ORIGINAL RESEARCH article
Effects of social media use on psychological well-being: a mediated model.

- 1 School of Finance and Economics, Jiangsu University, Zhenjiang, China
- 2 Research Unit of Governance, Competitiveness, and Public Policies (GOVCOPP), Center for Economics and Finance (cef.up), School of Economics and Management, University of Porto, Porto, Portugal
- 3 Department of Business Administration, Sukkur Institute of Business Administration (IBA) University, Sukkur, Pakistan
- 4 CETYS Universidad, Tijuana, Mexico
- 5 Department of Business Administration, Al-Quds University, Jerusalem, Israel
- 6 Business School, Shandong University, Weihai, China
The growth in social media use has given rise to concerns about the impacts it may have on users' psychological well-being. This paper's main objective is to shed light on the effect of social media use on psychological well-being. Building on contributions from various fields in the literature, it provides a more comprehensive study of the phenomenon by considering a set of mediators, including social capital types (i.e., bonding social capital and bridging social capital), social isolation, and smartphone addiction. The paper includes a quantitative study of 940 social media users from Mexico, using structural equation modeling (SEM) to test the proposed hypotheses. The findings point to an overall positive indirect impact of social media usage on psychological well-being, mainly due to the positive effect of bonding and bridging social capital. The empirical model's explanatory power is 45.1%. This paper provides empirical evidence and robust statistical analysis that demonstrates both positive and negative effects coexist, helping to reconcile the inconsistencies found so far in the literature.

Introduction
The use of social media has grown substantially in recent years ( Leong et al., 2019 ; Kemp, 2020 ). Social media refers to “the websites and online tools that facilitate interactions between users by providing them opportunities to share information, opinions, and interest” ( Swar and Hameed, 2017 , p. 141). Individuals use social media for many reasons, including entertainment, communication, and searching for information. Notably, adolescents and young adults are spending an increasing amount of time on online networking sites, e-games, texting, and other social media ( Twenge and Campbell, 2019 ). In fact, some authors (e.g., Dhir et al., 2018 ; Tateno et al., 2019 ) have suggested that social media has altered the forms of group interaction and its users' individual and collective behavior around the world.
Consequently, there are increased concerns regarding the possible negative impacts associated with social media usage addiction ( Swar and Hameed, 2017 ; Kircaburun et al., 2020 ), particularly on psychological well-being ( Chotpitayasunondh and Douglas, 2016 ; Jiao et al., 2017 ; Choi and Noh, 2019 ; Chatterjee, 2020 ). Smartphones sometimes distract their users from relationships and social interaction ( Chotpitayasunondh and Douglas, 2016 ; Li et al., 2020a ), and several authors have stressed that the excessive use of social media may lead to smartphone addiction ( Swar and Hameed, 2017 ; Leong et al., 2019 ), primarily because of the fear of missing out ( Reer et al., 2019 ; Roberts and David, 2020 ). Social media usage has been associated with anxiety, loneliness, and depression ( Dhir et al., 2018 ; Reer et al., 2019 ), social isolation ( Van Den Eijnden et al., 2016 ; Whaite et al., 2018 ), and “phubbing,” which refers to the extent to which an individual uses, or is distracted by, their smartphone during face-to-face communication with others ( Chotpitayasunondh and Douglas, 2016 ; Jiao et al., 2017 ; Choi and Noh, 2019 ; Chatterjee, 2020 ).
However, social media use also contributes to building a sense of connectedness with relevant others ( Twenge and Campbell, 2019 ), which may reduce social isolation. Indeed, social media provides several ways to interact both with close ties, such as family, friends, and relatives, and weak ties, including coworkers, acquaintances, and strangers ( Chen and Li, 2017 ), and plays a key role among people of all ages as they exploit their sense of belonging in different communities ( Roberts and David, 2020 ). Consequently, despite the fears regarding the possible negative impacts of social media usage on well-being, there is also an increasing number of studies highlighting social media as a new communication channel ( Twenge and Campbell, 2019 ; Barbosa et al., 2020 ), stressing that it can play a crucial role in developing one's presence, identity, and reputation, thus facilitating social interaction, forming and maintaining relationships, and sharing ideas ( Carlson et al., 2016 ), which consequently may be significantly correlated to social support ( Chen and Li, 2017 ; Holliman et al., 2021 ). Interestingly, recent studies (e.g., David et al., 2018 ; Bano et al., 2019 ; Barbosa et al., 2020 ) have suggested that the impact of smartphone usage on psychological well-being depends on the time spent on each type of application and the activities that users engage in.
Hence, the literature provides contradictory cues regarding the impacts of social media on users' well-being, highlighting both the possible negative impacts and the social enhancement it can potentially provide. In line with views on the need to further investigate social media usage ( Karikari et al., 2017 ), particularly regarding its societal implications ( Jiao et al., 2017 ), this paper argues that there is an urgent need to further understand the impact of the time spent on social media on users' psychological well-being, namely by considering other variables that mediate and further explain this effect.
One of the relevant perspectives worth considering is that provided by social capital theory, which is adopted in this paper. Social capital theory has previously been used to study how social media usage affects psychological well-being (e.g., Bano et al., 2019 ). However, extant literature has so far presented only partial models of associations that, although statistically acceptable and contributing to the understanding of the scope of social networks, do not provide as comprehensive a vision of the phenomenon as that proposed within this paper. Furthermore, the contradictory views, suggesting both negative (e.g., Chotpitayasunondh and Douglas, 2016 ; Van Den Eijnden et al., 2016 ; Jiao et al., 2017 ; Whaite et al., 2018 ; Choi and Noh, 2019 ; Chatterjee, 2020 ) and positive impacts ( Carlson et al., 2016 ; Chen and Li, 2017 ; Twenge and Campbell, 2019 ) of social media on psychological well-being, have not been adequately explored.
Given this research gap, this paper's main objective is to shed light on the effect of social media use on psychological well-being. As explained in detail in the next section, this paper explores the mediating effect of bonding and bridging social capital. To provide a broad view of the phenomenon, it also considers several variables highlighted in the literature as affecting the relationship between social media usage and psychological well-being, namely smartphone addiction, social isolation, and phubbing. The paper utilizes a quantitative study conducted in Mexico, comprising 940 social media users, and uses structural equation modeling (SEM) to test a set of research hypotheses.
This article provides several contributions. First, it adds to existing literature regarding the effect of social media use on psychological well-being and explores the contradictory indications provided by different approaches. Second, it proposes a conceptual model that integrates complementary perspectives on the direct and indirect effects of social media use. Third, it offers empirical evidence and robust statistical analysis that demonstrates that both positive and negative effects coexist, helping resolve the inconsistencies found so far in the literature. Finally, this paper provides insights on how to help reduce the potential negative effects of social media use, as it demonstrates that, through bridging and bonding social capital, social media usage positively impacts psychological well-being. Overall, the article offers valuable insights for academics, practitioners, and society in general.
The remainder of this paper is organized as follows. Section Literature Review presents a literature review focusing on the factors that explain the impact of social media usage on psychological well-being. Based on the literature review, a set of hypotheses are defined, resulting in the proposed conceptual model, which includes both the direct and indirect effects of social media usage on psychological well-being. Section Research Methodology explains the methodological procedures of the research, followed by the presentation and discussion of the study's results in section Results. Section Discussion is dedicated to the conclusions and includes implications, limitations, and suggestions for future research.
Literature Review
Putnam (1995 , p. 664–665) defined social capital as “features of social life – networks, norms, and trust – that enable participants to act together more effectively to pursue shared objectives.” Li and Chen (2014 , p. 117) further explained that social capital encompasses “resources embedded in one's social network, which can be assessed and used for instrumental or expressive returns such as mutual support, reciprocity, and cooperation.”
Putnam (1995 , 2000) conceptualized social capital as comprising two dimensions, bridging and bonding, considering the different norms and networks in which they occur. Bridging social capital refers to the inclusive nature of social interaction and occurs when individuals from different origins establish connections through social networks. Hence, bridging social capital is typically provided by heterogeneous weak ties ( Li and Chen, 2014 ). This dimension widens individual social horizons and perspectives and provides extended access to resources and information. Bonding social capital refers to the social and emotional support each individual receives from his or her social networks, particularly from close ties (e.g., family and friends).
Overall, social capital is expected to be positively associated with psychological well-being ( Bano et al., 2019 ). Indeed, Williams (2006) stressed that interaction generates affective connections, resulting in positive impacts, such as emotional support. The following sub-sections use the lens of social capital theory to explore further the relationship between the use of social media and psychological well-being.
Social Media Use, Social Capital, and Psychological Well-Being
The effects of social media usage on social capital have gained increasing scholarly attention, and recent studies have highlighted a positive relationship between social media use and social capital ( Brown and Michinov, 2019 ; Tefertiller et al., 2020 ). Li and Chen (2014) hypothesized that the intensity of Facebook use by Chinese international students in the United States was positively related to social capital forms. A longitudinal survey based on the quota sampling approach illustrated the positive effects of social media use on the two social capital dimensions ( Chen and Li, 2017 ). Abbas and Mesch (2018) argued that, as Facebook usage increases, it will also increase users' social capital. Karikari et al. (2017) also found positive effects of social media use on social capital. Similarly, Pang (2018) studied Chinese students residing in Germany and found positive effects of social networking sites' use on social capital, which, in turn, was positively associated with psychological well-being. Bano et al. (2019) analyzed the 266 students' data and found positive effects of WhatsApp use on social capital forms and the positive effect of social capital on psychological well-being, emphasizing the role of social integration in mediating this positive effect.
Kim and Kim (2017) stressed the importance of having a heterogeneous network of contacts, which ultimately enhances the potential social capital. Overall, the manifest and social relations between people from close social circles (bonding social capital) and from distant social circles (bridging social capital) are strengthened when they promote communication, social support, and the sharing of interests, knowledge, and skills, which are shared with other members. This is linked to positive effects on interactions, such as acceptance, trust, and reciprocity, which are related to the individuals' health and psychological well-being ( Bekalu et al., 2019 ), including when social media helps to maintain social capital between social circles that exist outside of virtual communities ( Ellison et al., 2007 ).
Grounded on the above literature, this study proposes the following hypotheses:
H1a: Social media use is positively associated with bonding social capital.
H1b: Bonding social capital is positively associated with psychological well-being.
H2a: Social media use is positively associated with bridging social capital.
H2b: Bridging social capital is positively associated with psychological well-being.
Social Media Use, Social Isolation, and Psychological Well-Being
Social isolation is defined as “a deficit of personal relationships or being excluded from social networks” ( Choi and Noh, 2019 , p. 4). The state that occurs when an individual lacks true engagement with others, a sense of social belonging, and a satisfying relationship is related to increased mortality and morbidity ( Primack et al., 2017 ). Those who experience social isolation are deprived of social relationships and lack contact with others or involvement in social activities ( Schinka et al., 2012 ). Social media usage has been associated with anxiety, loneliness, and depression ( Dhir et al., 2018 ; Reer et al., 2019 ), and social isolation ( Van Den Eijnden et al., 2016 ; Whaite et al., 2018 ). However, some recent studies have argued that social media use decreases social isolation ( Primack et al., 2017 ; Meshi et al., 2020 ). Indeed, the increased use of social media platforms such as Facebook, WhatsApp, Instagram, and Twitter, among others, may provide opportunities for decreasing social isolation. For instance, the improved interpersonal connectivity achieved via videos and images on social media helps users evidence intimacy, attenuating social isolation ( Whaite et al., 2018 ).
Chappell and Badger (1989) stated that social isolation leads to decreased psychological well-being, while Choi and Noh (2019) concluded that greater social isolation is linked to increased suicide risk. Schinka et al. (2012) further argued that, when individuals experience social isolation from siblings, friends, family, or society, their psychological well-being tends to decrease. Thus, based on the literature cited above, this study proposes the following hypotheses:
H3a: Social media use is significantly associated with social isolation.
H3b: Social isolation is negatively associated with psychological well-being.
Social Media Use, Smartphone Addiction, Phubbing, and Psychological Well-Being
Smartphone addiction refers to “an individuals' excessive use of a smartphone and its negative effects on his/her life as a result of his/her inability to control his behavior” ( Gökçearslan et al., 2018 , p. 48). Regardless of its form, smartphone addiction results in social, medical, and psychological harm to people by limiting their ability to make their own choices ( Chotpitayasunondh and Douglas, 2016 ). The rapid advancement of information and communication technologies has led to the concept of social media, e-games, and also to smartphone addiction ( Chatterjee, 2020 ). The excessive use of smartphones for social media use, entertainment (watching videos, listening to music), and playing e-games is more common amongst people addicted to smartphones ( Jeong et al., 2016 ). In fact, previous studies have evidenced the relationship between social use and smartphone addiction ( Salehan and Negahban, 2013 ; Jeong et al., 2016 ; Swar and Hameed, 2017 ). In line with this, the following hypotheses are proposed:
H4a: Social media use is positively associated with smartphone addiction.
H4b: Smartphone addiction is negatively associated with psychological well-being.
While smartphones are bringing individuals closer, they are also, to some extent, pulling people apart ( Tonacci et al., 2019 ). For instance, they can lead to individuals ignoring others with whom they have close ties or physical interactions; this situation normally occurs due to extreme smartphone use (i.e., at the dinner table, in meetings, at get-togethers and parties, and in other daily activities). This act of ignoring others is called phubbing and is considered a common phenomenon in communication activities ( Guazzini et al., 2019 ; Chatterjee, 2020 ). Phubbing is also referred to as an act of snubbing others ( Chatterjee, 2020 ). This term was initially used in May 2012 by an Australian advertising agency to describe the “growing phenomenon of individuals ignoring their families and friends who were called phubbee (a person who is a recipients of phubbing behavior) victim of phubber (a person who start phubbing her or his companion)” ( Chotpitayasunondh and Douglas, 2018 ). Smartphone addiction has been found to be a determinant of phubbing ( Kim et al., 2018 ). Other recent studies have also evidenced the association between smartphones and phubbing ( Chotpitayasunondh and Douglas, 2016 ; Guazzini et al., 2019 ; Tonacci et al., 2019 ; Chatterjee, 2020 ). Vallespín et al. (2017 ) argued that phubbing behavior has a negative influence on psychological well-being and satisfaction. Furthermore, smartphone addiction is considered responsible for the development of new technologies. It may also negatively influence individual's psychological proximity ( Chatterjee, 2020 ). Therefore, based on the above discussion and calls for the association between phubbing and psychological well-being to be further explored, this study proposes the following hypotheses:
H5: Smartphone addiction is positively associated with phubbing.
H6: Phubbing is negatively associated with psychological well-being.
Indirect Relationship Between Social Media Use and Psychological Well-Being
Beyond the direct hypotheses proposed above, this study investigates the indirect effects of social media use on psychological well-being mediated by social capital forms, social isolation, and phubbing. As described above, most prior studies have focused on the direct influence of social media use on social capital forms, social isolation, smartphone addiction, and phubbing, as well as the direct impact of social capital forms, social isolation, smartphone addiction, and phubbing on psychological well-being. Very few studies, however, have focused on and evidenced the mediating role of social capital forms, social isolation, smartphone addiction, and phubbing derived from social media use in improving psychological well-being ( Chen and Li, 2017 ; Pang, 2018 ; Bano et al., 2019 ; Choi and Noh, 2019 ). Moreover, little is known about smartphone addiction's mediating role between social media use and psychological well-being. Therefore, this study aims to fill this gap in the existing literature by investigating the mediation of social capital forms, social isolation, and smartphone addiction. Further, examining the mediating influence will contribute to a more comprehensive understanding of social media use on psychological well-being via the mediating associations of smartphone addiction and psychological factors. Therefore, based on the above, we propose the following hypotheses (the conceptual model is presented in Figure 1 ):
H7: (a) Bonding social capital; (b) bridging social capital; (c) social isolation; and (d) smartphone addiction mediate the relationship between social media use and psychological well-being.
