DS) is driving the change, where machine learning (ML), a core part of “Artificial Intelligence” (AI) can play a vital role to discover the insights from data. Machine learning can significantly change the cybersecurity landscape and data science is leading a new scientific paradigm [ 13 , 14 ]. The popularity of these related technologies is increasing day-by-day, which is shown in Fig. 1 , based on the data of the last five years collected from Google Trends [ 15 ]. The figure represents timestamp information in terms of a particular date in the x-axis and corresponding popularity in the range of 0 (minimum) to 100 (maximum) in the y-axis. As shown in Fig. 1 , the popularity indication values of these areas are less than 30 in 2014, while they exceed 70 in 2019, i.e., more than double in terms of increased popularity. In this paper, we focus on cybersecurity data science (CDS), which is broadly related to these areas in terms of security data processing techniques and intelligent decision making in real-world applications. Overall, CDS is security data-focused, applies machine learning methods to quantify cyber risks, and ultimately seeks to optimize cybersecurity operations. Thus, the purpose of this paper is for those academia and industry people who want to study and develop a data-driven smart cybersecurity model based on machine learning techniques. Therefore, great emphasis is placed on a thorough description of various types of machine learning methods, and their relations and usage in the context of cybersecurity. This paper does not describe all of the different techniques used in cybersecurity in detail; instead, it gives an overview of cybersecurity data science modeling based on artificial intelligence, particularly from machine learning perspective.
The ultimate goal of cybersecurity data science is data-driven intelligent decision making from security data for smart cybersecurity solutions. CDS represents a partial paradigm shift from traditional well-known security solutions such as firewalls, user authentication and access control, cryptography systems etc. that might not be effective according to today’s need in cyber industry [ 16 , 17 , 18 , 19 ]. The problems are these are typically handled statically by a few experienced security analysts, where data management is done in an ad-hoc manner [ 20 , 21 ]. However, as an increasing number of cybersecurity incidents in different formats mentioned above continuously appear over time, such conventional solutions have encountered limitations in mitigating such cyber risks. As a result, numerous advanced attacks are created and spread very quickly throughout the Internet. Although several researchers use various data analysis and learning techniques to build cybersecurity models that are summarized in “ Machine learning tasks in cybersecurity ” section, a comprehensive security model based on the effective discovery of security insights and latest security patterns could be more useful. To address this issue, we need to develop more flexible and efficient security mechanisms that can respond to threats and to update security policies to mitigate them intelligently in a timely manner. To achieve this goal, it is inherently required to analyze a massive amount of relevant cybersecurity data generated from various sources such as network and system sources, and to discover insights or proper security policies with minimal human intervention in an automated manner.
Analyzing cybersecurity data and building the right tools and processes to successfully protect against cybersecurity incidents goes beyond a simple set of functional requirements and knowledge about risks, threats or vulnerabilities. For effectively extracting the insights or the patterns of security incidents, several machine learning techniques, such as feature engineering, data clustering, classification, and association analysis, or neural network-based deep learning techniques can be used, which are briefly discussed in “ Machine learning tasks in cybersecurity ” section. These learning techniques are capable to find the anomalies or malicious behavior and data-driven patterns of associated security incidents to make an intelligent decision. Thus, based on the concept of data-driven decision making, we aim to focus on cybersecurity data science , where the data is being gathered from relevant cybersecurity sources such as network activity, database activity, application activity, or user activity, and the analytics complement the latest data-driven patterns for providing corresponding security solutions.
The contributions of this paper are summarized as follows.
We first make a brief discussion on the concept of cybersecurity data science and relevant methods to understand its applicability towards data-driven intelligent decision making in the domain of cybersecurity. For this purpose, we also make a review and brief discussion on different machine learning tasks in cybersecurity, and summarize various cybersecurity datasets highlighting their usage in different data-driven cyber applications.
We then discuss and summarize a number of associated research issues and future directions in the area of cybersecurity data science, that could help both the academia and industry people to further research and development in relevant application areas.
Finally, we provide a generic multi-layered framework of the cybersecurity data science model based on machine learning techniques. In this framework, we briefly discuss how the cybersecurity data science model can be used to discover useful insights from security data and making data-driven intelligent decisions to build smart cybersecurity systems.
The remainder of the paper is organized as follows. “ Background ” section summarizes background of our study and gives an overview of the related technologies of cybersecurity data science. “ Cybersecurity data science ” section defines and discusses briefly about cybersecurity data science including various categories of cyber incidents data. In “ Machine learning tasks in cybersecurity ” section, we briefly discuss various categories of machine learning techniques including their relations with cybersecurity tasks and summarize a number of machine learning based cybersecurity models in the field. “ Research issues and future directions ” section briefly discusses and highlights various research issues and future directions in the area of cybersecurity data science. In “ A multi-layered framework for smart cybersecurity services ” section, we suggest a machine learning-based framework to build cybersecurity data science model and discuss various layers with their roles. In “ Discussion ” section, we highlight several key points regarding our studies. Finally, “ Conclusion ” section concludes this paper.
In this section, we give an overview of the related technologies of cybersecurity data science including various types of cybersecurity incidents and defense strategies.
- Cybersecurity
Over the last half-century, the information and communication technology (ICT) industry has evolved greatly, which is ubiquitous and closely integrated with our modern society. Thus, protecting ICT systems and applications from cyber-attacks has been greatly concerned by the security policymakers in recent days [ 22 ]. The act of protecting ICT systems from various cyber-threats or attacks has come to be known as cybersecurity [ 9 ]. Several aspects are associated with cybersecurity: measures to protect information and communication technology; the raw data and information it contains and their processing and transmitting; associated virtual and physical elements of the systems; the degree of protection resulting from the application of those measures; and eventually the associated field of professional endeavor [ 23 ]. Craigen et al. defined “cybersecurity as a set of tools, practices, and guidelines that can be used to protect computer networks, software programs, and data from attack, damage, or unauthorized access” [ 24 ]. According to Aftergood et al. [ 12 ], “cybersecurity is a set of technologies and processes designed to protect computers, networks, programs and data from attacks and unauthorized access, alteration, or destruction”. Overall, cybersecurity concerns with the understanding of diverse cyber-attacks and devising corresponding defense strategies that preserve several properties defined as below [ 25 , 26 ].
Confidentiality is a property used to prevent the access and disclosure of information to unauthorized individuals, entities or systems.
Integrity is a property used to prevent any modification or destruction of information in an unauthorized manner.
Availability is a property used to ensure timely and reliable access of information assets and systems to an authorized entity.
The term cybersecurity applies in a variety of contexts, from business to mobile computing, and can be divided into several common categories. These are - network security that mainly focuses on securing a computer network from cyber attackers or intruders; application security that takes into account keeping the software and the devices free of risks or cyber-threats; information security that mainly considers security and the privacy of relevant data; operational security that includes the processes of handling and protecting data assets. Typical cybersecurity systems are composed of network security systems and computer security systems containing a firewall, antivirus software, or an intrusion detection system [ 27 ].
Cyberattacks and security risks
The risks typically associated with any attack, which considers three security factors, such as threats, i.e., who is attacking, vulnerabilities, i.e., the weaknesses they are attacking, and impacts, i.e., what the attack does [ 9 ]. A security incident is an act that threatens the confidentiality, integrity, or availability of information assets and systems. Several types of cybersecurity incidents that may result in security risks on an organization’s systems and networks or an individual [ 2 ]. These are:
Unauthorized access that describes the act of accessing information to network, systems or data without authorization that results in a violation of a security policy [ 2 ];
Malware known as malicious software, is any program or software that intentionally designed to cause damage to a computer, client, server, or computer network, e.g., botnets. Examples of different types of malware including computer viruses, worms, Trojan horses, adware, ransomware, spyware, malicious bots, etc. [ 3 , 26 ]; Ransom malware, or ransomware , is an emerging form of malware that prevents users from accessing their systems or personal files, or the devices, then demands an anonymous online payment in order to restore access.
Denial-of-Service is an attack meant to shut down a machine or network, making it inaccessible to its intended users by flooding the target with traffic that triggers a crash. The Denial-of-Service (DoS) attack typically uses one computer with an Internet connection, while distributed denial-of-service (DDoS) attack uses multiple computers and Internet connections to flood the targeted resource [ 2 ];
Phishing a type of social engineering , used for a broad range of malicious activities accomplished through human interactions, in which the fraudulent attempt takes part to obtain sensitive information such as banking and credit card details, login credentials, or personally identifiable information by disguising oneself as a trusted individual or entity via an electronic communication such as email, text, or instant message, etc. [ 26 ];
Zero-day attack is considered as the term that is used to describe the threat of an unknown security vulnerability for which either the patch has not been released or the application developers were unaware [ 4 , 28 ].
Beside these attacks mentioned above, privilege escalation [ 29 ], password attack [ 30 ], insider threat [ 31 ], man-in-the-middle [ 32 ], advanced persistent threat [ 33 ], SQL injection attack [ 34 ], cryptojacking attack [ 35 ], web application attack [ 30 ] etc. are well-known as security incidents in the field of cybersecurity. A data breach is another type of security incident, known as a data leak, which is involved in the unauthorized access of data by an individual, application, or service [ 5 ]. Thus, all data breaches are considered as security incidents, however, all the security incidents are not data breaches. Most data breaches occur in the banking industry involving the credit card numbers, personal information, followed by the healthcare sector and the public sector [ 36 ].
Cybersecurity defense strategies
Defense strategies are needed to protect data or information, information systems, and networks from cyber-attacks or intrusions. More granularly, they are responsible for preventing data breaches or security incidents and monitoring and reacting to intrusions, which can be defined as any kind of unauthorized activity that causes damage to an information system [ 37 ]. An intrusion detection system (IDS) is typically represented as “a device or software application that monitors a computer network or systems for malicious activity or policy violations” [ 38 ]. The traditional well-known security solutions such as anti-virus, firewalls, user authentication, access control, data encryption and cryptography systems, however might not be effective according to today’s need in the cyber industry
[ 16 , 17 , 18 , 19 ]. On the other hand, IDS resolves the issues by analyzing security data from several key points in a computer network or system [ 39 , 40 ]. Moreover, intrusion detection systems can be used to detect both internal and external attacks.
Intrusion detection systems are different categories according to the usage scope. For instance, a host-based intrusion detection system (HIDS), and network intrusion detection system (NIDS) are the most common types based on the scope of single computers to large networks. In a HIDS, the system monitors important files on an individual system, while it analyzes and monitors network connections for suspicious traffic in a NIDS. Similarly, based on methodologies, the signature-based IDS, and anomaly-based IDS are the most well-known variants [ 37 ].
Signature-based IDS : A signature can be a predefined string, pattern, or rule that corresponds to a known attack. A particular pattern is identified as the detection of corresponding attacks in a signature-based IDS. An example of a signature can be known patterns or a byte sequence in a network traffic, or sequences used by malware. To detect the attacks, anti-virus software uses such types of sequences or patterns as a signature while performing the matching operation. Signature-based IDS is also known as knowledge-based or misuse detection [ 41 ]. This technique can be efficient to process a high volume of network traffic, however, is strictly limited to the known attacks only. Thus, detecting new attacks or unseen attacks is one of the biggest challenges faced by this signature-based system.
Anomaly-based IDS : The concept of anomaly-based detection overcomes the issues of signature-based IDS discussed above. In an anomaly-based intrusion detection system, the behavior of the network is first examined to find dynamic patterns, to automatically create a data-driven model, to profile the normal behavior, and thus it detects deviations in the case of any anomalies [ 41 ]. Thus, anomaly-based IDS can be treated as a dynamic approach, which follows behavior-oriented detection. The main advantage of anomaly-based IDS is the ability to identify unknown or zero-day attacks [ 42 ]. However, the issue is that the identified anomaly or abnormal behavior is not always an indicator of intrusions. It sometimes may happen because of several factors such as policy changes or offering a new service.
In addition, a hybrid detection approach [ 43 , 44 ] that takes into account both the misuse and anomaly-based techniques discussed above can be used to detect intrusions. In a hybrid system, the misuse detection system is used for detecting known types of intrusions and anomaly detection system is used for novel attacks [ 45 ]. Beside these approaches, stateful protocol analysis can also be used to detect intrusions that identifies deviations of protocol state similarly to the anomaly-based method, however it uses predetermined universal profiles based on accepted definitions of benign activity [ 41 ]. In Table 1 , we have summarized these common approaches highlighting their pros and cons. Once the detecting has been completed, the intrusion prevention system (IPS) that is intended to prevent malicious events, can be used to mitigate the risks in different ways such as manual, providing notification, or automatic process [ 46 ]. Among these approaches, an automatic response system could be more effective as it does not involve a human interface between the detection and response systems.
- Data science
We are living in the age of data, advanced analytics, and data science, which are related to data-driven intelligent decision making. Although, the process of searching patterns or discovering hidden and interesting knowledge from data is known as data mining [ 47 ], in this paper, we use the broader term “data science” rather than data mining. The reason is that, data science, in its most fundamental form, is all about understanding of data. It involves studying, processing, and extracting valuable insights from a set of information. In addition to data mining, data analytics is also related to data science. The development of data mining, knowledge discovery, and machine learning that refers creating algorithms and program which learn on their own, together with the original data analysis and descriptive analytics from the statistical perspective, forms the general concept of “data analytics” [ 47 ]. Nowadays, many researchers use the term “data science” to describe the interdisciplinary field of data collection, preprocessing, inferring, or making decisions by analyzing the data. To understand and analyze the actual phenomena with data, various scientific methods, machine learning techniques, processes, and systems are used, which is commonly known as data science. According to Cao et al. [ 47 ] “data science is a new interdisciplinary field that synthesizes and builds on statistics, informatics, computing, communication, management, and sociology to study data and its environments, to transform data to insights and decisions by following a data-to-knowledge-to-wisdom thinking and methodology”. As a high-level statement in the context of cybersecurity, we can conclude that it is the study of security data to provide data-driven solutions for the given security problems, as known as “the science of cybersecurity data”. Figure 2 shows the typical data-to-insight-to-decision transfer at different periods and general analytic stages in data science, in terms of a variety of analytics goals (G) and approaches (A) to achieve the data-to-decision goal [ 47 ].
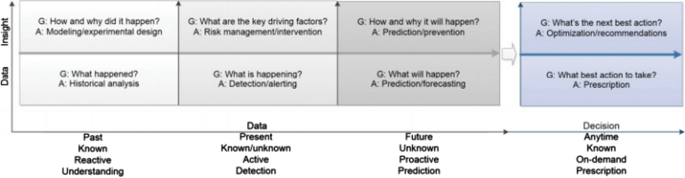
Data-to-insight-to-decision analytic stages in data science [ 47 ]
Based on the analytic power of data science including machine learning techniques, it can be a viable component of security strategies. By using data science techniques, security analysts can manipulate and analyze security data more effectively and efficiently, uncovering valuable insights from data. Thus, data science methodologies including machine learning techniques can be well utilized in the context of cybersecurity, in terms of problem understanding, gathering security data from diverse sources, preparing data to feed into the model, data-driven model building and updating, for providing smart security services, which motivates to define cybersecurity data science and to work in this research area.
Cybersecurity data science
In this section, we briefly discuss cybersecurity data science including various categories of cyber incidents data with the usage in different application areas, and the key terms and areas related to our study.
Understanding cybersecurity data
Data science is largely driven by the availability of data [ 48 ]. Datasets typically represent a collection of information records that consist of several attributes or features and related facts, in which cybersecurity data science is based on. Thus, it’s important to understand the nature of cybersecurity data containing various types of cyberattacks and relevant features. The reason is that raw security data collected from relevant cyber sources can be used to analyze the various patterns of security incidents or malicious behavior, to build a data-driven security model to achieve our goal. Several datasets exist in the area of cybersecurity including intrusion analysis, malware analysis, anomaly, fraud, or spam analysis that are used for various purposes. In Table 2 , we summarize several such datasets including their various features and attacks that are accessible on the Internet, and highlight their usage based on machine learning techniques in different cyber applications. Effectively analyzing and processing of these security features, building target machine learning-based security model according to the requirements, and eventually, data-driven decision making, could play a role to provide intelligent cybersecurity services that are discussed briefly in “ A multi-layered framework for smart cybersecurity services ” section.
Defining cybersecurity data science
Data science is transforming the world’s industries. It is critically important for the future of intelligent cybersecurity systems and services because of “security is all about data”. When we seek to detect cyber threats, we are analyzing the security data in the form of files, logs, network packets, or other relevant sources. Traditionally, security professionals didn’t use data science techniques to make detections based on these data sources. Instead, they used file hashes, custom-written rules like signatures, or manually defined heuristics [ 21 ]. Although these techniques have their own merits in several cases, it needs too much manual work to keep up with the changing cyber threat landscape. On the contrary, data science can make a massive shift in technology and its operations, where machine learning algorithms can be used to learn or extract insight of security incident patterns from the training data for their detection and prevention. For instance, to detect malware or suspicious trends, or to extract policy rules, these techniques can be used.
In recent days, the entire security industry is moving towards data science, because of its capability to transform raw data into decision making. To do this, several data-driven tasks can be associated, such as—(i) data engineering focusing practical applications of data gathering and analysis; (ii) reducing data volume that deals with filtering significant and relevant data to further analysis; (iii) discovery and detection that focuses on extracting insight or incident patterns or knowledge from data; (iv) automated models that focus on building data-driven intelligent security model; (v) targeted security alerts focusing on the generation of remarkable security alerts based on discovered knowledge that minimizes the false alerts, and (vi) resource optimization that deals with the available resources to achieve the target goals in a security system. While making data-driven decisions, behavioral analysis could also play a significant role in the domain of cybersecurity [ 81 ].
Thus, the concept of cybersecurity data science incorporates the methods and techniques of data science and machine learning as well as the behavioral analytics of various security incidents. The combination of these technologies has given birth to the term “cybersecurity data science”, which refers to collect a large amount of security event data from different sources and analyze it using machine learning technologies for detecting security risks or attacks either through the discovery of useful insights or the latest data-driven patterns. It is, however, worth remembering that cybersecurity data science is not just about a collection of machine learning algorithms, rather, a process that can help security professionals or analysts to scale and automate their security activities in a smart way and in a timely manner. Therefore, the formal definition can be as follows: “Cybersecurity data science is a research or working area existing at the intersection of cybersecurity, data science, and machine learning or artificial intelligence, which is mainly security data-focused, applies machine learning methods, attempts to quantify cyber-risks or incidents, and promotes inferential techniques to analyze behavioral patterns in security data. It also focuses on generating security response alerts, and eventually seeks for optimizing cybersecurity solutions, to build automated and intelligent cybersecurity systems.”
Table 3 highlights some key terms associated with cybersecurity data science. Overall, the outputs of cybersecurity data science are typically security data products, which can be a data-driven security model, policy rule discovery, risk or attack prediction, potential security service and recommendation, or the corresponding security system depending on the given security problem in the domain of cybersecurity. In the next section, we briefly discuss various machine learning tasks with examples within the scope of our study.
Machine learning tasks in cybersecurity
Machine learning (ML) is typically considered as a branch of “Artificial Intelligence”, which is closely related to computational statistics, data mining and analytics, data science, particularly focusing on making the computers to learn from data [ 82 , 83 ]. Thus, machine learning models typically comprise of a set of rules, methods, or complex “transfer functions” that can be applied to find interesting data patterns, or to recognize or predict behavior [ 84 ], which could play an important role in the area of cybersecurity. In the following, we discuss different methods that can be used to solve machine learning tasks and how they are related to cybersecurity tasks.
Supervised learning
Supervised learning is performed when specific targets are defined to reach from a certain set of inputs, i.e., task-driven approach. In the area of machine learning, the most popular supervised learning techniques are known as classification and regression methods [ 129 ]. These techniques are popular to classify or predict the future for a particular security problem. For instance, to predict denial-of-service attack (yes, no) or to identify different classes of network attacks such as scanning and spoofing, classification techniques can be used in the cybersecurity domain. ZeroR [ 83 ], OneR [ 130 ], Navies Bayes [ 131 ], Decision Tree [ 132 , 133 ], K-nearest neighbors [ 134 ], support vector machines [ 135 ], adaptive boosting [ 136 ], and logistic regression [ 137 ] are the well-known classification techniques. In addition, recently Sarker et al. have proposed BehavDT [ 133 ], and IntruDtree [ 106 ] classification techniques that are able to effectively build a data-driven predictive model. On the other hand, to predict the continuous or numeric value, e.g., total phishing attacks in a certain period or predicting the network packet parameters, regression techniques are useful. Regression analyses can also be used to detect the root causes of cybercrime and other types of fraud [ 138 ]. Linear regression [ 82 ], support vector regression [ 135 ] are the popular regression techniques. The main difference between classification and regression is that the output variable in the regression is numerical or continuous, while the predicted output for classification is categorical or discrete. Ensemble learning is an extension of supervised learning while mixing different simple models, e.g., Random Forest learning [ 139 ] that generates multiple decision trees to solve a particular security task.
Unsupervised learning
In unsupervised learning problems, the main task is to find patterns, structures, or knowledge in unlabeled data, i.e., data-driven approach [ 140 ]. In the area of cybersecurity, cyber-attacks like malware stays hidden in some ways, include changing their behavior dynamically and autonomously to avoid detection. Clustering techniques, a type of unsupervised learning, can help to uncover the hidden patterns and structures from the datasets, to identify indicators of such sophisticated attacks. Similarly, in identifying anomalies, policy violations, detecting, and eliminating noisy instances in data, clustering techniques can be useful. K-means [ 141 ], K-medoids [ 142 ] are the popular partitioning clustering algorithms, and single linkage [ 143 ] or complete linkage [ 144 ] are the well-known hierarchical clustering algorithms used in various application domains. Moreover, a bottom-up clustering approach proposed by Sarker et al. [ 145 ] can also be used by taking into account the data characteristics.
Besides, feature engineering tasks like optimal feature selection or extraction related to a particular security problem could be useful for further analysis [ 106 ]. Recently, Sarker et al. [ 106 ] have proposed an approach for selecting security features according to their importance score values. Moreover, Principal component analysis, linear discriminant analysis, pearson correlation analysis, or non-negative matrix factorization are the popular dimensionality reduction techniques to solve such issues [ 82 ]. Association rule learning is another example, where machine learning based policy rules can prevent cyber-attacks. In an expert system, the rules are usually manually defined by a knowledge engineer working in collaboration with a domain expert [ 37 , 140 , 146 ]. Association rule learning on the contrary, is the discovery of rules or relationships among a set of available security features or attributes in a given dataset [ 147 ]. To quantify the strength of relationships, correlation analysis can be used [ 138 ]. Many association rule mining algorithms have been proposed in the area of machine learning and data mining literature, such as logic-based [ 148 ], frequent pattern based [ 149 , 150 , 151 ], tree-based [ 152 ], etc. Recently, Sarker et al. [ 153 ] have proposed an association rule learning approach considering non-redundant generation, that can be used to discover a set of useful security policy rules. Moreover, AIS [ 147 ], Apriori [ 149 ], Apriori-TID and Apriori-Hybrid [ 149 ], FP-Tree [ 152 ], and RARM [ 154 ], and Eclat [ 155 ] are the well-known association rule learning algorithms that are capable to solve such problems by generating a set of policy rules in the domain of cybersecurity.
Neural networks and deep learning
Deep learning is a part of machine learning in the area of artificial intelligence, which is a computational model that is inspired by the biological neural networks in the human brain [ 82 ]. Artificial Neural Network (ANN) is frequently used in deep learning and the most popular neural network algorithm is backpropagation [ 82 ]. It performs learning on a multi-layer feed-forward neural network consists of an input layer, one or more hidden layers, and an output layer. The main difference between deep learning and classical machine learning is its performance on the amount of security data increases. Typically deep learning algorithms perform well when the data volumes are large, whereas machine learning algorithms perform comparatively better on small datasets [ 44 ]. In our earlier work, Sarker et al. [ 129 ], we have illustrated the effectiveness of these approaches considering contextual datasets. However, deep learning approaches mimic the human brain mechanism to interpret large amount of data or the complex data such as images, sounds and texts [ 44 , 129 ]. In terms of feature extraction to build models, deep learning reduces the effort of designing a feature extractor for each problem than the classical machine learning techniques. Beside these characteristics, deep learning typically takes a long time to train an algorithm than a machine learning algorithm, however, the test time is exactly the opposite [ 44 ]. Thus, deep learning relies more on high-performance machines with GPUs than classical machine-learning algorithms [ 44 , 156 ]. The most popular deep neural network learning models include multi-layer perceptron (MLP) [ 157 ], convolutional neural network (CNN) [ 158 ], recurrent neural network (RNN) or long-short term memory (LSTM) network [ 121 , 158 ]. In recent days, researchers use these deep learning techniques for different purposes such as detecting network intrusions, malware traffic detection and classification, etc. in the domain of cybersecurity [ 44 , 159 ].
Other learning techniques
Semi-supervised learning can be described as a hybridization of supervised and unsupervised techniques discussed above, as it works on both the labeled and unlabeled data. In the area of cybersecurity, it could be useful, when it requires to label data automatically without human intervention, to improve the performance of cybersecurity models. Reinforcement techniques are another type of machine learning that characterizes an agent by creating its own learning experiences through interacting directly with the environment, i.e., environment-driven approach, where the environment is typically formulated as a Markov decision process and take decision based on a reward function [ 160 ]. Monte Carlo learning, Q-learning, Deep Q Networks, are the most common reinforcement learning algorithms [ 161 ]. For instance, in a recent work [ 126 ], the authors present an approach for detecting botnet traffic or malicious cyber activities using reinforcement learning combining with neural network classifier. In another work [ 128 ], the authors discuss about the application of deep reinforcement learning to intrusion detection for supervised problems, where they received the best results for the Deep Q-Network algorithm. In the context of cybersecurity, genetic algorithms that use fitness, selection, crossover, and mutation for finding optimization, could also be used to solve a similar class of learning problems [ 119 ].
Various types of machine learning techniques discussed above can be useful in the domain of cybersecurity, to build an effective security model. In Table 4 , we have summarized several machine learning techniques that are used to build various types of security models for various purposes. Although these models typically represent a learning-based security model, in this paper, we aim to focus on a comprehensive cybersecurity data science model and relevant issues, in order to build a data-driven intelligent security system. In the next section, we highlight several research issues and potential solutions in the area of cybersecurity data science.
Research issues and future directions
Our study opens several research issues and challenges in the area of cybersecurity data science to extract insight from relevant data towards data-driven intelligent decision making for cybersecurity solutions. In the following, we summarize these challenges ranging from data collection to decision making.
Cybersecurity datasets : Source datasets are the primary component to work in the area of cybersecurity data science. Most of the existing datasets are old and might insufficient in terms of understanding the recent behavioral patterns of various cyber-attacks. Although the data can be transformed into a meaningful understanding level after performing several processing tasks, there is still a lack of understanding of the characteristics of recent attacks and their patterns of happening. Thus, further processing or machine learning algorithms may provide a low accuracy rate for making the target decisions. Therefore, establishing a large number of recent datasets for a particular problem domain like cyber risk prediction or intrusion detection is needed, which could be one of the major challenges in cybersecurity data science.
Handling quality problems in cybersecurity datasets : The cyber datasets might be noisy, incomplete, insignificant, imbalanced, or may contain inconsistency instances related to a particular security incident. Such problems in a data set may affect the quality of the learning process and degrade the performance of the machine learning-based models [ 162 ]. To make a data-driven intelligent decision for cybersecurity solutions, such problems in data is needed to deal effectively before building the cyber models. Therefore, understanding such problems in cyber data and effectively handling such problems using existing algorithms or newly proposed algorithm for a particular problem domain like malware analysis or intrusion detection and prevention is needed, which could be another research issue in cybersecurity data science.
Security policy rule generation : Security policy rules reference security zones and enable a user to allow, restrict, and track traffic on the network based on the corresponding user or user group, and service, or the application. The policy rules including the general and more specific rules are compared against the incoming traffic in sequence during the execution, and the rule that matches the traffic is applied. The policy rules used in most of the cybersecurity systems are static and generated by human expertise or ontology-based [ 163 , 164 ]. Although, association rule learning techniques produce rules from data, however, there is a problem of redundancy generation [ 153 ] that makes the policy rule-set complex. Therefore, understanding such problems in policy rule generation and effectively handling such problems using existing algorithms or newly proposed algorithm for a particular problem domain like access control [ 165 ] is needed, which could be another research issue in cybersecurity data science.
Hybrid learning method : Most commercial products in the cybersecurity domain contain signature-based intrusion detection techniques [ 41 ]. However, missing features or insufficient profiling can cause these techniques to miss unknown attacks. In that case, anomaly-based detection techniques or hybrid technique combining signature-based and anomaly-based can be used to overcome such issues. A hybrid technique combining multiple learning techniques or a combination of deep learning and machine-learning methods can be used to extract the target insight for a particular problem domain like intrusion detection, malware analysis, access control, etc. and make the intelligent decision for corresponding cybersecurity solutions.
Protecting the valuable security information : Another issue of a cyber data attack is the loss of extremely valuable data and information, which could be damaging for an organization. With the use of encryption or highly complex signatures, one can stop others from probing into a dataset. In such cases, cybersecurity data science can be used to build a data-driven impenetrable protocol to protect such security information. To achieve this goal, cyber analysts can develop algorithms by analyzing the history of cyberattacks to detect the most frequently targeted chunks of data. Thus, understanding such data protecting problems and designing corresponding algorithms to effectively handling these problems, could be another research issue in the area of cybersecurity data science.
Context-awareness in cybersecurity : Existing cybersecurity work mainly originates from the relevant cyber data containing several low-level features. When data mining and machine learning techniques are applied to such datasets, a related pattern can be identified that describes it properly. However, a broader contextual information [ 140 , 145 , 166 ] like temporal, spatial, relationship among events or connections, dependency can be used to decide whether there exists a suspicious activity or not. For instance, some approaches may consider individual connections as DoS attacks, while security experts might not treat them as malicious by themselves. Thus, a significant limitation of existing cybersecurity work is the lack of using the contextual information for predicting risks or attacks. Therefore, context-aware adaptive cybersecurity solutions could be another research issue in cybersecurity data science.
Feature engineering in cybersecurity : The efficiency and effectiveness of a machine learning-based security model has always been a major challenge due to the high volume of network data with a large number of traffic features. The large dimensionality of data has been addressed using several techniques such as principal component analysis (PCA) [ 167 ], singular value decomposition (SVD) [ 168 ] etc. In addition to low-level features in the datasets, the contextual relationships between suspicious activities might be relevant. Such contextual data can be stored in an ontology or taxonomy for further processing. Thus how to effectively select the optimal features or extract the significant features considering both the low-level features as well as the contextual features, for effective cybersecurity solutions could be another research issue in cybersecurity data science.
Remarkable security alert generation and prioritizing : In many cases, the cybersecurity system may not be well defined and may cause a substantial number of false alarms that are unexpected in an intelligent system. For instance, an IDS deployed in a real-world network generates around nine million alerts per day [ 169 ]. A network-based intrusion detection system typically looks at the incoming traffic for matching the associated patterns to detect risks, threats or vulnerabilities and generate security alerts. However, to respond to each such alert might not be effective as it consumes relatively huge amounts of time and resources, and consequently may result in a self-inflicted DoS. To overcome this problem, a high-level management is required that correlate the security alerts considering the current context and their logical relationship including their prioritization before reporting them to users, which could be another research issue in cybersecurity data science.
Recency analysis in cybersecurity solutions : Machine learning-based security models typically use a large amount of static data to generate data-driven decisions. Anomaly detection systems rely on constructing such a model considering normal behavior and anomaly, according to their patterns. However, normal behavior in a large and dynamic security system is not well defined and it may change over time, which can be considered as an incremental growing of dataset. The patterns in incremental datasets might be changed in several cases. This often results in a substantial number of false alarms known as false positives. Thus, a recent malicious behavioral pattern is more likely to be interesting and significant than older ones for predicting unknown attacks. Therefore, effectively using the concept of recency analysis [ 170 ] in cybersecurity solutions could be another issue in cybersecurity data science.
The most important work for an intelligent cybersecurity system is to develop an effective framework that supports data-driven decision making. In such a framework, we need to consider advanced data analysis based on machine learning techniques, so that the framework is capable to minimize these issues and to provide automated and intelligent security services. Thus, a well-designed security framework for cybersecurity data and the experimental evaluation is a very important direction and a big challenge as well. In the next section, we suggest and discuss a data-driven cybersecurity framework based on machine learning techniques considering multiple processing layers.
A multi-layered framework for smart cybersecurity services
As discussed earlier, cybersecurity data science is data-focused, applies machine learning methods, attempts to quantify cyber risks, promotes inferential techniques to analyze behavioral patterns, focuses on generating security response alerts, and eventually seeks for optimizing cybersecurity operations. Hence, we briefly discuss a multiple data processing layered framework that potentially can be used to discover security insights from the raw data to build smart cybersecurity systems, e.g., dynamic policy rule-based access control or intrusion detection and prevention system. To make a data-driven intelligent decision in the resultant cybersecurity system, understanding the security problems and the nature of corresponding security data and their vast analysis is needed. For this purpose, our suggested framework not only considers the machine learning techniques to build the security model but also takes into account the incremental learning and dynamism to keep the model up-to-date and corresponding response generation, which could be more effective and intelligent for providing the expected services. Figure 3 shows an overview of the framework, involving several processing layers, from raw security event data to services. In the following, we briefly discuss the working procedure of the framework.
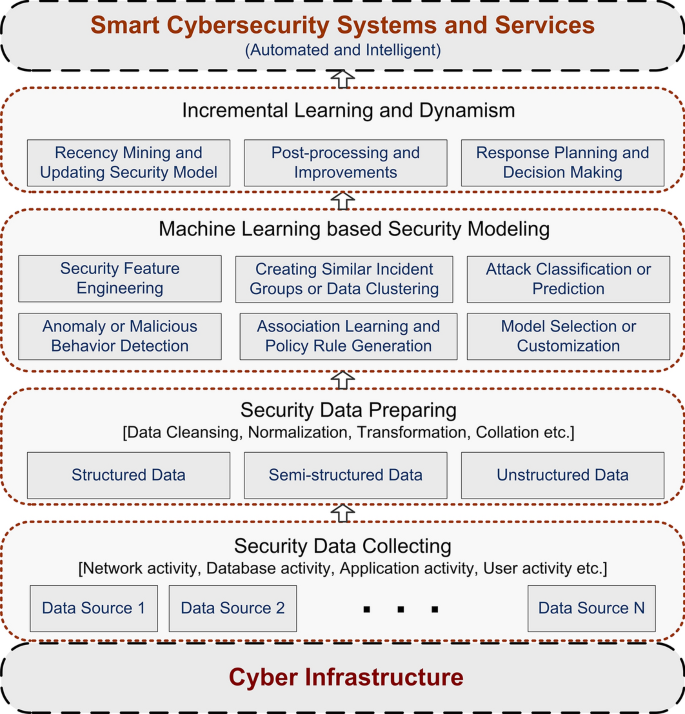
A generic multi-layered framework based on machine learning techniques for smart cybersecurity services
Security data collecting
Collecting valuable cybersecurity data is a crucial step, which forms a connecting link between security problems in cyberinfrastructure and corresponding data-driven solution steps in this framework, shown in Fig. 3 . The reason is that cyber data can serve as the source for setting up ground truth of the security model that affect the model performance. The quality and quantity of cyber data decide the feasibility and effectiveness of solving the security problem according to our goal. Thus, the concern is how to collect valuable and unique needs data for building the data-driven security models.
The general step to collect and manage security data from diverse data sources is based on a particular security problem and project within the enterprise. Data sources can be classified into several broad categories such as network, host, and hybrid [ 171 ]. Within the network infrastructure, the security system can leverage different types of security data such as IDS logs, firewall logs, network traffic data, packet data, and honeypot data, etc. for providing the target security services. For instance, a given IP is considered malicious or not, could be detected by performing data analysis utilizing the data of IP addresses and their cyber activities. In the domain of cybersecurity, the network source mentioned above is considered as the primary security event source to analyze. In the host category, it collects data from an organization’s host machines, where the data sources can be operating system logs, database access logs, web server logs, email logs, application logs, etc. Collecting data from both the network and host machines are considered a hybrid category. Overall, in a data collection layer the network activity, database activity, application activity, and user activity can be the possible security event sources in the context of cybersecurity data science.
Security data preparing
After collecting the raw security data from various sources according to the problem domain discussed above, this layer is responsible to prepare the raw data for building the model by applying various necessary processes. However, not all of the collected data contributes to the model building process in the domain of cybersecurity [ 172 ]. Therefore, the useless data should be removed from the rest of the data captured by the network sniffer. Moreover, data might be noisy, have missing or corrupted values, or have attributes of widely varying types and scales. High quality of data is necessary for achieving higher accuracy in a data-driven model, which is a process of learning a function that maps an input to an output based on example input-output pairs. Thus, it might require a procedure for data cleaning, handling missing or corrupted values. Moreover, security data features or attributes can be in different types, such as continuous, discrete, or symbolic [ 106 ]. Beyond a solid understanding of these types of data and attributes and their permissible operations, its need to preprocess the data and attributes to convert into the target type. Besides, the raw data can be in different types such as structured, semi-structured, or unstructured, etc. Thus, normalization, transformation, or collation can be useful to organize the data in a structured manner. In some cases, natural language processing techniques might be useful depending on data type and characteristics, e.g., textual contents. As both the quality and quantity of data decide the feasibility of solving the security problem, effectively pre-processing and management of data and their representation can play a significant role to build an effective security model for intelligent services.
Machine learning-based security modeling
This is the core step where insights and knowledge are extracted from data through the application of cybersecurity data science. In this section, we particularly focus on machine learning-based modeling as machine learning techniques can significantly change the cybersecurity landscape. The security features or attributes and their patterns in data are of high interest to be discovered and analyzed to extract security insights. To achieve the goal, a deeper understanding of data and machine learning-based analytical models utilizing a large number of cybersecurity data can be effective. Thus, various machine learning tasks can be involved in this model building layer according to the solution perspective. These are - security feature engineering that mainly responsible to transform raw security data into informative features that effectively represent the underlying security problem to the data-driven models. Thus, several data-processing tasks such as feature transformation and normalization, feature selection by taking into account a subset of available security features according to their correlations or importance in modeling, or feature generation and extraction by creating new brand principal components, may be involved in this module according to the security data characteristics. For instance, the chi-squared test, analysis of variance test, correlation coefficient analysis, feature importance, as well as discriminant and principal component analysis, or singular value decomposition, etc. can be used for analyzing the significance of the security features to perform the security feature engineering tasks [ 82 ].
Another significant module is security data clustering that uncovers hidden patterns and structures through huge volumes of security data, to identify where the new threats exist. It typically involves the grouping of security data with similar characteristics, which can be used to solve several cybersecurity problems such as detecting anomalies, policy violations, etc. Malicious behavior or anomaly detection module is typically responsible to identify a deviation to a known behavior, where clustering-based analysis and techniques can also be used to detect malicious behavior or anomaly detection. In the cybersecurity area, attack classification or prediction is treated as one of the most significant modules, which is responsible to build a prediction model to classify attacks or threats and to predict future for a particular security problem. To predict denial-of-service attack or a spam filter separating tasks from other messages, could be the relevant examples. Association learning or policy rule generation module can play a role to build an expert security system that comprises several IF-THEN rules that define attacks. Thus, in a problem of policy rule generation for rule-based access control system, association learning can be used as it discovers the associations or relationships among a set of available security features in a given security dataset. The popular machine learning algorithms in these categories are briefly discussed in “ Machine learning tasks in cybersecurity ” section. The module model selection or customization is responsible to choose whether it uses the existing machine learning model or needed to customize. Analyzing data and building models based on traditional machine learning or deep learning methods, could achieve acceptable results in certain cases in the domain of cybersecurity. However, in terms of effectiveness and efficiency or other performance measurements considering time complexity, generalization capacity, and most importantly the impact of the algorithm on the detection rate of a system, machine learning models are needed to customize for a specific security problem. Moreover, customizing the related techniques and data could improve the performance of the resultant security model and make it better applicable in a cybersecurity domain. The modules discussed above can work separately and combinedly depending on the target security problems.
Incremental learning and dynamism
In our framework, this layer is concerned with finalizing the resultant security model by incorporating additional intelligence according to the needs. This could be possible by further processing in several modules. For instance, the post-processing and improvement module in this layer could play a role to simplify the extracted knowledge according to the particular requirements by incorporating domain-specific knowledge. As the attack classification or prediction models based on machine learning techniques strongly rely on the training data, it can hardly be generalized to other datasets, which could be significant for some applications. To address such kind of limitations, this module is responsible to utilize the domain knowledge in the form of taxonomy or ontology to improve attack correlation in cybersecurity applications.
Another significant module recency mining and updating security model is responsible to keep the security model up-to-date for better performance by extracting the latest data-driven security patterns. The extracted knowledge discussed in the earlier layer is based on a static initial dataset considering the overall patterns in the datasets. However, such knowledge might not be guaranteed higher performance in several cases, because of incremental security data with recent patterns. In many cases, such incremental data may contain different patterns which could conflict with existing knowledge. Thus, the concept of RecencyMiner [ 170 ] on incremental security data and extracting new patterns can be more effective than the existing old patterns. The reason is that recent security patterns and rules are more likely to be significant than older ones for predicting cyber risks or attacks. Rather than processing the whole security data again, recency-based dynamic updating according to the new patterns would be more efficient in terms of processing and outcome. This could make the resultant cybersecurity model intelligent and dynamic. Finally, response planning and decision making module is responsible to make decisions based on the extracted insights and take necessary actions to prevent the system from the cyber-attacks to provide automated and intelligent services. The services might be different depending on particular requirements for a given security problem.
Overall, this framework is a generic description which potentially can be used to discover useful insights from security data, to build smart cybersecurity systems, to address complex security challenges, such as intrusion detection, access control management, detecting anomalies and fraud, or denial of service attacks, etc. in the area of cybersecurity data science.
Although several research efforts have been directed towards cybersecurity solutions, discussed in “ Background ” , “ Cybersecurity data science ”, and “ Machine learning tasks in cybersecurity ” sections in different directions, this paper presents a comprehensive view of cybersecurity data science. For this, we have conducted a literature review to understand cybersecurity data, various defense strategies including intrusion detection techniques, different types of machine learning techniques in cybersecurity tasks. Based on our discussion on existing work, several research issues related to security datasets, data quality problems, policy rule generation, learning methods, data protection, feature engineering, security alert generation, recency analysis etc. are identified that require further research attention in the domain of cybersecurity data science.
The scope of cybersecurity data science is broad. Several data-driven tasks such as intrusion detection and prevention, access control management, security policy generation, anomaly detection, spam filtering, fraud detection and prevention, various types of malware attack detection and defense strategies, etc. can be considered as the scope of cybersecurity data science. Such tasks based categorization could be helpful for security professionals including the researchers and practitioners who are interested in the domain-specific aspects of security systems [ 171 ]. The output of cybersecurity data science can be used in many application areas such as Internet of things (IoT) security [ 173 ], network security [ 174 ], cloud security [ 175 ], mobile and web applications [ 26 ], and other relevant cyber areas. Moreover, intelligent cybersecurity solutions are important for the banking industry, the healthcare sector, or the public sector, where data breaches typically occur [ 36 , 176 ]. Besides, the data-driven security solutions could also be effective in AI-based blockchain technology, where AI works with huge volumes of security event data to extract the useful insights using machine learning techniques, and block-chain as a trusted platform to store such data [ 177 ].
Although in this paper, we discuss cybersecurity data science focusing on examining raw security data to data-driven decision making for intelligent security solutions, it could also be related to big data analytics in terms of data processing and decision making. Big data deals with data sets that are too large or complex having characteristics of high data volume, velocity, and variety. Big data analytics mainly has two parts consisting of data management involving data storage, and analytics [ 178 ]. The analytics typically describe the process of analyzing such datasets to discover patterns, unknown correlations, rules, and other useful insights [ 179 ]. Thus, several advanced data analysis techniques such as AI, data mining, machine learning could play an important role in processing big data by converting big problems to small problems [ 180 ]. To do this, the potential strategies like parallelization, divide-and-conquer, incremental learning, sampling, granular computing, feature or instance selection, can be used to make better decisions, reducing costs, or enabling more efficient processing. In such cases, the concept of cybersecurity data science, particularly machine learning-based modeling could be helpful for process automation and decision making for intelligent security solutions. Moreover, researchers could consider modified algorithms or models for handing big data on parallel computing platforms like Hadoop, Storm, etc. [ 181 ].
Based on the concept of cybersecurity data science discussed in the paper, building a data-driven security model for a particular security problem and relevant empirical evaluation to measure the effectiveness and efficiency of the model, and to asses the usability in the real-world application domain could be a future work.
Motivated by the growing significance of cybersecurity and data science, and machine learning technologies, in this paper, we have discussed how cybersecurity data science applies to data-driven intelligent decision making in smart cybersecurity systems and services. We also have discussed how it can impact security data, both in terms of extracting insight of security incidents and the dataset itself. We aimed to work on cybersecurity data science by discussing the state of the art concerning security incidents data and corresponding security services. We also discussed how machine learning techniques can impact in the domain of cybersecurity, and examine the security challenges that remain. In terms of existing research, much focus has been provided on traditional security solutions, with less available work in machine learning technique based security systems. For each common technique, we have discussed relevant security research. The purpose of this article is to share an overview of the conceptualization, understanding, modeling, and thinking about cybersecurity data science.
We have further identified and discussed various key issues in security analysis to showcase the signpost of future research directions in the domain of cybersecurity data science. Based on the knowledge, we have also provided a generic multi-layered framework of cybersecurity data science model based on machine learning techniques, where the data is being gathered from diverse sources, and the analytics complement the latest data-driven patterns for providing intelligent security services. The framework consists of several main phases - security data collecting, data preparation, machine learning-based security modeling, and incremental learning and dynamism for smart cybersecurity systems and services. We specifically focused on extracting insights from security data, from setting a research design with particular attention to concepts for data-driven intelligent security solutions.
Overall, this paper aimed not only to discuss cybersecurity data science and relevant methods but also to discuss the applicability towards data-driven intelligent decision making in cybersecurity systems and services from machine learning perspectives. Our analysis and discussion can have several implications both for security researchers and practitioners. For researchers, we have highlighted several issues and directions for future research. Other areas for potential research include empirical evaluation of the suggested data-driven model, and comparative analysis with other security systems. For practitioners, the multi-layered machine learning-based model can be used as a reference in designing intelligent cybersecurity systems for organizations. We believe that our study on cybersecurity data science opens a promising path and can be used as a reference guide for both academia and industry for future research and applications in the area of cybersecurity.
Availability of data and materials
Not applicable.
Abbreviations
- Machine learning
Artificial Intelligence
Information and communication technology
Internet of Things
Distributed Denial of Service
Intrusion detection system
Intrusion prevention system
Host-based intrusion detection systems
Network Intrusion Detection Systems
Signature-based intrusion detection system
Anomaly-based intrusion detection system
Li S, Da Xu L, Zhao S. The internet of things: a survey. Inform Syst Front. 2015;17(2):243–59.
Google Scholar
Sun N, Zhang J, Rimba P, Gao S, Zhang LY, Xiang Y. Data-driven cybersecurity incident prediction: a survey. IEEE Commun Surv Tutor. 2018;21(2):1744–72.
McIntosh T, Jang-Jaccard J, Watters P, Susnjak T. The inadequacy of entropy-based ransomware detection. In: International conference on neural information processing. New York: Springer; 2019. p. 181–189
Alazab M, Venkatraman S, Watters P, Alazab M, et al. Zero-day malware detection based on supervised learning algorithms of api call signatures (2010)
Shaw A. Data breach: from notification to prevention using pci dss. Colum Soc Probs. 2009;43:517.
Gupta BB, Tewari A, Jain AK, Agrawal DP. Fighting against phishing attacks: state of the art and future challenges. Neural Comput Appl. 2017;28(12):3629–54.
Av-test institute, germany, https://www.av-test.org/en/statistics/malware/ . Accessed 20 Oct 2019.
Ibm security report, https://www.ibm.com/security/data-breach . Accessed on 20 Oct 2019.
Fischer EA. Cybersecurity issues and challenges: In brief. Congressional Research Service (2014)
Juniper research. https://www.juniperresearch.com/ . Accessed on 20 Oct 2019.
Papastergiou S, Mouratidis H, Kalogeraki E-M. Cyber security incident handling, warning and response system for the european critical information infrastructures (cybersane). In: International Conference on Engineering Applications of Neural Networks, p. 476–487 (2019). New York: Springer
Aftergood S. Cybersecurity: the cold war online. Nature. 2017;547(7661):30.
Hey AJ, Tansley S, Tolle KM, et al. The fourth paradigm: data-intensive scientific discovery. 2009;1:
Cukier K. Data, data everywhere: A special report on managing information, 2010.
Google trends. In: https://trends.google.com/trends/ , 2019.
Anwar S, Mohamad Zain J, Zolkipli MF, Inayat Z, Khan S, Anthony B, Chang V. From intrusion detection to an intrusion response system: fundamentals, requirements, and future directions. Algorithms. 2017;10(2):39.
MATH Google Scholar
Mohammadi S, Mirvaziri H, Ghazizadeh-Ahsaee M, Karimipour H. Cyber intrusion detection by combined feature selection algorithm. J Inform Sec Appl. 2019;44:80–8.
Tapiador JE, Orfila A, Ribagorda A, Ramos B. Key-recovery attacks on kids, a keyed anomaly detection system. IEEE Trans Depend Sec Comput. 2013;12(3):312–25.
Tavallaee M, Stakhanova N, Ghorbani AA. Toward credible evaluation of anomaly-based intrusion-detection methods. IEEE Transactions on Systems, Man, and Cybernetics, Part C (Applications and Reviews) 40(5), 516–524 (2010)
Foroughi F, Luksch P. Data science methodology for cybersecurity projects. arXiv preprint arXiv:1803.04219 , 2018.
Saxe J, Sanders H. Malware data science: Attack detection and attribution, 2018.
Rainie L, Anderson J, Connolly J. Cyber attacks likely to increase. Digital Life in. 2014, vol. 2025.
Fischer EA. Creating a national framework for cybersecurity: an analysis of issues and options. LIBRARY OF CONGRESS WASHINGTON DC CONGRESSIONAL RESEARCH SERVICE, 2005.
Craigen D, Diakun-Thibault N, Purse R. Defining cybersecurity. Technology Innovation. Manag Rev. 2014;4(10):13–21.
Council NR. et al. Toward a safer and more secure cyberspace, 2007.
Jang-Jaccard J, Nepal S. A survey of emerging threats in cybersecurity. J Comput Syst Sci. 2014;80(5):973–93.
MathSciNet MATH Google Scholar
Mukkamala S, Sung A, Abraham A. Cyber security challenges: Designing efficient intrusion detection systems and antivirus tools. Vemuri, V. Rao, Enhancing Computer Security with Smart Technology.(Auerbach, 2006), 125–163, 2005.
Bilge L, Dumitraş T. Before we knew it: an empirical study of zero-day attacks in the real world. In: Proceedings of the 2012 ACM conference on computer and communications security. ACM; 2012. p. 833–44.
Davi L, Dmitrienko A, Sadeghi A-R, Winandy M. Privilege escalation attacks on android. In: International conference on information security. New York: Springer; 2010. p. 346–60.
Jovičić B, Simić D. Common web application attack types and security using asp .net. ComSIS, 2006.
Warkentin M, Willison R. Behavioral and policy issues in information systems security: the insider threat. Eur J Inform Syst. 2009;18(2):101–5.
Kügler D. “man in the middle” attacks on bluetooth. In: International Conference on Financial Cryptography. New York: Springer; 2003, p. 149–61.
Virvilis N, Gritzalis D. The big four-what we did wrong in advanced persistent threat detection. In: 2013 International Conference on Availability, Reliability and Security. IEEE; 2013. p. 248–54.
Boyd SW, Keromytis AD. Sqlrand: Preventing sql injection attacks. In: International conference on applied cryptography and network security. New York: Springer; 2004. p. 292–302.
Sigler K. Crypto-jacking: how cyber-criminals are exploiting the crypto-currency boom. Comput Fraud Sec. 2018;2018(9):12–4.
2019 data breach investigations report, https://enterprise.verizon.com/resources/reports/dbir/ . Accessed 20 Oct 2019.
Khraisat A, Gondal I, Vamplew P, Kamruzzaman J. Survey of intrusion detection systems: techniques, datasets and challenges. Cybersecurity. 2019;2(1):20.
Johnson L. Computer incident response and forensics team management: conducting a successful incident response, 2013.
Brahmi I, Brahmi H, Yahia SB. A multi-agents intrusion detection system using ontology and clustering techniques. In: IFIP international conference on computer science and its applications. New York: Springer; 2015. p. 381–93.
Qu X, Yang L, Guo K, Ma L, Sun M, Ke M, Li M. A survey on the development of self-organizing maps for unsupervised intrusion detection. In: Mobile networks and applications. 2019;1–22.
Liao H-J, Lin C-HR, Lin Y-C, Tung K-Y. Intrusion detection system: a comprehensive review. J Netw Comput Appl. 2013;36(1):16–24.
Alazab A, Hobbs M, Abawajy J, Alazab M. Using feature selection for intrusion detection system. In: 2012 International symposium on communications and information technologies (ISCIT). IEEE; 2012. p. 296–301.
Viegas E, Santin AO, Franca A, Jasinski R, Pedroni VA, Oliveira LS. Towards an energy-efficient anomaly-based intrusion detection engine for embedded systems. IEEE Trans Comput. 2016;66(1):163–77.
Xin Y, Kong L, Liu Z, Chen Y, Li Y, Zhu H, Gao M, Hou H, Wang C. Machine learning and deep learning methods for cybersecurity. IEEE Access. 2018;6:35365–81.
Dutt I, Borah S, Maitra IK, Bhowmik K, Maity A, Das S. Real-time hybrid intrusion detection system using machine learning techniques. 2018, p. 885–94.
Ragsdale DJ, Carver C, Humphries JW, Pooch UW. Adaptation techniques for intrusion detection and intrusion response systems. In: Smc 2000 conference proceedings. 2000 IEEE international conference on systems, man and cybernetics.’cybernetics evolving to systems, humans, organizations, and their complex interactions’(cat. No. 0). IEEE; 2000. vol. 4, p. 2344–2349.
Cao L. Data science: challenges and directions. Commun ACM. 2017;60(8):59–68.
Rizk A, Elragal A. Data science: developing theoretical contributions in information systems via text analytics. J Big Data. 2020;7(1):1–26.
Lippmann RP, Fried DJ, Graf I, Haines JW, Kendall KR, McClung D, Weber D, Webster SE, Wyschogrod D, Cunningham RK, et al. Evaluating intrusion detection systems: The 1998 darpa off-line intrusion detection evaluation. In: Proceedings DARPA information survivability conference and exposition. DISCEX’00. IEEE; 2000. vol. 2, p. 12–26.
Kdd cup 99. http://kdd.ics.uci.edu/databases/kddcup99/kddcup99.html . Accessed 20 Oct 2019.
Tavallaee M, Bagheri E, Lu W, Ghorbani AA. A detailed analysis of the kdd cup 99 data set. In: 2009 IEEE symposium on computational intelligence for security and defense applications. IEEE; 2009. p. 1–6.
Caida ddos attack 2007 dataset. http://www.caida.org/data/ passive/ddos-20070804-dataset.xml/ . Accessed 20 Oct 2019.
Caida anonymized internet traces 2008 dataset. https://www.caida.org/data/passive/passive-2008-dataset . Accessed 20 Oct 2019.
Isot botnet dataset. https://www.uvic.ca/engineering/ece/isot/ datasets/index.php/ . Accessed 20 Oct 2019.
The honeynet project. http://www.honeynet.org/chapters/france/ . Accessed 20 Oct 2019.
Canadian institute of cybersecurity, university of new brunswick, iscx dataset, http://www.unb.ca/cic/datasets/index.html/ . Accessed 20 Oct 2019.
Shiravi A, Shiravi H, Tavallaee M, Ghorbani AA. Toward developing a systematic approach to generate benchmark datasets for intrusion detection. Comput Secur. 2012;31(3):357–74.
The ctu-13 dataset. https://stratosphereips.org/category/datasets-ctu13 . Accessed 20 Oct 2019.
Moustafa N, Slay J. Unsw-nb15: a comprehensive data set for network intrusion detection systems (unsw-nb15 network data set). In: 2015 Military Communications and Information Systems Conference (MilCIS). IEEE; 2015. p. 1–6.
Cse-cic-ids2018 [online]. available: https://www.unb.ca/cic/ datasets/ids-2018.html/ . Accessed 20 Oct 2019.
Cic-ddos2019 [online]. available: https://www.unb.ca/cic/datasets/ddos-2019.html/ . Accessed 28 Mar 2019.
Jing X, Yan Z, Jiang X, Pedrycz W. Network traffic fusion and analysis against ddos flooding attacks with a novel reversible sketch. Inform Fusion. 2019;51:100–13.
Xie M, Hu J, Yu X, Chang E. Evaluating host-based anomaly detection systems: application of the frequency-based algorithms to adfa-ld. In: International conference on network and system security. New York: Springer; 2015. p. 542–49.
Lindauer B, Glasser J, Rosen M, Wallnau KC, ExactData L. Generating test data for insider threat detectors. JoWUA. 2014;5(2):80–94.
Glasser J, Lindauer B. Bridging the gap: A pragmatic approach to generating insider threat data. In: 2013 IEEE Security and Privacy Workshops. IEEE; 2013. p. 98–104.
Enronspam. https://labs-repos.iit.demokritos.gr/skel/i-config/downloads/enron-spam/ . Accessed 20 Oct 2019.
Spamassassin. http://www.spamassassin.org/publiccorpus/ . Accessed 20 Oct 2019.
Lingspam. https://labs-repos.iit.demokritos.gr/skel/i-config/downloads/lingspampublic.tar.gz/ . Accessed 20 Oct 2019.
Alexa top sites. https://aws.amazon.com/alexa-top-sites/ . Accessed 20 Oct 2019.
Bambenek consulting—master feeds. available online: http://osint.bambenekconsulting.com/feeds/ . Accessed 20 Oct 2019.
Dgarchive. https://dgarchive.caad.fkie.fraunhofer.de/site/ . Accessed 20 Oct 2019.
Zago M, Pérez MG, Pérez GM. Umudga: A dataset for profiling algorithmically generated domain names in botnet detection. Data in Brief. 2020;105400.
Zhou Y, Jiang X. Dissecting android malware: characterization and evolution. In: 2012 IEEE Symposium on security and privacy. IEEE; 2012. p. 95–109.
Virusshare. http://virusshare.com/ . Accessed 20 Oct 2019.
Virustotal. https://virustotal.com/ . Accessed 20 Oct 2019.
Comodo. https://www.comodo.com/home/internet-security/updates/vdp/database . Accessed 20 Oct 2019.
Contagio. http://contagiodump.blogspot.com/ . Accessed 20 Oct 2019.
Kumar R, Xiaosong Z, Khan RU, Kumar J, Ahad I. Effective and explainable detection of android malware based on machine learning algorithms. In: Proceedings of the 2018 international conference on computing and artificial intelligence. ACM; 2018. p. 35–40.
Microsoft malware classification (big 2015). arXiv:org/abs/1802.10135/ . Accessed 20 Oct 2019.
Koroniotis N, Moustafa N, Sitnikova E, Turnbull B. Towards the development of realistic botnet dataset in the internet of things for network forensic analytics: bot-iot dataset. Future Gen Comput Syst. 2019;100:779–96.
McIntosh TR, Jang-Jaccard J, Watters PA. Large scale behavioral analysis of ransomware attacks. In: International conference on neural information processing. New York: Springer; 2018. p. 217–29.
Han J, Pei J, Kamber M. Data mining: concepts and techniques, 2011.
Witten IH, Frank E. Data mining: Practical machine learning tools and techniques, 2005.
Dua S, Du X. Data mining and machine learning in cybersecurity, 2016.
Kotpalliwar MV, Wajgi R. Classification of attacks using support vector machine (svm) on kddcup’99 ids database. In: 2015 Fifth international conference on communication systems and network technologies. IEEE; 2015. p. 987–90.
Pervez MS, Farid DM. Feature selection and intrusion classification in nsl-kdd cup 99 dataset employing svms. In: The 8th international conference on software, knowledge, information management and applications (SKIMA 2014). IEEE; 2014. p. 1–6.
Yan M, Liu Z. A new method of transductive svm-based network intrusion detection. In: International conference on computer and computing technologies in agriculture. New York: Springer; 2010. p. 87–95.
Li Y, Xia J, Zhang S, Yan J, Ai X, Dai K. An efficient intrusion detection system based on support vector machines and gradually feature removal method. Expert Syst Appl. 2012;39(1):424–30.
Raman MG, Somu N, Jagarapu S, Manghnani T, Selvam T, Krithivasan K, Sriram VS. An efficient intrusion detection technique based on support vector machine and improved binary gravitational search algorithm. Artificial Intelligence Review. 2019, p. 1–32.
Kokila R, Selvi ST, Govindarajan K. Ddos detection and analysis in sdn-based environment using support vector machine classifier. In: 2014 Sixth international conference on advanced computing (ICoAC). IEEE; 2014. p. 205–10.
Xie M, Hu J, Slay J. Evaluating host-based anomaly detection systems: Application of the one-class svm algorithm to adfa-ld. In: 2014 11th international conference on fuzzy systems and knowledge discovery (FSKD). IEEE; 2014. p. 978–82.
Saxena H, Richariya V. Intrusion detection in kdd99 dataset using svm-pso and feature reduction with information gain. Int J Comput Appl. 2014;98:6.
Chandrasekhar A, Raghuveer K. Confederation of fcm clustering, ann and svm techniques to implement hybrid nids using corrected kdd cup 99 dataset. In: 2014 international conference on communication and signal processing. IEEE; 2014. p. 672–76.
Shapoorifard H, Shamsinejad P. Intrusion detection using a novel hybrid method incorporating an improved knn. Int J Comput Appl. 2017;173(1):5–9.
Vishwakarma S, Sharma V, Tiwari A. An intrusion detection system using knn-aco algorithm. Int J Comput Appl. 2017;171(10):18–23.
Meng W, Li W, Kwok L-F. Design of intelligent knn-based alarm filter using knowledge-based alert verification in intrusion detection. Secur Commun Netw. 2015;8(18):3883–95.
Dada E. A hybridized svm-knn-pdapso approach to intrusion detection system. In: Proc. Fac. Seminar Ser., 2017, p. 14–21.
Sharifi AM, Amirgholipour SK, Pourebrahimi A. Intrusion detection based on joint of k-means and knn. J Converg Inform Technol. 2015;10(5):42.
Lin W-C, Ke S-W, Tsai C-F. Cann: an intrusion detection system based on combining cluster centers and nearest neighbors. Knowl Based Syst. 2015;78:13–21.
Koc L, Mazzuchi TA, Sarkani S. A network intrusion detection system based on a hidden naïve bayes multiclass classifier. Exp Syst Appl. 2012;39(18):13492–500.
Moon D, Im H, Kim I, Park JH. Dtb-ids: an intrusion detection system based on decision tree using behavior analysis for preventing apt attacks. J Supercomput. 2017;73(7):2881–95.
Ingre, B., Yadav, A., Soni, A.K.: Decision tree based intrusion detection system for nsl-kdd dataset. In: International conference on information and communication technology for intelligent systems. New York: Springer; 2017. p. 207–18.
Malik AJ, Khan FA. A hybrid technique using binary particle swarm optimization and decision tree pruning for network intrusion detection. Cluster Comput. 2018;21(1):667–80.
Relan NG, Patil DR. Implementation of network intrusion detection system using variant of decision tree algorithm. In: 2015 international conference on nascent technologies in the engineering field (ICNTE). IEEE; 2015. p. 1–5.
Rai K, Devi MS, Guleria A. Decision tree based algorithm for intrusion detection. Int J Adv Netw Appl. 2016;7(4):2828.
Sarker IH, Abushark YB, Alsolami F, Khan AI. Intrudtree: a machine learning based cyber security intrusion detection model. Symmetry. 2020;12(5):754.
Puthran S, Shah K. Intrusion detection using improved decision tree algorithm with binary and quad split. In: International symposium on security in computing and communication. New York: Springer; 2016. p. 427–438.
Balogun AO, Jimoh RG. Anomaly intrusion detection using an hybrid of decision tree and k-nearest neighbor, 2015.
Azad C, Jha VK. Genetic algorithm to solve the problem of small disjunct in the decision tree based intrusion detection system. Int J Comput Netw Inform Secur. 2015;7(8):56.
Jo S, Sung H, Ahn B. A comparative study on the performance of intrusion detection using decision tree and artificial neural network models. J Korea Soc Dig Indus Inform Manag. 2015;11(4):33–45.
Zhan J, Zulkernine M, Haque A. Random-forests-based network intrusion detection systems. IEEE Trans Syst Man Cybern C. 2008;38(5):649–59.
Tajbakhsh A, Rahmati M, Mirzaei A. Intrusion detection using fuzzy association rules. Appl Soft Comput. 2009;9(2):462–9.
Mitchell R, Chen R. Behavior rule specification-based intrusion detection for safety critical medical cyber physical systems. IEEE Trans Depend Secure Comput. 2014;12(1):16–30.
Alazab M, Venkataraman S, Watters P. Towards understanding malware behaviour by the extraction of api calls. In: 2010 second cybercrime and trustworthy computing Workshop. IEEE; 2010. p. 52–59.
Yuan Y, Kaklamanos G, Hogrefe D. A novel semi-supervised adaboost technique for network anomaly detection. In: Proceedings of the 19th ACM international conference on modeling, analysis and simulation of wireless and mobile systems. ACM; 2016. p. 111–14.
Ariu D, Tronci R, Giacinto G. Hmmpayl: an intrusion detection system based on hidden markov models. Comput Secur. 2011;30(4):221–41.
Årnes A, Valeur F, Vigna G, Kemmerer RA. Using hidden markov models to evaluate the risks of intrusions. In: International workshop on recent advances in intrusion detection. New York: Springer; 2006. p. 145–64.
Hansen JV, Lowry PB, Meservy RD, McDonald DM. Genetic programming for prevention of cyberterrorism through dynamic and evolving intrusion detection. Decis Supp Syst. 2007;43(4):1362–74.
Aslahi-Shahri B, Rahmani R, Chizari M, Maralani A, Eslami M, Golkar MJ, Ebrahimi A. A hybrid method consisting of ga and svm for intrusion detection system. Neural Comput Appl. 2016;27(6):1669–76.
Alrawashdeh K, Purdy C. Toward an online anomaly intrusion detection system based on deep learning. In: 2016 15th IEEE international conference on machine learning and applications (ICMLA). IEEE; 2016. p. 195–200.
Yin C, Zhu Y, Fei J, He X. A deep learning approach for intrusion detection using recurrent neural networks. IEEE Access. 2017;5:21954–61.
Kim J, Kim J, Thu HLT, Kim H. Long short term memory recurrent neural network classifier for intrusion detection. In: 2016 international conference on platform technology and service (PlatCon). IEEE; 2016. p. 1–5.
Almiani M, AbuGhazleh A, Al-Rahayfeh A, Atiewi S, Razaque A. Deep recurrent neural network for iot intrusion detection system. Simulation Modelling Practice and Theory. 2019;102031.
Kolosnjaji B, Zarras A, Webster G, Eckert C. Deep learning for classification of malware system call sequences. In: Australasian joint conference on artificial intelligence. New York: Springer; 2016. p. 137–49.
Wang W, Zhu M, Zeng X, Ye X, Sheng Y. Malware traffic classification using convolutional neural network for representation learning. In: 2017 international conference on information networking (ICOIN). IEEE; 2017. p. 712–17.
Alauthman M, Aslam N, Al-kasassbeh M, Khan S, Al-Qerem A, Choo K-KR. An efficient reinforcement learning-based botnet detection approach. J Netw Comput Appl. 2020;150:102479.
Blanco R, Cilla JJ, Briongos S, Malagón P, Moya JM. Applying cost-sensitive classifiers with reinforcement learning to ids. In: International conference on intelligent data engineering and automated learning. New York: Springer; 2018. p. 531–38.
Lopez-Martin M, Carro B, Sanchez-Esguevillas A. Application of deep reinforcement learning to intrusion detection for supervised problems. Exp Syst Appl. 2020;141:112963.
Sarker IH, Kayes A, Watters P. Effectiveness analysis of machine learning classification models for predicting personalized context-aware smartphone usage. J Big Data. 2019;6(1):1–28.
Holte RC. Very simple classification rules perform well on most commonly used datasets. Mach Learn. 1993;11(1):63–90.
John GH, Langley P. Estimating continuous distributions in bayesian classifiers. In: Proceedings of the eleventh conference on uncertainty in artificial intelligence. Morgan Kaufmann Publishers Inc.; 1995. p. 338–45.
Quinlan JR. C4.5: Programs for machine learning. Machine Learning, 1993.
Sarker IH, Colman A, Han J, Khan AI, Abushark YB, Salah K. Behavdt: a behavioral decision tree learning to build user-centric context-aware predictive model. Mobile Networks and Applications. 2019, p. 1–11.
Aha DW, Kibler D, Albert MK. Instance-based learning algorithms. Mach Learn. 1991;6(1):37–66.
Keerthi SS, Shevade SK, Bhattacharyya C, Murthy KRK. Improvements to platt’s smo algorithm for svm classifier design. Neural Comput. 2001;13(3):637–49.
Freund Y, Schapire RE, et al: Experiments with a new boosting algorithm. In: Icml, vol. 96, p. 148–156 (1996). Citeseer
Le Cessie S, Van Houwelingen JC. Ridge estimators in logistic regression. J Royal Stat Soc C. 1992;41(1):191–201.
Watters PA, McCombie S, Layton R, Pieprzyk J. Characterising and predicting cyber attacks using the cyber attacker model profile (camp). J Money Launder Control. 2012.
Breiman L. Random forests. Mach Learn. 2001;45(1):5–32.
Sarker IH. Context-aware rule learning from smartphone data: survey, challenges and future directions. J Big Data. 2019;6(1):95.
MacQueen J. Some methods for classification and analysis of multivariate observations. In: Fifth Berkeley symposium on mathematical statistics and probability, vol. 1, 1967.
Rokach L. A survey of clustering algorithms. In: Data Mining and Knowledge Discovery Handbook. New York: Springer; 2010. p. 269–98.
Sneath PH. The application of computers to taxonomy. J Gen Microbiol. 1957;17:1.
Sorensen T. method of establishing groups of equal amplitude in plant sociology based on similarity of species. Biol Skr. 1948;5.
Sarker IH, Colman A, Kabir MA, Han J. Individualized time-series segmentation for mining mobile phone user behavior. Comput J. 2018;61(3):349–68.
Kim G, Lee S, Kim S. A novel hybrid intrusion detection method integrating anomaly detection with misuse detection. Exp Syst Appl. 2014;41(4):1690–700.
MathSciNet Google Scholar
Agrawal R, Imieliński T, Swami A. Mining association rules between sets of items in large databases. In: ACM SIGMOD Record. ACM; 1993. vol. 22, p. 207–16.
Flach PA, Lachiche N. Confirmation-guided discovery of first-order rules with tertius. Mach Learn. 2001;42(1–2):61–95.
Agrawal R, Srikant R, et al: Fast algorithms for mining association rules. In: Proc. 20th Int. Conf. Very Large Data Bases, VLDB, 1994, vol. 1215, p. 487–99.
Houtsma M, Swami A. Set-oriented mining for association rules in relational databases. In: Proceedings of the eleventh international conference on data engineering. IEEE; 1995. p. 25–33.
Ma BLWHY. Integrating classification and association rule mining. In: Proceedings of the fourth international conference on knowledge discovery and data mining, 1998.
Han J, Pei J, Yin Y. Mining frequent patterns without candidate generation. In: ACM Sigmod Record. ACM; 2000. vol. 29, p. 1–12.
Sarker IH, Salim FD. Mining user behavioral rules from smartphone data through association analysis. In: Proceedings of the 22nd Pacific-Asia Conference on Knowledge Discovery and Data Mining (PAKDD), Melbourne, Australia. New York: Springer; 2018. p. 450–61.
Das A, Ng W-K, Woon Y-K. Rapid association rule mining. In: Proceedings of the tenth international conference on information and knowledge management. ACM; 2001. p. 474–81.
Zaki MJ. Scalable algorithms for association mining. IEEE Trans Knowl Data Eng. 2000;12(3):372–90.
Coelho IM, Coelho VN, Luz EJS, Ochi LS, Guimarães FG, Rios E. A gpu deep learning metaheuristic based model for time series forecasting. Appl Energy. 2017;201:412–8.
Van Efferen L, Ali-Eldin AM. A multi-layer perceptron approach for flow-based anomaly detection. In: 2017 International symposium on networks, computers and communications (ISNCC). IEEE; 2017. p. 1–6.
Liu H, Lang B, Liu M, Yan H. Cnn and rnn based payload classification methods for attack detection. Knowl Based Syst. 2019;163:332–41.
Berman DS, Buczak AL, Chavis JS, Corbett CL. A survey of deep learning methods for cyber security. Information. 2019;10(4):122.
Bellman R. A markovian decision process. J Math Mech. 1957;1:679–84.
Kaelbling LP, Littman ML, Moore AW. Reinforcement learning: a survey. J Artif Intell Res. 1996;4:237–85.
Sarker IH. A machine learning based robust prediction model for real-life mobile phone data. Internet of Things. 2019;5:180–93.
Kayes ASM, Han J, Colman A. OntCAAC: an ontology-based approach to context-aware access control for software services. Comput J. 2015;58(11):3000–34.
Kayes ASM, Rahayu W, Dillon T. An ontology-based approach to dynamic contextual role for pervasive access control. In: AINA 2018. IEEE Computer Society, 2018.
Colombo P, Ferrari E. Access control technologies for big data management systems: literature review and future trends. Cybersecurity. 2019;2(1):1–13.
Aleroud A, Karabatis G. Contextual information fusion for intrusion detection: a survey and taxonomy. Knowl Inform Syst. 2017;52(3):563–619.
Sarker IH, Abushark YB, Khan AI. Contextpca: Predicting context-aware smartphone apps usage based on machine learning techniques. Symmetry. 2020;12(4):499.
Madsen RE, Hansen LK, Winther O. Singular value decomposition and principal component analysis. Neural Netw. 2004;1:1–5.
Qiao L-B, Zhang B-F, Lai Z-Q, Su J-S. Mining of attack models in ids alerts from network backbone by a two-stage clustering method. In: 2012 IEEE 26th international parallel and distributed processing symposium workshops & Phd Forum. IEEE; 2012. p. 1263–9.
Sarker IH, Colman A, Han J. Recencyminer: mining recency-based personalized behavior from contextual smartphone data. J Big Data. 2019;6(1):49.
Ullah F, Babar MA. Architectural tactics for big data cybersecurity analytics systems: a review. J Syst Softw. 2019;151:81–118.
Zhao S, Leftwich K, Owens M, Magrone F, Schonemann J, Anderson B, Medhi D. I-can-mama: Integrated campus network monitoring and management. In: 2014 IEEE network operations and management symposium (NOMS). IEEE; 2014. p. 1–7.
Abomhara M, et al. Cyber security and the internet of things: vulnerabilities, threats, intruders and attacks. J Cyber Secur Mob. 2015;4(1):65–88.
Helali RGM. Data mining based network intrusion detection system: A survey. In: Novel algorithms and techniques in telecommunications and networking. New York: Springer; 2010. p. 501–505.
Ryoo J, Rizvi S, Aiken W, Kissell J. Cloud security auditing: challenges and emerging approaches. IEEE Secur Priv. 2013;12(6):68–74.
Densham B. Three cyber-security strategies to mitigate the impact of a data breach. Netw Secur. 2015;2015(1):5–8.
Salah K, Rehman MHU, Nizamuddin N, Al-Fuqaha A. Blockchain for ai: review and open research challenges. IEEE Access. 2019;7:10127–49.
Gandomi A, Haider M. Beyond the hype: big data concepts, methods, and analytics. Int J Inform Manag. 2015;35(2):137–44.
Golchha N. Big data-the information revolution. Int J Adv Res. 2015;1(12):791–4.
Hariri RH, Fredericks EM, Bowers KM. Uncertainty in big data analytics: survey, opportunities, and challenges. J Big Data. 2019;6(1):44.
Tsai C-W, Lai C-F, Chao H-C, Vasilakos AV. Big data analytics: a survey. J Big data. 2015;2(1):21.
Download references
Acknowledgements
The authors would like to thank all the reviewers for their rigorous review and comments in several revision rounds. The reviews are detailed and helpful to improve and finalize the manuscript. The authors are highly grateful to them.
Author information
Authors and affiliations.
Swinburne University of Technology, Melbourne, VIC, 3122, Australia
Iqbal H. Sarker
Chittagong University of Engineering and Technology, Chittagong, 4349, Bangladesh
La Trobe University, Melbourne, VIC, 3086, Australia
A. S. M. Kayes, Paul Watters & Alex Ng
University of Nevada, Reno, USA
Shahriar Badsha
Macquarie University, Sydney, NSW, 2109, Australia
Hamed Alqahtani
You can also search for this author in PubMed Google Scholar
Contributions
This article provides not only a discussion on cybersecurity data science and relevant methods but also to discuss the applicability towards data-driven intelligent decision making in cybersecurity systems and services. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Iqbal H. Sarker .
Ethics declarations
Competing interests.
The authors declare that they have no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Sarker, I.H., Kayes, A.S.M., Badsha, S. et al. Cybersecurity data science: an overview from machine learning perspective. J Big Data 7 , 41 (2020). https://doi.org/10.1186/s40537-020-00318-5
Download citation
Received : 26 October 2019
Accepted : 21 June 2020
Published : 01 July 2020
DOI : https://doi.org/10.1186/s40537-020-00318-5
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Decision making
- Cyber-attack
- Security modeling
- Intrusion detection
- Cyber threat intelligence
- In The Press
- Newsletters
- CAMS Events
- Members Login