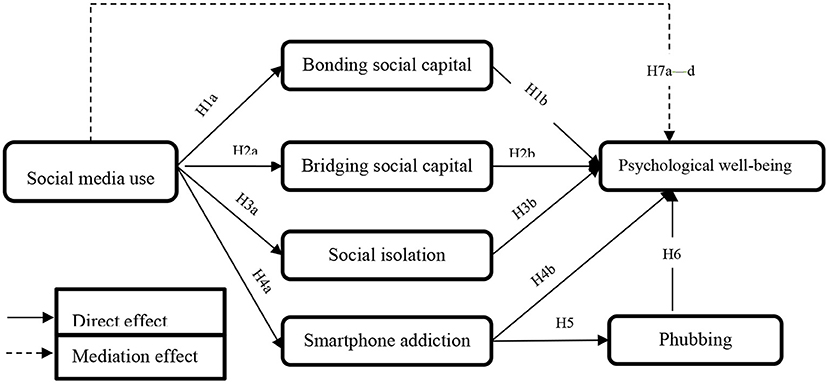
Figure 1 . Conceptual model.
Research Methodology
Sample procedure and online survey.
This study randomly selected students from universities in Mexico. We chose University students for the following reasons. First, students are considered the most appropriate sample for e-commerce studies, particularly in the social media context ( Oghazi et al., 2018 ; Shi et al., 2018 ). Second, University students are considered to be frequent users and addicted to smartphones ( Mou et al., 2017 ; Stouthuysen et al., 2018 ). Third, this study ensured that respondents were experienced, well-educated, and possessed sufficient knowledge of the drawbacks of social media and the extreme use of smartphones. A total sample size of 940 University students was ultimately achieved from the 1,500 students contacted, using a convenience random sampling approach, due both to the COVID-19 pandemic and budget and time constraints. Additionally, in order to test the model, a quantitative empirical study was conducted, using an online survey method to collect data. This study used a web-based survey distributed via social media platforms for two reasons: the COVID-19 pandemic; and to reach a large number of respondents ( Qalati et al., 2021 ). Furthermore, online surveys are considered a powerful and authenticated tool for new research ( Fan et al., 2021 ), while also representing a fast, simple, and less costly approach to collecting data ( Dutot and Bergeron, 2016 ).
Data Collection Procedures and Respondent's Information
Data were collected by disseminating a link to the survey by e-mail and social network sites. Before presenting the closed-ended questionnaire, respondents were assured that their participation would remain voluntary, confidential, and anonymous. Data collection occurred from July 2020 to December 2020 (during the pandemic). It should be noted that, because data were collected during the pandemic, this may have had an influence on the results of the study. The reason for choosing a six-month lag time was to mitigate common method bias (CMB) ( Li et al., 2020b ). In the present study, 1,500 students were contacted via University e-mail and social applications (Facebook, WhatsApp, and Instagram). We sent a reminder every month for 6 months (a total of six reminders), resulting in 940 valid responses. Thus, 940 (62.6% response rate) responses were used for hypotheses testing.
Table 1 reveals that, of the 940 participants, three-quarters were female (76.4%, n = 719) and nearly one-quarter (23.6%, n = 221) were male. Nearly half of the participants (48.8%, n = 459) were aged between 26 and 35 years, followed by 36 to 35 years (21.9%, n = 206), <26 (20.3%, n = 191), and over 45 (8.9%, n = 84). Approximately two-thirds (65%, n = 611) had a bachelor's degree or above, while one-third had up to 12 years of education. Regarding the daily frequency of using the Internet, nearly half (48.6%, n = 457) of the respondents reported between 5 and 8 h a day, and over one-quarter (27.2%) 9–12 h a day. Regarding the social media platforms used, over 38.5 and 39.6% reported Facebook and WhatsApp, respectively. Of the 940 respondents, only 22.1% reported Instagram (12.8%) and Twitter (9.2%). It should be noted, however, that the sample is predominantly female and well-educated.
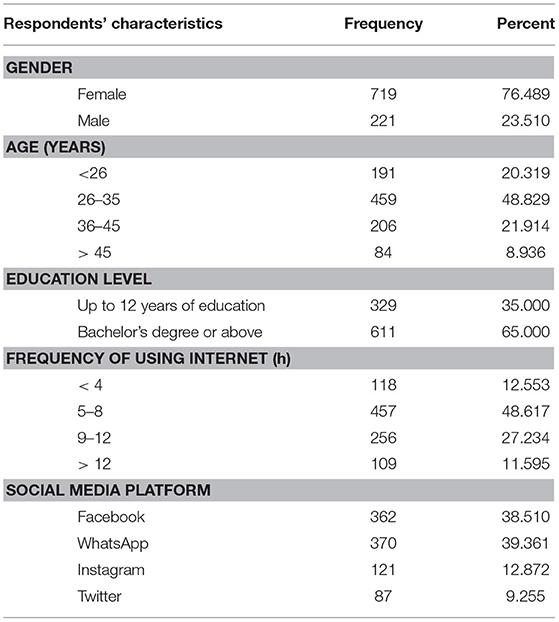
Table 1 . Respondents' characteristics.
Measurement Items
The study used five-point Likert scales (1 = “strongly disagree;” 5 = “strongly agree”) to record responses.
Social Media Use
Social media use was assessed using four items adapted from Karikari et al. (2017) . Sample items include “Social media is part of my everyday activity,” “Social media has become part of my daily life,” “I would be sorry if social media shut down,” and “I feel out of touch, when I have not logged onto social media for a while.” The adapted items had robust reliability and validity (CA = 783, CR = 0.857, AVE = 0.600).
Social Capital
Social capital was measured using a total of eight items, representing bonding social capital (four items) and bridging social capital (four items) adapted from Chan (2015) . Sample construct items include: bonging social capital (“I am willing to spend time to support general community activities,” “I interact with people who are quite different from me”) and bridging social capital (“My social media community is a good place to be,” “Interacting with people on social media makes me want to try new things”). The adapted items had robust reliability and validity [bonding social capital (CA = 0.785, CR = 0.861, AVE = 0.608) and bridging social capital (CA = 0.834, CR = 0.883, AVE = 0.601)].
Social Isolation
Social isolation was assessed using three items from Choi and Noh (2019) . Sample items include “I do not have anyone to play with,” “I feel alone from people,” and “I have no one I can trust.” This adapted scale had substantial reliability and validity (CA = 0.890, CR = 0.928, AVE = 0.811).
Smartphone Addiction
Smartphone addiction was assessed using five items taken from Salehan and Negahban (2013) . Sample items include “I am always preoccupied with my mobile,” “Using my mobile phone keeps me relaxed,” and “I am not able to control myself from frequent use of mobile phones.” Again, these adapted items showed substantial reliability and validity (CA = 903, CR = 0.928, AVE = 0.809).
Phubbing was assessed using four items from Chotpitayasunondh and Douglas (2018) . Sample items include: “I have conflicts with others because I am using my phone” and “I would rather pay attention to my phone than talk to others.” This construct also demonstrated significant reliability and validity (CA = 770, CR = 0.894, AVE = 0.809).
Psychological Well-Being
Psychological well-being was assessed using five items from Jiao et al. (2017) . Sample items include “I lead a purposeful and meaningful life with the help of others,” “My social relationships are supportive and rewarding in social media,” and “I am engaged and interested in my daily on social media.” This study evidenced that this adapted scale had substantial reliability and validity (CA = 0.886, CR = 0.917, AVE = 0.688).
Data Analysis
Based on the complexity of the association between the proposed construct and the widespread use and acceptance of SmartPLS 3.0 in several fields ( Hair et al., 2019 ), we utilized SEM, using SmartPLS 3.0, to examine the relationships between constructs. Structural equation modeling is a multivariate statistical analysis technique that is used to investigate relationships. Further, it is a combination of factor and multivariate regression analysis, and is employed to explore the relationship between observed and latent constructs.
SmartPLS 3.0 “is a more comprehensive software program with an intuitive graphical user interface to run partial least square SEM analysis, certainly has had a massive impact” ( Sarstedt and Cheah, 2019 ). According to Ringle et al. (2015) , this commercial software offers a wide range of algorithmic and modeling options, improved usability, and user-friendly and professional support. Furthermore, Sarstedt and Cheah (2019) suggested that structural equation models enable the specification of complex interrelationships between observed and latent constructs. Hair et al. (2019) argued that, in recent years, the number of articles published using partial least squares SEM has increased significantly in contrast to covariance-based SEM. In addition, partial least squares SEM using SmartPLS is more appealing for several scholars as it enables them to predict more complex models with several variables, indicator constructs, and structural paths, instead of imposing distributional assumptions on the data ( Hair et al., 2019 ). Therefore, this study utilized the partial least squares SEM approach using SmartPLS 3.0.
Common Method Bias (CMB) Test
This study used the Kaiser–Meyer–Olkin (KMO) test to measure the sampling adequacy and ensure data suitability. The KMO test result was 0.874, which is greater than an acceptable threshold of 0.50 ( Ali Qalati et al., 2021 ; Shrestha, 2021 ), and hence considered suitable for explanatory factor analysis. Moreover, Bartlett's test results demonstrated a significance level of 0.001, which is considered good as it is below the accepted threshold of 0.05.
The term CMB is associated with Campbell and Fiske (1959) , who highlighted the importance of CMB and identified that a portion of variance in the research may be due to the methods employed. It occurs when all scales of the study are measured at the same time using a single questionnaire survey ( Podsakoff and Organ, 1986 ); subsequently, estimates of the relationship among the variables might be distorted by the impacts of CMB. It is considered a serious issue that has a potential to “jeopardize” the validity of the study findings ( Tehseen et al., 2017 ). There are several reasons for CMB: (1) it mainly occurs due to response “tendencies that raters can apply uniformity across the measures;” and (2) it also occurs due to similarities in the wording and structure of the survey items that produce similar results ( Jordan and Troth, 2019 ). Harman's single factor test and a full collinearity approach were employed to ensure that the data was free from CMB ( Tehseen et al., 2017 ; Jordan and Troth, 2019 ; Ali Qalati et al., 2021 ). Harman's single factor test showed a single factor explained only 22.8% of the total variance, which is far below the 50.0% acceptable threshold ( Podsakoff et al., 2003 ).
Additionally, the variance inflation factor (VIF) was used, which is a measure of the amount of multicollinearity in a set of multiple regression constructs and also considered a way of detecting CMB ( Hair et al., 2019 ). Hair et al. (2019) suggested that the acceptable threshold for the VIF is 3.0; as the computed VIFs for the present study ranged from 1.189 to 1.626, CMB is not a key concern (see Table 2 ). Bagozzi et al. (1991) suggested a correlation-matrix procedure to detect CMB. Common method bias is evident if correlation among the principle constructs is >0.9 ( Tehseen et al., 2020 ); however, no values >0.9 were found in this study (see section Assessment of Measurement Model). This study used a two-step approach to evaluate the measurement model and the structural model.

Table 2 . Common method bias (full collinearity VIF).
Assessment of Measurement Model
Before conducting the SEM analysis, the measurement model was assessed to examine individual item reliability, internal consistency, and convergent and discriminant validity. Table 3 exhibits the values of outer loading used to measure an individual item's reliability ( Hair et al., 2012 ). Hair et al. (2017) proposed that the value for each outer loading should be ≥0.7; following this principle, two items of phubbing (PHUB3—I get irritated if others ask me to get off my phone and talk to them; PHUB4—I use my phone even though I know it irritated others) were removed from the analysis Hair et al. (2019) . According to Nunnally (1978) , Cronbach's alpha values should exceed 0.7. The threshold values of constructs in this study ranged from 0.77 to 0.903. Regarding internal consistency, Bagozzi and Yi (1988) suggested that composite reliability (CR) should be ≥0.7. The coefficient value for CR in this study was between 0.857 and 0.928. Regarding convergent validity, Fornell and Larcker (1981) suggested that the average variance extracted (AVE) should be ≥0.5. Average variance extracted values in this study were between 0.60 and 0.811. Finally, regarding discriminant validity, according to Fornell and Larcker (1981) , the square root of the AVE for each construct should exceed the inter-correlations of the construct with other model constructs. That was the case in this study, as shown in Table 4 .
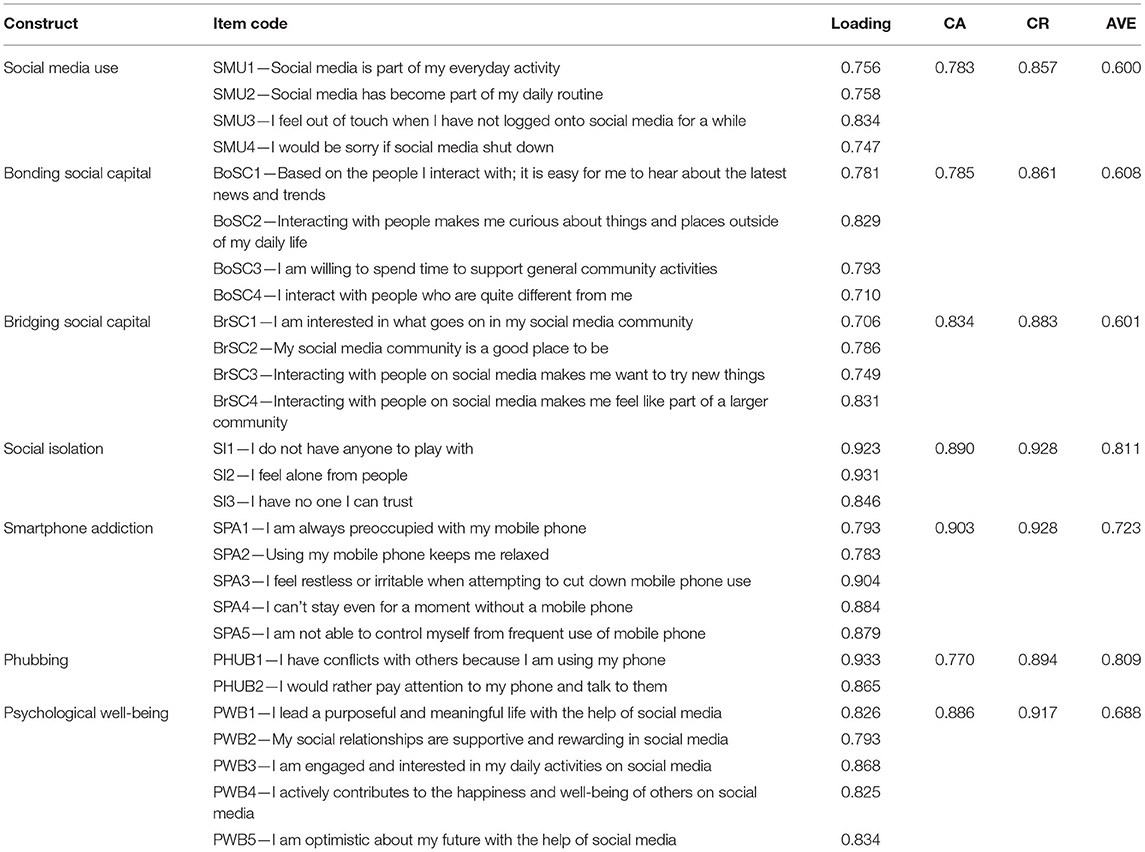
Table 3 . Study measures, factor loading, and the constructs' reliability and convergent validity.
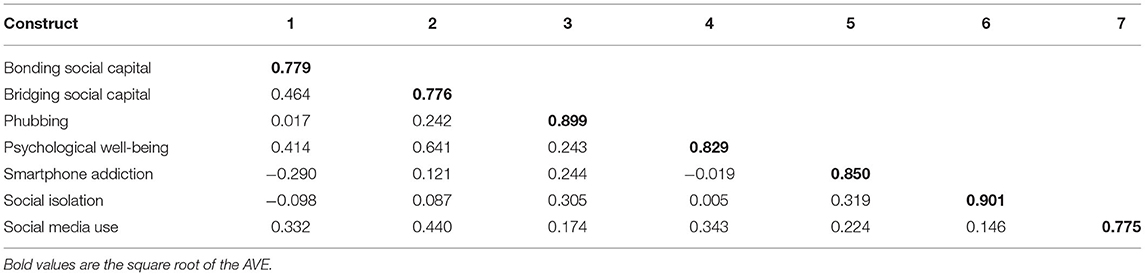
Table 4 . Discriminant validity and correlation.
Hence, by analyzing the results of the measurement model, it can be concluded that the data are adequate for structural equation estimation.
Assessment of the Structural Model
This study used the PLS algorithm and a bootstrapping technique with 5,000 bootstraps as proposed by Hair et al. (2019) to generate the path coefficient values and their level of significance. The coefficient of determination ( R 2 ) is an important measure to assess the structural model and its explanatory power ( Henseler et al., 2009 ; Hair et al., 2019 ). Table 5 and Figure 2 reveal that the R 2 value in the present study was 0.451 for psychological well-being, which means that 45.1% of changes in psychological well-being occurred due to social media use, social capital forms (i.e., bonding and bridging), social isolation, smartphone addiction, and phubbing. Cohen (1998) proposed that R 2 values of 0.60, 0.33, and 0.19 are considered substantial, moderate, and weak. Following Cohen's (1998) threshold values, this research demonstrates a moderate predicting power for psychological well-being among Mexican respondents ( Table 6 ).
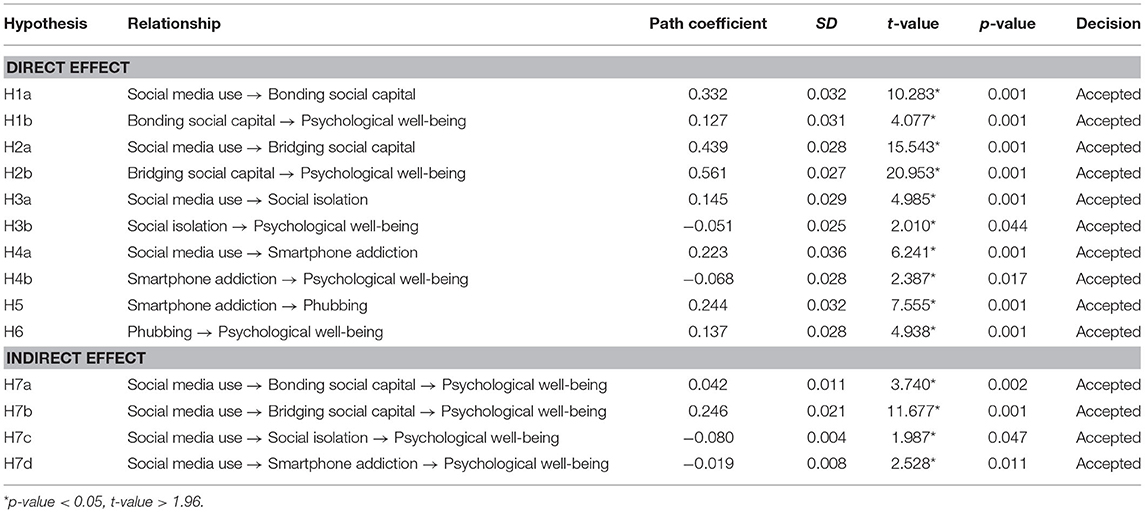
Table 5 . Summary of path coefficients and hypothesis testing.
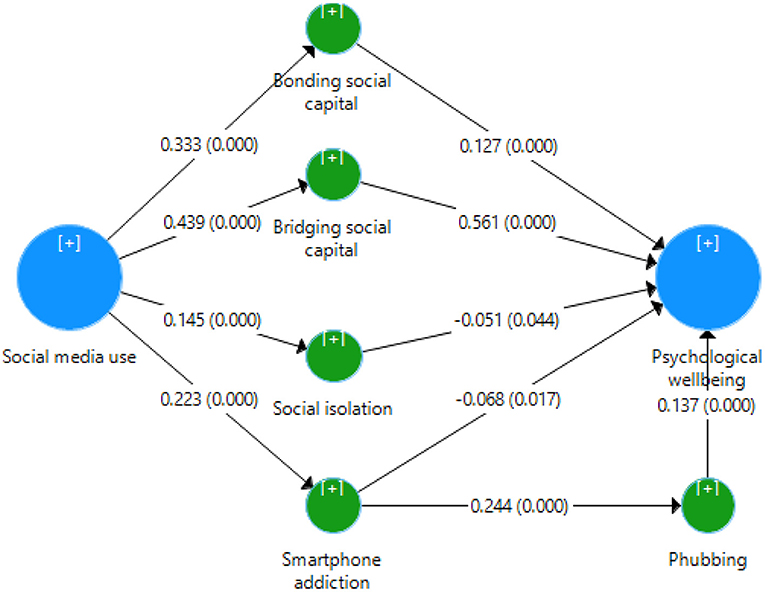
Figure 2 . Structural model.

Table 6 . Strength of the model (Predictive relevance, coefficient of determination, and model fit indices).
Apart from the R 2 measure, the present study also used cross-validated redundancy measures, or effect sizes ( q 2 ), to assess the proposed model and validate the results ( Ringle et al., 2012 ). Hair et al. (2019) suggested that a model exhibiting an effect size q 2 > 0 has predictive relevance ( Table 6 ). This study's results evidenced that it has a 0.15 <0.29 <0.35 (medium) predictive relevance, as 0.02, 0.15, and 0.35 are considered small, medium, and large, respectively ( Cohen, 1998 ). Regarding the goodness-of-fit indices, Hair et al. (2019) suggested the standardized root mean square residual (SRMR) to evaluate the goodness of fit. Standardized root mean square is an absolute measure of fit: a value of zero indicates perfect fit and a value <0.08 is considered good fit ( Hair et al., 2019 ). This study exhibits an adequate model fitness level with an SRMR value of 0.063 ( Table 6 ).
Table 5 reveals that all hypotheses of the study were accepted base on the criterion ( p -value < 0.05). H1a (β = 0.332, t = 10.283, p = 0.001) was confirmed, with the second most robust positive and significant relationship (between social media use and bonding social capital). In addition, this study evidenced a positive and significant relationship between bonding social capital and psychological well-being (β = 0.127, t = 4.077, p = 0.001); therefore, H1b was accepted. Regarding social media use and bridging social capital, the present study found the most robust positive and significant impact (β = 0.439, t = 15.543, p = 0.001); therefore, H2a was accepted. The study also evidenced a positive and significant association between bridging social capital and psychological well-being (β = 0.561, t = 20.953, p = 0.001); thus, H2b was accepted. The present study evidenced a significant effect of social media use on social isolation (β = 0.145, t = 4.985, p = 0.001); thus, H3a was accepted. In addition, this study accepted H3b (β = −0.051, t = 2.01, p = 0.044). Furthermore, this study evidenced a positive and significant effect of social media use on smartphone addiction (β = 0.223, t = 6.241, p = 0.001); therefore, H4a was accepted. Furthermore, the present study found that smartphone addiction has a negative significant influence on psychological well-being (β = −0.068, t = 2.387, p = 0.017); therefore, H4b was accepted. Regarding the relationship between smartphone addiction and phubbing, this study found a positive and significant effect of smartphone addiction on phubbing (β = 0.244, t = 7.555, p = 0.001); therefore, H5 was accepted. Furthermore, the present research evidenced a positive and significant influence of phubbing on psychological well-being (β = 0.137, t = 4.938, p = 0.001); therefore, H6 was accepted. Finally, the study provides interesting findings on the indirect effect of social media use on psychological well-being ( t -value > 1.96 and p -value < 0.05); therefore, H7a–d were accepted.
Furthermore, to test the mediating analysis, Preacher and Hayes's (2008) approach was used. The key characteristic of an indirect relationship is that it involves a third construct, which plays a mediating role in the relationship between the independent and dependent constructs. Logically, the effect of A (independent construct) on C (the dependent construct) is mediated by B (a third variable). Preacher and Hayes (2008) suggested the following: B is a construct acting as a mediator if A significantly influences B, A significantly accounts for variability in C, B significantly influences C when controlling for A, and the influence of A on C decreases significantly when B is added simultaneously with A as a predictor of C. According to Matthews et al. (2018) , if the indirect effect is significant while the direct insignificant, full mediation has occurred, while if both direct and indirect effects are substantial, partial mediation has occurred. This study evidenced that there is partial mediation in the proposed construct ( Table 5 ). Following Preacher and Hayes (2008) this study evidenced that there is partial mediation in the proposed construct, because the relationship between independent variable (social media use) and dependent variable (psychological well-being) is significant ( p -value < 0.05) and indirect effect among them after introducing mediator (bonding social capital, bridging social capital, social isolation, and smartphone addiction) is also significant ( p -value < 0.05), therefore it is evidenced that when there is a significant effect both direct and indirect it's called partial mediation.
The present study reveals that the social and psychological impacts of social media use among University students is becoming more complex as there is continuing advancement in technology, offering a range of affordable interaction opportunities. Based on the 940 valid responses collected, all the hypotheses were accepted ( p < 0.05).
H1a finding suggests that social media use is a significant influencing factor of bonding social capital. This implies that, during a pandemic, social media use enables students to continue their close relationships with family members, friends, and those with whom they have close ties. This finding is in line with prior work of Chan (2015) and Ellison et al. (2007) , who evidenced that social bonding capital is predicted by Facebook use and having a mobile phone. H1b findings suggest that, when individuals believe that social communication can help overcome obstacles to interaction and encourage more virtual self-disclosure, social media use can improve trust and promote the establishment of social associations, thereby enhancing well-being. These findings are in line with those of Gong et al. (2021) , who also witnessed the significant effect of bonding social capital on immigrants' psychological well-being, subsequently calling for the further evidence to confirm the proposed relationship.
The findings of the present study related to H2a suggest that students are more likely to use social media platforms to receive more emotional support, increase their ability to mobilize others, and to build social networks, which leads to social belongingness. Furthermore, the findings suggest that social media platforms enable students to accumulate and maintain bridging social capital; further, online classes can benefit students who feel shy when participating in offline classes. This study supports the previous findings of Chan (2015) and Karikari et al. (2017) . Notably, the present study is not limited to a single social networking platform, taking instead a holistic view of social media. The H2b findings are consistent with those of Bano et al. (2019) , who also confirmed the link between bonding social capital and psychological well-being among University students using WhatsApp as social media platform, as well as those of Chen and Li (2017) .
The H3a findings suggest that, during the COVID-19 pandemic when most people around the world have had limited offline or face-to-face interaction and have used social media to connect with families, friends, and social communities, they have often been unable to connect with them. This is due to many individuals avoiding using social media because of fake news, financial constraints, and a lack of trust in social media; thus, the lack both of offline and online interaction, coupled with negative experiences on social media use, enhances the level of social isolation ( Hajek and König, 2021 ). These findings are consistent with those of Adnan and Anwar (2020) . The H3b suggests that higher levels of social isolation have a negative impact on psychological well-being. These result indicating that, consistent with Choi and Noh (2019) , social isolation is negatively and significantly related to psychological well-being.
The H4a results suggests that substantial use of social media use leads to an increase in smartphone addiction. These findings are in line with those of Jeong et al. (2016) , who stated that the excessive use of smartphones for social media, entertainment (watching videos, listening to music), and playing e-games was more likely to lead to smartphone addiction. These findings also confirm the previous work of Jeong et al. (2016) , Salehan and Negahban (2013) , and Swar and Hameed (2017) . The H4b results revealed that a single unit increase in smartphone addiction results in a 6.8% decrease in psychological well-being. These findings are in line with those of Tangmunkongvorakul et al. (2019) , who showed that students with higher levels of smartphone addiction had lower psychological well-being scores. These findings also support those of Shoukat (2019) , who showed that smartphone addiction inversely influences individuals' mental health.
This suggests that the greater the smartphone addiction, the greater the phubbing. The H5 findings are in line with those of Chatterjee (2020) , Chotpitayasunondh and Douglas (2016) , Guazzini et al. (2019) , and Tonacci et al. (2019) , who also evidenced a significant impact of smartphone addiction and phubbing. Similarly, Chotpitayasunondh and Douglas (2018) corroborated that smartphone addiction is the main predictor of phubbing behavior. However, these findings are inconsistent with those of Vallespín et al. (2017 ), who found a negative influence of phubbing.
The H6 results suggests that phubbing is one of the significant predictors of psychological well-being. Furthermore, these findings suggest that, when phubbers use a cellphone during interaction with someone, especially during the current pandemic, and they are connected with many family members, friends, and relatives; therefore, this kind of action gives them more satisfaction, which simultaneously results in increased relaxation and decreased depression ( Chotpitayasunondh and Douglas, 2018 ). These findings support those of Davey et al. (2018) , who evidenced that phubbing has a significant influence on adolescents and social health students in India.
The findings showed a significant and positive effect of social media use on psychological well-being both through bridging and bonding social capital. However, a significant and negative effect of social media use on psychological well-being through smartphone addiction and through social isolation was also found. Hence, this study provides evidence that could shed light on the contradictory contributions in the literature suggesting both positive (e.g., Chen and Li, 2017 ; Twenge and Campbell, 2019 ; Roberts and David, 2020 ) and negative (e.g., Chotpitayasunondh and Douglas, 2016 ; Jiao et al., 2017 ; Choi and Noh, 2019 ; Chatterjee, 2020 ) effects of social media use on psychological well-being. This study concludes that the overall impact is positive, despite some degree of negative indirect impact.
Theoretical Contributions
This study's findings contribute to the current literature, both by providing empirical evidence for the relationships suggested by extant literature and by demonstrating the relevance of adopting a more complex approach that considers, in particular, the indirect effect of social media on psychological well-being. As such, this study constitutes a basis for future research ( Van Den Eijnden et al., 2016 ; Whaite et al., 2018 ) aiming to understand the impacts of social media use and to find ways to reduce its possible negative impacts.
In line with Kim and Kim (2017) , who stressed the importance of heterogeneous social networks in improving social capital, this paper suggests that, to positively impact psychological well-being, social media usage should be associated both with strong and weak ties, as both are important in building social capital, and hence associated with its bonding and bridging facets. Interestingly, though, bridging capital was shown as having the greatest impact on psychological well-being. Thus, the importance of wider social horizons, the inclusion in different groups, and establishing new connections ( Putnam, 1995 , 2000 ) with heterogeneous weak ties ( Li and Chen, 2014 ) are highlighted in this paper.
Practical Contributions
These findings are significant for practitioners, particularly those interested in dealing with the possible negative impacts of social media use on psychological well-being. Although social media use is associated with factors that negatively impact psychological well-being, particularly smartphone addiction and social isolation, these negative impacts can be lessened if the connections with both strong and weak ties are facilitated and featured by social media. Indeed, social media platforms offer several features, from facilitating communication with family, friends, and acquaintances, to identifying and offering access to other people with shared interests. However, it is important to access heterogeneous weak ties ( Li and Chen, 2014 ) so that social media offers access to wider sources of information and new resources, hence enhancing bridging social capital.
Limitations and Directions for Future Studies
This study is not without limitations. For example, this study used a convenience sampling approach to reach to a large number of respondents. Further, this study was conducted in Mexico only, limiting the generalizability of the results; future research should therefore use a cross-cultural approach to investigate the impacts of social media use on psychological well-being and the mediating role of proposed constructs (e.g., bonding and bridging social capital, social isolation, and smartphone addiction). The sample distribution may also be regarded as a limitation of the study because respondents were mainly well-educated and female. Moreover, although Internet channels represent a particularly suitable way to approach social media users, the fact that this study adopted an online survey does not guarantee a representative sample of the population. Hence, extrapolating the results requires caution, and study replication is recommended, particularly with social media users from other countries and cultures. The present study was conducted in the context of mainly University students, primarily well-educated females, via an online survey on in Mexico; therefore, the findings represent a snapshot at a particular time. Notably, however, the effect of social media use is increasing due to COVID-19 around the globe and is volatile over time.