CAMS Research Framework
Successful cybersecurity leadership covers four critical areas shown in the pillars of our research program framework.
Explore the research projects associated with each area by clicking on that pillar.
Click here to see full diagram with list of projects
- Board’s role in cybersecurity leadership
- Education of Boards and C-levels on cybersecurity
- Structure of cybersecurity workforce
- Prioritizing innovation and cybersecurity together
- Cybersecurity Information and mitigation sharing for competitive advantage
- International trade cybersecurity considerations
- House of Security: assessing cyber maturity
- Building organizational cybersecurity culture
- Bridging the IT/OT culture gap
- Framework for cyber education
- Ethics of cybersecurity
- Cyber safety: research in accident prevention
- Cybersecurity of Industrial Control Systems (ICS)
- Cloud computing cybersecurity
- Cybersecurity of IoT and autonomous vehicles
- Vulnerability research
- Smart cities cybersecurity
Organization
- Cyber insurance and risk mitigation
- Comparing national cybersecurity frameworks
- International cyber information sharing processes
- Creating security without sacrificing usability
- Success factors for cybersecurity companies
CAMS Research Priorities for 2024
Cams research priorities for 2023, cams research priorities for 2022, see previous research framework here, research briefs.
- (IC) 3 Research Framework Overview
- Understanding the Cyber Attack Business
- Cybersecurity Culture Maturity Model
- Managing Risk with Cybersecurity Insurance
- House of Security: Assessing Cybersecurity Readiness
- Cybersecurity Concerns in the Adoption of IoT Technology
- Security Threats to Cyber Physical Systems (CPS)
- Cybersecurity and International Trade
- The Business of the Dark Web
- Building a Culture of Cybersecurity
- Cybersecurity Management in Pharmaceutical and Biotechnology Industries
- Cybersecurity Management in Pharmaceutical and Biotechnology Industries — one page
- Cybersecurity of IoT using Blockchain: Endpoint Security
- Understanding the Risks in the Mobility-as-a-Service Industry
- Balanced Scorecard for Cybersecurity Management
- Zero Trust Networks
- The Cyber Risk Cube
- Cybersecurity of AI Systems
- Fire Drills and Tabletop Exercises
- EarFisher: Detecting Wireless Eavesdroppers
- SolarWinds as a Cybersecurity Game Changer
- The Convergence and Divergence of Regulatory Compliance and Cybersecurity
- Designing Cybersecurity into Digital Offerings
- Simulating Attack Scenarios
- Cybersecurity for Small and Medium Businesses
Posters & Presentations
- Are you Adequately Protecting Against Increasing COVID-19 Cyber Threats? by Michael Coden, BCG and CAMS Research Affiliate, presented to the CAMS Friday Research Meeting March 27, 2020.
- Risk Management During COVID-19 by Ron Ford, DHS, presented to the CAMS Friday Research Meeting, March 27, 2020
- PreventOTPhysDamage: Anticipating and Preventing Catastrophic OT Physical Damage Through System Thinking Analysis b y Shaharyar Khan and Stuart Madnick, presented at CREDC 2020.
- Evaluating Effectiveness of an Embedded System Endpoint Security Technology on EDS: Defeating the Hackers of IIoT Devices : by Matt Maloney, Michael Siegel, Greg Falco, and Elizabeth Reilly. Presented at CREDC 2020.
- Scenario-Based Simulator for Operational Resilience During a Cyber Attack by Keman Huang and Michael Siegel presented at CREDC 2020.
- A Smart IoT Integrity – First Communication Protocol via an Ethereum Blockchain Light Client presented to the 1st International Workshop on Software Engineering Research & Practices for the Internet of Things (SERP4IoT 2019) by Elizabeth Reilly, Matthew Maloney, Michael Siegel, and Gregory Falco, March 27, 2019.
- Status Update: Research Exploring Malware in Energy Delivery Systems (REMEDYS) presented to CREDC by Michael Sapienza and Keri Pearlson, February 15, 2019.
- GDPR Update – presented to Cybersecurity at MIT Sloan Research Team by Emerald de Leeuw, November 16, 2018.
- Cutting Edge Cybersecurity Leadership Research at MIT’s Sloan School – presented to the Society of Information Management (SIM) Boston Summit, October 23, 2018
- Creating a Cybersecurity Culture: (ISC) 2 Survey Responses – presented to The International Information System Security Certification Consortium (ISC) 2 October 8, 2018 by Keri Pearlson.
- Blockchain for Defensive Social Engineering – presented to Society of Information Management (SIM) April 12, 2018 by Greg Falco
- Building a Cybersecurity Culture: A Measurement Model and a Maturity Model – presented to Society of Information Management (SIM) Cybersecurity Special Interest Group February 2018 by Keri Pearlson
- Studying the Tension Between Digital Innovation and Cybersecurity – as presented at the AMCIS conference, August 2017, by Natasha Nelson and Stuart Madnick.
- PreventOTPhysDamage: Anticipating and Preventing Catastrophic OT Physical Damage Through System Thinking Analysis – as presented at the CRED-C conference, March 2017, by Matt Angle, Stuart Madnick, James L. Kirtley, and Nabil Sayfayn.
- The Wolves of Vuln Street: The 1st System Dynamics Model of the 0day Market – as presented at the RSA Conference, April 21, 2015, Moscone Center, by Michael Siegel and Katie Moussouris of HackerOne.
- Cyber Safety: A Systems Thinking and Systems Theory Approach to Managing Cybersecurity Applied to TJX Case – as presented at the International Atomic Energy Agency, Vienna, June 2, 2015, by Qi Van Eikema Hommes, Hamid Salim, Stuart Madnick, and Michael Coden.
- Advancing Cybersecurity Using System Dynamics Simulation Modeling For System Resilience, Patching, and Software Development (download) – as presented September 3, 2014, by Michael Siegel and James Houghton.
- Advancing Cybersecurity Using System Dynamics Simulation Modeling For Analyzing & Disrupting Cybercrime Ecosystem & Vulnerability Markets – as presented September 3, 2014, by Michael Siegel and James Houghton.
- Cyber Safety: A Systems Thinking and Systems Theory Approach to Managing Cybersecurity Applied to TJX Case – as presented by Hamid Salim and Stuart Madnick on September 3, 2014, by Stuart Madnick and Hamid Salim.
- MIT House of Security and Measurement of Security Perceptions in Corporations and Organizations – as presented on September 3, 2014 by Stuart Madnick.
Early Research Papers
- ‘The Cyber Risk Cube: A New Tool for Cybersecurity Risk Management” by Michael Siegel and Kristin Chen. Working Paper. November 2021.
- “Trusting the Needle in the Haystack: Cybersecurity Management of AI/ML Systems” by Sanjana Skukla, José Ignacio Parada, and Keri Pearlson. (Copyright Notice: This manuscript is scheduled for publication at the Future of Information and Communication Conference (FICC) 2022.)
- “The Cybersecurity Skills Survey: Response to the 2020 SIM IT Trends Study” by Chris Maurer, Mary Sumner, Dan Mazzola, Tim Jacks, and Keri Pearlson. June 2021.
- “A Systematic Framework to Understand Transnational Governance for Cybersecurity Risks from Digital Trade” by Keman Huang, Stuart Madnick, Nazli Choucri, and Fang Zhang. June 2021.
- “Convergence and Divergence of Regulatory Compliance and Cybersecurity” by Angelica Marotta and Stuart Madnick. June 2021.
- “Applying the Lessons from the Equifax Cybersecurity Incident to Build a Better Defense” by Ilya Kabanov and Stuart Madnick. June 2021.
- “Cybersafety Approach to Cybersecurity Analysis and Mitigation for Mobility-as-a-Service and Internet of Vehicles” by Chee Wei Lee and Stuart Madnick. May 2021.
- “Cybersecurity Management of AI Systems” by Keri Pearlson, Sanjana Shukla, and Ignacio Parada. May 2021. (White Paper)
- “Cyber Range for Industrial Control Systems (CR-ICS) for Simulating Attack Scenarios” by Shaharyar Khan, Alberto Volpatto, Geet Kalra, Jonathan Esteban, Tommaso Pescanoce, Sabino Caporusso, and Michael Siegel. Presented at the ITASEC conference 2021.
- “Building a Security Propaganda Machine: The Cybersecurity Culture of Verizon Media” by Keri Pearlson (CAMS), Sean Sposito, Masha Arbisman, and Josh Schwartz (Verizon Media), February 15, 2021.
- “Preparing for Cyber Breaches with Fire Drills and Table Top Exercises” by Keri Pearlson, Brett Thorson, Stuart Madnick and Michael Coden. Submitted to Harvard Business Review, February 7, 2021.
- Sneak peek : “From Bolted-On to Baked-In: Designing Cybersecurity into Digital Offerings” (Full Paper) by Dr. Keman Huang and Dr. Keri Pearlson, in progress, January 28, 2021.
- Sneak peek: “A Major Breakdown of International Trade and Next Global Financial Crisis: Could be Caused by Efforts to Prevent Cyberattack on the Web” by Stuart Madnick and Keman Huang, In-progress, 2021.
- Sneak peek: “Development of a Research Plan to Understand the Role of Compliance in Improving or Hindering Cybersecurity in Organizations” by Stuart Madnick and Angelica Marotta, In-progress, 2021.
- “Varieties of Public-Private co-governance on cybersecurity within the digital trade: Implications from Huawei’s 5G ” by Keman Huang, Matthew Deegan, Stuart Madnick, Fang Zhang, and Michael Siegel. 2021.
- “A Culture of Cybersecurity can be Your Competitive Advantage” by Keri Pearlson and Keman Huang (CAMS), December 20, 2020.
- “Does High Cybersecurity Capability Lead to Openness in Digital Trade? The Mediation Effect of of E-Government Maturity” by Keman Huang and Stuart Madnick, November 2020
- “Building Global Digital Supply Chain Hub by Cybersecurity Commitment: Singapore’s Strategic Role in the Digital Age”, by Keman Huang, Stuart Madnick, and Nazli Choucri. Submitted in Global Policy (Online), October 2020.
- “ Cybersecurity Culture at C6 Bank Case Study ” by Keri Pearlson, Madeline Li and Sarah Chou, October 14, 2020 (CAMS Teaching Case Study)
- “Cybersecurity Management of AI/ML Systems” by Keri Pearlson, George Wrenn, and Sanjana Shukla, September 2020.
- “The Impact of Corporate Values and Factors of Internal and External Culture on Formulating the Post-COVID “New Normal” : Implications for Cybersecurity and Information Systems” by Leonardo Castro, Keri Pearlson, Daniel Gozman, and Ganna Pogrebna, September 2020 (CAMS White Paper)
- “Cybersecurity Management of AI Systems: Managing an Attempted Breach at E-Fortress Capital” by Keri Pearlson, George Wrenn, and Sanjana Shukla, June 2020 (Case Study).
- “Inter-sector network and clean energy innovation: Evidence from the wind power sector”, by Fang Zhang, Tian Tang, Jun Su, Keman Huang. Published in the Journal of Cleaner Production, May 2020.
- “CEO’s Cybersecurity Role During COVID19” by Keri Pearlson and George Wrenn, March 20, 2020 (CAMS White Paper)
- “Analyzing the Interplay Between Regulatory Compliance and Cybersecurity” by Angelica Marotta and Stuart Madnick. Presented at the 19th annual Security Conference, Las Vegas (virtual) in March 2020.
- “A Case Study of the Capital One Data Breach” by Nelson Novaes Neto, Stuart Madnick, Anchises Moraes, and Natasha Borges. Presented at the 19th annual Security Conference, Las Vegas (virtual) in March 2020.
- “Cyber Securing Cross Border Financial Services: Calling for a Financial Cybersecurity Action Task Force” by Keman Huang and Stuart Madnick. Presented at the 19th annual Security Conference, Las Vegas (virtual) in March 2020.
- “ Cybersafety Analysis of Industrial Control Systems: Chiller Systems” by Shaharyar Khan and Stuart Madnick. Presented at the 19th annual Security Conference, Las Vegas (virtual) in March 2020.
- “Companies Should Stop Telling Employees to Keep Changing Passwords” by Stuart Madnick for The Wall Street Journal, March 2020.
- “How to Safeguard Against Cyberattacks on Utilities” by Stuart Madnick, published in the Harvard Business Review January 2020
- “Cybersafety: A System- theoretic Approach to Identify Cyber-vulnerabilities & Mitigation Requirements in Industrial Control Systems” by Shaharyar Khan, Stuart Madnick, Member, and IEEE, January 2020.
- “Cyber-Physical System Security Automation through Blockchain Remediation and Execution (SABRE)” by Matthew Maloney, Gregory Falco, and Michael Siegel, January 2020.
- “Responding to a Large Scale Energy Delivery Sector Cyber Attack Teaching Packet” (Case and Teaching Note) by Keri Pearlson, Michael Sapienza and Sarah Chou, December 31, 2019 (Submitted to CREDC as final deliverable for REMEDYS project).
- “Building a Model of Organizational Cyber Security Culture: 2019 Survey Results” by Dr. Keman Huang and Dr. Keri Pearlson, December 2019.
- “ Casting the Dark Web in a New Light ” by Keman Huang, Michael Siegel, and Keri Pearlson. Featured in the MIT Sloan Management Review July 2019 edition.
- “ Analysis of Cross-Border Data Trade Restrictions using Mixture-based Clustering” by Keman Huang, Samuel Chinnery, Stuart Madnick, and Keri Pearlson. Presented at AMCIS August 2019.
- “ Cyber Physical IoT Device Management ” by Matthew Maloney, Elizabeth Reilly, Michael Siegel, and Gregory Falco. July 2019.
- “ The Internet of Things Promises New Benefits and Risks ” by Mohammad S. Jalali, Jessica P. Kaiser, Michael Siegel, and Stuart Madnick. April 2019.
- “ A Culture of Cybersecurity at Banca Popolare di Sondrio ” by Angelica Marotta and Dr. Keri Pearlson. March 01, 2019.
- “ Identification and Mitigation of Cyber Vulnerabilities in Industrial Control Systems using a System Theoretic Design Approach ” by Shaharyar Khan. January 2019.
- “Responding to a Large Scale Energy Sector Cyber Attack Case Study” by Keri Pearlson, Michael Sapienza and Sarah Chou, December 31, 2019 (Teaching note available upon request).
- “Research Plan to Analyze the Role of Compliance in Influencing Cybersecurity in Organizations” by Stuart Madnick, Angelica Marotta, Nelson Novaes, and Kevin Powers. December 2019.
- “Framework for Understanding Cybersecurity Impacts on Digital Trade” by Keman Huang, Stuart Madnick, and Simon Johnson. December 2019.
- “ Building a Model of Cybersecurity Culture: Survey Results ” by Keman Huang and Keri Pearlson, December 20, 2019.
- “ Blockchain Isn’t as Unbreakable as You Think ” by Stuart Madnick. Published in Sloan Management Review, November 2019.
- “Casting the Dark Web In a New Light” by Keman Huang, Michael Siegel, Keri Pearlson and Stuart Madnick. Published in Sloan Management Review, July 2019.
- “Identifying and Anticipating Cyber Attacks that Could Cause Physical Damage to Industrial Control Systems” by Matthew G. Angle, Stuart Madnick, James L. Kirtley Jr., and Shaharyar Khan. June 2019.
- “Health Care and Cybersecurity: Bibliometric Analysis of the Literature” by Mohammad S. Jalali, Sabina Razak, William Gordon, Eric Perakslis, and Stuart Madnick. February 15, 2019.
- “The Internet of (Wonderful and Scary) Things” by Mohammad Jalali. January 2019.
- “For What Technology Can’t Fix: Building a Model of Organizational Cybersecurity Culture” by Keman Huang and Keri Pearlson. January 2019.
- “Enhancing Cybersecurity Education through High Fidelity Live Exercises (HiFLiX)” by Johan Sigholm, Gregory Falco, and Arun Viswanathan. September 2018.
- “ For What Technology Can’t Fix: Building a Model of Organizational Cybersecurity Culture ” by Keman Huang and Keri Pearlson. 2018.
- “ Cyber negotiation: a cyber risk management approach to defend urban critical infrastructure from cyberattacks ” by Gregory Falco, Alicia Norieha, and Lawrence Susskind published in Journal of Cyber Policy . December 17, 2018.
- “ Systematically Understanding the Cyber Attack Business: A Survey ” by Keman Huang, Michael Siegel, and Stuart Madnick. July 2018.
- “ Cyber Insurance as a Risk Mitigation Strategy ” by Michael Siegel, Nadya Bartol, Juan Jose Carrascosa Pulido, Stuart Madnick, Michael Coden, Mohammad Jalali, and Michael Bernaski. April 2018. A brief accompanying this report is also available here.
- “ A Framework for Systematically Understanding the Cyber Attack Business ” by Keman Huang, Michael Siegel, and Stuart Madnick. January 24, 2018.
- “ Profiling the Organizational Cybersecurity Culture: Toward a Cybersecurity Culture Framework ” by Keman Huang and Keri Pearlson. January 2018.
- “Cyber Resiliency in Hospitals: a Systematic, Organizational Perspective” by Mohammad S. Jalali and Jessica Paige Kaiser. January 2018.
- “Measuring Stakeholders’ Perceptions of Cybersecurity for Renewable Energy Systems” by Stuart Madnick, Mohammad S. Jalali, Michael Siegel, Yang Lee, Diane Strong, Richard Wang, Wee Horng Ang, Vicki Deng, and Dinsha Mistree. In book: Lecture Notes in Artificial Intelligence 10097, 2017, 67–77.
- “Trust and Collaboration to Enhance Cybersecurity” by Keman Huang, Keri Pearlson, and Stuart Madnick. December 14, 2017.
- “Decision Making and Biases in Cybersecurity Capability Development: Evidence from a Simulation Game Experiment” by Mohammad S. Jalali, Michael Siegel, and Stuart Madnick. December 2017.
- “The Internet of Things (IoT) Promises New Benefits — and Risks: A Systematic Analysis of Adoption Dynamics of IoT Products” by Mohammad S. Jalali, Jessica Paige Kaiser, Michael Siegel, and Stuart Madnick. November 2017.
- “Cybercrime-as-a-Service: Identifying Control Points to Disrupt” by Keman Huang, Michael Siegel, and Stuart Madnick. November 2017.
- “Beyond Keywords: Tracking the evolution of conversational clusters in social media” by James P. Houghton, Michael Siegel, Stuart Madnick, Nobuaki Tounaka, Kazutaka Nakamura, Takaaki Sugiyama, Daisuke Nakagawa, and Buyanjargal Shirnen. October 2017.
- “Decision Making and Biases in Cybersecurity Capability Development: Evidence from a Simulation Game Experiment” by Mohammad S. Jalali, Michael Siegel, and Stuart Madnick. August 2017.
- “The Internet of Things (IoT) Promises New Benefits — And Risks: A Systematic Analysis of Adoption Dynamics of IoT Products” by Mohammad S. Jalali, Jessica Paige Kaiser, Michael Siegel, and Stuart Madnick. August 2017.
- “Identifying and Mitigating Cyber Attacks that could cause Physical Damage to Industrial Control Systems” by Matthew G. Angle, Stuart Madnick, and James L. Kirtley, Jr. August 2017.
- “Cybersecurity Information Sharing Incentives and Barriers” by Priscilla Koepke. June 2017.
- “Striking a balance between usability and cyber-security in IoT devices” by Saurabh Dutta. May 2017.
- “Cyber Warfare Conflict Analysis and Case Studies” by Mohan B. Gazula. May 2017.
- “Cybersafety Analysis of the Maroochy Shire Sewage Spill” by Nabil Sayfayn and Stuart Madnick. May 2017.
- “Preparing for the Cyberattack That Will Knock Out U.S. Power Grids” by Stuart Madnick. May 2017.
- “Institutions for Cyber Security: International Responses and Data Sharing Initiatives” by Nazli Choucri, Stuart Madnick, and Priscilla Koepke. April 2017.
- “Studying the Tension Between Digital Innovation and Cybersecurity” by Natasha Nelson and Stuart Madnick. April 2017.
- “Trade-offs between digital innovation and cyber-security” (31 pages) by Natasha Nelson and Stuart Madnick. March 2017.
- “Diversity or Concentration? Hackers’ Strategy for Working Across Multiple Bug Bounty Programs” by Keman Huang, Michael Siegel, Stuart Madnick, Xiaohong Li, and Zhiyong Feng. December 2016.
- “Ukraine Power Grid Cyberattack and US Susceptibility: Cybersecurity Implications of Smart Grid Advancements in the US” by Abir Shehod. December 2016.
- “Analysis of the Digital Direct-to-Customer channel in Insurance” by Nithila Jeyakumar. December 2016.
- “Institutions for Cyber Security: International Responses and Data Sharing Initiatives” by Nazli Choucri, Stuart Madnick, and Priscilla Koepke. August 2016.
- “Cyber Safety: A Systems Theory Approach to Managing Cyber Security Risks – Applied to TJX Cyber Attack” by Hamid Salim and Stuart Madnick. August 2016.
- “Measuring Stakeholders’ Perceptions of Cybersecurity for Renewable Energy Systems” by Stuart Madnick, Mohammad S. Jalali, Michael Siegel, Yang Lee, Diane Strong, Richard Wang, Wee Horng Ang, Vicki Deng, and Dinsha Mistree. August 2016.
- “A Systems Theoretic Approach to the Security Threats in Cyber Physical Systems: Applied to Stuxnet” by Arash Nourian and Stuart Madnick. September 2014.
- “Cyber Safety: A Systems Thinking and Systems Theory Approach to Managing Cyber Security Risks” (Condensed 37 page version) by Hamid Salim and Stuart Madnick. September 2014.
- “Cyber Safety: A Systems Thinking and Systems Theory Approach to Managing Cyber Security Risks” (Full 157 page version) by Hamid Salim. May 2014.
- “Institutional Foundations for Cyber Security: Current Responses and New Challenges” (JITD) by Nazli Choucri, Stuart Madnick, and Jeremy Ferwerda. October 2013.
- “Inter-Organizational Information Sharing of Customer Data in Retail” by John Tengberg. May 2013.
- “Issues in Strategic Management of Large-Scale Software Product Line Development” by Jean-Baptiste Henri Nivoit. May 2013.
- “Challenges in Implementing Enterprise Resource Planning (ERP) system in Large Organizations: Similarities and Differences Between Corporate and University Environment” by Goeun Seo. May 2013.
- “Using System Dynamics to Analyze the Effect of Funding Fluctuation on Software Development” (ASEM) by Travis Trammell, Stuart Madnick, and Allen Moulton. March 2013.
- “Agile Project Dynamics: A System Dynamics Investigation of Agile Software Development Methods” (SD Conference) by Firas Glaiel, Allen Moulton, and Stuart Madnick. March 2013.
- “Towards better understanding Cybersecurity: or are “Cyberspace” and “Cyber Space” the same?” (WISP) by Stuart Madnick, Nazli Choucri, Steven Camiña, and Wei Lee Woon. November 2012.
- “Strategic Philanthropy for Cyber Security: An extended cost-benefit analysis framework to study cybersecurity” by Yiseul Cho. June 2012.
- “Comparative Analysis of Cybersecurity Metrics to Develop New Hypotheses” (WISP) by Stuart Madnick, Nazli Choucri, Xitong Li, and Jeremy Ferwerda. November 2011.
- “Institutional Foundations for Cyber Security: Current Responses and New Challenges” (revised) by Jeremy Ferwerda, Nazli Choucri, and Stuart Madnick. September 2011.
- “Exploring Terms and Taxonomies Relating to the Cyber International Relations Research Field: or are “Cyberspace” and “Cyber Space” the same?” by Steven Camiña, Stuart Madnick, Nazli Choucri, and Wei Lee Woon. August 2011.
- “Experiences and Challenges with using CERT Data to Analyze International Cyber Security” (AIS/WISP) by Stuart Madnick, Xitong Li, and Nazli Choucri. September 2009.
- “Explorations in Cyber International Relations (ECIR) – Data Dashboard Report #1: CERT Data Sources and Prototype Dashboard System” Stuart Madnick, Nazli Choucri, Steven Camiña, Erik Fogg, Xitong Li, and Fan Wei. August 2009.
- “Institutional Foundations for Cyber Security: Current Responses and New Challenges” by Jeremy Ferwerda, Nazli Choucri, and Stuart Madnick. September 2010.
- “A Systems Approach to Risk Management” (ASEM) by Nathan A. Minami, Stuart Madnick, and Donna Rhodes. November 2008.
- “An Economic Analysis of Policies for the Protection and Reuse of Non-Copyrightable Database Contents” (JMIS) by Hongwei Zhu, Stuart Madnick, and Michael Siegel. February 2008.
- “Preventing Accidents and Building a Culture of Safety: Insights from a Simulation Model” by John Lyneis and Stuart Madnick. February 2008.
- “Enhancing Vehicle Safety Management in Training Deployments: An Application of System Dynamics” by Kelvin F. H. Lim. February 2008.
- “The House of Security: Stakeholder Perceptions of Security Assessment and Importance” (FSTC) by Wee Horng Ang, Vicki Deng, Yang Lee, Stuart Madnick, Dinsha Mistree, Michael Siegel, Diane Strong, and Richard Wang. July 2007.
- “Using System Dynamics to Model and Better Understand State Stability” (SD) by Nazli Choucri, Daniel Goldsmith, Stuart E. Madnick, Dinsha Mistree, J. Bradley Morrison, and Michael D. Siegel. July 2007.
- “House of Security: Locale, Roles and Resources for Ensuring Information Security” (AMCIS) by Wee Horng Ang, Yang W. Lee, Stuart E. Madnick, Dinsha Mistress, Michael Siegel, Diane M. Strong, Richard Y. Wang, and Chrisy Yao. August 2006.
- “Improving National and Homeland Security through Context Knowledge Representation & Reasoning Technologies” (Book chapter) by Nazli Choucri, Stuart E. Madnick, and Michael D. Siegel. April 2006.
- “Understanding & Modeling State Stability: Exploiting System Dynamics” (IEEE Aerospace) by Nazli Choucri, Christi Electris, Daniel Goldsmith, Dinsha Mistree, Stuart E. Madnick, J. Bradley Morrison, Michael D. Siegel, and Margaret Sweitzer-Hamilton. January 2006.
- “Understanding & Modeling State Stability: Exploiting System Dynamics” (PCAS Final Report with Appendices) by Nazli Choucri, Christi Electris, Daniel Goldsmith, Dinsha Mistree, Stuart E. Madnick, J. Bradley Morrison, Michael D. Siegel, and Margaret Sweitzer-Hamilton. December 2005.
- “Policy for the Protection and Reuse of Non-Copyrightable Database Contents” by Hongwei Zhu, Stuart Madnick, and Michael Siegel. November 2005.
- “To Standardize Enterprise Data or Not? An Economic Analysis of Flexibility versus Control” by Chander K. Velu, Stuart E. Madnick, and Marshall W. Van Alstyne. November 2005.
- “Context Mediation Demonstration of Counter-Terrorism Intelligence (CTI) Integration” by Stuart E. Madnick, Allen Moulton, and Michael D. Siegel. May 2005.
- “Research Initiative to Understand & Model State Stability: Exploiting System Dynamics” (SD) by Nazli Choucri, Stuart E. Madnick, and Michael D. Siegel. February 2005.
- “Linkage Between Pre- and Post- Conflict: Exploiting Information Integration & System Dynamics” (IEEE Aerospace) by Nazli Choucri, Stuart E. Madnick, Allen Moulton, Michael D. Siegel, and Hongwei Zhu. January 2005.
- “Improving National and Homeland Security through a proposed Laboratory for Information Globalization and Harmonization Technologies” (LIGHT) by Nazli Choucri, Stuart Madnick, Michael Siegel, and Richard Wang. February 2004.
- “Global e-Readiness – For What? Readiness for e-Banking” (Journal of IT Development) by V. Maugis, N. Choucri, S. Madnick, M. Siegel, S. Gillett, F. Haghseta, H. Zhu, and M. Best. April 2004.
- “Improving UccNet-Compliant B2B Supply-Chain Applications Using a Context Interchange Framework” (BAI2004) by Steven Yi-Cheng Tu, Stuart Madnick, and Luis Chin-Jung Wu. February 2004.
- “Information Integration for Counter Terrorism Activities: The Requirement for Context Mediation” (IEEE Aerospace) by Nazli Choucri, Stuart E. Madnick, Allen Moulton, Michael D. Siegel, and Hongwei Zhu. November 2003.
- “LIGHTS: Laboratory for Information Globalization and Harmonization Technologies and Studies” by Nazli Choucri, Stuart Madnick, Michael Siegel, and Richard Wang. February 2003.
- “Attribution Principles for Data Integration: Technology and Policy Perspectives – Part 2: Focus on Policy” by Thomas Lee. February 2002.
- “Attribution Principles for Data Integration: Technology and Policy Perspectives – Part 1: Focus on Technology” by Thomas Lee. February 2002.
- “Why Not One Big Database? Principles for Data Ownership” (DSS) by Marshall Van Alstyne, Erik Brynjolfsson, and Stuart Madnick.
Why Join Cybersecurity at MIT Sloan?
Benefit from usable research! Cybersecurity at MIT Sloan (CAMS), formerly (IC) 3 , is focusing MIT’s uniquely qualified interdisciplinary faculty and researchers on the fundamental principles of cyberspace, cybercrime, & cybersecurity applied to critical infrastructure. Cybersecurity at MIT Sloan is a confidential academic forum in which leaders and managers can benefit from the experiences of CSO/CISOs across multiple sectors.