Two of the proposed hypotheses of this study, namely the expected negative impacts of social media use on social isolation and of phubbing on psychological well-being, should be further explored. One possible approach is to consider the type of connections (i.e., weak and strong ties) to explain further the impact of social media usage on social isolation. Apparently, the prevalence of weak ties, although facilitating bridging social capital, may have an adverse impact in terms of social isolation. Regarding phubbing, the fact that the findings point to a possible positive impact on psychological well-being should be carefully addressed, specifically by psychology theorists and scholars, in order to identify factors that may help further understand this phenomenon. Other suggestions for future research include using mixed-method approaches, as qualitative studies could help further validate the results and provide complementary perspectives on the relationships between the considered variables.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the authors, without undue reservation.
Ethics Statement
The studies involving human participants were reviewed and approved by Jiangsu University. The patients/participants provided their written informed consent to participate in this study.
Author Contributions
All authors listed have made a substantial, direct and intellectual contribution to the work, and approved it for publication.
This study is supported by the National Statistics Research Project of China (2016LY96).
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Abbas, R., and Mesch, G. (2018). Do rich teens get richer? Facebook use and the link between offline and online social capital among Palestinian youth in Israel. Inf. Commun. Soc. 21, 63–79. doi: 10.1080/1369118X.2016.1261168
CrossRef Full Text | Google Scholar
Adnan, M., and Anwar, K. (2020). Online learning amid the COVID-19 pandemic: students' perspectives. J. Pedagog. Sociol. Psychol. 2, 45–51. doi: 10.33902/JPSP.2020261309
PubMed Abstract | CrossRef Full Text | Google Scholar
Ali Qalati, S., Li, W., Ahmed, N., Ali Mirani, M., and Khan, A. (2021). Examining the factors affecting SME performance: the mediating role of social media adoption. Sustainability 13:75. doi: 10.3390/su13010075
Bagozzi, R. P., and Yi, Y. (1988). On the evaluation of structural equation models. J. Acad. Mark. Sci. 16, 74–94. doi: 10.1007/BF02723327
Bagozzi, R. P., Yi, Y., and Phillips, L. W. (1991). Assessing construct validity in organizational research. Admin. Sci. Q. 36, 421–458. doi: 10.2307/2393203
Bano, S., Cisheng, W., Khan, A. N., and Khan, N. A. (2019). WhatsApp use and student's psychological well-being: role of social capital and social integration. Child. Youth Serv. Rev. 103, 200–208. doi: 10.1016/j.childyouth.2019.06.002
Barbosa, B., Chkoniya, V., Simoes, D., Filipe, S., and Santos, C. A. (2020). Always connected: generation Y smartphone use and social capital. Rev. Ibérica Sist. Tecnol. Inf. E 35, 152–166.
Google Scholar
Bekalu, M. A., McCloud, R. F., and Viswanath, K. (2019). Association of social media use with social well-being, positive mental health, and self-rated health: disentangling routine use from emotional connection to use. Health Educ. Behav. 46(2 Suppl), 69S−80S. doi: 10.1177/1090198119863768
Brown, G., and Michinov, N. (2019). Measuring latent ties on Facebook: a novel approach to studying their prevalence and relationship with bridging social capital. Technol. Soc. 59:101176. doi: 10.1016/j.techsoc.2019.101176
Campbell, D. T., and Fiske, D. W. (1959). Convergent and discriminant validation by the multitrait-multimethod matrix. Psychol. Bull. 56, 81–105. doi: 10.1037/h0046016
Carlson, J. R., Zivnuska, S., Harris, R. B., Harris, K. J., and Carlson, D. S. (2016). Social media use in the workplace: a study of dual effects. J. Org. End User Comput. 28, 15–31. doi: 10.4018/JOEUC.2016010102
Chan, M. (2015). Mobile phones and the good life: examining the relationships among mobile use, social capital and subjective well-being. New Media Soc. 17, 96–113. doi: 10.1177/1461444813516836
Chappell, N. L., and Badger, M. (1989). Social isolation and well-being. J. Gerontol. 44, S169–S176. doi: 10.1093/geronj/44.5.s169
Chatterjee, S. (2020). Antecedents of phubbing: from technological and psychological perspectives. J. Syst. Inf. Technol. 22, 161–118. doi: 10.1108/JSIT-05-2019-0089
Chen, H.-T., and Li, X. (2017). The contribution of mobile social media to social capital and psychological well-being: examining the role of communicative use, friending and self-disclosure. Comput. Hum. Behav. 75, 958–965. doi: 10.1016/j.chb.2017.06.011
Choi, D.-H., and Noh, G.-Y. (2019). The influence of social media use on attitude toward suicide through psychological well-being, social isolation, and social support. Inf. Commun. Soc. 23, 1–17. doi: 10.1080/1369118X.2019.1574860
Chotpitayasunondh, V., and Douglas, K. M. (2016). How “phubbing” becomes the norm: the antecedents and consequences of snubbing via smartphone. Comput. Hum. Behav. 63, 9–18. doi: 10.1016/j.chb.2016.05.018
Chotpitayasunondh, V., and Douglas, K. M. (2018). The effects of “phubbing” on social interaction. J. Appl. Soc. Psychol. 48, 304–316. doi: 10.1111/jasp.12506
Cohen, J. (1998). Statistical Power Analysis for the Behavioural Sciences . Hillsdale, NJ: Lawrence Erlbaum Associates.
Davey, S., Davey, A., Raghav, S. K., Singh, J. V., Singh, N., Blachnio, A., et al. (2018). Predictors and consequences of “phubbing” among adolescents and youth in India: an impact evaluation study. J. Fam. Community Med. 25, 35–42. doi: 10.4103/jfcm.JFCM_71_17
David, M. E., Roberts, J. A., and Christenson, B. (2018). Too much of a good thing: investigating the association between actual smartphone use and individual well-being. Int. J. Hum. Comput. Interact. 34, 265–275. doi: 10.1080/10447318.2017.1349250
Dhir, A., Yossatorn, Y., Kaur, P., and Chen, S. (2018). Online social media fatigue and psychological wellbeing—a study of compulsive use, fear of missing out, fatigue, anxiety and depression. Int. J. Inf. Manag. 40, 141–152. doi: 10.1016/j.ijinfomgt.2018.01.012
Dutot, V., and Bergeron, F. (2016). From strategic orientation to social media orientation: improving SMEs' performance on social media. J. Small Bus. Enterp. Dev. 23, 1165–1190. doi: 10.1108/JSBED-11-2015-0160
Ellison, N. B., Steinfield, C., and Lampe, C. (2007). The benefits of Facebook “friends:” Social capital and college students' use of online social network sites. J. Comput. Mediat. Commun. 12, 1143–1168. doi: 10.1111/j.1083-6101.2007.00367.x
Fan, M., Huang, Y., Qalati, S. A., Shah, S. M. M., Ostic, D., and Pu, Z. (2021). Effects of information overload, communication overload, and inequality on digital distrust: a cyber-violence behavior mechanism. Front. Psychol. 12:643981. doi: 10.3389/fpsyg.2021.643981
Fornell, C., and Larcker, D. F. (1981). Evaluating structural equation models with unobservable variables and measurement error. J. Market. Res. 18, 39–50. doi: 10.1177/002224378101800104
Gökçearslan, S., Uluyol, Ç., and Sahin, S. (2018). Smartphone addiction, cyberloafing, stress and social support among University students: a path analysis. Child. Youth Serv. Rev. 91, 47–54. doi: 10.1016/j.childyouth.2018.05.036
Gong, S., Xu, P., and Wang, S. (2021). Social capital and psychological well-being of Chinese immigrants in Japan. Int. J. Environ. Res. Public Health 18:547. doi: 10.3390/ijerph18020547
Guazzini, A., Duradoni, M., Capelli, A., and Meringolo, P. (2019). An explorative model to assess individuals' phubbing risk. Fut. Internet 11:21. doi: 10.3390/fi11010021
Hair, J. F., Risher, J. J., Sarstedt, M., and Ringle, C. M. (2019). When to use and how to report the results of PLS-SEM. Eur. Bus. Rev. 31, 2–24. doi: 10.1108/EBR-11-2018-0203
Hair, J. F., Sarstedt, M., Pieper, T. M., and Ringle, C. M. (2012). The use of partial least squares structural equation modeling in strategic management research: a review of past practices and recommendations for future applications. Long Range Plann. 45, 320–340. doi: 10.1016/j.lrp.2012.09.008
Hair, J. F., Sarstedt, M., Ringle, C. M., and Gudergan, S. P. (2017). Advanced Issues in Partial Least Squares Structural Equation Modeling. Thousand Oaks, CA: Sage.
Hajek, A., and König, H.-H. (2021). Social isolation and loneliness of older adults in times of the CoViD-19 pandemic: can use of online social media sites and video chats assist in mitigating social isolation and loneliness? Gerontology 67, 121–123. doi: 10.1159/000512793
Henseler, J., Ringle, C. M., and Sinkovics, R. R. (2009). “The use of partial least squares path modeling in international marketing,” in New Challenges to International Marketing , Vol. 20, eds R.R. Sinkovics and P.N. Ghauri (Bigley: Emerald), 277–319.
Holliman, A. J., Waldeck, D., Jay, B., Murphy, S., Atkinson, E., Collie, R. J., et al. (2021). Adaptability and social support: examining links with psychological wellbeing among UK students and non-students. Fron. Psychol. 12:636520. doi: 10.3389/fpsyg.2021.636520
Jeong, S.-H., Kim, H., Yum, J.-Y., and Hwang, Y. (2016). What type of content are smartphone users addicted to? SNS vs. games. Comput. Hum. Behav. 54, 10–17. doi: 10.1016/j.chb.2015.07.035
Jiao, Y., Jo, M.-S., and Sarigöllü, E. (2017). Social value and content value in social media: two paths to psychological well-being. J. Org. Comput. Electr. Commer. 27, 3–24. doi: 10.1080/10919392.2016.1264762
Jordan, P. J., and Troth, A. C. (2019). Common method bias in applied settings: the dilemma of researching in organizations. Austr. J. Manag. 45, 3–14. doi: 10.1177/0312896219871976
Karikari, S., Osei-Frimpong, K., and Owusu-Frimpong, N. (2017). Evaluating individual level antecedents and consequences of social media use in Ghana. Technol. Forecast. Soc. Change 123, 68–79. doi: 10.1016/j.techfore.2017.06.023
Kemp, S. (January 30, 2020). Digital 2020: 3.8 billion people use social media. We Are Social . Available online at: https://wearesocial.com/blog/2020/01/digital-2020-3-8-billion-people-use-social-media .
Kim, B., and Kim, Y. (2017). College students' social media use and communication network heterogeneity: implications for social capital and subjective well-being. Comput. Hum. Behav. 73, 620–628. doi: 10.1016/j.chb.2017.03.033
Kim, K., Milne, G. R., and Bahl, S. (2018). Smart phone addiction and mindfulness: an intergenerational comparison. Int. J. Pharmaceut. Healthcare Market. 12, 25–43. doi: 10.1108/IJPHM-08-2016-0044
Kircaburun, K., Alhabash, S., Tosuntaş, S. B., and Griffiths, M. D. (2020). Uses and gratifications of problematic social media use among University students: a simultaneous examination of the big five of personality traits, social media platforms, and social media use motives. Int. J. Mental Health Addict. 18, 525–547. doi: 10.1007/s11469-018-9940-6
Leong, L.-Y., Hew, T.-S., Ooi, K.-B., Lee, V.-H., and Hew, J.-J. (2019). A hybrid SEM-neural network analysis of social media addiction. Expert Syst. Appl. 133, 296–316. doi: 10.1016/j.eswa.2019.05.024
Li, L., Griffiths, M. D., Mei, S., and Niu, Z. (2020a). Fear of missing out and smartphone addiction mediates the relationship between positive and negative affect and sleep quality among Chinese University students. Front. Psychiatr. 11:877. doi: 10.3389/fpsyt.2020.00877
Li, W., Qalati, S. A., Khan, M. A. S., Kwabena, G. Y., Erusalkina, D., and Anwar, F. (2020b). Value co-creation and growth of social enterprises in developing countries: moderating role of environmental dynamics. Entrep. Res. J. 2020:20190359. doi: 10.1515/erj-2019-0359
Li, X., and Chen, W. (2014). Facebook or Renren? A comparative study of social networking site use and social capital among Chinese international students in the United States. Comput. Hum. Behav . 35, 116–123. doi: 10.1016/j.chb.2014.02.012
Matthews, L., Hair, J. F., and Matthews, R. (2018). PLS-SEM: the holy grail for advanced analysis. Mark. Manag. J. 28, 1–13.
Meshi, D., Cotten, S. R., and Bender, A. R. (2020). Problematic social media use and perceived social isolation in older adults: a cross-sectional study. Gerontology 66, 160–168. doi: 10.1159/000502577
Mou, J., Shin, D.-H., and Cohen, J. (2017). Understanding trust and perceived usefulness in the consumer acceptance of an e-service: a longitudinal investigation. Behav. Inf. Technol. 36, 125–139. doi: 10.1080/0144929X.2016.1203024
Nunnally, J. (1978). Psychometric Methods . New York, NY: McGraw-Hill.
Oghazi, P., Karlsson, S., Hellström, D., and Hjort, K. (2018). Online purchase return policy leniency and purchase decision: mediating role of consumer trust. J. Retail. Consumer Serv. 41, 190–200.
Pang, H. (2018). Exploring the beneficial effects of social networking site use on Chinese students' perceptions of social capital and psychological well-being in Germany. Int. J. Intercult. Relat. 67, 1–11. doi: 10.1016/j.ijintrel.2018.08.002
Podsakoff, P. M., MacKenzie, S. B., Lee, J.-Y., and Podsakoff, N. P. (2003). Common method biases in behavioral research: a critical review of the literature and recommended remedies. J. Appl. Psychol. 88, 879–903. doi: 10.1037/0021-9010.88.5.879
Podsakoff, P. M., and Organ, D. W. (1986). Self-reports in organizational research: problems and prospects. J. Manag. 12, 531–544. doi: 10.1177/014920638601200408
Preacher, K. J., and Hayes, A. F. (2008). Asymptotic and resampling strategies for assessing and comparing indirect effects in multiple mediator models. Behav Res. Methods 40, 879–891. doi: 10.3758/brm.40.3.879
Primack, B. A., Shensa, A., Sidani, J. E., Whaite, E. O., yi Lin, L., Rosen, D., et al. (2017). Social media use and perceived social isolation among young adults in the US. Am. J. Prev. Med. 53, 1–8. doi: 10.1016/j.amepre.2017.01.010
Putnam, R. D. (1995). Tuning in, tuning out: the strange disappearance of social capital in America. Polit. Sci. Polit. 28, 664–684. doi: 10.2307/420517
Putnam, R. D. (2000). Bowling Alone: The Collapse and Revival of American Community . New York, NY: Simon and Schuster.
Qalati, S. A., Ostic, D., Fan, M., Dakhan, S. A., Vela, E. G., Zufar, Z., et al. (2021). The general public knowledge, attitude, and practices regarding COVID-19 during the lockdown in Asian developing countries. Int. Q. Commun. Health Educ. 2021:272684X211004945. doi: 10.1177/0272684X211004945
Reer, F., Tang, W. Y., and Quandt, T. (2019). Psychosocial well-being and social media engagement: the mediating roles of social comparison orientation and fear of missing out. New Media Soc. 21, 1486–1505. doi: 10.1177/1461444818823719
Ringle, C., Wende, S., and Becker, J. (2015). SmartPLS 3 [software] . Bönningstedt: SmartPLS.