Cybersecurity at MIT Sloan
Professor Stuart Madnick, Director, [email protected] Dr. Michael Siegel, Director, [email protected] Dr. Keri Pearlson, Executive Director, [email protected]
© Copyright 2023
Cybersecurity at MIT Sloan (CAMS) Privacy Statement
Securing software, hardware, systems, and the safety and privacy of those who access them, relies on an integrated network of technological, legal, and social approaches. Research initiatives at the Center for Cybersecurity reflect this diversity of topics and approaches, as well as the application of the interdisciplinary expertise required to implement effective security solutions.
Below are very broad descriptions of the primary research categories in which CCS faculty and students are proving to be defensive game-changers.
You can stay abreast of all the CCS research initiatives making headlines by checking the postings under Press Highlights and CCS News .
SPECIALIZATIONS
Artificial intelligence is playing an increasingly critical role in the field of cybersecurity, both as a tool that can be leveraged as a threat, or as a solution to that threat. At the Center for Cybersecurity, researchers are working to better understand the former, through initiatives like a recent study showing the potential vulnerabilities in AI generated code, while expanding its use for the latter through projects that include producing simulated bugs to improve detection and testing methods. (See related research projects under Disinformation and Deepfakes, Privacy and Data Protection, Supply Chain Security)
Find out more
According to the FBI’s 2021 Internet crime report , more than $6.9 billion was lost in the United States to cybercrime activities in 2021. These attacks can range from the use of cyber technology for illegal surveillance and online harassment, to the manipulation of access to in-demand items through dark web marketplaces. Research initiatives from the Center for Cybersecurity have addressed strategies for mapping and disrupting cybercrime networks, and designed legal and policy interventions that can deter criminal networks from raising, storing, moving, and using funds.
When it comes to cybersecurity, who is responsible for developing and enforcing policies to adequately address current and future risk? Our work on cyber governance aims to identify the appropriate roles and obligations of various stakeholders—including private companies and government agencies. This includes issues of technical capacity, the regulatory environment, and commercial incentives. CCS research in Cyber Strategy works to sharpen the boundaries between cybersecurity and intelligence authorities, the ways in which cyber capabilities are integrated into larger strategic structures, and the development of international laws and norms.
Disinformation can take several forms, be it a digitally manipulated photograph or an anonymous ad campaign spreading false information. Faculty and students of the Center for Cybersecurity are working on several fronts to maintain image integrity, and to craft legal and regulatory responses to disinformation. Through its affiliated project, Cybersecurity for Democracy, CCS is also conducting research and disseminating information about “the online threats to our social fabric,” as well as developing strategies to counter them.
The Internet-of-Things (IoT) is primarily associated with “smart home” devices like Alexa. But, IoT technologies are also integral parts of industrial systems, and even provide software updates to the electronic control units on automobiles. Despite the growing number of IoT applications, these devices often run insecure software and engage in obscure privacy practices, such as sending data to unknown third parties. The Center for Cybersecurity is currently analyzing the security and privacy threats from real-world IoT devices from all over the world through the IoT Inspector project. Data gathered using this tool is shared with consumers to educate them about the risks, and with other researchers who can use the information to mitigate these threats. Other CCS research teams have introduced practical strategies to protect software updates for automotive electronic control units and other systems that rely on software over the air update strategies. This research goes hand in hand with other areas of CCS, including Privacy and Data Protection, Securing Cyberphysical Systems, and Supply Chain Security.
Computing technology has become an intrinsic part of manufacturing operations across all industrial sectors. And, as promising new technologies, such as digital manufacturing, have emerged, threats to their security have not been far behind. At the Center for Cybersecurity, an interdisciplinary team of researchers is tackling these threats on several fronts. In addition to conducting research in this expanding arena, CCS has sponsored or co-sponsored a series of panel discussions and workshops, Researchers at CCS also investigate solutions for other hardware security issues, such as improving the secure properties of encrypted microchips, and the detection of hardware Trojans.
Data and privacy security tools and strategies have become critical to businesses and government agencies as well as to individuals. CCS is expanding these technologies on a number of fronts, including harnessing emerging technologies like homomorphic encryption. The Center has also identified emerging targets, such as current and future IT/communication systems, IoT devices, and social media. Lastly, CCS researchers are also investigating how data mining can be used to infringe on our privacy, and how systems and laws can be redesigned to limit these intrusions.
Cyberphysical systems are mechanical systems monitored and controlled by computers. Attacks aimed at cyberphysical systems can have catastrophic effects on electric power generation and delivery, traffic flow management, public health, national economic security, and more. Our work focuses on enhancing the security of these systems, including emerging technologies like 5G.
Securing systems and the software that powers them requires a multitude of approaches. Current research initiatives at CCS address compromise resilience, virtualization security, design and implementation of distributed content networks, memory forensics, embedded systems, security and human behavior, and the delivery of secure updates to repositories, automobiles, and smart devices. A common thread among all these initiatives is that they are based on deployments in real world systems.
In the computer science field, security has generally been piecemeal in nature, rather than a holistic operation that can guarantee the security of a project from end to end. Faculty and students at the Center for Cybersecurity have been actively engaged in changing this perspective by developing and implementing both software and hardware supply chain defenses. These strategies include identifying flaws in microchips, ensuring consistency and quality control in digitally-manufactured products, adding transparency and accountability to each step in the software supply chain, and utilizing financial incentives as a defensive strategy.

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
https://www.nist.gov/cybersecurity

Cybersecurity
NIST develops cybersecurity standards, guidelines, best practices, and other resources to meet the needs of U.S. industry, federal agencies and the broader public. Our activities range from producing specific information that organizations can put into practice immediately to longer-term research that anticipates advances in technologies and future challenges.
Some NIST cybersecurity assignments are defined by federal statutes, executive orders and policies. For example, the Office of Management and Budget (OMB) mandates that all federal agencies implement NIST’s cybersecurity standards and guidance for non-national security systems. Our cybersecurity activities also are driven by the needs of U.S. industry and the broader public. We engage vigorously with stakeholders to set priorities and ensure that our resources address the key issues that they face.
NIST also advances understanding and improves the management of privacy risks, some of which relate directly to cybersecurity.
Priority areas to which NIST contributes – and plans to focus more on – include cryptography, education and workforce, emerging technologies, risk management , identity and access management, measurements, privacy, trustworthy networks and trustworthy platforms.
Additional details can be found in these brief and more detailed fact sheets.
Featured Content
Cybersecurity topics.
- Cryptography
- Cybersecurity education and workforce development
- Cybersecurity measurement
- Identity & access management
- Privacy engineering
- Risk Management
- Securing emerging technologies
- Trustworthy networks
- Trustworthy platforms
The Research
Projects & programs.

Exposure Notification – protecting workplaces and vulnerable communities during a pandemic

Trustworthy Networks of Things
Cryptographic module validation program (cmvp).

Cyber-Physical Systems/Internet of Things for Smart Cities
Additional resources links.

NIST Drafts Major Update to Its Widely Used Cybersecurity Framework

NIST Awards Over $1.2 Million to Small Businesses to Advance Cybersecurity, Biopharmaceuticals, Semiconductors and More

NIST Finalizes Updated Guidelines for Protecting Sensitive Information

NIST hosts meeting of O-RAN Alliance security experts
Cybersecurity Insights Blog
Latest nice framework update offers improvements for the cybersecurity workforce, protecting model updates in privacy-preserving federated learning: part two, take a tour nist cybersecurity framework 2.0: small business quick start guide, giving nist digital identity guidelines a boost: supplement for incorporating syncable authenticators, nice webinar: empowering refugee communities in cybersecurity roles, 2024 iris experts group (ieg) meeting, nist workshop on the requirements for an accordion cipher mode 2024, stay in touch.
Sign up for our newsletter to stay up to date with the latest research, trends, and news for Cybersecurity.
For enquiries call:
+1-469-442-0620

60+ Latest Cyber Security Research Topics in 2024
Home Blog Security 60+ Latest Cyber Security Research Topics in 2024
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cybersecurity thesis topics helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The network can be attacked in various ways, including Distributed DoS, Knowledge Disruptions, Computer Viruses / Worms, and many more. Cyber-attacks are still rising, and more are waiting to harm their targeted systems and networks. Detecting Intrusions in cybersecurity has become challenging due to their Intelligence Performance. Therefore, it may negatively affect data integrity, privacy, availability, and security.
This article aims to demonstrate the most current Cyber Security Topics for Projects and areas of research currently lacking. We will talk about cyber security research questions, cyber security topics for the project, latest research titles about cyber security.
.jpg&w=3840&q=75)

List of Trending Cyber Security Research Topics in 2024
Digital technology has revolutionized how all businesses, large or small, work, and even governments manage their day-to-day activities, requiring organizations, corporations, and government agencies to utilize computerized systems. To protect data against online attacks or unauthorized access, cybersecurity is a priority. There are many Cyber Security Courses online where you can learn about these topics. With the rapid development of technology comes an equally rapid shift in Cyber Security Research Topics and cybersecurity trends, as data breaches, ransomware, and hacks become almost routine news items. In 2024, these will be the top cybersecurity trends.
A. Exciting Mobile Cyber Security Research Paper Topics
- The significance of continuous user authentication on mobile gadgets.
- The efficacy of different mobile security approaches.
- Detecting mobile phone hacking.
- Assessing the threat of using portable devices to access banking services.
- Cybersecurity and mobile applications.
- The vulnerabilities in wireless mobile data exchange.
- The rise of mobile malware.
- The evolution of Android malware.
- How to know you’ve been hacked on mobile.
- The impact of mobile gadgets on cybersecurity.
B. Top Computer and Software Security Topics to Research
- Learn algorithms for data encryption
- Concept of risk management security
- How to develop the best Internet security software
- What are Encrypting Viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC
- Infiltrating a Mac OS X operating system
- What are the effects of RSA on network security ?
- How do encrypting viruses work?
- DDoS attacks on IoT devices
C. Trending Information Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2024
- Discuss digital piracy in 2024
- critical cyber-attack concepts
- Social engineering and its importance
D. Current Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Firewall
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
E. Best Data Security Research Topics
- Importance of backup and recovery
- Benefits of logging for applications
- Understand physical data security
- Importance of Cloud Security
- In computing, the relationship between privacy and data security
- Talk about data leaks in mobile apps
- Discuss the effects of a black hole on a network system.
F. Important Application Security Research Topics
- Detect Malicious Activity on Google Play Apps
- Dangers of XSS attacks on apps
- Discuss SQL injection attacks.
- Insecure Deserialization Effect
- Check Security protocols
G. Cybersecurity Law & Ethics Research Topics
- Strict cybersecurity laws in China
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries' cybersecurity laws
- Discuss The Pipeline Security Act in the United States
H. Recent Cyberbullying Topics
- Protecting your Online Identity and Reputation
- Online Safety
- Sexual Harassment and Sexual Bullying
- Dealing with Bullying
- Stress Center for Teens
I. Operational Security Topics
- Identify sensitive data
- Identify possible threats
- Analyze security threats and vulnerabilities
- Appraise the threat level and vulnerability risk
- Devise a plan to mitigate the threats
J. Cybercrime Topics for a Research Paper
- Crime Prevention.
- Criminal Specialization.
- Drug Courts.
- Criminal Courts.
- Criminal Justice Ethics.
- Capital Punishment.
- Community Corrections.
- Criminal Law.
Cyber Security Future Research Topics
- Developing more effective methods for detecting and responding to cyber attacks
- Investigating the role of social media in cyber security
- Examining the impact of cloud computing on cyber security
- Investigating the security implications of the Internet of Things
- Studying the effectiveness of current cyber security measures
- Identifying new cyber security threats and vulnerabilities
- Developing more effective cyber security policies
- Examining the ethical implications of cyber security
Cyber Security Topics For Research Paper
- Cyber security threats and vulnerabilities
- Cyber security incident response and management
- Cyber security risk management
- Cyber security awareness and training
- Cyber security controls and countermeasures
- Cyber security governance
- Cyber security standards
- Cyber security insurance
- Cyber security and the law
- The future of cyber security
5 Current Research Topics in Cybersecurity
Below are the latest 5 cybersecurity research topics. They are:
- Artificial Intelligence
- Digital Supply Chains
- Internet of Things
- State-Sponsored Attacks
- Working From Home
Research Area in Cyber Security
The field of cyber security is extensive and constantly evolving. Its research covers a wide range of subjects, including:
- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
- RFID Security
- Authorisation Infrastructure
- Digital Forensics
- Autonomous Security
- Social Influence on Social Networks
How to Choose the Best Research Topics in Cyber Security
A good cybersecurity assignment heading is a skill that not everyone has, and unfortunately, not everyone has one. You might have your teacher provide you with the topics, or you might be asked to come up with your own. If you want more research topics, you can take references from Certified Ethical Hacker Certification, where you will get more hints on new topics. If you don't know where to start, here are some tips. Follow them to create compelling cybersecurity assignment topics.
1. Brainstorm
In order to select the most appropriate heading for your cybersecurity assignment, you first need to brainstorm ideas. What specific matter do you wish to explore? In this case, come up with relevant topics about the subject and select those relevant to your issue when you use our list of topics. You can also go to cyber security-oriented websites to get some ideas. Using any blog post on the internet can prove helpful if you intend to write a research paper on security threats in 2024. Creating a brainstorming list with all the keywords and cybersecurity concepts you wish to discuss is another great way to start. Once that's done, pick the topics you feel most comfortable handling. Keep in mind to stay away from common topics as much as possible.
2. Understanding the Background
In order to write a cybersecurity assignment, you need to identify two or three research paper topics. Obtain the necessary resources and review them to gain background information on your heading. This will also allow you to learn new terminologies that can be used in your title to enhance it.
3. Write a Single Topic
Make sure the subject of your cybersecurity research paper doesn't fall into either extreme. Make sure the title is neither too narrow nor too broad. Topics on either extreme will be challenging to research and write about.
4. Be Flexible
There is no rule to say that the title you choose is permanent. It is perfectly okay to change your research paper topic along the way. For example, if you find another topic on this list to better suit your research paper, consider swapping it out.
The Layout of Cybersecurity Research Guidance
It is undeniable that usability is one of cybersecurity's most important social issues today. Increasingly, security features have become standard components of our digital environment, which pervade our lives and require both novices and experts to use them. Supported by confidentiality, integrity, and availability concerns, security features have become essential components of our digital environment.
In order to make security features easily accessible to a wider population, these functions need to be highly usable. This is especially true in this context because poor usability typically translates into the inadequate application of cybersecurity tools and functionality, resulting in their limited effectiveness.
Writing Tips from Expert
Additionally, a well-planned action plan and a set of useful tools are essential for delving into Cyber Security Research Topics. Not only do these topics present a vast realm of knowledge and potential innovation, but they also have paramount importance in today's digital age. Addressing the challenges and nuances of these research areas will contribute significantly to the global cybersecurity landscape, ensuring safer digital environments for all. It's crucial to approach these topics with diligence and an open mind to uncover groundbreaking insights.
- Before you begin writing your research paper, make sure you understand the assignment.
- Your Research Paper Should Have an Engaging Topic
- Find reputable sources by doing a little research
- Precisely state your thesis on cybersecurity
- A rough outline should be developed
- Finish your paper by writing a draft
- Make sure that your bibliography is formatted correctly and cites your sources.
Discover the Power of ITIL 4 Foundation - Unleash the Potential of Your Business with this Cost-Effective Solution. Boost Efficiency, Streamline Processes, and Stay Ahead of the Competition. Learn More!
Studies in the literature have identified and recommended guidelines and recommendations for addressing security usability problems to provide highly usable security. The purpose of such papers is to consolidate existing design guidelines and define an initial core list that can be used for future reference in the field of Cyber Security Research Topics.
The researcher takes advantage of the opportunity to provide an up-to-date analysis of cybersecurity usability issues and evaluation techniques applied so far. As a result of this research paper, researchers and practitioners interested in cybersecurity systems who value human and social design elements are likely to find it useful. You can find KnowledgeHut’s Cyber Security courses online and take maximum advantage of them.
Frequently Asked Questions (FAQs)
Businesses and individuals are changing how they handle cybersecurity as technology changes rapidly - from cloud-based services to new IoT devices.
Ideally, you should have read many papers and know their structure, what information they contain, and so on if you want to write something of interest to others.
The field of cyber security is extensive and constantly evolving. Its research covers various subjects, including Quantum & Space, Data Privacy, Criminology & Law, and AI & IoT Security.
Inmates having the right to work, transportation of concealed weapons, rape and violence in prison, verdicts on plea agreements, rehab versus reform, and how reliable are eyewitnesses?