Ringle, C. M., Sarstedt, M., and Straub, D. (2012). A critical look at the use of PLS-SEM in “MIS Quarterly.” MIS Q . 36, iii–xiv. doi: 10.2307/41410402
Roberts, J. A., and David, M. E. (2020). The social media party: fear of missing out (FoMO), social media intensity, connection, and well-being. Int. J. Hum. Comput. Interact. 36, 386–392. doi: 10.1080/10447318.2019.1646517
Salehan, M., and Negahban, A. (2013). Social networking on smartphones: when mobile phones become addictive. Comput. Hum. Behav. 29, 2632–2639. doi: 10.1016/j.chb.2013.07.003
Sarstedt, M., and Cheah, J.-H. (2019). Partial least squares structural equation modeling using SmartPLS: a software review. J. Mark. Anal. 7, 196–202. doi: 10.1057/s41270-019-00058-3
Schinka, K. C., VanDulmen, M. H., Bossarte, R., and Swahn, M. (2012). Association between loneliness and suicidality during middle childhood and adolescence: longitudinal effects and the role of demographic characteristics. J. Psychol. Interdiscipl. Appl. 146, 105–118. doi: 10.1080/00223980.2011.584084
Shi, S., Mu, R., Lin, L., Chen, Y., Kou, G., and Chen, X.-J. (2018). The impact of perceived online service quality on swift guanxi. Internet Res. 28, 432–455. doi: 10.1108/IntR-12-2016-0389
Shoukat, S. (2019). Cell phone addiction and psychological and physiological health in adolescents. EXCLI J. 18, 47–50. doi: 10.17179/excli2018-2006
Shrestha, N. (2021). Factor analysis as a tool for survey analysis. Am. J. Appl. Math. Stat. 9, 4–11. doi: 10.12691/ajams-9-1-2
Stouthuysen, K., Teunis, I., Reusen, E., and Slabbinck, H. (2018). Initial trust and intentions to buy: The effect of vendor-specific guarantees, customer reviews and the role of online shopping experience. Electr. Commer. Res. Appl. 27, 23–38. doi: 10.1016/j.elerap.2017.11.002
Swar, B., and Hameed, T. (2017). “Fear of missing out, social media engagement, smartphone addiction and distraction: moderating role of self-help mobile apps-based interventions in the youth ,” Paper presented at the 10th International Conference on Health Informatics (Porto).
Tangmunkongvorakul, A., Musumari, P. M., Thongpibul, K., Srithanaviboonchai, K., Techasrivichien, T., Suguimoto, S. P., et al. (2019). Association of excessive smartphone use with psychological well-being among University students in Chiang Mai, Thailand. PLoS ONE 14:e0210294. doi: 10.1371/journal.pone.0210294
Tateno, M., Teo, A. R., Ukai, W., Kanazawa, J., Katsuki, R., Kubo, H., et al. (2019). Internet addiction, smartphone addiction, and hikikomori trait in Japanese young adult: social isolation and social network. Front. Psychiatry 10:455. doi: 10.3389/fpsyt.2019.00455
Tefertiller, A. C., Maxwell, L. C., and Morris, D. L. (2020). Social media goes to the movies: fear of missing out, social capital, and social motivations of cinema attendance. Mass Commun. Soc. 23, 378–399. doi: 10.1080/15205436.2019.1653468
Tehseen, S., Qureshi, Z. H., Johara, F., and Ramayah, T. (2020). Assessing dimensions of entrepreneurial competencies: a type II (reflective-formative) measurement approach using PLS-SEM. J. Sustain. Sci. Manage. 15, 108–145.
Tehseen, S., Ramayah, T., and Sajilan, S. (2017). Testing and controlling for common method variance: a review of available methods. J. Manag. Sci. 4, 146–165. doi: 10.20547/jms.2014.1704202
Tonacci, A., Billeci, L., Sansone, F., Masci, A., Pala, A. P., Domenici, C., et al. (2019). An innovative, unobtrusive approach to investigate smartphone interaction in nonaddicted subjects based on wearable sensors: a pilot study. Medicina (Kaunas) 55:37. doi: 10.3390/medicina55020037
Twenge, J. M., and Campbell, W. K. (2019). Media use is linked to lower psychological well-being: evidence from three datasets. Psychiatr. Q. 90, 311–331. doi: 10.1007/s11126-019-09630-7
Vallespín, M., Molinillo, S., and Muñoz-Leiva, F. (2017). Segmentation and explanation of smartphone use for travel planning based on socio-demographic and behavioral variables. Ind. Manag. Data Syst. 117, 605–619. doi: 10.1108/IMDS-03-2016-0089
Van Den Eijnden, R. J., Lemmens, J. S., and Valkenburg, P. M. (2016). The social media disorder scale. Comput. Hum. Behav. 61, 478–487. doi: 10.1016/j.chb.2016.03.038
Whaite, E. O., Shensa, A., Sidani, J. E., Colditz, J. B., and Primack, B. A. (2018). Social media use, personality characteristics, and social isolation among young adults in the United States. Pers. Indiv. Differ. 124, 45–50. doi: 10.1016/j.paid.2017.10.030
Williams, D. (2006). On and off the'net: scales for social capital in an online era. J. Comput. Mediat. Commun. 11, 593–628. doi: 10.1016/j.1083-6101.2006.00029.x
Keywords: smartphone addiction, social isolation, bonding social capital, bridging social capital, phubbing, social media use
Citation: Ostic D, Qalati SA, Barbosa B, Shah SMM, Galvan Vela E, Herzallah AM and Liu F (2021) Effects of Social Media Use on Psychological Well-Being: A Mediated Model. Front. Psychol. 12:678766. doi: 10.3389/fpsyg.2021.678766
Received: 10 March 2021; Accepted: 25 May 2021; Published: 21 June 2021.
Reviewed by:
Copyright © 2021 Ostic, Qalati, Barbosa, Shah, Galvan Vela, Herzallah and Liu. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY) . The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Sikandar Ali Qalati, sidqalati@gmail.com ; 5103180243@stmail.ujs.edu.cn ; Esthela Galvan Vela, esthela.galvan@cetys.mx
† ORCID: Dragana Ostic orcid.org/0000-0002-0469-1342 Sikandar Ali Qalati orcid.org/0000-0001-7235-6098 Belem Barbosa orcid.org/0000-0002-4057-360X Esthela Galvan Vela orcid.org/0000-0002-8778-3989 Feng Liu orcid.org/0000-0001-9367-049X
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Cyberpsychol Behav Soc Netw

Twenty-Five Years of Social Media: A Review of Social Media Applications and Definitions from 1994 to 2019
Thomas aichner.
1 Department of Business Administration, John Cabot University, Rome, Italy.
Matthias Grünfelder
2 Johannes Kepler University Linz, Linz, Austria.
Oswin Maurer
3 Faculty of Economics and Management, Free University of Bozen-Bolzano, Bozen-Bolzano, Italy.
Deni Jegeni
In this article, the authors present the results from a structured review of the literature, identifying and analyzing the most quoted and dominant definitions of social media (SM) and alternative terms that were used between 1994 and 2019 to identify their major applications. Similarities and differences in the definitions are highlighted to provide guidelines for researchers and managers who use results from previous research to further study SM or to find practical applications. In other words, when reading an article about SM, it is essential to understand how the researchers defined SM and how results from articles that use different definitions can be compared. This article is intended to act as a guideline for readers of those articles.
Introduction
The term “social media” (SM) was first used in 1994 on a Tokyo online media environment, called Matisse. 1 It was in these early days of the commercial Internet that the first SM platforms were developed and launched. Over time, both the number of SM platforms and the number of active SM users have increased significantly, making it one of the most important applications of the Internet.
With a similarly fast pace, businesses have moved their marketing interests toward SM platforms. The presence of both businesses and users on SM has further led to a shift in how companies interact with their customers, who are additionally no longer limited to a passive role in their relationship with a company. 2 Customers give feedback, ask questions, and expect quick and customized answers to their specific problems. In addition, customers post text, pictures, and videos. Managers came to the understanding that the brand transition to SM ultimately involves a re-casting of the customer relationship, where the customer has become an ally or an enemy, not an audience. 3
In research, SM is generally used as an umbrella term that describes a variety of online platforms, including blogs, business networks, collaborative projects, enterprise social networks (SN), forums, microblogs, photo sharing, products review, social bookmarking, social gaming, SN, video sharing, and virtual worlds. 4 Given this broad spectrum of SM platforms, the applications of SM are quite diverse and not limited to sharing holiday snapshots or advertising and promotion.
As of January 2020, there are more than 110,000 publications that have the term “social media” in their title. Over the past 25 years in which these works were published, countless researchers have formulated quite varying definitions of SM—sometimes using alternative terms. In this period, the perceptions and understanding of what SM is, what it includes, and what it represents have also varied considerably. This can make it difficult for both researchers and companies to interpret and apply research findings; for example , when referring to SM in general, rather than referring to a specific type of SM, such as SN. It can be problematic to quote previous research that was carried out exclusively on one SM platform as being generalizable to SM, or to refer to results from research that defined SM as being more or less inclusive in terms of which platforms qualify as SM and which do not.
Major Applications of SM
This section serves as the background of SM functions, rather than how the definition has changed. It provides a general, although not comprehensive, overview of some of the most important applications of SM over the past two and a half decades. This is important, as it highlights that SM cover a broad variety of scopes with specific functions and applications that can differ greatly between the different types of SM. Consequently, also the purpose and the users' perceived value of using SM varies. From a research perspective, this section serves as a foundation for classifying and discussing the SM definitions that are presented in the following chapters.
Socializing with friends and family
Although not all SM platforms are specifically designed to facilitate socialization between its users, it may be considered one of the most apparent commonalities of all types of SM. 4 Sometimes referred to as online communities, these SM platforms are valuable given that people often do not perceive a difference between virtual friends and real friends, as long as they feel supported and belong to a community of like-minded individuals. 5 The SM helps to strengthen relationships through the sharing of important life events in the form of status updates, photos, etc., reinforcing at the same time their in-person encounters as well. 6
The SM has also become a common tool for communication in families. A study conducted by Sponcil and Gitimu 7 showed that for 91.7 percent of students the main reason for using SM is communicating with family and friends. In addition, 50 percent of the students communicated with their family and friends every day, and another 40 percent at least a few days a week. Williams and Merten 8 suggest that by using SM in everyday life, people strengthen the relationships with family. Especially in relation to globalization and constant migration, it has become a vital tool for maintaining contact within migrant families. The need for transnational communication between family members and the people they left behind is of great importance. 9
Romance and flirting
Several studies suggest that SM significantly influences the romantic aspects of life. Aside from facilitating human interaction, communication technologies are also shaping and defining our relationships. 10 It has been shown that SM is important in the starting phases of a relationship and has a significant influence on the relationship of many couples in the long run. 11 The SM can help when starting a romantic relationship, for example , contacting a crush through SM can have special benefits for introverts, who otherwise would avoid face-to-face contact and would otherwise communicate less. 7 Moreover, in some cases, online dating is preferable to live dating, as it gives the same feeling and allows users to avoid unnecessary discomforts. 11 Finally, rejection on SM is less painful compared with face-to-face rejection. 10 Further, users can contemplate their responses and do not have to worry about their physical appearance while conversing/chatting online, making it a less stressful environment to flirt with people on SM than face-to-face conversations. 12
Interacting with companies and brands
It is estimated that close to 100 percent of larger companies (both B2C and B2B) are using some sort of SM platform to inform their customers, gather information, receive feedback, provide after-sales service or consultancy, and promote their products or services. The key characteristic that makes SM so relevant for companies is the fact that SM allows for two-way communication between the brand and the customer. 13 Sometimes referred to as “social customer relationship management,” 14 SM can be viewed as an effective tool used to get closer to the customer. However, some studies suggest that what customers seek is somewhat different from what companies offer through SM. 14 Customers are mainly interested in communicating easily and quickly with the company. From a business perspective, the company wants to make sure customers receive the right information in a timely manner, linking the customer closer to the brand and, simultaneously, controlling the flow of information. Successful SM managers understand how an SM platform works and is used by its customers, and they then develop corporate communication tools that fit the behavior of their users. Many researchers highlight the need for customer relationship management to adapt to the rise of SM 2 to efficiently manage relationships with modern, connected, and empowered customers.
Job seeking and professional networking
Another application of SM is to connect job seekers with employers. The vast majority of Fortune 500 companies use LinkedIn for talent acquisition. 15 With more than 660 million users in 2020, it is an important tool for companies searching to expand their talent pool. This pool of individuals is extended, as the nature of SM also allows recruiters to identify and target, apart from active users, talented candidates who are passive or semi-passive and lure them to prospective job positions. 16 In fact, through SM platforms such as LinkedIn, Facebook, and Twitter, recruiters can post job advertisements to lure potential applicants who are not actively looking for a job. 17 Rather than the costly and time-consuming traditional ways of staffing with interviews and tests, hiring through SM offers recruiters the benefit of free access to prospects' profiles and an instant means of communication. For users, LinkedIn profiles allow them to create an idealized portrait by displaying their skills to recruiters and peers. 18 Indeed, LinkedIn asks members to highlight their relevant skills, promoting their abilities and strengths, urging them to complete their profiles through getting recommendations and praise from peers/colleagues and clients for their performance or skills. 19
Doing business
The SM has a considerable impact on how companies approach clients and vice versa. In addition, SM utilizing SM as a means of understanding and informing customers has become imperative for businesses to remain competitive. The SM providers have created possibilities for companies to improve their internal operations and communicate in new ways with customers, other businesses, and suppliers. 20 At the same time, companies can actively engage customers, encouraging them to become advocates of their brands. 2 This is certainly important, as users can create online customer communities, which potentially add value to the brand beyond just increased sales. 20 The engagement of customers can be beneficial, as they will frequently interact with the brand and share positive word-of-mouth since they have become more emotionally attached to the brand. 21 This electronic word-of-mouth created in SM communities helps consumers in their purchasing decisions. 22 This suggestion is important given that customers are actually more interested in other users' recommendations and word-of-mouth rather than the vendor-created product information. 23
Research questions
Reviewing the existent literature about SM applications inevitably leads to the question of whether the researchers had the same definition in mind when talking about SM, SN, online communities, and the like. It is also apparent that the focus of the researcher's interest has changed over time, and that the time when the research was conducted could have an impact on how the findings should be interpreted. Therefore, the remainder of this article aims at answering the following research questions (RQ):
RQ1: How has the definition of social media changed from 1994 to 2019? RQ2: What are the differences and commonalities in social media definitions from 1994 to 2019?
To answer the two RQ, we decided to conduct a systematic literature review (SLR). Using a multi-step SLR approach as recommended by Tranfield et al. 24 ( Fig. 1 ), we structurally examined the literature between 1994 and 2019 to find all relevant SM definitions to identify the major differences and commonalities.

Structure and process of the systematic literature review.
After identifying 88 potential papers, all the articles were read to find original definitions for SM or related terms. In addition, we used backward and forward snowballing, two methods frequently employed in academic research to find additional relevant sources based on the references used in the original publication (backward snowballing) and searched papers that cited the article (forward snowballing), respectively. 25 In combination with the SLR, the backward snowballing led to the identification of a total number of 21 original definitions, including some definitions that were published in books and conference proceedings, which were not included in the SLR.
In this chapter, we present all major definitions of SM (and synonymous terms) that were formulated from 1994 to 2019 ( Table 1 ). Table 1 further includes details about the source and the number of citations according to Google Scholar as of August 2020.
Social Media Definitions with Author Names, Source, and the Number of Citations As of August 2020
Before we assess the meaning and compare the definitions in terms of the two RQ, a few quantitative results are provided. Analyzing the 21 definitions, we found a lexical density (i.e., the percentage of nouns, adjectives, verbs, and adverbs) of 57.5 percent. The most frequently used word with 23 occurrences is “social,” followed by “people” with 12 occurrences, and “virtual,” “content,” “user,” and “network” with 8 occurrences each. In terms of two-word phrases, “social network[s]” (8 occurrences) is followed by “social media” and “social networking” (5 occurrences each), as well as “virtual communities” (VC) (4 occurrences).