Mrinal Prakash
I am a B.Tech Student who blogs about various topics on cyber security and is specialized in web application security
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
75 Cyber Security Research Topics in 2024
Introduction to Cybersecurity Research
Cybersecurity research aims to protect computer systems, networks, and data from unauthorised access, theft, or damage. It involves studying and developing methods and techniques to identify, understand, and mitigate cyber threats and vulnerabilities.
The field can be divided into theoretical and applied research and faces challenges such as
- Increasing complexity
- New forms of malware
- The growing sophistication of cyber attacks
On a daily basis, approximately 2,200 cyber attacks occur, with an average of one cyber attack happening every 39 seconds. This is the reason why researchers must stay up-to-date and collaborate with others in the field.
In this article, let’s discuss the different cybersecurity research topics and how they will help you become an expert in the field.

Check out our free technology courses to get an edge over the competition.
Here are some of the latest research topics in cyber security –
Emerging Cyber Threats and Vulnerabilities in 2024
Continual technological advancements lead to changes in cybersecurity trends, with data breaches, ransomware, and hacks becoming more prevalent.
- Cyber Attacks and Their Countermeasures – Discuss – This research paper will discuss various cyber attacks and their corresponding countermeasures. It aims to provide insights on how organisations can better protect themselves from cyber threats.
- Is Cryptography Necessary for Cybersecurity Applications? – Explore the role of cryptography in ensuring the confidentiality, integrity, and availability of data and information in cybersecurity. It would examine the various cryptographic techniques used in cybersecurity and their effectiveness in protecting against cyber threats.
Here are some other cyber security topics that you may consider –
- Discuss the Application of Cyber Security for Cloud-based Applications
- Data Analytics Tools in Cybersecurity
- Malware Analysis
- What Are the Behavioural Aspects of Cyber Security?
- Role of Cyber Security on Intelligent Transporation Systems
- How to Stop and Spot Different Types of Malware?
Check Out upGrad’s Software Development Courses to upskill yourself.
Machine Learning and AI in Cybersecurity Research
Machine learning and AI are research topics in cybersecurity, aiming to develop algorithms for threat detection, enhance intelligence and automate risk mitigation. However, security risks like adversarial attacks require attention.

- Using AI/ML to Analyse Cyber Threats – This cyber security research paper analyses cyber threats and could include an overview of the current state of cyber threats and how AI/ML can help with threat detection and response. The paper could also discuss the challenges and limitations of using AI/ML in cybersecurity and potential areas for further research.
Here are some other topics to consider –
- Developing Cognitive Systems for Cyber Threat Detection and Response
- Developing Distributed Ai Systems to Enhance Cybersecurity
- Developing Deep Learning Architectures for Cyber Defence
- Exploring the Use of Computational Intelligence and Neuroscience in Enhancing Security and Privacy
- How is Cyber Security Relevant for Everyone? Discuss
- Discuss the Importance of Network Traffic Analysis
- How to Build an App to Break Ceasar Cipher
You can check out the Advanced Certificate Programme in Cyber Security course by upGrad, which will help students become experts in cyber security.
IoT Security and Privacy
IoT security and privacy research aim to develop secure and privacy-preserving architectures, protocols, and algorithms for IoT devices, including encryption, access control, and secure communication. The challenge is to balance security with usability while addressing the risk of cyber-attacks and compromised privacy.
- Service Orchestration and Routing for IoT – It may focus on developing efficient and secure methods for managing and routing traffic between IoT devices and services. The paper may explore different approaches for optimising service orchestration.
- Efficient Resource Management, Energy Harvesting, and Power Consumption in IoT – This paper may focus on developing strategies to improve energy use efficiency in IoT devices. This may involve investigating the use of energy harvesting technologies, optimising resource allocation and management, and exploring methods to reduce power consumption.
Here are some other cyber security project topics to consider –
- Computation and Communication Gateways for IoT
- The Miniaturisation of Sensors, Cpus, and Networks in IoT
- Big Data Analytics in IoT
- Semantic Technologies in IoT
- Virtualisation in IoT
- Privacy, Security, Trust, Identity, and Anonymity in IoT
- Heterogeneity, Dynamics, and Scale in IoT
- Consequences of Leaving Unlocked Devices Unattended
Explore our Popular Software Engineering Courses
Blockchain security: research challenges and opportunities.
Blockchain security research aims to develop secure and decentralised architectures, consensus algorithms, and privacy-preserving techniques while addressing challenges such as smart contract security and consensus manipulation. Opportunities include transparent supply chain management and decentralised identity management.
- Advanced Cryptographic Technologies in the Blockchain – Explore the latest advancements and emerging trends in cryptographic techniques used in blockchain-based systems. It could also analyse the security and privacy implications of these technologies and discuss their potential impact.
- Applications of Smart Contracts in Blockchain – Explore the various use cases and potential benefits of using smart contracts to automate and secure business processes. It could also examine the challenges and limitations of smart contracts and propose potential solutions for these issues.
Here are some other topics –
- Ensuring Data Consistency, Transparency, and Privacy in the Blockchain
- Emerging Blockchain Models for Digital Currencies
- Blockchain for Advanced Information Governance Models
- The Role of Blockchain in Future Wireless Mobile Networks
- Law and Regulation Issues in the Blockchain
- Transaction Processing and Modification in the Blockchain
- Collaboration of Big Data With Blockchain Networks
Cloud Security: Trends and Innovations in Research
Cloud security research aims to develop innovative techniques and technologies for securing cloud computing environments, including threat detection with AI, SECaaS, encryption and access control, secure backup and disaster recovery, container security, and blockchain-based solutions. The goal is to ensure the security, privacy, and integrity of cloud-based data and applications for organisations.
- Posture Management in Cloud Security – Discuss the importance of identifying and addressing vulnerabilities in cloud-based systems and strategies for maintaining a secure posture over time. This could include topics such as threat modelling, risk assessment, access control, and continuous monitoring.
- Are Cloud Services 100% Secure?
- What is the Importance of Cloud Security?
- Cloud Security Service to Identify Unauthorised User Behaviour
- Preventing Theft-of-service Attacks and Ensuring Cloud Security on Virtual Machines
- Security Requirements for Cloud Computing
- Privacy and Security of Cloud Computing
Explore Our Software Development Free Courses
Cybercrime investigations and forensics.
Cybercrime investigations and forensics involve analysing digital evidence to identify and prosecute cybercriminals, including developing new data recovery, analysis, and preservation techniques. Research also focuses on identifying cybercriminals and improving legal and regulatory frameworks for prosecuting cybercrime.
- Black Hat and White Hat Hacking: Comparison and Contrast – Explore the similarities and differences between these two approaches to hacking. It would examine the motivations and methods of both types of hackers and their impact on cybersecurity.
- Legal Requirements for Computer Forensics Laboratories
- Wireless Hacking Techniques: Emerging Technologies and Mitigation Strategies
- Cyber Crime: Current Issues and Threats
- Computer Forensics in Law Enforcement: Importance and Challenges
- Basic Procedures for Computer Forensics and Investigations
- Digital Forensic Examination of Counterfeit Documents: Techniques and Tools
- Cybersecurity and Cybercrime: Understanding the Nature and Scope
An integral part of cybercrime investigation is to learn software development. Become experts in this field with the help of upGrad’s Executive Post Graduate Programme in Software Development – Specialisation in Full Stack Development .
Cybersecurity Policy and Regulations
Cybersecurity policy and regulations research aims to develop laws, regulations, and guidelines to ensure the security and privacy of digital systems and data, including addressing gaps in existing policies, promoting international cooperation, and developing standards and best practices for cybersecurity. The goal is to protect digital systems and data while promoting innovation and growth in the digital economy.
- The Ethicality of Government Access to Citizens’ Data – Explore the ethical considerations surrounding government access to citizens’ data for surveillance and security purposes, analysing the potential risks and benefits and the legal and social implications of such access.
- The Moral Permissibility of Using Music Streaming Services – Explore the ethical implications of using music streaming services, examining issues such as intellectual property rights, artist compensation, and the environmental impact of streaming.
- Real Name Requirements on Internet Forums
- Restrictions to Prevent Domain Speculation
- Regulating Adult Content Visibility on the Internet
- Justification for Illegal Downloading
- Adapting Law Enforcement to Online Technologies
- Balancing Data Privacy With Convenience and Centralisation
- Understanding the Nature and Dangers of Cyber Terrorism
Human Factors in Cybersecurity
Human factors in cybersecurity research study how human behaviour impacts cybersecurity, including designing interfaces, developing security training, addressing user error and negligence, and examining cybersecurity’s social and cultural aspects. The goal is to improve security by mitigating human-related security risks.
- Review the Human Factors in Cybersecurity – It explores various human factors such as awareness, behaviour, training, and culture and their influence on cybersecurity, offering insights and recommendations for improving cybersecurity outcomes.
- Integrating Human Factors in Cybersecurity for Better Risk Management
- Address the Human Factors in Cybersecurity Leadership
- Human Factors in IoT Security
- Internal Vulnerabilities: the Human Factor in It Security
- Cyber Security Human Factors – the Ultimate List of Statistics and Data
In-Demand Software Development Skills
Cybersecurity education and awareness.
Cybersecurity education and awareness aims to educate individuals and organisations about potential cybersecurity threats and best practices to prevent cyber attacks. It involves promoting safe online behaviour, training on cybersecurity protocols, and raising awareness about emerging cyber threats.
- Identifying Phishing Attacks – This research paper explores various techniques and tools to identify and prevent phishing attacks, which are common types of cyber attacks that rely on social engineering tactics to trick victims into divulging sensitive information or installing malware on their devices.
- Risks of Password Reuse for Personal and Professional Accounts – Investigate the risks associated with reusing the same password across different personal and professional accounts, such as the possibility of credential stuffing attacks and the impact of compromised accounts on organisational security.
- Effective Defence Against Ransomware
- Information Access Management: Privilege and Need-to-know Access
- Protecting Sensitive Data on Removable Media
- Recognising Social Engineering Attacks
- Preventing Unauthorised Access to Secure Areas: Detecting Piggybacking and Tailgating
- E-mail Attack and Its Characteristics
- Safe Wifi Practice: Understanding VPN
With the increasing use of digital systems and networks, avoiding potential cyber-attacks is more important than ever. The 75 research topics outlined in this list offer a glimpse into the different dimensions of this important field. By focusing on these areas, researchers can make significant contributions to enhancing the security and safety of individuals, organisations, and society as a whole.
upGrad’s Master of Science in Computer Science program is one of the top courses students can complete to become experts in the field of tech and cyber security. The program covers topics such as Java Programming and other forms of software engineering which will help students understand the latest technologies and techniques used in cyber security.
The program also includes hands-on projects and case studies to ensure students have practical experience in applying these concepts. Graduates will be well-equipped to take on challenging roles in the rapidly growing field of cyber security.

Pavan Vadapalli
Something went wrong
Our Popular Software Engineering Courses
Our Trending Software Engineering Courses
- Master of Science in Computer Science from LJMU
- Executive PG Program in Software Development Specialisation in Full Stack Development from IIIT-B
- Advanced Certificate Programme in Cyber Security from IIITB
- Full Stack Software Development Bootcamp
- Software Engineering Bootcamp from upGrad
Popular Software Development Skills
- React Courses
- Javascript Courses
- Core Java Courses
- Data Structures Courses
- ReactJS Courses
- NodeJS Courses
- Blockchain Courses
- SQL Courses
- Full Stack Development Courses
- Big Data Courses
- Devops Courses
- NFT Courses
- Cyber Security Courses
- Cloud Computing Courses
- Database Design Courses
- Crypto Courses
- Python Courses
Frequently Asked Questions (FAQs)
Artificial intelligence (AI) has proved to be an effective tool in cyber defence. AI is anticipated to gain even more prominence in 2024, mainly in monitoring, resource and threat analysis, and quick response capabilities.
One area of focus is the development of secure quantum and space communications to address the increasing use of quantum technologies and space travel. Another area of research is improving data privacy.
The approach to cybersecurity is expected to change from defending against attacks to acknowledging and managing ongoing cyber risks. The focus will be on improving resilience and recovering from potential cyber incidents.
Related Programs View All
Certification
40 Hrs Live, Expert-Led Sessions
2 High-Quality Practice Exams
View Program

Master's Degree
40000+ Enrolled Learners

Executive PG Program
IIIT-B Alumni Status

2 Unique Specialisations

Job Assistance
300+ Hiring Partners
159+ Hours of Live Sessions
126+ Hours of Live Sessions
Fully Online
20+ Hrs Instructor-Led Sessions
Live Doubt-Solving Sessions
13+ Hrs Instructor-Led Sessions
17+ Hrs Instructor-Led Training
3 Real-World Capstone Projects
32-Hr Training by Dustin Brimberry
Question Bank with 300+ Practice Qs
16 Hrs Live Expert-Led Training
CLF-C02 Exam Prep Support

Microsoft-Approved Curriculum
24 Hrs Live Expert-Led Training
4 Real-World Capstone Projects
45 Hrs Live Expert-Led Training
289 Hours of Self-Paced Learning
10+ Capstone Projects
288 Hours Self-Paced Learning
9 Capstone Projects
490+ Hours Self-Paced Learning
4 Real-World Projects
690+ Hours Self-Paced Learning
Cloud Labs-Enabled Learning
40 Hrs Live Expert-Led Sessions
2 Mock Exams, 9 Assessments

Executive PG Certification
GenAI integrated curriculum

Job Prep Support
Instructor-Led Sessions
Hands-on UI/UX
16 Hrs Live Expert-Led Sessions
12 Hrs Hand-On Practice
30+ Hrs Live Expert-Led Sessions
24+ Hrs Hands-On with Open Stack
2 Days Live, Expert-Led Sessions
34+ Hrs Instructor-Led Sessions
10 Real-World Live Projects
24 Hrs Live Expert-Led Sessions
16 Hrs Hand-On Practice
8 Hrs Instructor-Led Training
Case-Study Based Discussions
40 Hrs Instructor-Led Sessions
Hands-On Practice, Exam Support
24-Hrs Live Expert-Led Sessions
Regular Doubt-Clearing Sessions
Extensive Exam Prep Support
6 Hrs Live Expert-Led Sessions
440+ Hours Self-Paced Learning
400 Hours of Cloud Labs
15-Hrs Live Expert-Led Sessions
32 Hrs Live Expert-Led Sessions
28 Hrs Hand-On Practice
Mentorship by Industry Experts
24 Hrs Live Trainer-Led Sessions
Mentorship by Certified Trainers
GenAI Integrated Curriculum
Full Access to Digital Resources
16 Hrs Live Instructor-Led Sessions
80+ Hrs Hands-On with Cloud Labs
160+ Hours Live Instructor-Led Sessions
Hackathons and Mock Interviews
31+ Hrs Instructor-Led Sessions
120+ Hrs of Cloud Labs Access
35+ Hrs Instructor-Led Sessions
6 Real-World Live Projects
24+ Hrs Instructor-Led Training
Self-Paced Course by Nikolai Schuler
Access Digital Resources Library
300+ Hrs Live Expert-Led Training
90 Hrs Doubt Clearing Sessions
56 Hours Instructor-Led Sessions
82 Hrs Live Expert-Led Sessions
22 Hrs Live, Expert-Led Sessions
CISA Job Practice Exams
Explore Free Courses
Learn more about the education system, top universities, entrance tests, course information, and employment opportunities in Canada through this course.
Advance your career in the field of marketing with Industry relevant free courses
Build your foundation in one of the hottest industry of the 21st century
Master industry-relevant skills that are required to become a leader and drive organizational success
Build essential technical skills to move forward in your career in these evolving times
Get insights from industry leaders and career counselors and learn how to stay ahead in your career
Kickstart your career in law by building a solid foundation with these relevant free courses.
Stay ahead of the curve and upskill yourself on Generative AI and ChatGPT
Build your confidence by learning essential soft skills to help you become an Industry ready professional.
Learn more about the education system, top universities, entrance tests, course information, and employment opportunities in USA through this course.
Suggested Tutorials

Explore Python programming with this concise tutorial, covering basics to advanced concepts for beginners and enthusiasts alike.

Introduction to C Programming, Learn all the C programming language concepts in this tutorial.
Suggested Blogs
12 Apr 2024
![research areas of cyber security Scrum Master Salary in India: For Freshers & Experienced [2023]](https://www.upgrad.com/__khugblog-next/image/?url=https%3A%2F%2Fd14b9ctw0m6fid.cloudfront.net%2Fugblog%2Fwp-content%2Fuploads%2F2020%2F05%2F486.png&w=3840&q=75)
by Rohan Vats
05 Mar 2024
![research areas of cyber security SDE Developer Salary in India: For Freshers & Experienced [2024]](https://www.upgrad.com/__khugblog-next/image/?url=https%3A%2F%2Fd14b9ctw0m6fid.cloudfront.net%2Fugblog%2Fwp-content%2Fuploads%2F2020%2F05%2F482-1.png&w=3840&q=75)
by Prateek Singh
29 Feb 2024
by venkatesh Rajanala
by Harish K
by Geetika Mathur
by spandita hati

BreachSight
Vendor risk, trust exchange, product features, vendor risk assessments, security questionnaires.
- Security Ratings
Data Leaks Detection
- Integrations
AI Autofill
- Financial Services
eBooks, Reports, & more
What are the different fields in cybersecurity.

Cybersecurity is a broad term that describes the practice of securing and protecting all computer systems, devices, and programs in an IT environment from cyber attacks or cyber threats . However, within the field of cybersecurity, there are many different specializations that individuals can choose for their career paths. Cybersecurity touches nearly every aspect of society , from the healthcare industry to finance to governments, and it continues to be one of the fastest-growing career opportunities for professionals.
How Can I Get Into the Cybersecurity Field?
As one of the fastest-growing fields in the world today, cybersecurity jobs have one of the highest average salaries in both entry-level and experienced roles. Even with no technical background experience , it’s still possible to choose a cybersecurity career.
There are both technical and non-technical positions within the industry, and not all of them require a bachelor’s degree. If you’re interested in becoming a cybersecurity professional, it’s important to build up both soft and technical skills that are extremely important to succeed in the industry.
To get a security job, the most valued skills to have are:
- Critical thinking and problem-solving ability
- Strong desire and passion for learning new concepts and technologies
- Detail-oriented and task-focused mindset
- Adaptability to constantly changing environments
Of course, it’s also important to maintain a working knowledge of the cybersecurity landscape by keeping up to date with the latest news and reports. It’s highly recommended to stay up to date with the latest stories and join the cybersecurity community to become truly ingrained in the field.
Sign up for UpGuard’s weekly newsletter to stay informed on the latest developments in the cybersecurity world.
What Are The Different Cybersecurity Fields?
Here are the main fields in cybersecurity that individuals can choose to branch out to:
Information Security
Information technology (IT) security analysts and security engineers are common entry-level roles for those looking to get started in the cybersecurity world. Most information security specialists require a computer science or software engineering background, and it’s also highly recommended that they become certified (CompTIA Security+, GCIA, GCIH).
Their main responsibilities are:
- Network security /application security
- Investigating and documenting data breaches or data leaks
- Carrying out security plans and procedures
- Protecting systems from security risks and malware
- Configuring security protocols such as firewalls, intrusion detection systems (IDS) , and intrusion prevention systems (IPS)
- Troubleshooting computer network and security infrastructure
Most cybersecurity analysts and engineers work within a larger team, led by an IT security manager, security administrator, or security architect. While analysts focus more on identifying and responding to cyber threats and executing security procedures, engineers are responsible for creating the individual security systems of a company. Cybersecurity engineers can become certified with Certified Information Systems Security Professional (CISSP) and Certified Cloud Security Professional (CCSP).
Security architects are one of the highest levels in information security as they are responsible for designing the entire security infrastructure of a company. As the main cybersecurity managers, they are generally less hands-on than engineers and require a broader knowledge of information security to make executive decisions. They typically report directly to the Chief Information Security Officer (CISO) and often get promoted to the CISO position later in their careers.
Learn more about the role of CISOs.
IT Auditing & Consulting
An IT auditor performs audits on an organization’s security standards, compliance, and overall infrastructure to ensure that they can effectively secure their data. Two main cybersecurity certifications are necessary to become an IT auditor: CISA (Certified Information Systems Auditor) and CISM (Certified Information Security Manager).
Auditors must have a broad understanding of multiple fields, including:
- Network security infrastructure (firewalls, VPNs , web proxy , IDS/IPS )
- Telecommunications
- Information security and processing
- Computer systems and applications
- Data analysis tools
- Third-Party Risk Management
- Security testing procedures
- Industry security standards
IT auditors are typically a mid-level role, requiring a few years of working in information security (CISA - 5 years, CISM - 3 years). They can perform standard audits or become security consultants at the highest level to help identify areas of security needs within an organization. Top auditors and consultants also have advanced knowledge of market standards and competitors that allow them to determine what the best security practices are.
Ethical Hacking/Penetration Testing
An ethical hacker is a unique job title that attempts to find all of the system vulnerabilities within an organization to expose flaws or exploits in each system. A CEH has a unique skill set because they must think like a potential threat actor and stay updated with the latest hacking techniques and tools in the entire threat landscape . Sometimes companies may put out “bug bounties” to invite ethical hackers to find vulnerabilities in their systems in exchange for a financial reward.
One important area of ethical hacking is penetration testing . A penetration tester conducts simulated tests on specific areas of a security system to find new vulnerabilities . This allows organizations to focus on higher risk areas rather than testing the entire system every time. Penetration testers may be given specific pieces of sensitive information and attempt to penetrate a system to test its security.
Aspiring ethical hackers can become certified by attaining the Certified Ethical Hacker (CEH), GIAC Penetration Tester (GPEN), or CompTIA PenTest+ certifications.
Learn more about penetration testing.
Learn the differences between cybersecurity and ethical hacking.
Threat Intelligence
Threat intelligence analysts collect existing evidence and data on common attack behaviors, techniques, and indicators ( IOCs and IOAs ) and help develop new security plans to address them. Many organizations make important security decisions based on the threat intelligence data to not only respond to security incidents but also prevent them.
One particular role of threat intelligence is proactive cyber threat hunting, which aims to anticipate any potential threats before an actual attack. Their main goal is to review common attack behaviors and techniques, or TTP (tactics, techniques, and procedures) , and apply them to current systems to protect their attack surface and improve security posture . Experienced threat hunters have a much higher understanding of the threat landscape than most other fields and require thinking from a threat actor’s perspective.
OSINT (open-source intelligence) analysts and investigators are also crucial in threat intelligence. OSINT investigators use specialized methods to gather sensitive information that may be publicly available online. By identifying which information has been leaked, companies can use that data to improve their security and prevent future breaches.
Learn more about threat intelligence.
Software Development
Software development is a product and client-focused field that helps integrate programs and applications into an organization’s security structure. Developers are fully involved in the design, testing, and implementation of systems to make sure they fully meet the needs of a company or individual. By identifying user pain points, they can use the data to create new features to protect against potential vulnerabilities.
Cybersecurity software developers must have a wide range of knowledge of all information security fields to accurately assess what front-end software designs are needed. Developers differ from security engineers in that they are not responsible for building the security systems directly but instead provide client-facing solutions for the product. Typically, developers have more substantial knowledge of forward-facing coding languages, such as HTML, CSS, or JavaScript.
Digital Forensics
Digital forensics is a critical function in cybersecurity that focuses on investigating cyberattacks and figuring out how hackers were able to penetrate a system. They must look for clues to determine which techniques were used by the cybercriminals to access the networks illegally. There are many branches of digital forensics, including computer forensics, network forensics, and database forensics.
The main responsibilities of digital forensics and incident response (DFIR) analysts or computer security and incident response teams (CSIRT) are to:
- Identify common attack behaviors
- Investigate suspicious network activity
- Collect and review digital evidence to create stronger security measures
- Create remediation and recovery procedures
- Assist law enforcement during a cybercrime investigation
Although digital forensics typically waits for an attack to occur before responding, recent advancements in artificial intelligence (AI) and machine learning (ML) have helped establish preventative measures. As such, the field of digital forensics is closely tied with cyber threat hunting. Working in digital forensics requires a strong understanding of the attack landscape to quickly respond to and eliminate threat actors.
Learn more about digital forensics.
Cryptography
Cryptographers have one main responsibility: to write encryption code strong enough to secure important or sensitive data . Cryptography engineers often come from computer programming, computer engineering, and mathematics backgrounds because they are expected to write and refine complex algorithms or ciphers that outside parties can’t break.
Most cryptographers have at least a master’s degree, if not a doctorate, in their field of study. The most common certification to obtain for cryptography is the EC-Council Certified Encryption Specialist (ECES).
Because the technology landscape is constantly evolving, cryptographers are expected to stay informed of the latest cryptology theories, security solutions, and infrastructure designs. Government agencies often hire the top cryptographers worldwide to protect their classified information, particularly if there is communication involved, to prevent potential hackers from decoding or intercepting encrypted information.
Reviewed by

Kaushik Sen
Ready to see upguard in action, ready to save time and streamline your trust management process, scale your tprm.

Join 27,000+ cybersecurity newsletter subscribers
Related posts
The top cybersecurity websites and blogs of 2024.

14 Cybersecurity Metrics + KPIs You Must Track in 2024
What are security ratings cyber performance scoring explained, why is cybersecurity important, what is typosquatting (and how to prevent it), introducing upguard's new sig lite questionnaire.

- UpGuard Vendor Risk
- UpGuard BreachSight
- Product Video
- Release notes
- SecurityScorecard
- All comparisons
- Security Reports
- Instant Security Score
- Attack Surface Management
- Cybersecurity
The future of cybersecurity

With TikTok in the hands of 170 million Americans, cybersecurity expert Amy Zegart says it’s time to talk about consequences. Foreign access to all that data on so many Americans is a national security threat, she asserts.
For those as concerned as she, Zegart has good news and bad. The government has gotten better at fighting cyberthreats, but artificial intelligence is making things very complicated, very fast. The US needs to adapt quickly to keep pace, Zegart tells host Russ Altman on this episode of Stanford Engineering’s The Future of Everything podcast.
Listen on your favorite podcast platform:
Related : Amy Zegart , senior fellow at The Hoover Institution, Freeman Spogli Institute for International Studies (FSI), and Stanford Institute for Human Centered Artificial Intellligence (HAI)
[00:00:00] Amy Zegart: What we really need to pursue much more seriously is developing independent capacity. Developing the talent, developing the compute that, I know at Stanford's been really pushing this idea of a national AI, research resource. That's fancy talk for compute power so that independent researchers can ask hard questions, uh, and do the kind of analysis that, that needs to be done.
[00:00:27] I think we need to be investing much more in that. Compute is a strategic national asset like oil. And the government should be investing orders of magnitude more and making that available.
[00:00:44] Russ Altman: This is Stanford Engineering's The Future of Everything podcast, and I'm your host, Russ Altman. If you're enjoying the show or if it's helping you in any way, please consider sharing it with friends, family, and colleagues. Personal recommendations are one of the best ways to spread the news about the podcast.
[00:00:59] Today, Amy Zegart from Stanford University will tell us about cybersecurity and AI. How have things changed in the last three or four years since she was last a guest on The Future of Everything? It's the future of cybersecurity.
[00:01:13] Before we get started, a quick reminder that if you're enjoying this show, please consider sharing it with friends and family. Personal recommendations really do work in growing the podcast audience and improving the podcast.
[00:01:31] Cybersecurity is a huge issue for the United States. Computers are one of the battlefields where the next big conflicts are and will be waged. Specifically, we focus on four countries that are the source of lots of cyber attacks. These include Russia, China, North Korea, and Iran. Intelligence is complicated, and it's gotten more complicated in the last few years with the rise of AI.
[00:01:55] Now, disinformation can be generated and spread more quickly and more realistic looking. Amy Zegart is a senior fellow at the Hoover Institute, the Freeman Spogli Institute for International Affairs, and the Institute for Human Centered AI at Stanford University. She's an expert in cybersecurity. She's written several books and she's an advisor to the nation.
[00:02:17] She's going to tell us that AI has accelerated the work of both the good guys trying to combat cyber warfare and cyber attacks, as well as, unfortunately, the bad guys who are making the attacks. However, things are looking better and there's reason to be optimistic. Amy, you're a return visitor to The Future of Everything.
[00:02:37] It's a great honor for me. You can decide if it's an honor for you or not. Last time we discussed cyber security and you said something very memorable, which is that the cyber security world is moving at light speed and the government is moving at government speed. Now in the interim, since you were last on the show, there's this thing called AI that has just exploded. ChatGPT and many other technologies. Has that changed the situation? Is the government able to respond faster? Are the cyber attacks able to come faster? Both, neither. Where are we these days with respect to the relative strengths of the government and of the cyber attackers?
[00:03:18] Amy Zegart: Well, Russ, thanks for starting me off with such a softball question. It's really an honor to be back with you too. It's a complicated question. There's good news and bad news. Let me start with the good news. Government has matured. So part of the challenge, as you know, of dealing with cyber is do we have capacity in the government to understand and coordinate and work with the private sector?
[00:03:40] That's gotten a lot better. So we have the creation of the National Cyber Director. That office has matured. There's a state department ambassador at large for cyber. That's a really important component to it. Um, secondly, there are SEC regulations now.
[00:03:55] Russ Altman: Wow.
[00:03:55] Amy Zegart: So there's an incentive for corporate boards to pay much more attention to cyber security. And when the incentives are aligned, of course, companies pay more money for cybersecurity, do a lot more investing in cybersecurity. So that, those SEC rules have kicked in. And I think that's important to bear in mind.
[00:04:12] Russ Altman: Can you, just to take, just to dive down, why would the SEC, why does the SEC even regulate that? I'm a little bit surprised. I think of them as regulating, you know, disclosures about the company and the financials and all that kind of stuff, monopolies, where does cybersecurity come into their kind of purview?
[00:04:28] Amy Zegart: I think there's a sense that it's a question of governance and it's not, the SEC regulations aren't dictating specific cybersecurity actions, but they are incentivizing processes. So corporate directors are held responsible for oversight of cybersecurity. And that's then catalyzed a whole bunch of other things, you know, regular reporting and in private and public companies as well.
[00:04:53] Russ Altman: And it's not the case that the companies would have been independently motivated not to be attacked, not to have ransomware? I'm just surprised that we needed to tell them this.
[00:05:02] Amy Zegart: Well, many companies are incentivized. When you think about financial services, for example, they've invested an enormous amount of money in their cyber security, and they know they need to. But many companies think that cyber security is really for the big guys. Cyber security is for the sexy industries. Remember Home Depot? When Home Depot got hacked?
[00:05:20] Russ Altman: Yes.
[00:05:20] Amy Zegart: Right? Their defense was, we just sell hammers. Why are we a victim of cyber attacks? So, when you think about,
[00:05:27] Russ Altman: Now the bad guys know about my wheelbarrow.
[00:05:30] Amy Zegart: Exactly. So when you think about the cyber attack surface, it's everywhere. So you really want to incentivize all companies to spend more money and pay more attention to cybersecurity. I think that's,
[00:05:41] Russ Altman: Sorry, I interrupted you on that because I was just surprised. Keep going. Yeah.
[00:05:44] Amy Zegart: So that's the plus side of the ledger. The negative side of the ledger, and you asked about AI, is AI makes everything more complicated and faster. So is AI being used to automate cybersecurity on the defensive side? Yes. Is AI used to automate offensive attacks against cybersecurity defenses? Yes.
[00:06:04] So it sort of washes out. It's good news and bad news on that side. But let me add one other, uh, depressing wrinkle to the story, which is, of course, what are the attackers thinking? What are their capabilities? And what are their intentions? And there, the picture is bad. So I want to read to you the intelligence threat assessment, the annual intelligence threat assessment that was just delivered last month by the Director of National Intelligence to Congress. And this is about China. This is what the intelligence community’s assessment said.
[00:06:38] If Beijing believed that a major conflict with the United States were imminent it would consider aggressive cyber operations against U.S. critical infrastructure, by the way, that means just about everything, and military assets. It goes on to say, designed to induce societal panic.
[00:07:02] What they're saying is, it's not just if a war breaks out, if China believes conflict is imminent, they're already in our systems. And they have an incentive and an interest in attacking. So the bad guys are out there. Just because they haven't attacked us yet, doesn't mean they won't. So when you think about nation states with real cyber capabilities, China, Russia, Iran, North Korea, they're out there and they have not been defeated on the cyber landscape.
[00:07:30] Russ Altman: I'm glad you mentioned our favorite four countries because, uh, because I wanted to ask you, are they, are there, I'm suspecting that their interests are not precisely aligned and that they all have a different kind of, uh, piece of the game in mind. So you just kind of described how China might be thinking of it as a defensive slash offensive, basically a weapon for a potential, uh, conflict with the U.S., is that the same kind of thinking that Russia is doing? Or are they just, they seem more random? That's why I ask, because they seem more random in their attacks.
[00:08:04] Amy Zegart: There are different flavors of their interests, right? So Russia is really focused on the disinformation space. So think about foreign election interference. So the Russians really like that space, uh, fomenting, uh, you know, exacerbating polarization in the United States. By the way, the Chinese are trying to do that too. The Iranians too, but Russia is the A team. That's, they're really good at that. The North Koreans want to steal. Right? So they're trying to steal everything they can in cyberspace. When you think about ransomware, I think primarily North Koreans, Russians too.
[00:08:35] Russ Altman: Okay.
[00:08:35] Amy Zegart: But they're really in it for the money. The Iranians have sort of a vengeful attitude towards cyber attacks. So you'll see cyber attacks against, um, particular targets like casinos, right? And they're very vengeful, uh, in there, like specifically targeting, uh, you know, assets that are owned by people that say things that they don't like.
[00:08:58] Now that's a broad simplification of the differences between these four countries, but they're all very capable cyber adversaries. Uh, and those capabilities are growing over time. So it's a cat and mouse defense offense game.
[00:09:13] Russ Altman: And can you update us on the issue of Russia? What have we learned from the Russian Ukrainian conflict? Has Russia, uh, have they been successful in kind of as part of their to include the cyber security or have the Ukrainians successfully fended them off? And are we learning anything by watching this conflict? Are we learning anything that could be useful to us in combating the Russians?
[00:09:37] Amy Zegart: So yes and yes.
[00:09:38] Russ Altman: Okay, good.
[00:09:39] Amy Zegart: Yes. Um, I think the narrative of the Russian cyber attacks against Ukraine at the start of the war turns out to be not quite right. You'll remember at the start of the war, the big question was, how come they didn't do more in cyberspace? They actually did do a lot in cyberspace, we now know, right?
[00:09:58] They attacked Viasat, so this is a pretty significant cyber attack. And they tried to do a lot more. Why didn't they succeed is the question, is the more important question. Part of the answer we now know is that United States Cyber Command was helping the Ukrainians weeks before the Russian attack.
[00:10:18] And so this was about moving critical digital assets to safer, uh, configurations. This was about fending off attacks. This was about working side by side with the Ukrainians to try to mitigate the risk of a cyber sort of first strike that would really take them out. And so we know a lot more now that's been revealed publicly about U.S. Cyber Command's role there.
[00:10:40] The other thing I think that we learned is that cyber attacks in an ongoing conflict are actually really hard to pull off, right? So it's one thing to initiate an attack at the start of a conflict where you're planning to go in.
[00:10:53] Russ Altman: The surprise.
[00:10:54] Amy Zegart: But then sustaining that level of activity and adapting to the threat landscape turns out to be much harder.
[00:11:03] Russ Altman: Really interesting. Okay. So, um, all right. So you gave a great answer to my initial question. And the answer is that the cyber guys have gotten faster. The government is a little bit, is more on board and presumably is getting faster. Um, what about a domestic? I know that you've spent a lot of time thinking about, uh, global threats. Um, I think you also think about internal, um, domestic threats. Um, Is that true?
[00:11:29] Amy Zegart: Not so much. I worry about things coming from outside the United States, not inside the United States.
[00:11:35] Russ Altman: Okay. So tell me about, um, have they gotten, so misinformation, I want to talk about misinformation. Um, you already alluded to it as especially like messing up elections. Uh, and generally it's an attempt to create chaos. Is that how I should think about it?
[00:11:52] Amy Zegart: So it depends. So let's just talk a little bit about terminology. So misinformation is information that is wrong, but people are mistakenly sending it around, right? So this is your crazy uncle sending things that he may think may be true, but are actually not true.
[00:12:08] So disinformation is a deliberate effort by somebody to spread something that they know to be false. We have both problems. People spreading things that are patently false, but they don't know they're false and they go viral. And then nefarious actors, domestic and foreign, that are knowingly spreading information that is false.
[00:12:28] And in that category, right, there are a variety of motives, but from a foreign adversary perspective, it is to fray the bonds of democratic societies that bring us together. Anything that gets you and me to fight with each other about what's true or what's not, or what we believe in and, um, what our values are in conflict benefits these adversaries.
[00:12:50] Russ Altman: Yeah. So, and I've heard that. And so, you know, as you may be aware, Uh, there is a lot of splits in the U.S. right now, politically, and it makes me wonder when you say things like what you just said, um, is some of that manufactured not from deeply held beliefs of the two sides. Uh, but from external sources, and that would actually, in a funny way, be a hopeful thing, because it might imply that we actually have a chance to resolve some of these divides if we could kind of get the noise from the, uh, external pertur, perturbators out, but I don't know if that's too Pollyanna.
[00:13:25] I'm sure it is too Pollyannaish. So how should I think about when I look at the political divides in the U.S.? Do we have a sense for how much is that created from external sources and how much is in some sense? Like real, or is that not even a question that makes sense?
[00:13:39] Amy Zegart: I think it's a great question. I don't think we know the answer. It's so hard to unravel what are the roots of, uh, the particular information that's being spread. Now there are researchers that are trying to do this, but that they're caught in the political maw as well, right? Seen as either censoring or favoring one side or the other. It's a really hard thing to unwind.
[00:14:00] And of course our adversaries are getting better at it and hiding their tracks. So you think back to, you know, Russia's early efforts to interfere with a presidential election. And, uh, we may have talked about this in the last time I came on. You know, you could easily trace it back after the fact to Facebook groups that were created by Prigozhin in St. Petersburg in an office with trolls that, you know, came to work nine to five and they masqueraded as Americans trying to get followers and getting Americans to be pitted against each other. Not just online, but in real life, right? On the streets of Texas, protesting against each other, all fomented by the Kremlin.
[00:14:40] Now it's a lot harder. And, you know, you think about TikTok, for example, the Chinese don't need the Russian playbook, which is utilize American platforms against ourselves. They have their own platform. Directly into the hands of forty percent of Americans, which is why there's been this whole bruhaha about banning TikTok or forcing a sale of TikTok. It is a legitimate national security concern.
[00:15:04] Russ Altman: Great. Okay. Now there's something juicy and meaty we can talk about. So there are these big tech companies and uh, TikTok is a great example because I have graduate students who are ready to hit the streets in protest if, uh, if TikTok is shut down, because it evidently has become a huge part of their life. Um, so talk to me about your perception of the real risks of TikTok, uh, versus kind of manufactured political rhetoric that you think is not so beefy.
[00:15:35] Amy Zegart: So I will say, and I mentioned this to General Nakasone when he was the head of Cyber Command and the National Security Agency, that, um, we were talking about our kids, I said, you know, I have a college daughter, and she runs her team's TikTok page, right?
[00:15:47] Russ Altman: Right, exactly. There you go.
[00:15:49] Amy Zegart: How do you, and you know, and I had to send a note to the parents saying, hey, if you want to know what your kids are up to on TikTok, uh, you can take a look, but I have to tell you it's a national security threat.
[00:16:00] Russ Altman: Oh my god. Oh, what a great message that would have been to get.
[00:16:03] Amy Zegart: So it was a bit of an awkward position to be in. So yes, I hear what you're saying, particularly young people, they get their news from TikTok. TikTok is a very big part of their life. So why do we care so much?
[00:16:15] Russ Altman: They'll ask me, what's email? What's Instagram? Facebook is for my grandmother. It's all about TikTok. And they also say, just be, sorry to interrupt you. They also say, and these are my technical students, my computer science, or they say that we don't know how their algorithm works, but it is light years better than all the other algorithms in terms of putting things in front of me that I find interesting.
[00:16:37] Amy Zegart: Yeah. And by the way, that's one of the reasons China may not want to actually divest TikTok to an American buyer because they don't want that IP, that algorithm to be in foreign hands.
[00:16:49] Russ Altman: Yes, it seems to be magically good.
[00:16:50] Amy Zegart: So this dilemma, the U.S. is trying to force a sale. China doesn't want to sell. It's going to be very interesting to see what happens.
[00:16:57] But back to your question about what's the real national security concern about TikTok? There are several. Number one, access to data. So TikTok executives have been saying, no, no, no, no, no. There's a firewall between American data and Chinese access to the data. That is not true. Right? We know empirically that is not true.
[00:17:17] So data on a hundred and seventy million Americans can be accessible by Chinese owners of this company. And we know the national security law in China mandates that companies turn over data when asked.
[00:17:31] Russ Altman: Is this data generated within the app or is this even other stuff on your phone that can be grabbed?
[00:17:37] Amy Zegart: That I don't know.
[00:17:39] Russ Altman: Okay, but it's at least what I'm watching on TikTok, what I'm typing into TikTok, maybe where I am, if there's geolocation. I don't know if there's geolocation on TikTok.
[00:17:48] Amy Zegart: So let me put it to you this way, Russ. Imagine the U.S. government had the ability to reach into the phones of forty percent of citizens in China. And know with the algorithm what gets their attention, what they like and what they don't. How much would we pay to have that kind of access to the populace of a foreign country?
[00:18:10] Russ Altman: And that's what they have.
[00:18:11] Amy Zegart: That's what they have, right? That's what our kids and your students have. So that's issue number one is access to the data.
[00:18:19] Number two is influence. So it doesn't have to be a heavy handed, the Chinese Communist Party is great kind of TikTok algorithm, right? Where you're, you know, the viewers or my daughter is suddenly watching this. It can be things at the margin, right? You probably saw the story about Osama Bin Laden really had legitimate grievances when he masterminded the nine eleven attack.
[00:18:42] Just horrifying things. But on TikTok, this messaging went viral. Now, I don't know whether this was deliberately put there, right, by, in a deliberate effort by a foreign adversary, but you can see how ideas, if a government wanted to influence opinion on issues, uh, it would be pretty easy to do.
[00:19:03] Russ Altman: Yeah, and your point is a really good one, that these can be nudges and not bludgeons.
[00:19:07] Amy Zegart: Right.
[00:19:08] Russ Altman: And actually nudges are probably more insidious and difficult to find and are way less detectable.
[00:19:15] Amy Zegart: That's a better way of putting it than what I just said. Yes.
[00:19:17] Russ Altman: This is The Future of Everything. I'm Russ Altman. We'll have more with Amy Zegart next.
[00:19:36] Welcome back to The Future of Everything. I'm Russ Altman, your host, and I'm speaking with Amy Zegart from Stanford University.
[00:19:42] In the last segment, Amy described to us some of the changes that have happened since we last spoke with her in cybersecurity threat assessment and also response. In this segment, we're going to talk about the role of corporations. They have more compute power, not only more than academics. In many cases, they have more than the government has to use in building AI tools. This has created new challenges for regulation and for collaboration between industry and government and academics.
[00:20:11] Amy, to start off this segment, I wanted to ask you about the role of corporations. We talked about it a tiny bit when we're talking about the SEC regulations, but there are these big tech companies that are really holding AI and controlling AI. What is the role of the corporation in national security these days?
[00:20:28] Amy Zegart: Well Russ, the role of the corporation is totally different than it was when we were growing up. So it used to be that innovations were invented in the government and then they became commercialized, right? You think about the internet started that way, or GPS satellites. And now the script has flipped. So now innovations, and we see this with large language models, are being invented outside of the government, and the government has to figure out not only what to do about that in the private sector, but how to bring those capabilities into the government itself.
[00:20:57] That's a new world for them. We're in a world right now where a handful of companies really dwarf the capacity of the government or universities to, uh, to compete and understand these large language models.
[00:21:12] Russ Altman: And there is no way that me and my friends could have built ChatGPT. We don't have a tenth of the compute power we would need.
[00:21:21] Amy Zegart: And I think Russ, many people don't know that, right? So the orders of magnitude of compute power, right? So how much more compute power does OpenAI have than Stanford, for example? I mean, you know, it's, you know, you probably don't have,
[00:21:37] Russ Altman: It's ten to a hundred, it's a hundred X. It's a hundred X.
[00:21:40] Amy Zegart: So I was trying to find a specific number cause I'm writing about this now. And I saw an announcement that Princeton is buying, is very excited, that they're buying three hundred NVIDIA chips by the end of the year. Meta is expected to have three hundred and fifty thousand, right? So,
[00:21:59] Russ Altman: So it's a thousand X. I was off by an order of magnitude. You're right.
[00:22:03] Amy Zegart: And so what that means is that these companies are not just at the forefront of innovating, they're grading their own homework, right? Because how do you know what's safe? How do you know what potential risks there are? What kinds of questions do you need to ask? They're deciding those things largely by themselves, and that's never a good setup. I would say that, but I also want to emphasize that we don't want to impede innovation.
[00:22:26] So the question is, how do you strike the right balance between mitigating harms from these AI models. And how do you make sure that we're allowing the private sector leaders in this space, and they are all American at this moment, to continue innovating in ways that help, you know, there's so many positive benefits to these models as well. So we don't want to impede that either.
[00:22:47] Russ Altman: So what is the approach? I mean, is it now requiring government to have some kind of super awkward type of conversations that it's not used to having where it's kind of, it has to be a little bit more humble, perhaps, and come to the companies and say, hey, could we work together?
[00:23:04] I mean, first of all, I presume that they're a part of the national security infrastructure. We would want to use many of those technologies to combat, uh, threats. On the other hand, um, they're not under the control of the government and they might say things like, who's going to pay for that? Or, you know, how much should the license that the government pays us, how much should that cost? And so, how far are we at figuring out how this new dance should be danced?
[00:23:30] Amy Zegart: Well, you know, we just talked about cyber and how long it took to sort of get the maturation of cyber organization in the U.S. government. We're on day one for AI. So we are not far along at all. Yes, there are awkward conversations. You can see them on television when Sam Altman goes to testify before Congress. You know, many members of Congress are learning how to spell AI. So we have a, we have an expertise challenge there too. So at one point I counted the number of members of Congress that had engineering degrees. I think it was in 2020.
[00:24:00] You will be unsurprised to know more than half the Senate had law degrees. And there were, I think, three engineers. Which is actually more than I thought there would be. So that's part of the challenge too, is, you know, ordinary folks don't know enough to be able to ask the right oversight questions.
[00:24:16] Russ Altman: So here's overly optimistic Russ's next question. Did we learn from cyber so many lessons that AI is going to be easier? Based on the cyber experience, or are we basically starting from scratch?
[00:24:28] Amy Zegart: I think I'm trying to be optimistic. I'm trying to get your optimism, Russ. Yes, we have learned some lessons. You can see efforts early on at conversation, both on the private sector side. They know they've got this powerful technology and they're concerned about the risks. I don't want to overstate.
[00:24:45] Russ Altman: They want to be patriots to some degree, I would guess, slash hope.
[00:24:49] Amy Zegart: And they know that what they have has great promise and also great peril and trying to harness the upside while mitigating the downside is in everybody's interest.
[00:24:58] So those conversations are happening. We don't have the Edward Snowden problem. So you remember in 2013, former NSA contractor revealed highly classified programs, and it really sowed distrust, deep distrust between companies here in the Valley and the government. We don't have that right now.
[00:25:15] Thanks to Xi Jinping and Vladimir Putin there's a joint concern about authoritarians in the world and the bad they can do. So that's good. We have learned from that, but you know, there is this question of what do we do, given that there's just this capacity differential between talent and compute and algorithms and a handful of companies and what everybody else can do.
[00:25:38] And I think we have three options. One is regulation. I'm concerned about that because you can really, you know, uh, throw the baby out with the bath water. Two is do nothing, let them grade their own homework. That concerns me too. What happens if, uh, people violate OpenAI's rules in the presidential election? They, they go to OpenAI jail, right? I mean, it's voluntary compliance.
[00:25:59] Russ Altman: No chat for you.
[00:26:01] Amy Zegart: So that's the world we're in right now. And then the third option, I think this is what we really need to pursue much more seriously is developing independent capacity. Developing the talent, developing the compute thing.
[00:26:15] I know Stanford's been really pushing this idea of a national AI research resource. That's fancy talk for compute power so that independent researchers can ask hard questions, uh, and do the kind of analysis that, that needs to be done. I think we need to be investing much more in that. Compute is a strategic national asset like oil and the government should be investing orders of magnitude more and making that available.
[00:26:44] Russ Altman: You know, as a biomedical researcher, I'm very aware of this because whenever, for example, the drug industry gets out ahead of NIH researchers, the NIH has a history, and I've seen this several times in my career, of making huge investments to try to level the playing field so that academic can kind of not really compete with the pharmaceutical industry. But do things at the same scale.
[00:27:05] And I'm somewhat surprised to not have seen a government scale, uh, AI resource that's as big as Facebook's or OpenAIs or Anthropics or, it's just surprising because the government can definitely afford it. Yes, it's expensive, but you know, the government has a bigger budget than Facebook even and so it's just surprising and maybe we'll see this.
[00:27:27] Um, let me just ask you, you mentioned about regulation. I'm sure you have opinions about the Europeans. As you know, the Europeans have been very aggressive at um, kind of AI and data protections. What's your take on that in terms of the security implications? Is that a model that the U.S. should seriously look at? Or do you have concerns about how they've approached it?
[00:27:47] Amy Zegart: I understand where they're coming from, and the Europeans share our values. And so I think that the impetus, I understand. I think their hearts in the right place, but I don't think it's a coincidence that the leading AI companies in the world are not coming out of Europe.
[00:28:01] They're coming out of the United States. Our, you know, wild west approach to innovation, hands off regulation is both a feature and a bug, right? It is what is fostering this innovation explosion that we've had for a long time. But it also means that we have a harder time mitigating the harms. So what I think is most promising and what the Europeans have done, two things.
[00:28:26] One is starting an international conversation about norms. That's really important. Ultimately, I think that we also need a serious bilateral conversation about AI guardrails between the U.S. and China. Things like AI and nuclear command and control, AI and financial system security, things where we have mutual interests, we need to have that.
[00:28:48] But the multilateral approach is important, too, for building norms about what's acceptable and what isn't. The second thing the Europeans are doing is the UK has really taken the lead on their AI Safety Institute. Independent capacity building to really understand what the risks of this technology could be.
[00:29:06] Now it's a beginning, it's not an end. The United States is behind. We're behind in our organization. We're behind in our funding compared to the Brits. And as you probably know, now there's conversation about how can we join our efforts together. And I think that's very promising.
[00:29:21] Russ Altman: Great. So to finish up. How is AI going to help intelligence? Like, I know that the bad guys might use AI as well, but what are some of the ways, like, kind of tangible ways that we should be excited about AI helping increase our security and safety?
[00:29:36] Amy Zegart: So, I do think there is some good news of the potential of AI. So, it can help intelligence in a number of ways.
[00:29:43] First, you have to think about intelligence isn't really about secrets, it's about insight. So the question is, how can analysts sitting inside the Central Intelligence Agency better develop insight about what's going on around the world? Well, what can AI do? AI can do pattern recognition at scale and speeds that humans cannot.
[00:30:02] So you think about an analyst, there was actually an experiment done several years ago by the National Geospatial Intelligence Agency. And they had a human team and an AI team looking at identifying surface to air missile sites over a huge swath of territory. The humans and the algorithms did the, had the same level of accuracy, ninety percent accuracy, but the AI did it eighty times faster.
[00:30:28] What does that mean? Now you're freeing up the human analysts to do things that only humans can do well, like thinking about intention. What does the adversary intend to do with those surface to air?
[00:30:40] Russ Altman: Why are they pointing in that direction?
[00:30:42] Amy Zegart: Why are they pointing in that direction? Yeah. So, so incredible efficiency gains, right?
[00:30:46] Pattern recognition. That's thing one. Thing two is AI can help find needles in haystacks. Much better than humans can pouring over images or pouring over data. And the third thing that AI can do, is AI can derive insight from the haystacks themselves. So I think about in your world, AI, um, accelerating scientific discovery, the new antibiotic at MIT, that's finding insight from mounds and mounds of data, all the haystacks, connections that humans didn't even know existed. AI can help with that.
[00:31:23] Russ Altman: Thanks to Amy Zegart, that was The Future of Cybersecurity. Thanks for tuning into this episode. With over 250 episodes in our archive, you have instant access to an extensive array of fascinating discussions on the future of pretty much everything. Please remember to hit follow in the app that you're listening to now.
[00:31:41] This will guarantee that you never miss out on the future of anything. You can connect with me on x or twitter @rbaltman. You can connect with Stanford Engineering @stanfordeng.

The future of robotics

Regenerating worms have genetic control over their algal partners

Understanding how racism and emotion impact affordable housing support
- ISI Media Relations
Information Sciences Institute
Networking & cybersecurity, research areas.
Networking is the backbone of the interconnected world, and cybersecurity is its guardian. The researchers, faculty, Ph.D. students, and student workers in the Networking and Cybersecurity Division focus on the following research areas:
Areas of Research
Cyber experimentation research, methods, and infrastructure, network measurement, analysis, and defenses, security for wireless networks, networking consensus algorithms, cyber-physical systems and autonomy.
- Understanding Communication for Human-focused Problems
- Human Behavior for Cybersecurity
Catalyzing a robust ecosystem of experimental infrastructure, capabilities, and communities by creating models, frameworks, testbeds, tools, and approaches to enhance the science of cyber experimentation and make the experiments rigorous, reusable, and repeatable.

The Internet – the largest, most complex object ever made by humans – is self-evolving, constantly changing, and poorly understood. Novel internet measurement techniques, tools, and data inform understanding and benefit technical developers, social scientists, government policymakers, and observers worldwide. Measurement is complemented by the application of formal methods and temporal logic, for operational identification of attack dependencies and descriptions of traffic behaviors; and by machine learning, for classification and quantification of privacy leaks.
Significantly improving the security of wireless networks, including 5G and next-generation mobile networks, through research into novel network embedding techniques, constraints validation, and protection of information in transit, and from direct and side-channel attacks. The application of machine learning assists identification of applications based on their network traffic, and the application of advanced network mapping capabilities identifies the current state and structure of the network between communicating entities.

Researching algorithms for blockchain consensus and smart contracts, federated learning, privacy preserving computations and linkage of data; and their application to financial transactions, medical data records, and 5G/edge compute environments.
Safety-critical autonomy hinges on verifying the underlying controller software against a domain application's safety and security requirements. Modeling and understanding the semantics of cyber-physical systems (e.g., space, energy, medical, automotive) to understand how the software will interact with higher-level, human-understandable physical models, operate in mission-critical zero trust environments, and interoperate with legacy systems. We tie in the semantics of cyber-physical behavior, to formally verify whether software control adheres to safety constraints.

Understanding Communication for Human-focused Agents
Automated comprehension of human language enables better communication between humans and computers. Our research explores enabling better communication between humans and computers through automated comprehension of multimedia data, effective use operator feedback for learning, and determining proper representations of objects and actions.
Modeling Human Behavior for Cybersecurity
Social engineering attacks pose an increasing threat. Our work develops methods for detecting and fingerprinting attack campaigns by leveraging metadata from communication channels and employing novel techniques to redirect attackers. We also apply the DASH agent simulation platform to combine observational data with cognitive models of behavior at the scale of millions of individual agents.