Notably, the first formal definition is from 1996 and uses “computer-supported social networks” or “CSSNs,” although the term “SM” was coined about 2 years earlier. Later, researchers used different terms such as “virtual communities,” “social networks,” “social networking services,” “online social network,” “social networking sites,” “social network sites,” and “social media.” Although there are small variations in these terms, they can be classified into three categories: VC, SN, and SM. It is important to mention that all these definitions describe the same concept, but with different terms. Assessing the SM definitions that resulted from the SLR reveals that from 1997 to 2002, VC was the dominant term. In contrast, SN was used over a longer period, but it was dominant from 2005 to 2009. It was only in 2010 that researchers started using predominantly SM. But how did the definitions—independent from their terminology—change?
Throughout the observed period, the role of SM, as an enabler for human interaction as well as an avenue to connect with other users, has been a constant in defining SM. In early definitions, the focus was mainly on people and how people interact, whereas later definitions (after 2010) have largely substituted the term “people” with “user” and placed more focus on generating and sharing content. This changed focus, with regard to both the application of SM and the terminology of people versus user, may also reflect the increasingly important role of anonymity in SM. 47
The role of user-generated content is not reflected in early definitions, whereas it has become a central part of recent definitions. It was Kaplan and Haenlein 38 who first mentioned “creation,” whereas later definitions use terms such as “user-supplied content” and “user-driven platforms” in addition to “user-generated content,” which is the common term used in research and practice today.
Another notable change is that until 2009, several researchers included the common interests that linked people with each other, whereas this link is completely missing in post-2010 definitions. Again, this may be reflected by the fact that in the early days, SM users were mostly close or loosely related friends communicating with each other, whereas in recent years, SM has evolved to a set of media that are also used as a powerful tool by companies, celebrities, and influencers to reach the masses. 48
Finally, although sharing information and content is generally not the central aspect in defining SM, the terminology has changed over time. Until 2010, researchers used “exchange” or “upload,” which were substituted with the term “share” in subsequent years. The underlying meaning, however, remained the same.
Conclusions
About 60,000 articles have cited the SM definitions summarized in this article. Therefore, the value this research provides goes beyond a simple overview of the definitions and major applications of SM in the 25 years, since the term was originally coined. The result is a timeline of SM definitions that helps researchers and practitioners to quickly put the results of previous research in perspective and to avoid time-consuming research of the single definitions in different papers. Why is this necessary? This is because, based on the definition, the results may need to be interpreted in a more or less different way.
One notable result is that, although SM is one of the main research areas in social sciences (and beyond) and its landscape has been changing quickly, only a handful of scholars have made an effort to develop a definition of SM. Although some elements, for example , the fact that SM connects people, are common, the definitions are rather different from each other. The commonalities and differences highlighted in the previous section allow for the division of the definitions into two main streams: those published before 2010 and after 2010. Before 2010, SM was commonly approached as a tool of connectivity for people with common interests. After 2010, the focus changed to creating and sharing user-generated content.
These results are in line with previous research about the evolution of SM literature, which concluded that SM definitions changed over time, namely from platforms for socializing in the past to tools for information aggregation. 45 Similarly, Kapoor et al. 45 found that there was an evolution in SM definitions and a cut in the early 2010. Our research shows that there is no single or commonly accepted definition, but that several definitions have been co-existing and found broad acceptance in literature.
Future SM researchers can use these findings to better compare SM articles and avoid flaws in their theory or methodological design. Especially when comparing the results of empirical studies, it may be critical to consider both when the study was conducted and which SM definition was used as a basis for hypothesis development and data analysis. In addition, this article gives SM researchers the possibility to make an informed choice of which SM definition to use for their studies.
Given the method employed to identify the SM definitions, we are confident that this is the most comprehensive overview that includes all major publications. However, the results may be limited by the original search terms used to identify the papers to be included in the SLR. Although the use of backward snowballing should have helped in minimizing this risk, there may still be some less explicit definitions of SM that were not included in this article. In addition, non-English articles and other gray literature were not considered, which is common criticism in academic research. Future research could also try to identify the differences in how SM is defined by researchers from different scientific backgrounds, for example , marketing versus medicine versus psychology versus anthropology versus engineering versus information technology. It would also be insightful to see whether there are tendencies of certain researchers, for example , from engineering, to base their research on specific definitions rather than on others. For example, if one definition is dominant in engineering but not in medical research, this would imply that interdisciplinary research about SM applications needs to be compared more carefully, as the basic definition differs. Similarly, it would be interesting to link the use of SM definitions to the cultural or national context of where the research was carried out, for example , to identify whether European versus American versus Asian researchers have a generally different understanding of SM and its applications. These possible cultural differences in the definition or selection of an SM definition as a basis for research could be linked to the fact that in different countries and cultural clusters different SM platforms are more or less popular. 49 Overall, our research will help compare findings from SM literature more easily and avoid misinterpretations of past and future research.
Author Disclosure Statement
No competing financial interests exist.
Funding Information
This work was supported by the Open Access Publishing Fund of the Free University of Bozen-Bolzano.
Online social networks security and privacy: comprehensive review and analysis
- Survey and State of the Art
- Open access
- Published: 01 June 2021
- Volume 7 , pages 2157–2177, ( 2021 )
Cite this article
You have full access to this open access article

- Ankit Kumar Jain ORCID: orcid.org/0000-0002-9482-6991 1 ,
- Somya Ranjan Sahoo 2 &
- Jyoti Kaubiyal 1
60k Accesses
70 Citations
14 Altmetric
Explore all metrics
With fast-growing technology, online social networks (OSNs) have exploded in popularity over the past few years. The pivotal reason behind this phenomenon happens to be the ability of OSNs to provide a platform for users to connect with their family, friends, and colleagues. The information shared in social network and media spreads very fast, almost instantaneously which makes it attractive for attackers to gain information. Secrecy and surety of OSNs need to be inquired from various positions. There are numerous security and privacy issues related to the user’s shared information especially when a user uploads personal content such as photos, videos, and audios. The attacker can maliciously use shared information for illegitimate purposes. The risks are even higher if children are targeted. To address these issues, this paper presents a thorough review of different security and privacy threats and existing solutions that can provide security to social network users. We have also discussed OSN attacks on various OSN web applications by citing some statistics reports. In addition to this, we have discussed numerous defensive approaches to OSN security. Finally, this survey discusses open issues, challenges, and relevant security guidelines to achieve trustworthiness in online social networks.
Similar content being viewed by others

Social Media Account Hacking Using Kali Linux-Based Tool BeEF
Fighting against phishing attacks: state of the art and future challenges.
Open-source intelligence: a comprehensive review of the current state, applications and future perspectives in cyber security
Avoid common mistakes on your manuscript.
Introduction
When the internet became popular in the mid-1990’s it made it possible to share information in ways that were never possible before. But a personal aspect was still lacking in sharing information [ 1 ]. And then in the early 2000s, social networking sites introduce a personal flavor to online information sharing which was embraced by the masses [ 2 ]. Social networking is the practice of expanding one’s contact with other individuals mostly through social media sites like Facebook, Twitter, Instagram, LinkedIn and many more [ 3 ]. It can be used for both personal and business reasons [ 4 ]. It brings people together to talk, share ideas and interests and make new friends. Basically, it helps people from different geographical regions to collaborate [ 5 ]. Social networking platforms have always been found to be easy to use. This is the reason social media sites are growing exponentially in popularity and numbers. Figure 1 shows the basic constituents of social networks and the fields in which it is playing a major role [ 6 ]. As the figure shows, social networking can be used for entertainment, building business opportunities, making a career, improving one’s social skills, and forging relationships with other individuals [ 7 ]. Facebook and Myspace are among the most preferred social networking sites Since a large chunk of the online population utilize social media platform, it has become a significant medium to promote business, awareness campaign.
Constituents of online social networks
Since people consider social media as a personal communication tool, the importance to safeguard their information stored in these social networking sites is often taken for granted. With the passage of time, people are putting more and more information in different forms on social networks which can lead to unprecedented access to people’s and business information. The amount of information stored in social networks is very enticing for adversaries whose aim is to harm someone. They can create havoc worldwide with this huge amount of information in hands. Moreover, social media has become a great medium of advertisement for marketers and if they do not take social media security issues seriously enough, they make themselves vulnerable to a wide variety of threats and put their confidential data at risk. Also, social network can be classified into many types based on their uses. Social networks can be classified into four broad classifications namely, ‘social connections’, ‘multimedia sharing’, ‘professional’ and ‘discussion forums’. This section discusses the types of social networking sites and vulnerabilities and instances of phishing that have occurred on said classifications. Current problems are also stated with an emphasis on malicious content-based phishing attacks. Figure 2 shows different types of social networking sites can broadly be classified into.
Types of social networking sites
In Social connection, People use this network to connect with people and brands online. Although there are other types of social networking sites available online, this type certainly defines social media now. Sites that come under this category are ‘Facebook’, ‘Twitter’, ‘Google + ’, ‘Myspace’. Although there are advantages of using these sites, it has some disadvantages also. These sites are vulnerable to phishing attacks in numerous ways. An intruder can make a portal that looks identical to a Facebook page. And then may lure users into entering into their credentials in different ways. Some of these methods are:
Sending fake messages which states that their Facebook account is about to be disabled in a few days.
The user may be tricked into clicking a link from the personal message sent by his friend stating that someone has uploaded personal pictures of the user in the given link.
Some attackers send a message claiming that the user’s account needs to be updated to use it further. And a link is given to download that update which contains an address of the malicious site.
Also, multimedia sharing networks are used to share pictures, videos, live videos, and other media online. They give an opportunity to users and brands to share their media online. Sites under this category are ‘YouTube’, ‘Flickr’, ‘Instagram’, ‘Snapchat’. Nowadays every social media has an “inbox” feature where anyone can send messages to their friends and chat with them. Recently, YouTube has also released this feature. This gives the attacker a great opportunity to phish his target. He can send a shortened URL in the message which redirects the user to a malicious website [ 8 ]. Since it is not easy to recognize a shortened URL, whether it is legitimate or not, attackers take advantage and obfuscate their malicious content in shortened URLs. Professional social networks are developed to provide career opportunities to their users. It may provide a general forum or may be focused on specific occupations or interest depending on the nature of the website. ‘LinkedIn’, ‘Classroom2.0’, ‘Pinterest’ are some of the examples of professional social networking sites. Since these social networking sites contain all professional information of the user including email id, an attacker can use these details to send a victim a personalized mail. These emails may be like emails claiming prize-money which contains the malicious link. Similarly, in discussion forums, people use these networks to discuss topics and share opinions. These networks are an excellent resource for market research and one of the oldest forms of social network. ‘Reddit’, ‘Quora’ and ‘Digg’ are some examples of popular discussion forums. In these forums, people also share links related to their research so that users can get more information about their topic of research. Some illegitimate users share malicious links to lead astray users to some phishing websites. In this way, phishing can also be done in discussion forums.
The lasting part of our paper is incorporated as follows. We present different statistics for OSN security in " Statistics of online social network and media " section. Segment 3 particularizes the positive and negative impacts of online social networking. In Segment 4, we depict different threats that affect the user behavior in OSN platform. We describe the reason behind the OSN security issues in-depth in Segment 5. In " Solutions for various threats " section, we discuss the defensive solutions for various threats. For user awareness in " Security-guidelines for OSNs user " section, we portray certain security rules to protect your system, account, and information. In the following section, i.e. in " Open research issues and challenges " section, we portray the open research issues and challenges for OSN users. At last, we conclude our work in " Conclusion " section.
Statistics of online social network and media
Near about 4 billion users exist in the online internet landscape [ 9 ]. Out of the total population on the internet, there are 2.7 billion monthly dynamic clients on Facebook, 330 million active users on Twitter, 320 million active users on Pinterest, as of Dec 30, 2020 [ 10 ]. Figure 3 illustrates the number of users on different social networking platforms [ 11 ]. According to a report from Zephoria, there is a 16 percent increase year over year in monthly active users of Facebook. Seven new profiles are created every second [ 12 ]. Users uploaded a total 350 million pictures per day. On average 510,000 comments are posted in every 60 s on Facebook, 298,000 statuses are updated, and 136,000 photos are uploaded. Since a huge amount of data is uploaded on Facebook, there is a high chance of having security risks. Anyone can post malicious content hidden inside multimedia data or with shortened uniform resource locators (URLs). There are around 83 million fake profiles which can be of illegitimate users or of professionals doing testing and research. Around 1 lakh websites are hacked daily [ 13 ].
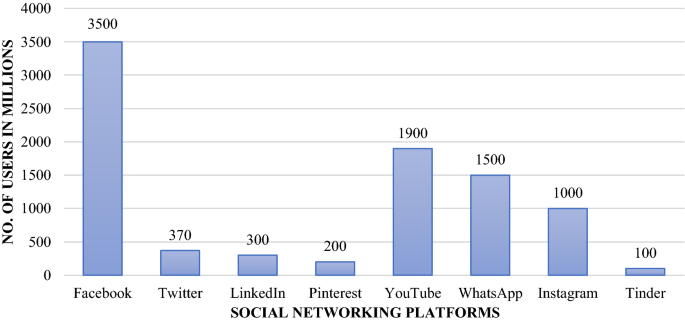
Number of users on different social networking platforms
As per the data depicted in Fig. 4 , the use of social networking sites has amplified exponentially such that there is a large amount of data and information available on these sites which has increased risks of information leakage and has opened doors for several cyber-crimes like data interception, privacy spying, copyright infringement, and information fraudulence. Although some Social Networking Sites like Twitter do not allow disclosing private information to users, some experienced attackers can infer confidential information by analyzing user’s posts and the information they share online. The personal information we share online could give cybercriminals enough to get our email and passwords. We have taken cognizance of popularity and narrowed down the list of networks to keep the scope of study feasible. By extension, the chosen social networks employ state-of-the-art defence strategies. Thus, any possible attacks on these networks would employ state-of-the-art techniques. Transitively, the analysis holds relevance for other social networks as well.
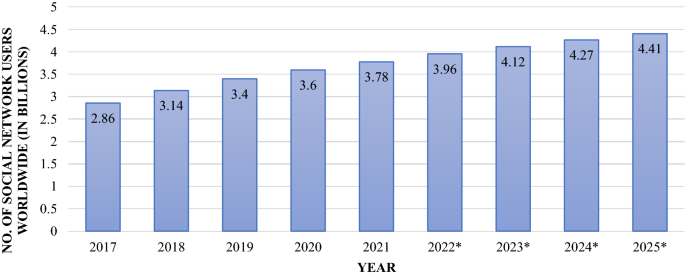
Number of users on social media worldwide (year-wise)
Insights in Fig. 5 presents a positioning of the most banned sorts of hacking. It is as indicated by the reaction of adults to a survey in the United States during January 2021. It reports around 44% of the respondents accept that digital secret activities ought to have the most severe punishments.
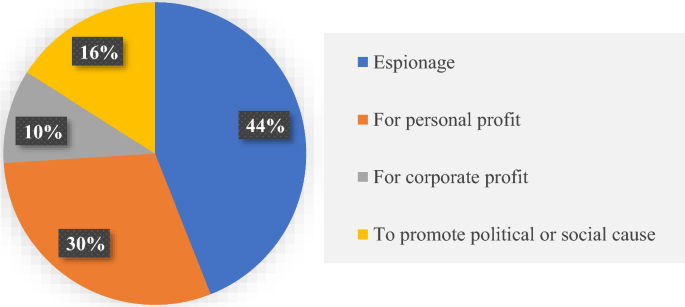
Most punishable types of hacking in 2021
Figure 6 portrays the most vulnerable way for information breaches worldwide in 2021, sorted by share of identities exposed [ 14 ]. According to the recent report, 91.6 percent of data breaches resulted in impersonation or stolen identities.