- भारत सरकार GOVERNMENT OF INDIA
- विज्ञान और प्रौद्योगिकी मंत्रालय MINISTRY OF SCIENCE AND TECHNOLOGY
- Screen Reader Access

Search form

विज्ञान एवं प्रौद्योगिकी विभाग

- Home >>
- ICPS Home >>
- Basic Research in Cyber Security >>
- ICPS Research
- Data Science Research Initiative
- Internet of Things (IoT) Research Initiative
Basic Research in Cyber Security
- Indian Heritage in Digital Space Research
- Detailed Call for proposals Last Date: 31/03/2017
- General Guidelines
- People @ ICPS Division
- Application Formats
Cyber is a prefix derived from the word cybernetics and has acquired the general meaning of through the use of a computer which is also termed as cyberspace. The word security in general usage is synonymous with being safe, but as a technical term security means not only that something is secure, but that it has been secured. Joining the two words together form the word cybersecurity is concerned with making cyberspace safe from threats, namely cyber threats. The information and communications technology (ICT) industry has evolved greatly over the last half century. With the advent of the internet, security becomes a major concern. ICT devices and components are generally inter dependable and vulnerable to the security attacks. The act of protecting ICT systems and their contents has come to be known as cybersecurity. Cybersecurity is an important tool in protecting and preventing unauthorized surveillance. As commonly used, the term cybersecurity refers to three things:
• A set of activities and other measures, technical and non-technical, intended to protect computers, computer networks, related hardware and devices software, and the information they contain and communicate, including software and data, as well as other elements of cyberspace, from all threats, including threats to the national security. • The degree of protection resulting from the application of these activities and measures. • The associated field of professional endeavor, including research and analysis, aimed at implementing and those activities and improving their quality
To secure a computer system, it is important to understand the attacks that can be made against it, and these threats can typically be classified as below (from wikipedia);
Backdoor attacks Denial of service attack • Direct Access attack • Eavesdropping • Spoofing • Phishing
Technology for cybersecurity • Cryptographic systems : A widely used cybersecurity system involves the use of codes and ciphers to transform information into unintelligible data. • Firewall : Use to block traffic from outside, but it could be also used to block traffic from inside. • An Intrusion Detection System (IDS): IDS is an additional protection measure used to detect attack. • AntiMalware Software and scanners : Viruses, worms and Trojan horses are all examples of malicious software, or Malware for short. Special so called antiMalware tools are used to detect them and cure an infected system. • Secure Socket Layer (SSL) : It is a suite of protocols that is a standard way to achieve a good level of security between web browser and websites. • Research Areas in cyber Security [17,18, 19, 20] • Identity, Privacy and Trust Management • Malware • Biometrics. • Cloud Security • Computer Forensics • Data protection legislation and security • Cryptography and Formal Methods
The cyber security research initiative is an attempt to define a national R&D agenda that is required to enable the country to get ahead of adversaries and produce the technologies. These futuristic technologies can protect information systems and networks. The research, development, test, evaluation and other life cycle considerations required are far reaching from technologies that secure individuals and their information to technologies that will ensure National Critical Infrastructures are much more resilient [17][18]. The R&D investments recommended in this initiative must tackle the vulnerabilities of today and envision those of the future. The initiative is a platform to work together to foster R&D to evolve transformative solutions and address critical cyber security challenges, through partnerships among academics, Industry and Govt.
Broad research areas 1. Information Security 1. Computer Network Security 2. Application Security 3. Web Services Security 4. Mobile Security 5. Protective Security 6. Software Security 7. Wireless & Sensor Network Security 8. Software Coding Security 9. Data Capturing devices and Security 10. Security in Middleware, Interface and Interaction 11. Security Services in Authentication, Authorisation, Accountability, Automation, Availability, Integrity and Non-repudiation 12. Security Management 13. Security Operations 14. Digital Trust and Reputation 15. Spatial Location (Geo-location) and Cyber Travel 16. spatial Intelligence Networks (Centralised, Distributed & Hybrid) 17. Policy, Legal, Legislation & Compliance 18. Security Standardisation 19. Law, Legal and Ethical issues
2. Digital Services 1. Web Services, Internet Banking, E-Booking 2. E-Government, Electronic Commerce 3. Citizens Public Online Services 4. Mobile Commerce 5. E-Postal Services, E-Health, E-Learning and Online & Virtual Education 6. Secure Protocols, Coding and Development 7. Security Principles, Theory and Analysis 8. Security Policy, Standards and Procedures 9. Security in Business Processes 10. Security Enforcing Function (SEF) Gateways 11. Intrusion Detection Systems 12. Intrusion Prevention Systems 13. Firewalls & Spam identification and protection 14. Anti-Virus and Anti-Malware Gateways 15. Data Loss Prevention and Encryption Services 3. Protection of Digital Services 1. Protection of Business Information Systems 2. Protection of Online Services 3. Public Online Services 4. Internet Banking 5. Security, Trust, Privacy 6. Security in Online Gaming Systems 7. Security in e-Government and Electoral Systems 8. Content Security 9. Protection of Public Online Content Distribution Systems 10. Secure practices, processes and procedures in Public Online Services 11. Cryptography -PKI, HSMs, Symmetric and Asymmetric Crypto, Crypto Custodian & Crypto Standards and Practices 12. Digital Forensics and Investigations 13. HoneyPots and Honey Nets 14. National Information Infrastructure (NII) protection 15. National Critical Infrastructures (NCI) protection 16. Critical Network Systems (CNS)
Related Organization
Miscellaneous.


Discovering the SoURCE of Cyber-Attacks
Cyber-attacks on individuals or organizations can be devastating. They may result in the loss of private personal information, the theft of proprietary company or financial data, and/or the release of organizational secrets.
The number and scope of cyber-attacks have increased exponentially over the years. For example, according to one study, there were 38 percent more cyber-attacks in 2022 than in 2021 1 , with each data breach costing critical infrastructure organizations—e.g. financial services, energy, transportation—millions of dollars to rectify.
As cyber-attacks grow and become more sophisticated, efforts to staunch data cyber-bleeding, as it were, have become equally urgent for both the private and government sectors.
For the Intelligence Community (IC), the need to prevent cyber-attacks and identify cyber-attackers is critical, as the loss of sensitive or classified information can have devastating or even life-threatening consequences.
This is why the Intelligence Advanced Research Projects Activity (IARPA) is working on a solution with its latest program, Securing Our Underlying Resources in Cyber Environments, or SoURCE CODE . The SoURCE CODE program seeks to provide novel technologies to assist forensic experts in making determinations of the most likely attackers, based on coding styles in both source code and binary executables.
The program will explore binary executables and source code files to measure the similarity between files and provide forensic experts with information on an attacker’s likely origins (country, groups, individuals, etc.). This capability will help automatically match similar binaries from known samples, allowing analysts to more rapidly attribute malicious attacks.
IARPA envisions the technology playing an integral part in cyber-defense postures of both the commercial threat intelligence space and within the IC, according to SoURCE CODE Program Manager, Dr. Kris Reese.
“Once fully developed, SoURCE CODE will be a vital supporting tool for forensic experts in both commercial and governmental positions.” Dr. Reese said. “As a result, SoURCE CODE will make it more difficult for cyber-criminals to operate without detection and remain anonymous.”
The SoURCE CODE program is anticipated to be a 30-month effort, comprised of two phases. Phase one will be 18 months in duration and phase two will last 12 months.
Phase one’s goal is to develop new methods to identify cyber-attackers by conducting foundational research on different approaches, theories, and concepts to establish the building blocks of their SoURCE CODE system(s). During phase two, performers will seek to extend the capabilities developed in phase one and work across both the source code forensics and binary forensic domains. Program phases are designed to test performer systems against increasingly challenging scenarios.
SoURCE CODE performers, although not yet selected, will be expected to have a deep background in computer science, data science, and cyber-forensics research. Testing and evaluation of the performers’ systems will be conducted by IARPA’s partners at Sandia National Laboratory, Lawrence Livermore National Laboratory, and the Software Engineering Institute.
“This is of course a challenging field of study, and attribution of attacks goes beyond simply similarity matching—into domains AI may have difficulty understanding,” Dr. Reese said. “However, the potential for SoURCE CODE to improve forensic capabilities will contribute to a better understanding of cyber-attack origins and advance the IC’s mission.”
1 Check Point Research Reports a 38% Increase in 2022 Global Cyberattacks - Check Point Blog


Published: 16 May 2024 Contributors: Matthew Finio, Amanda Downie
A cyber range is a virtual environment for cybersecurity training, testing, and research that simulates real-world networks and cyberattacks .
Cyber ranges are modern battlefields for cybersecurity. Much like traditional shooting or military ranges that act as proving grounds for marksmanship and combat skills, cyber range platforms provide users with a safe environment to practice responding to real-world cyber challenges. Within a secure and controlled setting, cyber ranges simulate complex networks and threats for cybersecurity training, allowing participants to learn and refine their strategies for defending against digital attacks. These training exercises offer realistic, real-time scenarios without putting actual systems at risk.
Using virtual machines , cyber ranges create realistic training environments that can be easily segmented from other networks such as a corporate LAN or the internet at large. These environments provide a safe space for experimentation and testing various cybersecurity tools and functionality. Target infrastructures within the cyber range mirror actual servers, firewalls, routers, storage devices, and personal computers. This allows users to deploy real-world cybersecurity tools such as penetration testing, intrusion detection systems and digital forensics tools. Participants can also safely practice defending against specific cyberthreats like malware and ransomware .
The NIST Cybersecurity Framework, which was designed by the National Institute of Standards and Technology (NIST), is commonly used in cyber ranges. The NIST framework is a guide based on five core functions—identify, protect, detect, respond, and recover—that provides a structured approach to cybersecurity strategy and risk management. By incorporating the NIST framework into cyber range exercises, organizations can align their training with industry standards and best practices. This offers participants practical, real-world experience and enhances the organizations’ security posture.
A cyber range often features a learning management system (LMS) for organizing coursework and tracking students' progress and performance. Instructors use the LMS to define the curriculum and facilitate communication, assignments, and assessments. By combining advanced technology with targeted learning and testing opportunities, cyber ranges prepare cybersecurity professionals to confront evolving challenges.
There are 4 common types of cyber ranges:
- Simulation ranges replicate the behavior of real-world networks and systems. They use software simulations and provide an efficient, cost-effective environment for training and testing without the need for extensive hardware.
- Emulation ranges mimic the actual hardware and software configurations of a real-world network, offering a high degree of realism for practicing with specific technologies and setups.
- Overlay ranges use real hardware and networks that are overlaid with virtual elements to simulate different scenarios, offering a mix of realism and flexibility.
- Hybrid ranges combine elements of simulation, overlay, and emulation to create a versatile environment that balances realism, cost, and resource efficiency.
Get insights to better manage the risk of a data breach.
Definitive Guide to Ransomware 2023
A cyber range consists of various technical components that work together to create a realistic and controlled environment for cybersecurity training, testing, and research:
A key component, the RLMS combines features of a traditional learning management system (LMS) with the specific needs of a cyber range. It provides educational resources, tracks participants' progress, and manages course curricula and assessments. It also integrates with other cyber range components to create a comprehensive experience.
The orchestration layer coordinates the various technology and service components of the cyber range. It integrates the underlying infrastructure, virtualization, or isolation layers and the target infrastructure. The layer also supports dynamic range extensibility, including compatibility with public cloud, private cloud, and dedicated hard-wired infrastructures.
This infrastructure includes networks, servers and storage, which may consist of physical devices such as switches, routers, firewalls, and endpoints. Many cyber ranges are changing to cloud-based and software-defined virtual infrastructure for scalability, cost-effectiveness, and extensibility. The choice of infrastructure greatly impacts the realism of the range.
Most cyber ranges employ virtualization to reduce the amount of physical equipment needed. This is typically done with hypervisor-based solutions or software-defined infrastructure. Virtualization creates a separation between the physical infrastructure and the simulated environment, which can affect realism and introduce some latency. However, virtualization acts as a protective barrier and helps make cyber ranges more cost effective.
The target infrastructure is the simulated environment where training occurs, sometimes replicating the student's actual IT and security infrastructure. It includes profiles of commercially available servers, storage systems, endpoints, applications, and firewalls. Advanced cyber range platforms might incorporate threat intelligence data and frameworks like MITRE ATT&CK to simulate realistic attack techniques.
The target infrastructure often incorporates the use of red teams and blue teams during exercises. Red teams simulate attackers and attempt to take advantage of vulnerabilities within the environment, while blue teams focus on defending against these attacks.
Cyber ranges were originally used primarily by military and government agencies. They are now used by a broad range of businesses and organizations due to their cost-effectiveness and valuable opportunities to upskill security team members. Cyber ranges offer essential training for various people and groups:
- Bug bounty hunters: Cyber ranges provide bug bounty hunters with a safe environment for researching security issues and discovering new vulnerabilities, helping them find and report bugs to developers and manufacturers.
- Cybersecurity professionals: Security analysts, penetration testers, ethical hackers, and other professionals use cyber ranges to refine their skills. They offer real-world practice, allowing professionals to keep up with emerging threats and learn new defense techniques.
- Government and military and agencies: As some of the first users of the internet, military and government agencies depend on cyber ranges to maintain national defense and data safety. Cyber ranges aid government personnel in handling the latest cyberthreats, including cyber warfare and espionage.
- IoT and smart grid developers: Developers and engineers working on Internet of Things (IoT) devices or smart grid technologies can use cyber ranges to test the security and resilience of their products.
- Organizations and individuals: Companies can use cyber ranges for situational operations testing, training, and assessing candidates for cybersecurity positions. Individuals entering cybersecurity roles can benefit from the workforce training cyber ranges offer.
- Researchers: Academics and researchers can use cyber ranges to study cybersecurity trends, conduct experiments, and test new tools and technologies in a controlled setting.
- Security trainers and educators: Instructors, educators, and facilities such as security operations centers (SOCs) can use cyber ranges as platforms for teaching cybersecurity courses and developing training programs that provide students with practical, hands-on experience.
- Students: Cyber ranges are now a key component of a top-tier cybersecurity education. They provide students pursuing certifications or degrees with practical experience through hands-on labs, enhancing their learning with realistic scenarios.
Cyber ranges are a critical tool for cybersecurity professionals. They offer a safe and controlled training platform for cybersecurity workforce development. Here are several reasons why cyber ranges are important:
- Addressing the talent gap: By offering practical training, cyber ranges help close the skills gap in the cybersecurity workforce by preparing individuals with job-ready skills.
- Continuous learning: Cyber ranges offer on-demand, ongoing opportunities for cybersecurity professionals and students to enhance their cyber skills, keeping them up-to-date with the latest cyberdefense strategies and tools.
- Controlled environment: Cyber ranges provide a safe space for trial and error. This allows for repeated and reusable training scenarios without impacting live systems and enables experimentation and learning without risking damage to real data and networks, helping to prevent data breaches .
- Incident response practice: Participants can practice and refine incident response plans in the range, learning how to use established playbooks and adapt to various threats. This experience enhances their readiness and confidence.
- Keeping up with evolving threats: Cyber ranges allow individuals to stay current with emerging cyberthreats and techniques and prepare them for real-world challenges.
- Performance assessment : Cyber ranges provide metrics and feedback to evaluate individual and team performance. These measurements help identify areas for improvement and enable tailored training for optimal results.
- Realistic training: Cyber ranges use realistic attack scenarios and network simulations in a controlled, safe environment for practicing cybersecurity skills. Trainees develop hands-on experience and confidence in handling real-world threats without the risks that are associated with practicing on live systems.
- Skills development: Trainees can hone their abilities to detect, prevent, and respond to cyberthreats. Cyber ranges help professionals stay updated with the evolving attack methods and defense strategies and help them enhance critical thinking, problem-solving skills, and confidence.
- Team collaboration: Cyber ranges enable teamwork and coordination as participants work together on complex scenarios. This fosters effective communication and teamwork in high-pressure situations and prepares security teams for coordinated incident response.
- Testing and research : Organizations can test new security tools and approaches within a cyber range, developing innovative solutions and assessing their efficacy. This enables safe testing of new technologies and supports ongoing research to improve cybersecurity measures.
Give your team the elite training that they need to improve your readiness to effectively respond to a breach.
Redefine SIEM to unleash analyst potential and outpace adversaries with speed, scale, and accuracy.
Transform your business and manage risk with a global industry leader in cybersecurity consulting, cloud, and managed security services.
Be confident in your security with threat intelligence.
Watch this discussion about the biggest attack trends and methods with key speakers from IBM Security and the FBI.
Learn how Canadian sports and entertainment organization MLSE teamed with IBM to monitor cyberthreats and protect digitally engaged fans.
Read about how Los Angeles teamed with IBM Security to create a first-of-its-kind cyberthreat sharing group.
Learn about the new IBM X-Force Cyber Range in Washington DC that helps federal agencies improve their resilience against evolving threats.
Read about industry leaders’ concerns for the future and three approaches organizations can take to build up their defenses.
IBM X-Force Cyber Range services use immersive simulations to guide your team through realistic breach scenarios, helping you respond to and recover from enterprise-level cybersecurity incidents, manage vulnerabilities and build a stronger security culture in your organization.
The unsolved opportunities for cybersecurity providers
The COVID-19 pandemic has forced rapid changes on corporate cybersecurity functions. Chief information-security officers (CISOs) have had to adjust their strategies to account for remote working, pivoting from working on routine tasks to working on long-term goals of establishing secure connections for remote situations. Managing business continuity has been the goal, with the patching of remote systems over virtual private networks, handling of those systems’ increased workloads, and monitoring of spiking cyberthreat levels and cyberattackers targeting at-home workers with an array of threats. In fact, a McKinsey survey of cybersecurity providers found a near-sevenfold increase in spear-phishing attacks since the pandemic began.
The challenges that face organizations are also forcing cybersecurity providers to pivot, adjusting their strategies and their product and service offerings to meet postpandemic objectives. That must be done in a manner that accommodates the new security landscape but continues to monitor customers’ needs while adjusting sales, service, and training accordingly. The elements that enterprises must secure (data, devices, people, networks, machines, and applications), how they must secure them (prevention, detection, response, and remediation), and why it’s important to secure them (to mitigate loss of lives and livelihoods) continue to evolve, and cybersecurity providers have yet to solve several crucial customer challenges. The stakes have never been higher.
Insights from the results of the cybersecurity-provider survey revealed that CISOs and cybersecurity-operations teams will continue to invest niche spending in the areas of perimeter security, next-generation identity and access controls, remote access, security automation, and security training. With a vast ecosystem of technology platforms and partners, cybersecurity providers will need to differentiate themselves. The research suggests that there remain four unsolved challenges: the visibility gap, fragmentation of technology, the talent gap, and the measurement of ROI. Addressing even one of these challenges can help providers gain a sustainable edge in an ever-evolving, fragmented, and competitive market.
Visibility gap
Without visibility into digital infrastructure, it will be difficult for companies to recognize when, where, or why there is a problem. According to a recent McKinsey survey of approximately 200 buyers of security-operations applications (such as security-information and -event management and security-orchestration, -automation, and -response tools) in the enterprise market (companies with more than 1,000 employees or topline revenue more than $1 billion), around 60 percent of buyers analyze and triage less than 40 percent of their enterprises’ log data. Worse, that figure may be understated: third-party and software-as-a-service log data are often excluded, since they are not prioritized for collection and analysis in many enterprise environments.
Case example: Cybersecurity visibility
Today’s typical enterprise environment, though, can make that necessary visibility difficult (see sidebar “Case example: Cybersecurity visibility”). Chief information officers and CISOs also need to rethink their analytics strategies, with an eye on deploying analytics designed for the volume and nature of today’s data, both structured and especially unstructured.
The best way to begin any compliance or security program is to assure telemetry at the endpoint, thus helping ensure that automated communication processes from multiple data sources are normalized and standardized for faster and more consistent analysis. That element alone can contribute to better customer experience, application health, quality, and performance, in addition to more scrutiny from a security standpoint. The sad truth is that few, if any, enterprises are confident that they have accurate and comprehensive telemetry to detect an intrusion in their environment. In solving the telemetry and visibility gap, cybersecurity providers should perform the following actions:
- Rethink the ‘pay by the drink’ approach (such as pay per log) to volume-based pricing models. Such payment mechanisms are unsustainable at scale for enterprises, particularly when considering an enterprise’s consumption models for cloud architecture and infrastructure. Offerings should be adjusted to solve rate limits of mass data processing at the peta- or terabyte level.
- Identify the missing puzzle pieces to building a 360° view. The security-telemetry implication is often the tip of the iceberg. In many companies, the broader ecosystems for IT- and data-asset management have not matured to keep up with the security approaches. Leading providers will build tooling that can construct an outside-in view of the puzzle and identify the critical missing pieces. Such business-aware, intelligent tooling provides substantial value to a cybersecurity-function because it shifts the conversation with business leaders away from numbers to the value chain and revenue streams of the business. Educating customers on how to plan for cost reduction and be purposeful about which logs they select to ingest, as well as building low-cost data lakes that can affordably collect all logs for pretriage to feed into the system of choice for security-information and -event management, can bridge the gap in the interim. That means that sales engineers, architects, analysts, and other personnel are critical in identifying puzzle pieces that are missing (or redundant) as part of the presales process to demonstrate to security buyers how a technology will close visibility gaps.
- Reduce false positives, forcing the organization to approach cyberthreats proactively, not reactively. The improved use of AI and machine learning provides a holistic view of an entire security program, including on-premises, in the cloud, across geographies, within business units, and from remote networks. Transparency here allows an organization to prioritize potential threats. By reducing false positives, it has a clearer picture of cyberthreats such as vulnerabilities, unpatched systems, and misconfigurations.
Technology-fragmentation challenge
Part of a CISO’s job has an impossibility element. Their teams are supposed to protect against future cyberattacks, with the nature, method, timing, scale, and identity of those attackers unknown. Those frightening unknowns fuel a fear of reducing the number of security applications, even seemingly redundant ones (perhaps obtained through an acquisition), because it’s possible that the targeted app might be the one to save the enterprise.
Enterprises grapple with the timeliness challenge of technology decisions (where and how to balance agile-best integrated options with fragile, fragmented, best-of-breed options), since different technology, applications, and providers are used across an organization. Often, a company may have more than 100 third-party security tools in use. In many cases, that number is driven by the CISO’s expanding mandate—and desire not to be the one who cancels the tool that might prevent the next big breach. There are several key drivers of this security complexity.
The enterprise perimeter has changed in recent years as the paths to access data assets has soared, with no single perimeter existing. The influx of IT functions hosting on-premises, private- and public-cloud environments is upon us. As a result, multi- and hybrid-cloud security will continue to be critical, and CISOs will be willing to pay for increasingly hard-to-find skills (such as mainframe security) from a service provider.
With many industries, the first challenge of operational-technology (OT) security is identifying who “owns” it. Once resolved, the logical next questions follow: Who funds it, who operates it, and what are the intersection points between IT and OT security? A duplication of security controls, policies, frameworks, and vendors across both IT and OT only drives complexity further.
The interlinkages among data governance , data privacy, and cybersecurity have precariously positioned the CISO as the only first-line enforcer amid a second-line function. With the continued expansion of data regulations, data-sovereignty laws, and customer interest in data privacy, the CISO is increasingly asked to add tooling, process, and prioritization to retrofit privacy into security. In many cases, that has led to a proliferation of tooling, such as data classification, data tagging, data-access governance, and privacy management, where the operating model between information security and privacy (compliance concerns) can get blurry.
While CISOs report varying degrees to which they have a seat at the table during M&A, one thing is for sure: after M&A, they will have plenty of cleanup to do. Companies are vulnerable to cyberattacks during acquisitions, which means that the last thing a CISO wants to do is rip and replace the tooling, leaving unknown vulnerabilities exposed. To understand capabilities, cyberthreats, and critical data, integration teams can prioritize a target’s function-specific technology applications by categorizing each. Here lies an opportunity for cybersecurity providers to offer material value.
To help CISOs extract themselves from the “one-way ratchet” that is enterprise cybersecurity tooling today, cybersecurity providers need to perform the following actions:
- Produce offerings that allow for seamless simplification of sprawl. Deploy a product that takes over incumbent functionality, generates data to show the efficacy of the new layer offering (such as recurring money and time saved by rationalizing tooling), and enables the sunsetting of old, legacy approaches.
- Use cloud and software-as-a-service adoption or updates as an opportunity for tool rationalization. Providers must maintain relationships with major cloud platforms, emphasizing native integration with software and platform leaders, as hybrid scenarios with on-premises, public- and private-cloud expand. Many major platform players have invested significantly in managing their relationships with cloud service providers.
- Engage all stakeholders, make business-based simplification decisions, and don’t put all the cybersecurity burden on the CISO. Organizations should empower their CISOs to make risk-based simplification decisions, gaining cross-functional support for key simplification decisions so the burden (and after any incident, the blame) do not rest solely on the CISO.
Cybersecurity-talent gap
With more than 3.12 million jobs in cybersecurity estimated to be unfilled in 2021, 1 “Cybersecurity workforce demand,” US National Initiative for Cybersecurity Education, 2021. the talent shortage is a massive problem, and it’s affecting both clients and providers. The use of technology—primarily AI and its machine-learning offspring—has helped slightly, especially in a security-operations center dealing with an active cyberattack. But the technology is primarily supplementing security analysts, allowing human capacity to be more efficient and to focus more on tasks where their experience and creativity are essential. Addressing the talent gap takes innovation and persistence:
- Recruiting realities. To manage the skill gap, cybersecurity providers may want to focus on offerings that are not as people intensive to deploy and manage or maintain. To remain talent competitive, providers should get creative when it comes to recruiting, training, and retaining talent, such as looking beyond traditional places, finding individuals with similar skills sets that can be trained, looking beyond formal education, and so on.
- More one-shop and full-stack-service providers (such as ‘infra in a box’) . Companies are moving away from the approach of product-delivery deployment and moving toward annual subscription models that include service delivery.
- Impact of delivery preferences on customers’ key buying factors. Delivery preferences are critical. For example, the rate of false positives has historically been a top buying factor in several security-product markets, for a logical reason: the more false positives, the more frustration and manual effort for security-operations teams to trudge through every day. However, as the delivery of those products has shifted to a service-driven approach, buyers care less about false positives because they no longer see level-one and -two data. Instead, the triage stage is outsourced almost entirely by the product provider’s service team. Buying preference moves farther right along the value chain to the value and actionability of the intelligence, response time, and so on.
Cybersecurity’s ROI
The most successful cybersecurity program is one that no one notices and that enables the underlying business to function unhindered. Organizations today struggle with understanding how to measure the return or value of a dollar spent on cybersecurity, as well as how to communicate its value to internal stakeholders, such as C-suite and board members. Providers should structure their output, reporting, and dashboards to speak to business audiences, as well as technical audiences. Provider solutions should take credit for all their accomplishments.
If an industry is not implementing the right cybersecurity programs and therefore spending less than their needs demand, there is no comfort in looking at its neighbors from a comparison standpoint. Maturity in no way guarantees resilience, but it does help define and measure ROI appropriately. To have a true security proposition, there are at least three dimensions that the cybersecurity provider community should consider:
- Business value. Do the organization’s security offerings reflect the priorities of its customers’ businesses today? When those business priorities change, can its security program adjust its priorities effectively? When there’s a crisis, can it quickly map online services to business processes?
- Customer value. Does the customer see the organization’s security capabilities as a differentiator? Do they know it is managing top risks?
- Market value . Do external stakeholders, including investors, vendors, and third-party supply chains, understand the organization’s security journey and the impact of the security team over time? Are security capabilities included as part of the company’s valuation? How does the organization talk about security to “the Street”?
Continuing to evolve
For cybersecurity providers, the ability to offer customers real-time technology and services that speak to the business, not only the CISO, is crucial. They also need to demonstrate the right value and key performance indicators to measure outcomes, which is the first step on the journey to helping its customers differentiate as security-minded businesses.
Case example: Cybersecurity trust
The four challenges detailed in this article can be solved, and a wait-and-see approach is not advised. It is important to realize that the challenges are fundamental to the industry and to define the constraints within which the industry operates. Executives must be cognizant of such issues, as well as try to solve them. But most importantly, cybersecurity professionals need to be open and transparent about them with internal stakeholders, working in collaboration to solve each challenge (see sidebar “Case example: Cybersecurity trust”).
From a go-to-market perspective, cybersecurity vendors that can appeal to business, functional, and technology executives alike will have more success in becoming household names.
Explore a career with us
Related articles.

Organizational cyber maturity: A survey of industries

Building cyber resilience in national critical infrastructure

Enterprise cybersecurity: Aligning third parties and supply chains
Language selection
- Français fr
WxT Search form
Sensitive technology research areas, pdf version.

358 KB , 16 pages
Introduction
The list of Sensitive Technology Research Areas consists of advanced and emerging technologies that are important to Canadian research and development, but may also be of interest to foreign state, state-sponsored, and non-state actors, seeking to misappropriate Canada’s technological advantages to our detriment.
While advancement in each of these areas is crucial for Canadian innovation, it is equally important to ensure that open and collaborative research funded by the Government of Canada does not cause injury to Canada’s national security or defence.
The list covers research areas and includes technologies at various stages of development. Of specific concern is the advancement of a technology during the course of the research . This list is not intended to cover the use of any technology that may already be ubiquitous in the course of a research project. Each high-level technology category is complemented by sub-categories which provide researchers with further specificity regarding where the main concerns lie.
The list will be reviewed on a regular basis and updated as technology areas evolve and mature, and as new information and insights are provided by scientific and technical experts across the Government of Canada, allied countries, and the academic research community.
top of page
1. Advanced Digital Infrastructure Technology
Advanced digital infrastructure technology refers to the devices, systems and technologies which compute, process, store, transmit and secure a growing amount of information and data that support an increasingly digital and data-driven world.
Advanced communications technology
Technologies that enable fast, secure and reliable wireless communication to facilitate growing demand for connectivity and faster processing and transmission of data and information. These technologies could also enable communications in remote environments or adverse conditions where conventional methods are ineffective, or in spectrum-congested areas. Examples include: adaptive/cognitive/intelligent radios; massive multiple input/multiple output; millimeter-wave spectrum, open/virtualized radio access networks, optical/photonic communications and wideband high frequency communications.
Advanced computing technology
Computing systems with high computational power that enable the processing of complex calculations that are data- or compute-intensive. Examples include: context-aware computing, edge computing, high performance computing and neuromorphic computing.
Cryptography
Methods and technologies that enable secure communications by transforming, transmitting or storing data in a secure format that can only be deciphered by the intended recipient. Examples of emerging capabilities in cryptography that may replace or enhance current encryption methods include: biometric encryption, DNA-based encryption, post-quantum cryptography, homomorphic encryption and optical stealth encryption.
Cyber security technology
Technologies that protect the integrity, confidentiality and availability of internet-connected systems, including their hardware, software, as well as data from unauthorized access or malicious activities. Examples include: cyber defence tools, cross domain solutions and moving target defence technology.
Data storage technology
The methods, tools, platforms, and infrastructure for storing data or information securely in a digital format. Examples include: five-dimensional (5D) optical storage, DNA storage, single-molecule magnets.
Distributed ledger technology
Digital ledgers or databases that track assets or records transactions in multiple locations at the same time, with no centralized or single point of control or storage. Examples include: blockchain, cryptocurrencies, digital currencies and non-fungible tokens.
Microelectronics
Microelectronics encompasses the development and manufacturing of very small electronic designs on a substrate. It incorporates semiconductors as well as more conventional components such as surface mount technology with the goal of producing smaller and faster products. As microelectronics reach the limit for integration, photonic components are making their way into this field. Examples of semiconductor components include: memory-centric logic, multi-chip module, systems-on-chip and stacked memory on chip.
Next-generation network technology
Fifth and future generations of communications networks that use high frequency spectrums to enable significantly faster processing and transmission speeds for larger amounts of data. Advancements in networking could allow for integrated communication across air, land, space and sea using terrestrial and non-terrestrial networks, as well as increased data speed and capacity for network traffic. It could also pave the way for new AI- and big data-driven applications and services, and its massive data processing capabilities could enable the Internet of Everything.
2. Advanced Energy Technology
Advanced energy technology refers to technologies and processes that enable improved generation, storage and transmission of energy, as well as operating in remote or adverse environments where power sources may not be readily available, but are required to support permanent or temporary infrastructure and power vehicles, equipment and devices.
Advanced energy storage technology
Technologies that store energy, such as batteries, with new or enhanced properties, including improved energy density, compact size and low weight to enable portability, survivability in harsh conditions and the ability to recharge quickly. Examples include: fuel cells, novel batteries (biodegradable batteries; graphene aluminium-ion batteries; lithium-air batteries; room-temperature all-liquid-metal batteries; solid-state batteries; structural batteries) and supercapacitors (or ultracapacitors).
Advanced nuclear generation technology
New reactors and technologies that are smaller in size than conventional nuclear reactors and are developed to be less capital-intensive, therefore minimizing risks faced during construction. Examples include: nuclear fusion and small modular reactors.
Wireless power transfer technology
Enables the transmission of electricity without using wire over extended distances that vary greatly and could be up to several kilometres. Examples include recharging zones (analogous to Wi-Fi zones) that allow for electric devices, such as vehicles, to be recharged within a large radius, as well as for recharging space-based objects, such as satellites.
3. Advanced Materials and Manufacturing
Advanced materials.
Advanced materials refer to high-value products, components or materials with new or enhanced structural or functional properties. They may rely on advanced manufacturing processes or novel approaches for their production.
Augmented conventional materials
Conventional materials such as high strength steel or aluminum and magnesium alloys – products that are already widely used – which are augmented to have unconventional or extraordinary properties. Examples of these properties could include improved durability or high temperature strength, corrosion resistance, flexibility, weldability, or reduced weight, among others.
Auxetic materials
Materials that have a negative Poisson’s ratio, meaning that when stretched horizontally, they thicken or expand vertically (rather than thinning as most materials do when stretched), and do the opposite when compressed horizontally. These materials possess unique properties, such as energy-absorption, high rigidity, improved energy/impact absorption and resistance to fracture.
High-entropy materials
Special materials, including high-entropy alloys, high-entropy oxides or other high-entropy compounds, comprised of several elements or components. Depending on their composition, high-entropy materials can enhance fracture toughness, strength, conductivity, corrosion resistance, hardness and other desired properties. Due to the breadth of the theoretically available combinations and their respective properties, these materials can be used in several industries, including aerospace. Additionally, high-entropy oxides are being considered for applications in energy production and storage, as well as thermal barrier coatings.
Metamaterials
Structured materials that are not found or easily obtained in nature. Metamaterials often have unique interactions with electromagnetic radiation (i.e. light or microwaves) or sound waves.
Multifunctional/smart materials
Materials that can transform in response to external stimuli (e.g. heat, water, light, etc.) within a given amount of time. Examples include: magnetorheological fluid, shape memory alloys, shape memory polymers and self-assembled materials.
Nanomaterials
Nanomaterial materials have dimensions of less than 100 nanometers and exhibit certain properties or unique characteristics such as increased durability or self-repair. A subset of nanomaterials, nano-energetic materials are energetic materials synthesized and fabricated at the nano-level that have a small particle size and high surface area between particles, which enable faster or more efficient reaction pathways when exposed to other substances.
Powder materials for additive manufacturing
Powders that typically consist of metal, polymer, ceramic and composite materials. These powders enable additive manufacturing processes, also referred to as 3D printing. Research into novel powder materials can lead to manufactured parts with enhanced mechanical properties and other desired characteristics.
Superconducting materials
Materials that can transmit electricity with no resistance, ultimately eliminating power losses associated with electrical resistivity that normally occurs in conductors. Manufacturing of superconducting electronic circuits is one of the most promising approaches to implementing quantum computers.
Two-dimensional (2D) materials
Materials with a thickness of roughly one atomic layer. One of the most well-known 2D materials, for which there are currently production/fabrication technologies, is graphene. Other examples of 2D materials include: silicene, germanene, stantene, metal chalcogenides and others, which are currently being researched with potential applications in sensors, miniaturized electronic devices, semiconductors and more.
Advanced Manufacturing
Advanced manufacturing refers to enhanced or novel technologies, tools and processes used to develop and manufacture advanced materials or components. This could include using specialized software, artificial intelligence, sensors and high performance tools, among others, to facilitate process automation or closed-loop automated machining and create new materials or components.
Additive manufacturing (3D printing)
Various processes in which solid three-dimensional objects are constructed using computer-aided-design (CAD) software to build an object, ranging from simple geometric shapes to parts for commercial airplanes. 3D printing could be used to accelerate the development through rapid prototyping of customized equipment, spare tools or novel shapes or objects that are stronger and lighter. Approaches are also being developed for multi-material additive manufacturing and volumetric additive manufacturing, as well as additive manufacturing for repair and restoration.
Advanced semiconductor manufacturing
Methods, materials and processes related to the manufacturing of semiconductor devices. Examples of techniques include: advancements in deposition, coating, lithography, ionization/doping, and other core and supporting processes, such as thermal management techniques. Recent technological advancements include developments in Extreme Ultraviolet (EUV) lithography, which is an advanced method for fabricating intricate patterns on a substrate to produce a semiconductor device with extremely small features.
Critical materials manufacturing
Up and midstream technologies necessary to extract, process, upgrade, and recycle/recover critical materials (e.g. rare earth elements, scandium, lithium, etc.) and establish and maintain secure domestic and allied supply chains. More information about critical minerals can be found in Canada’s Critical Minerals List .
Four-dimensional (4D) printing
Production and manufacture of 3D products using multifunctional or “smart” materials that are programmed to transform in response to external stimuli (e.g. heat, water, light, etc.) within a given amount of time. Recent developments have also been made in creating reversible 4D printed objects, which can return to their original shape without human involvement.
Nano-manufacturing
Production and manufacture of nanoscale materials, structures, devices and systems in a scaled-up, reliable and cost-effective manner.
Two-dimensional (2D) materials manufacturing
Standardized, scalable and cost-effective large-scale production of 2D materials.
4. Advanced Sensing and Surveillance
Advanced sensing and surveillance refers to a large array of advanced technologies that detect, measure or monitor physical, chemical, biological or environmental conditions and generate data or information about them. Advanced surveillance technologies, in particular, are used to monitor and observe the activities and communications of specific individuals or groups for national security or law enforcement purposes, but have also been used for mass surveillance with increased accuracy and scale.
Advanced biometric recognition technologies
Technologies that identify individuals based on their distinctive physical identifiers (e.g. face, fingerprint or DNA) or behavioural identifiers (e.g. gait, keystroke pattern and voice). These technologies are becoming more advanced due to improving sensing capabilities, as well as integrating artificial intelligence to identify/verify an individual more quickly and accurately.
Advanced radar technologies
Radar is a system that uses radio waves to detect moving objects and measure their distance, speed and direction. Advancements in radar technology could enable improved detection and surveillance in different environments and over greater distances. Examples include: active electronically-scanned arrays, cognitive radars, high frequency skywave radar (or over-the-horizon radar), passive radar and synthetic aperture radar.
Atomic interferometer sensors
Sensors that perform sensitive interferometric measurements using the wave character of atomic particles and quantum gases. These sensors can detect small changes in inertial forces and can be used in gravimetry. They can also improve accuracy in navigation and provide position information in environments where the Global Positioning System (GPS) is unavailable.
Cross-cueing sensors
Systems that enable multiple sensors to cue one another. Cross cueing can be used in satellites for data validation, objection tracking, enhanced reliability (i.e. in the event of a sensor failure) and earth observations.
Electric field sensors
Sensors that detect variations in electric fields and use low amounts of power. They are useful for detecting power lines or lightning, as well as locating power grids or damaged components in the aftermath of a natural disaster.
Imaging and optical devices and sensors
Devices and sensors that provide a visual depiction of the physical structure of an object beyond the typical capabilities of consumer grade imaging techniques such as cameras, cellphones, and visible light-imaging. Such technologies typically make use of electromagnetic radiation beyond the visible spectrum, or use advanced techniques and materials to improve optical capabilities, such as enabling more precise imaging from a greater distance. This sensitive research area also includes sensitive infrared sensors.
Magnetic field sensors (or magnetometers)
Sensors that are used to detect or measure changes in a magnetic field, or its intensity or direction.
Micro (or nano) electro-mechanical systems (M/NEMS)
Miniaturized, lightweight electro-mechanical devices that integrate mechanical and electrical functionality at the microscopic or nano level. A potential use of M/NEMS could be as ‘smart dust’, or a group of M/NEMs, made up of various components, including sensors, circuits, communications technology and a power supply, that function as a single digital entity. Smart dust could be light enough to float in the air and detect vibrations, light, pressure and temperature, among other things, to capture a great deal of information about a particular environment.
Position, navigation and timing (PNT) technology
Systems, platforms or capabilities that enable accurate and timely calculation of positioning, navigation and timing. These technologies are critical to a wide-range of applications, most notably for enabling the Global Navigation Satellite System (GNSS), one of which is the widely-used Global Positioning System (GPS), but also for enabling navigation in areas where GPS or GNSS do not work. Examples include: chip-scale advanced atomic clocks, gravity-aided inertial navigation system, long-range underwater navigation system, magnetic anomaly navigation, precision inertial navigation system.
Side scan sonar
An active sonar system that uses a transducer array to send and receive acoustic pulses in swaths laterally from the tow-body or vessel, enabling it to quickly scan a large area in a body of water to produce an image of the sea floor beneath the tow-body or vessel.
Synthetic aperture sonar (SAS)
An active sonar system that produces high resolution images of the sea floor along the track of the vessel or tow body. SAS can send continuous sonar signals to capture images underwater at 30 times the resolution of traditional sonar systems, as well as up to 10 times the range and area coverage.
Underwater (wireless) sensor network
Network of sensors and autonomous/uncrewed underwater vehicles that use acoustic waves to communicate with each other, or with underwater sinks that collect and transmit data from deep ocean sensors, to enable remote sensing, surveillance and ocean exploration, observation and monitoring.
5. Advanced Weapons
Emerging or improved weapons used by military, and in some instances law enforcement, for defence and national security purposes. Advancements in materials, manufacturing, propulsion, energy and other technologies have brought weapons like directed energy weapons and hypersonic weapons closer to reality, while nanotechnology, synthetic biology, artificial intelligence and sensing technologies, among others, have provided enhancements to existing weapons, such as biological/chemical weapons and autonomous weapons.
6. Aerospace, Space and Satellite Technology
Aerospace technology refers to the technology that enables the design, production, testing, operation and maintenance of aircraft, spacecraft and their respective components, as well as other aeronautics. Space and satellite technology refers to technologies that enable travel, research and exploration in space, as well as weather-tracking, advanced PNT, communications, remote sensing and other capabilities using satellites and other space-based assets.
Advanced wind tunnels
Technological advancements in systems related to wind tunnel infrastructure. Existing facilities are used to simulate various flight conditions and speeds ranging from subsonic, transonic, supersonic and hypersonic.
On-orbit servicing, assembly and manufacturing systems
Systems and equipment that are used for space-based servicing, assembly and manufacturing. On-orbit servicing, assembly and manufacturing systems can be used to optimize space logistics, increase efficiencies, mitigate debris threats and to modernize space asset capabilities.
Lower cost satellite payloads with increased performance that can meet the needs of various markets. This will require several technology improvements, such as light weight apertures, antennas, panels, transceivers, control actuators, optical/infrared sensor and multi-spectral imagers, to meet the growing demand and ever-increasing technical requirements.
Propulsion technologies
Components and systems that produce a powerful thrust to push an object forward, which is essential to launching aircraft, spacecraft, rockets or missiles. Innovations could range from new designs or advanced materials to enable improved performance, speed, energy-efficiency and other enhanced properties, as well as reduced aircraft production times and emissions. Examples include: electrified aircraft propulsion, solar electric propulsion, pulse detonation engines, nuclear thermal propulsion systems, nuclear pulse propulsion systems and nuclear electric propulsion systems, among others.
Artificial or human-made, including (semi-)autonomous, objects placed into orbit. Depending on their specific function, satellites typically consist of an antenna, radio communications system, a power source and a computer, but their exact composition may vary. Continued developments have led to smaller satellites that are less costly to manufacture and deploy compared to large satellites, resulting in faster development times and increased accessibility to space. Examples include: remote sensing and communications satellites.
Space-based positioning, navigation and timing technology
Global Navigation Satellite System (GNSS)-based satellites and technologies that will improve the accuracy, agility and resilience of GNSS and the Global Positioning System (GPS).
Space stations
Space-based facility that can act as an orbital outpost while having the ability to support extended human operations. Space stations can be used as a hub to support other space-based activities including assembly, manufacturing, research, experimentations, training, space vehicle docking and storage. Examples of innovations in space stations could include the ability to extend further out into space or enhanced life support systems that can be used to prolong human missions.
Zero-emission/fuel aircraft
Aircraft powered by energy sources that do not emit polluting emissions that disrupt the environment or do not require fuel to fly. While still in early stages, these advances in powering aircraft could support cleaner air travel, as well as enable flight over greater distances and to remote areas without the need for refueling (for zero-fuel aircraft).
7. Artificial Intelligence and Big Data Technology
Artificial intelligence (AI) is a broad field encompassing the science of making computers behave in a manner that simulates human behaviour/intelligence using data and algorithms. Big data refers to information and data that is large and complex in volume, velocity and variety, and as such, requires specialized tools, techniques and technologies to process, analyze and visualize it. AI and big data technology may be considered cross-cutting given how important they are in enabling developments in other technology areas, including biotechnology, advanced materials and manufacturing, robotics and autonomous systems and others.
AI chipsets
Custom-designed chips meant to process large amounts of data and information that enable algorithms to perform calculations more efficiently, simultaneously and using less energy than general-purpose chips. AI chips have unique design features specialized for AI, which may make them more cost-effective to use for AI development.
Computer vision
Field of AI that allows computers to see and extract meaning from the content of digital images such as photos and videos. Examples of computer vision techniques include: image classification, object detection, depth perception and others.
Data science and big data technology
Enables the autonomous or semi-autonomous analysis of data, namely large and/or complex sets of data when it comes to big data technology. It also includes the extraction or generation of deeper insights, predictions or recommendations to inform decision-making. Examples include: AI-enabled data analytics, big data technology (i.e. data warehouse, data mining, data correlation) and predictive analytics.
Digital twin technology
Virtual representations of physical objects or systems that combine real-time sensor data, big data processing and artificial intelligence (namely machine learning) to create an interactive model and predict the object or system’s future behaviour or performance. Advancements in digital twin technology could enable the growth and integration of an immersive digital experience (e.g. the metaverse) into daily life.
Machine learning (ML)
Branch of AI where computer programs are trained using algorithms and data to improve their decisions when introduced to a new set of data without necessarily being programmed to do so. Types of ML include: deep learning, evolutionary computation and neural networks.
Natural language processing
An area of AI that allows computers to process and make sense of, or ‘translate’, natural human language using speech and audio recognition to identify, analyze and interpret human voices and other types of audio. Examples include: syntactic and semantic analysis, tokenization, text classification and others, which enable capabilities like virtual assistants, chatbots, machine translation, predictive text, sentiment analysis and automatic summarization.
8. Human-Machine Integration
Human-machine integration refers to the pairing of operators with technology to enhance or optimize human capability. The nature of the integration can vary widely, with an important dimension being the invasive nature of the pairing.
Brain-computer interfaces
Interfaces that allow a human to interact with a computer directly via input from the brain through a device that senses brain activity, allowing for research, mapping, assistance or augmentation of human brain functions that could enable improved cognitive performance or communication with digital devices.
Exoskeletons
External devices or ‘wearable robots’ that can assist or augment the physical and physiological performance/capabilities of an individual or a group.
Neuroprosthetic/cybernetic devices
Implanted and worn devices that interact with the nervous system to enhance or restore motor, sensory, cognitive, visual, auditory or communicative functions, often resulting from brain injury. This includes cybernetic limbs or devices that go beyond medical use to contribute to human performance enhancement.
Virtual/augmented/mixed reality
Immersive technologies that combine elements of the virtual world with the real world to create an interactive virtual experience. An application of these technologies that several companies are developing is the ‘metaverse’ which is an immersive digital experience that integrates the physical world with the digital one and allows users to interact and perform a variety of activities like shopping and gaming, seamlessly in one virtual ecosystem. While still being explored, this could potentially translate into a digital economy with its own currency, property and other goods.
Wearable neurotechnology
Brain-computer interfaces that are wearable and non-invasive (i.e. do not need to be implanted). These wearable brain devices can be used for medical uses, such as tracking brain health and sending data to a doctor to inform treatment, as well as for non-medical applications related to human optimization, augmentation or enhancement, such as user-drowsiness, cognitive load monitoring or early reaction detection, among others.
9. Life Science Technology
Life science technology is a broad term that encompasses a wide array of technologies that enhance living organisms, such as biotechnology and medical and healthcare technologies.
Biotechnology
Biotechnology uses living systems, processes and organisms, or parts of them, to develop new or improved products, processes or services. It often integrates other areas of technology, such as nanotechnology, artificial intelligence, computing and others, to create novel solutions to problems, including in the area of human performance enhancement.
Biomanufacturing
Methods and processes that enable the industrial production of biological products and materials through the modification of biological organisms or systems. Advances in biomanufacturing, such as automation and sensor-based production, has led to commercial-scale production of new biological products, such as biomaterials and biosensors.
Genomic sequencing and genetic engineering
Technologies that enable whole genome sequencing, the direct manipulation of an organism’s genome using DNA, or genetic engineering to produce new or modified organisms. Examples include: Clustered Regularly Interspaced Short Palindromic Repeats (CRISPR) and Next Generation Sequencing (NGS).
Large-scale and experimental analysis of protein, proteomes and proteome informatics. Proteomic applications can be used for the identification of unknown bacterial species and strains, as well as species level identifications of tissues, body fluids, and bones of unknown origin.
Synthetic biology
Combination of biology and engineering to create new biological entities, such as cells or enzymes, or redesign existing biological systems, with new functions like sensing or producing a specific substance. Synthetic biology is expected to enable advancements in many areas, such as antibiotic, drug and vaccine development, biocomputers, biofuel, novel drug delivery platforms, novel chemicals, synthetic food, and synthetic life.
Medical and Healthcare Technology
Medical and healthcare technology refers to tools, processes or services that support good health and prevent, or attempt to prevent, disease. Advances in biotechnology, nanotechnology and advanced materials are enabling new methods of delivering medicine or treating injuries, diseases or exposure to toxic substances.
Chemical, Biological, Radiological and Nuclear (CBRN) medical countermeasures
Various medical assets used to prevent, identify or treat injuries or illnesses caused by chemical, biological, radiological or nuclear (CBRN) threats, whether naturally-occurring or engineered. CBRN medical countermeasures include therapeutics to treat injuries and illnesses, such as biologic products or drugs, as well diagnostics to identify the threats.
Gene therapy
Use of gene manipulation or modification in humans to prevent, treat or cure disease, either by replacing or disabling disease-causing genes or inserting new or modified genes.
Nanomedicine
Use of nanomaterials to diagnose, monitor, prevent and/or treat disease. Examples of nanomedicine include nanoparticles for targeted drug delivery, smart imaging using nanomaterials, as well as nano-engineered implants to support tissue engineering and regenerative medicine.
Tissue engineering and regenerative medicine
Methods of regenerating or rebuilding cells, tissues or organs to allow normal, biological functions to be restored. Regenerative medicine includes self-healing, where the body is able to use its own tools or other biological materials to regrow tissues or cells, whereas tissue engineering largely focuses on the use of synthetic and biological materials, such as stem cells, to build function constructs or supports that help heal or restore damaged tissues or organs.
10. Quantum Science and Technology
Quantum science and technology refers to a new generation of devices that use quantum effects to significantly enhance the performance over those of existing, ‘classical’, technologies. This technology is expected to deliver sensing and imaging, communications, and computing capabilities that far exceed those of conventional technologies in certain cases, well as new materials with extraordinary properties and many useful applications. Quantum science and technology may be considered cross-cutting, given that quantum-enhanced technologies are expected to enable advancements or improvements in most other technology areas, including biotechnology, advanced materials, robotics and autonomous systems, aerospace, space and satellite technology and others.
Quantum communications
Use of quantum physics to enable secure communications and protect data using quantum cryptography, also know as quantum key distribution.
Quantum computing
Use of quantum bits, also known as qubits, to process information by capitalizing on quantum mechanical effects that allow for a large amount of information, such as calculations, to be processed at the same time. A quantum computer that can harness qubits in a controlled quantum state may be able to compute and solve certain problems significantly faster than the most powerful supercomputers.
Quantum materials
Materials with unusual magnetic and electrical properties. Examples include: superconductors, graphene, topological insulators, Weyl semimetals, metal chalcogenides and others. While many of these materials are still being explored and studied, they are promising contenders that could enable energy-efficient electrical systems, better batteries and the development of new types of electronic devices.
Quantum sensing
Broad of range of devices, at various stages of technological readiness, that use quantum systems, properties, or phenomena to measure a physical quantity with increased precision, stability and accuracy. Recent developments in applications of quantum physics identified the possibility of exploiting quantum phenomena as means to develop quantum radar technology.
Quantum software
Software and algorithms that run on quantum computers, enable the efficient operation and design of quantum computers, or software that enables the development and optimization of quantum computing applications.
11. Robotics and Autonomous Systems
Robotics and Autonomous Systems are machines or systems with a certain degree of autonomy (ranging from semi- to fully autonomous) that are able to carry out certain activities with little to no human control or intervention by gathering insights from their surroundings and making decisions based on them, including improving their overall task performance.
Molecular (or nano) robotics
Development of robots at the molecular or nano-scale level by programming molecules to carry out a particular task.
(Semi-)autonomous/uncrewed aerial/ground/marine vehicles
Vehicles that function without any onboard human intervention, and instead, are either controlled remotely by a human operator, or operate semi-autonomously or autonomously. Uncrewed vehicles rely on software, sensors and artificial intelligence technology to collect and analyze information about their environment, plan and alter their route (if semi- or fully autonomous), and interact with other vehicles (or human operator, if remotely-controlled).
Service robots
Robots that carry out tasks useful to humans that may be tedious, time-consuming, repetitive, dangerous or complement human behaviour when resources are not available, e.g. supporting elderly people. They are semi- or fully-autonomous, able to make decisions with some or no human interaction/intervention (depending on the degree of autonomy), and can be manually overridden by a human.
Space robotics
Devices, or ‘space robots’, that are able to perform various functions in orbit, such as assembling or servicing, to support astronauts, or replace human explorers in the exploration of remote planets.

IMAGES
VIDEO
COMMENTS
These are actual studies, so they can provide some useful insight as to what a research topic looks like in practice. Cyber Security Vulnerability Detection Using Natural Language Processing (Singh et al., 2022) Security for Cloud-Native Systems with an AI-Ops Engine (Ck et al., 2022) Overview of Cyber Security (Yadav, 2022)
This research report shows you: Quick wins that take a short time and minimal effort to boost momentum; ... CISOs face a cyber risk deluge that is growing at an exponential rate, not only in volume, but in complexity and scope. ... (business information security officers, local information security officers, security champions). Match new ways ...
Whether you are a cybersecurity professional, a Master's or Ph.D. student, or simply interested in the field, this post will provide valuable insights into the challenges and opportunities in this rapidly evolving area of study. Cyber Security Research Topics. Cyber Security Research Topics are as follows:
This article is organized as Section 1) Introduction to Cyber security, Section 2) Application area of Cyber-security, Section 3) State-of-the-art in Cyber Security, Section 4) Related Work, Section 5) Challenges of Cyber Security, Section 6) Opportunities and future research direction of cyber security, and Section 7) conclusion. 2.
AI is a large, multidisciplinary research area, with a large body of literature addressing its applications and consequences from a variety of perspectives, e.g., technical, operational, practical and philosophical. ... Cyber supply chain security. Cyber supply chain security requires a secure integrated network between the incoming and ...
The journal publishes research articles and reviews in the areas including, but not limited to: • Cryptography and its applications. • Network and critical infrastructure security. • Hardware security. • Software and system security. • Cybersecurity data analytics. • Data-driven security and measurement studies. • Adversarial ...
About the journal. Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …. Find out more. The simple economics of an external shock to a bug bounty platform. The cybersecurity of fairy tales.
Therefore, the formal definition can be as follows: "Cybersecurity data science is a research or working area existing at the intersection of cybersecurity, data science, and machine learning or artificial intelligence, which is mainly security data-focused, applies machine learning methods, attempts to quantify cyber-risks or incidents, and ...
Why Join Cybersecurity at MIT Sloan? Benefit from usable research! Cybersecurity at MIT Sloan (CAMS), formerly (IC) 3, is focusing MIT's uniquely qualified interdisciplinary faculty and researchers on the fundamental principles of cyberspace, cybercrime, & cybersecurity applied to critical infrastructure.Cybersecurity at MIT Sloan is a confidential academic forum in which leaders and ...
Securing software, hardware, systems, and the safety and privacy of those who access them, relies on an integrated network of technological, legal, and social approaches. Research initiatives at the Center for Cybersecurity reflect this diversity of topics and approaches, as well as the application of the interdisciplinary expertise required to implement effective security solutions.
NIST develops cybersecurity standards, guidelines, best practices, and other resources to meet the needs of U.S. industry, federal agencies and the broader public. Our activities range from producing specific information that organizations can put into practice immediately to longer-term research that anticipates advances in technologies and ...
2. Cybersecurity is impacting other business activities. We see this happening in a few ways: Threat intelligence now includes new types of cyber threats like social engineering and ransomware attacks that highlight the intersection of technology and reality.; The web of regulatory issues and government agencies overseeing digital business is driving organizations to become more cognizant of ...
Here is a list of research ideas along with the cyber security research areas, tips to choose the best topic from experts and more. For enquiries call: +1-469-442-0620. For enquiries call: +1-469-442-0620. All Courses. Bootcamps. Enterprise. Resources. All Blogs. Agile. Project Management. Data Science. More. Subscribe. Courses.
The Lincoln Laboratory Supercomputing Center staff are advancing the capabilities of our supercomputing system by developing new technologies to improve the system's performance. More. Our group develops architectures and technologies for ensuring security and resiliency of mission-critical cyber-physical systems, from drones and satellites to ...
Cybersecurity research aims to protect computer systems, networks, and data from unauthorised access, theft, or damage. It involves studying and developing methods and techniques to identify, understand, and mitigate cyber threats and vulnerabilities. The field can be divided into theoretical and applied research and faces challenges such as.
Cybersecurity is a significant concern for businesses worldwide, as cybercriminals target business data and system resources. Cyber threat intelligence (CTI) enhances organizational cybersecurity resilience by obtaining, processing, evaluating, and disseminating information about potential risks and opportunities inside the cyber domain. This research investigates how companies can employ CTI ...
Research Areas. Cybersecurity is at the forefront of todays needs and challenges. The SECURE Center of Excellence is dedicated to emerging ideas and needs for the research arena. As such, we will continuously monitor and survey the field in order to identify novel and pivotal research ideas, so that our efforts are responding accordingly.
The term "policy" is used in a variety of areas related to cyber-security, and refers to information distribution rules and regulations, private sector goals for data conservation, system operations strategies for technology control. ... His research interests include information security, computational intelligence and big data analysis. E ...
Over the next three to five years, we expect three major cybersecurity trends that cross-cut multiple technologies to have the biggest implications for organizations. 1. On-demand access to ubiquitous data and information platforms is growing. Mobile platforms, remote work, and other shifts increasingly hinge on high-speed access to ubiquitous ...
Most cybersecurity analysts and engineers work within a larger team, led by an IT security manager, security administrator, or security architect. While analysts focus more on identifying and responding to cyber threats and executing security procedures, engineers are responsible for creating the individual security systems of a company.
Critical infrastructure security protects the computer systems, applications, networks, data and digital assets that a society depends on for national security, economic health and public safety. In the United States, the National Institute of Standards and Technology (NIST) developed a cybersecurity framework to help IT providers in this area.
[00:03:55] Amy Zegart: So there's an incentive for corporate boards to pay much more attention to cyber security. And when the incentives are aligned, of course, companies pay more money for cybersecurity, do a lot more investing in cybersecurity.
The researchers, faculty, Ph.D. students, and student workers in the Networking and Cybersecurity Division focus on the following research areas: Areas of Research. Cyber Experimentation Research, Methods, and Infrastructure. Network Measurement, Analysis, and Defenses. Security for Wireless Networks.
The initiative is a platform to work together to foster R&D to evolve transformative solutions and address critical cyber security challenges, through partnerships among academics, Industry and Govt. Broad research areas 1. Information Security 1. Computer Network Security 2. Application Security 3. Web Services Security 4.
Table of Contents Preface Introduction The Digital World: Opportunities and Challenges Cyber Attacks and National Security Threats Competing Internet Norms Threats to Internet and Digital Freedom Challenges of the Digital Economy The Future of AI Technologies Governance Working with the Private Sector and Civil Society Building Digital Solidarity ACTION AREA 1: Promote, Build, and Maintain […]
2024 RE P O R T O N T H E CY B E R S E C U R I T Y PO S T U R E O F T H E UN I T E D ST A T E S iv Five trends, in addition to enduring cybersecurity challenges, drove change in the strategic
This is why the Intelligence Advanced Research Projects Activity (IARPA) is working on a solution with its latest program, Securing Our Underlying Resources in Cyber Environments, or SoURCE CODE. The SoURCE CODE program seeks to provide novel technologies to assist forensic experts in making determinations of the most likely attackers, based on ...
Cyber ranges were originally used primarily by military and government agencies. They are now used by a broad range of businesses and organizations due to their cost-effectiveness and valuable opportunities to upskill security team members. Cyber ranges offer essential training for various people and groups:
Following a series of public breaches, a global software provider created the position of chief trust officer. It empowered that leader to be the company's external-facing cybersecurity ambassador to the market. The role serves as a bridge between customer-account teams and technical information security, as well as a convener role (for example, promoting industry-wide collaboration on ...
The list of Sensitive Technology Research Areas consists of advanced and emerging technologies that are important to Canadian research and development, ... Cyber security technology. Technologies that protect the integrity, confidentiality and availability of internet-connected systems, including their hardware, software, as well as data from ...