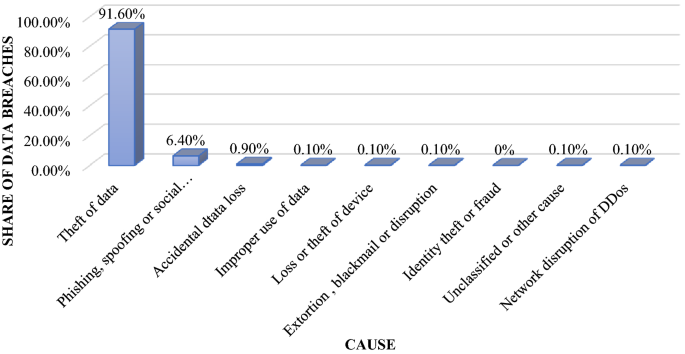
Leading cause of data breaches worldwide in 2020
Nowadays geotagged photos are very popular. People tag their geographical locations along with their pictures and share them online. Some applications have this feature of geotagging which automatically tags the current location inside a picture until and unless the user turns it off manually. This can expose one's personal information like where one lives, where one is traveling, and invites thieves who can target one for robbery. When someone updates their status with their whereabouts on a regular basis, it can pose a threat to their life through possible stalking and robbery. According to a report by Heimdal Security, around 6 lakh Facebook accounts are hacked daily [ 15 ]. Individuals who devote more time on social media and are probable to like the posts of their close friends. The hackers take advantage of this trust. Hackers can also use social media to sway elections. The most popular attacks on social media are like-jacking, which occurs when attackers post fake Facebook like buttons to web pages, phishing sites, and spam emails. The statistics in Table 1 entail the percentage of internet users in the United States who have shared their passwords on their online accounts and to their loved ones as of May 2020. It is sorted by age group. The entire survey depicted that 74% of respondents aged more than 65 and above do not share online passwords with family and friends.
With this remarkable expansion in social networking threats and security issues, numerous specialists and security associations have proposed different solutions for alleviating them. Such solutions incorporate PhishAri for phishing detection [ 16 ], spam detection [ 17 ], GARS for cyber grooming detection [ 18 ], clickjacking detection system [ 19 ], framework to detect cyber espionage [ 20 ], SybilTrap to detect Sybil attacks [ 21 ], worm detection system to detect malware [ 22 ]. Users themselves must be alert while posting any media or information on social networking sites. A strong password should be adopted, and it must not be shared with anyone. One should check the URL while visiting a website and must not click any malicious links. These habits could help a user to some extent to be protected against various cyber-attacks on social media. Table 2 presents a collection of the greatest online information breaks via social media worldwide as of November 2020 [ 23 ].
Positive and negative effects of online social networks based on users perspective
Social media has changed the manner in which individuals see the world and collaborate with each other. The near-universal accessibility and minimal effort of long-range informal communication locales, for example, Facebook and Twitter have assisted millions to stay connected with family and friends [ 28 ]. Similar to many technological revolutions, social networks also have a negative side. We describe some of the positive and negative effects of social networking based on the researchers' perceptions described below.
Positive factors of OSN
The various positive factors that influence the user to create and use the environments are maintaining social relationship, marketing the product and platforms, rescue efforts, and finding common group of people to communicate and share the thoughts.
Maintaining social relationships Social networking sites have proven to be convenient in keeping up with the lives of others who matter to us. It helps to nurture friendship and other social relationships [ 29 ].
Marketing platform Professionals can post work experience and build a network of professionally oriented people on sites such as LinkedIn or Plaxo which are career-building social networks [ 30 ]. They help discover better job opportunities. Marketers can influence their audience by posting advertisements on social networking sites [ 31 ].
Rescue efforts Social media sites play a huge role in rescue and recovery efforts during calamities and disasters [ 32 ]. They connect people during such crucial times when the conventional societal structure has broken down. Bulletins are easily managed by social networking sites which can reunite missing family members. The public can be kept informed using utilities extended by essential service providers through online social networking. Real-time local updates on social media help government officials to better understand the circumstances and make more informed decisions.
Finding common groups Social networking sites help people find groups with common interest [ 33 ]. People can share their likes and dislikes, interests and obsessions and thought and views to these groups which contribute to an open society.
Negative factors of OSN
When the general users use the social network platform, he/she face a lot of trouble that identified by various researchers based on security parameter. Like,
Online intimidation: while making friends is easier on social media, predators can also find victims easily [ 34 ]. The anonymity provided by social networks has been a consistent issue for social media users. Earlier someone was bullied only face-to-face [ 35 ]. Nonetheless, now any individual can bully someone online anonymously.
The exploitation of private information: although creating an account on social networking sites is free of charge, they make their money mostly from the advertisements they show on their websites [ 36 ]. The data once gathered is sold to brokers in relationships without the consent of social media users. Moreover, adversaries can also extract confidential information about their targets from these websites using different attack techniques.
Isolation : social media has surely improved the connection between users but conversely it has also averted real-life social interaction [ 37 ]. People find it easier to follow the posted comments of people they know rather than personally visit or call them [ 38 ].
General addiction: by the records we can depict that social media is more addictive than cigarettes and alcohol. People often feel empty and depressed if they do not check their social media account for a full day.
This paper presents a systematic and in-depth study of threats and security issues that are current and are emerging. More precisely, this study encompasses all the conventional threats that affect the majority of the clients in social networks and most of the modern threats that are prevalent nowadays with an emphasis on teenagers and children. The principle objective of this paper is to give knowledge into the social network’s security and protection. It introduces the reader to all the possible dimensions of online social networks and issues related to them. Our analysis throws light on the prevalent open challenges and issues that need to be discussed to enhance the trustworthiness of online social networks.
The remaining paper is systematized as: " Statistics of online social network and media " section describes various threats that are currently prevalent in social media. " Positive and negative effects of online social networks based on users perspective " section provides reasons for social media security issues. " Various threats on online social network and media " section discusses solutions that are given by various researchers, " Reasons behind online social media security issues " section consists of some security- guidelines suggested for users, some open issues and challenges in online social media is conferred in " Solutions for various threats " section, finally, Segment 7 presents the conclusion.
Various threats on online social network and media
Being the technology-based society that we are, and with the prevalence of the internet, we have extended our interaction through the electronic world of the internet. Following are the attacks which users have been observing right from the beginning of social networks.
We have divided threats into three categories i.e. conventional threats, modern threats, and targeted threats (as shown in Fig. 7 ). Conventional threats include threats that users have been experiencing from the beginning of the social network. Modern threats are attacks that use advanced techniques to compromise accounts of users and targeted attacks are attacks that are targeted on some particular user which can be committed by any user for varied personal vendettas.
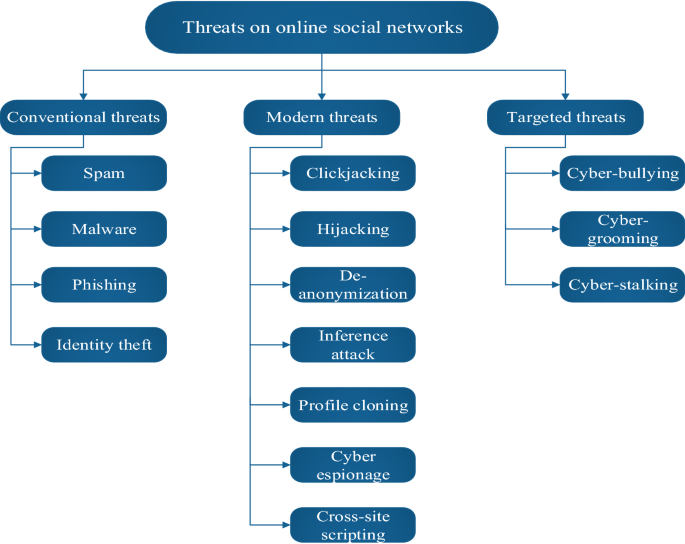
Classification of threats
Conventional threats
Spam attack.
Spam is the term used for unsolicited bulk electronic messages [ 39 ]. Although email is the conventional way to spread spam, social networking platform is more successful in spreading spam [ 40 ]. The communication details of legitimate users can easily be obtained from company websites, blogs, and newsgroup [ 27 ]. It is not difficult to convince the targeted client to read spam messages and trust it to be protected [ 41 ]. Most of the spams are commercial advertisements but they can also be used to collect sensitive information from users or may contain viruses, malware or scams [ 28 ].
Malware attack
Malware is a noxious programming which is explicitly evolved to contaminate or access a computer system, ordinarily without the information of the user [ 42 ]. An intruder can utilize numerous ways to spread malware and contaminate devices and networks [ 43 ]. For instance, malware may get installed by clicking a malicious URL, on the client’s framework or it might divert the client to a phony site which endeavors to acquire private data from the client. An attacker can inject some malicious script in URLs and clicking on that URLs can make that script run on a system that may collect sensitive information from that system [ 44 ]. In social networking platforms, the malware uses Online Social Network’s (OSN) structure to propagate itself such as the number of vertices, number of edges, average shortest path, and longest path.
A phishing attack is a kind of social engineering attack where the aggressor can acquire sensitive and confidential information like username, password and credit card details of a user through fake websites and emails which appears to be real [ 45 ]. An invader can impersonate an authentic user and may use his/her identity to send fake messages to other users via a social networking platform which contains malicious URL [ 46 ]. That URL might readdress a consumer to the phony website where it asks for personal information [ 47 ]. In the case of SNS, an assailant needs to attract the client to a phony page where he can execute a phishing attack. To accomplish this, the assailant uses different social engineering methodologies. For example, he can send a message to a user which says, “your personal pictures are shared on this website, please check!”. By clicking on that URL, the user is redirected to a fake website which looks like some legitimate social networking site.
Identity theft
In this sort of assault, the assailant utilizes someone else’s identity like social security number, mobile, number, and address, without their permission to commit attackers [ 48 ]. With the help of these details, the attacker can easily gain access to a victim's friend list and demand confidential information from them using different social engineering techniques [ 49 ]. Since the attacker impersonates a legitimate user, he can utilize that profile in any conceivable way which could seriously affect authentic clients [ 50 ].
Modern threats
Cross-site scripting attack.
Cross-site scripting is a very prevalent attack vector among infiltrators. The attack is abbreviated as XSS and is also known as “Self-XSS” [ 51 ]. Fundamentally, the attack executes a malicious JavaScript on the victim’s browser through different techniques. These are classified as persistent, reflected, and DOM-based XSS attacks [ 52 ]. The browser can be hijacked with just a single click of a button which may send a malicious script to the server [ 53 ]. This script is boomeranged back to the victim and gets executed on the browser. Attractive links and buttons in popular social media sites like Twitter and Facebook can trick the user into following URLs [ 54 ]. Worse yet, some users may feel compelled to copy and paste JavaScript containing links onto their browser's address bar [ 55 ]. These attacks can either steal information or act as spyware. Such attacks can also hijack computers to launch attacks on unsuspecting users. The real perpetrator of the attack is hidden behind the compromised machine.
Profile cloning attack
In this attack, the assaulter clones the users’ profile about which he has a prior knowledge. The attacker can use this cloned profile either in the same or in a different social networking platform to create a trusting relationship with the real user’s friends [ 56 ]. Once the connection is established, the attacker tricks the victim’s friends to believe in the validity of the fake profile and catch confidential information successfully which is not shared in their public profiles. This attack can also be used to commit other types of cyber-crimes like cyberbullying, cyber-stalking, and blackmailing [ 45 ].
In hijacking, the adversary compromises or takes control of a user’s account to carry out online frauds [ 57 ]. The sites without multifactor authentication and accounts with weak passwords are more vulnerable to hijacking as passwords can be obtained through phishing [ 58 ]. If we do not have multifactor authentication, then we lack a secondary line of defense [ 59 ]. Once an account is hijacked, the hijacker can send messages, share the malicious link, and can change the account information which could harm the reputation of the user [ 60 ].

Inference attack
Inference attack infers a handler’s confidential information which the user may not want to disclose, through other statistics that is put out by the user on some Social Networking Site (SNS) [ 61 ]. It uses data mining procedures on visibly available data like the user’s friend list and network topology [ 62 ]. Using this technique, an attacker can find an organization’s secret information or a user’s geographical and educational information [ 45 ].
Sybil attack
In Sybil attack, a node claims multiple identities in a network [ 63 ]. It can be harmful to social networking platforms as they contain a huge number of users who are coupled through a peer-to-peer network [ 64 ]. Peers are the computer frameworks which are associated with one another by means of the internet and they can share records straightforwardly without the need of a central server [ 32 ]. One online entity can make several fake identities and use those identities to distribute junk information, malware or even affect the reputation and popularity of an organization. For instance, a web survey can be manipulated utilizing various Internet Protocol (IP) delivers to submit an enormous number of votes, and aggressor can outvote a genuine client [ 33 ].
Clickjacking
Clickjacking is a procedure in which the invader deceives a user to click on a page that is different from what he intended to click [ 65 ]. It is also known as User Interface redress attack. The attacker exploits the vulnerability of the browsers to perform this attack [ 66 ]. He loads another page over the page which the user wants to access, as a transparent layer [ 67 ]. The two known variations of clickjacking are likejacking and cursorjacking. The front layer shows the substance with which the client can be baited. At the point when the client taps on that content he actually taps the like button. The more individuals like the post, the more it spreads.
In cursorjacking attacker replaces the actual cursor with a custom cursor image. The actual cursor is shifted from its actual mouse position. In this manner, the intruder can trick a consumer to click on the malicious site with clever positioning of page elements [ 68 ].
De-anonymization attack
In quite a lot of social networking sites like Twitter and Facebook, users can hide or protect their real identity before releasing any data by using an alias or fabricated name [ 69 ]. But if a third party wants to find out the real identity of the user, it can be done by simply linking the information leaked by these social networking sites [ 70 ]. They use strategies such as tracking cookies, network topologies, and user group enrollment to uncover the client’s genuine identity [ 71 ]. It is a sort of information mining method in which mysterious information is cross-referred to other information sources to re-recognize the unknown information [ 60 ]. An attacker can collect information about the group membership of a user by stealing history from their browser and by combining this history with the data collected. Thus the attacker can de-anonymize the user who visits that attacker’s website [ 72 ].
Cyber espionage
Cyber espionage is an act that uses cyber capabilities to gather sensitive information or intellectual property with the intention of communicating it to opposing parties [ 73 ]. These attacks are motivated by greed for monetary benefits and are popularly used as an integral part of military activity or as a demonstration of illegal intimidation [ 74 ]. It might bring about a loss of competitive advantage, materials, information, foundation or death toll. A social engineer can perform social engineering assaults using social networking sites. He can acquire important data like worker’s assignment, email address, and so forth utilizing social networking sites [ 75 ].
Targeted threats
- Cyberbullying
Cyberbullying is the use of electronic media such as emails, chats, phone conversations, and online social networks to bully or harass a person [ 76 ]. Unlike traditional bullying, cyberbullying is a continuous process [ 77 ]. It is continuously maintained through social media [ 78 ]. The attacker repeatedly sends intimidating messages, sexual remarks, posts rumors, and sometimes publishes embarrassing pictures or videos to harass a person [ 79 ]. He can also publish personal or private information about the victim causing embarrassment or humiliation. Cyberbullying can also happen accidentally. It is very difficult to find out the tone of the sender over text messages, instant messages, and emails. But the repeated patterns of such emails, texts, and online posts are rarely accidental [ 80 ].
- Cyber grooming
Cyber grooming is establishing an intimate and emotional relationship with the victim (usually children and adolescents) with the intention of compelling sexual abuse [ 81 ]. The principle point of cyber grooming is to acquire the trust of the youngster and through which intimate and individual information can be attained from the child [ 82 ]. The data is often voluptuous in nature through sexual conversations, pictures, and videos which gives the attacker an advantage to threaten and blackmail the child [ 83 ]. Assailants frequently approach teenagers or kids through counterfeit identity in child-friendly sites, leaving them vulnerable and uninformed of the fact that they have been drawn closer with the end goal of cyber grooming. However, the victim can also unknowingly initiate the grooming process when they get rewarding offers, for example, cash in return for contact details or personal photographs of themselves. In some cases, the victim knows about the fact that he/she is conversing with an adult which can prompt further commitment in sexual activities. However, it is with the individual under the age of consent and in this manner constitutes a crime. The anonymity and accessibility of advanced media permit groomers to move toward various youngsters simultaneously, exponentially increasing the instances of cyber grooming. Despite what might be expected, there are a couple of instances of feelings for the crime of cyber grooming worldwide, as 66% of the world's nations have no particular laws with respect to cyber grooming of children [ 84 ].
Cyberstalking
Cyberstalking is the observing of an individual by the means of internet, email or some other type of electronic correspondence that outcomes in fear of violence and interferes with the mental peace of that individual [ 85 ]. It involves the invasion of a person’s right to privacy. The attacker tracks the personal or confidential information of the victims and uses it to threaten them by continuous and persistent messages throughout the day. This conduct makes the victim exceptionally worried for his own safety and actuates a type of trouble, fear or disturbance in him [ 86 ]. Most of the individuals these days share their personal information like telephone number, place of residence, area, and schedule in their social networking profile. In addition, they likewise share their location-based data. An assailant can gather this data and use it for cyberstalking [ 87 ].
Reasons behind online social media security issues
Social media addresses one of the most unique, unstructured, and unregulated datasets anyplace in the advanced world and this scene is arising quickly all over the globe [ 88 ]. Every day millions of people upload their photos and other multimedia content on social media to share it with their friends. This is prompting the development of digital risk monitoring [ 89 ]. The development of web-based media has presented new security standards that put clients (representatives, clients, and partners) solidly in the aggressor’s line of sight. The social network has become the new digital milestone where attackers think that it's simple to target victims. It has presented one of the biggest, most powerful dangers to authoritative security. Attackers influence social media for the accompanying three reasons (as shown in Fig. 8 ):
The scale of social media: since a huge mass of people spend their time on social media for various purposes, attacks can spread like any other viral trend. The attacker can use hashtags, clickbait, and trending topics to announce their malware which might be focused on everyone or to some particular gathering of individuals. This represents a tremendous challenge for security experts to overcome physically.
Trusted nature of social media: adversaries take advantage of the trusting nature of social media. People sometimes accept an unknown friend request on the basis of mutual friends that requester has. They easily visit the link posted by their friends without thinking much about a possible security breach. Over one-third of the total population on social media acknowledge unknown friend requests, making online media perhaps the best mode for acquiring the trust of a target.
Invisibility to security team: majority of people in the world spend most of their time on social media networks. Observing this enormous populace is extremely troublesome as security teams do not have tools to broaden their perceptibility beyond a specific border into the social media domain where employees are intensively vulnerable to be compromised.
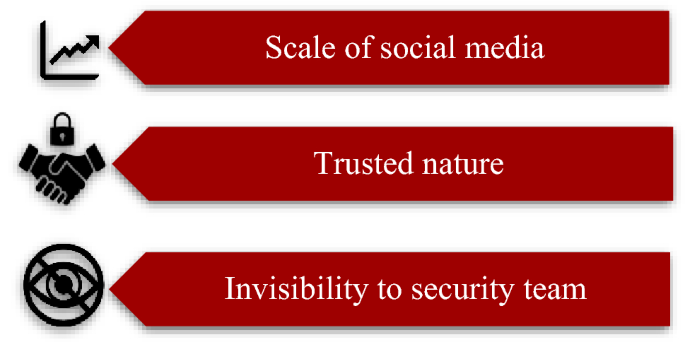
Reasons for social media security issues
Solutions for various threats
Many researchers in both academia and industries are constantly trying to find solutions for the aforementioned threats in social media. They have proposed many solutions and some approaches to combat these threats. This section provides a discussion on various methods and approaches proposed by different researchers on SNS security. We have classified solutions into two groups namely social network operator solutions and academic solutions. Figure 9 shows the classification.
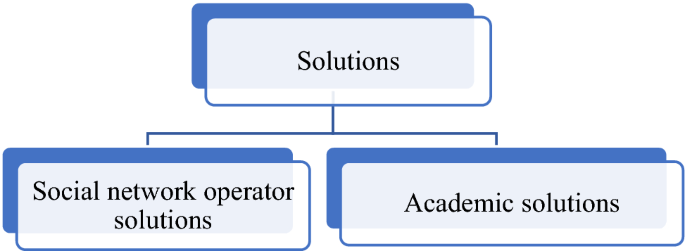
Classification of solutions to threats
Social network operator solutions
Authentication mechanism.
To make sure that only a legitimate user is logging or registering in a social network and not a socialbot, several OSN uses authentication procedures such as CAPTCHA, multi-factor authentication, and photos-of-friend identification. For instance, the leading social networks like Twitter and Facebook use two-factor authentication principles. This principle uses a login password and a verification code received through a mobile device. This helps to mitigate the risk of an account being compromised and prevents an attacker from hijacking a legitimate account and posting malicious content.
Security and privacy setting
Many social networking sites provide configurable security and privacy setting to empower the client to shield their personal information from undesirable access by outsiders or applications. For instance, the Facebook client can modify their security setting and select the audience (like friends, friends of friends, and everybody) in the network who can see their details, pictures, posts, and other sensitive information. Moreover, Facebook additionally permits its users to either acknowledge or reject the access of third-party applications to their personal information. Many social networking sites are equipped with security measures that are internal to the system. They ensure users of the network against spams, counterfeit profiles, spammers, and different risks.
Report users
Online social networks protect the young generation and teenagers from being harassed by providing the facility to report any form of abuse or policy violations by any user in their network. For instance, if a user sees something on Facebook that is objectionable to the individual’s sentiments, but it doesn’t violate the Facebook terms then the user can utilize the report links to send a message to the one who posted it asking him to take it down or remove. When Facebook receives reports, it is reviewed and removed according to the Facebook community standards.
Academic research-based solutions
Phishing detection.
Phishing distresses the privacy and security of many traditional web applications such as websites, social networking sites, emails, and blogs. Consequently, several anti-phishing techniques have been developed to detect phishing attacks. Many researchers have put forward anti-phishing procedures which are based on techniques that try to identify phishing websites and phishing URLs. As phishing attacks are becoming more and more pervasive in online social networking sites, the research community has suggested specialized solutions for phishing attacks in a social networking environment. For instance, Aggarwal et al. proposed the PhishAri technique for real-time identification of phishing attacks occurring on Twitter. It utilized specific Twitter features like account age and number of followers to detect if the posted tweet is phishing or safe [ 16 ].
Cyberbullying detection
Although detecting cyberbullying is more complex than detecting racist language and spam [ 90 ], some researchers have tried to detect it using more complex document representation and additional information about victims and bullies [ 91 ].
Machine learning techniques can be applied to detect cyberbullying [ 92 ]. Rather than using only words and emoticons which expresses insults, obscenity, and typical cyberbullying words [ 93 ], it can also use some additional information like the gender and personality of the participants in a suspected cyberbullying event [ 94 ]. To deal with uncertainty and imprecision, a fuzzy rule-based system can be used which is a mathematical tool. To optimize the results genetic algorithms are the direct and stochastic methods.
For addressing the problem of online cyber grooming, machine learning techniques appear to be an effective measure. Michalopoulos et al. [ 18 ] presented the Grooming Attack Recognition System (GARS) a technique to recognize, analyze and control grooming attacks so that children could be protected against online attacks. It calculates the total risk value which identifies grooming threats to which a child is exposed by analyzing conversations by the child. A threshold is predefined for risk value and when the total risk value crosses the predefined threshold, an alarm mechanism is prompted. This alarm mechanism also simultaneously transmits an on-the-spot warning message to the parent. A colored signal is generated to warn the child about the degree of danger in a conversation. Escalante et al. [ 95 ] evaluated the use and performance of a profile to detect sexual predators. Through this evaluation, they also investigated aggressive texting.
Balduzzi et al. [ 19 ] designed and developed an automated system that can analyze web pages to protect the user against clickjacking attacks. It consists of a code that can detect overlapping clickable elements. And in addition to this solution, they also adopted the NoScript tool, which has an anti-clickjacking feature included in it. Anas et al. [ 96 ] proposed a solution in which other visual components are added which guarantees that the user is not able to proceed with his actions until and unless he has visibility over the control in place. To enable the working of this solution, the existence of a HyperText Markup Language (HTML) object containing a pattern was ensured. Some checkpoints are generated based on user interaction. User must follow those checkpoints without a single mouse click. In addition to it, a panel area shows the third-party reference identity. And to ensure the integrity of actions, user interface verification control is used. This technique can be applied in two ways, one is by generating random patterns in which the user has to follow that pattern to further propagate his action and the other way is to ask the user to draw that specific pattern which he has already registered. Microsoft introduced X-FRAME-OPTIONS, an Hyper Text Transfer Protocol (HTTP) header sent on HTTP responses, as a defense against frame busting and clickjacking in Internet Explorer 8. JavaScript can also be used as a defense against clickjacking [ 97 ].
Encryption techniques are available for devices on recent versions of Android and iOS. If a device is stolen, the thief cannot read the contents if encryption is enabled. Further, any attempts to read the information from internal or external memory is thwarted by the existence of a device password [ 98 ]. There are various technologies which can be used against stalkers like smartphone fingerprint lock antivirus, specialized stalker app detection software, firewalls, and privacy guards. Device encryption can be used against spyware, stalker apps and device theft [ 98 ]. Frommholz et al. have described machine learning techniques for detecting cyberstalking using textual analysis altogether [ 99 ].
Cyber espionage is a kind of targeted attack. Sahoo et al. described the concept of an ATA detection framework and introduced a system design checklist which is explicitly designed for identifying targeted attacks [ 20 ]. Organizations can create their own team to fight against targeted attacks and analyze vulnerabilities, in their and as well as in other companies’ code. Google has its own team to analyze vulnerabilities and bugs in their code. Each company has its own profile that is different from each other. So, each company must take appropriate steps according to their profile to implement security measures to design and implement security controls to address various security risks. Organizations can also be secured to some extent against targeted attacks by means of authentication systems. Earlier only password was used to protect the data, but now a two-factor authentication system is used which is a combination of password and some pin or biometric details. It is more secure than using a single factor i.e. password. The data which is no longer required for business purposes should be removed from the company's network. Keeping those records may create the risk of unauthorized access to sensitive information in an organization [ 100 ].
Fake profile
The author in Ref. [ 101 ] describes one model to distinguish the counterfeit accounts and profiles. They extracted some user profile contents from LinkedIn platform and processed those profiles content to extract different features. Subsequent to preprocessing of profiles through principal component, a training set is created utilizing the resilient backpropagation algorithm in a neural network. Support Vector Machines (SVMs) is utilized for characterization of profile. The author in Ref. [ 102 ] proposed a model that detects bot net using adaptive multilayered-based machine learning approach. The proposed work presented a bot detection framework based on decision trees which effectively detects P2P botnets. Also, the author in Ref. [ 103 ] proposed an ensemble classification model for the detection of fake news that has achieved a better accuracy compared to the other state-of-the-art. The proposed model extracts important features from the fake news datasets, and the extracted features are then classified using the ensemble model comprising of three popular machine learning models namely, decision tree, random forest, and extra tree classifier. Furthermore, the author in Ref. [ 104 ] presented a systematic literature review of existing clone node detection schemes with some theoretical and analytical survey of the existing centralized and distributed schemes for the detection of clone nodes in static WSNs environment.
Sybil detection
Al-Qurishi et al. [ 105 ] proposed a new Sybil detection system that uses a deep learning model to predict a Sybil attack accurately. This model consists of three modules namely, one data harvesting module, one feature extracting module and a deep regression model. All these three modules work in a systematic form together to analyze a user’s profile on Twitter. Rahman et al. gave a model named SybilTrap which is a graph-based semi-supervised learning system that uses both content-based and structure-based techniques to detect Sybil attacks. It is based on a semi-supervised algorithm which utilizes the interaction graph information of a node where labeled information of nodes flows through unlabeled nodes. It gathers information about the network and its users and uses this information to detect malicious users. This system is resistant to various strategic attacks such as targeted or random attacks. It is designed to work under any condition and is applicable to all existing social networks regardless of their level of trust [ 21 ].
Spam detection
Rathore et al. proposed a framework called SpamSpotter to solve the issue of spam attack on Facebook. It is based on the intelligent decision support system (IDSS). It gathers all relevant information from the user profile with the help of a decision process in IDSS and then analyzes it by mapping user data to the classification of a user profile as a spammer or legitimate. It resolves some of the issues and challenges (1) It solves the issue of an inadequate set of features that exist in most of spammer detection system. (2) It resolves the issue of uncertainty about critical pieces of Facebook information and public unavailability. (3) The use of the IDSS system resolves the issue of low accuracy and high response time. The use of machine learning classifiers in IDSS provides fast response time that is very essential to detecting spam on Facebook [ 17 ].
Faghani and Saidi [ 106 ] found that the visiting behavior of the social network members affects the propagation of XSS worms. The worm propagates slower when members mostly visit their friends rather than strangers. It can also be slowed down by the clustered nature of social networks. This is so because infected profiles in the early stages of XSS worm propagation lead to faster propagation of worm. Xu et al. [ 22 ] developed an approach to detect worms which leverages properties of online social network and propagation characteristics of OSN worms. It first builds a surveillance network based on the properties of the social graph to gather evidence against suspicious worm propagation. It monitors only a small fraction of user accounts to maximize surveillance coverage. To ensure that noise is absent in a surveillance network, a scheme is further proposed. Table 3 represents the probability of encountering different types of threats in different platforms discussed in “ Introduction ” section. It shows that the platforms used for social connections are the most vulnerable among all platforms.
Other contributions
The author in Ref. [ 107 ] proposed a novel algorithm to reform any traffic domain into a complex network using the principles of decentralized Social Internet of Things (SIoT). With the help of social networking, concepts integrate into the Internet of Things (IoT), the concept of SIoT has been proposed. The idea of the article is, every vehicle acts as a smart thing, communicate with nearby vehicles within a particular distance in a decentralized manner and together form a complex network. Also, the author in Ref. [ 108 ] proposed propose a privacy-preserving ICN forwarding scheme based on homomorphic encryption for wireless ad hoc networks to protect the private information of the user. The trust-based model proposed by the author in Ref. [ 109 ]. The author proposed a secure trusted hypothetical mathematical model for ensuring secure communication among devices by computing the individual trust of each node. In addition to this, the author proposed a decision-making model, that integrated with the hypothetical model for further speeding up the real-time communication decision within the network.
Comparative analysis with other state of art techniques
This section compared our survey related to different threat analysis and their defensive approaches with other state of art techniques and survey to show the novelty shows in Table 4 .
Security-guidelines for OSNs user
Nowadays, online social media and network have become an integral part of everyone’s life. As the reputation of these social sites grows, so do the risks of using them. The number of users increases exponentially every year. So, it becomes a necessity to secure users on these platforms. Below are some security-guidelines for users which they can practice keeping themselves reasonably secure. We have tried to give security-guidelines in two ways. First, it has been described in a general form and then it is described platform-wise (as shown in Fig. 10 ).
Security guidelines for users
General guidelines
Use a strong password: for maintaining the security of accounts, users should choose a strong password. It should not be too short as short passwords can be easily guessed. It should be long enough and must contain alphanumeric values with some special characters [ 119 ]. Users should not use the same password which they use for other accounts because if somehow an attacker gets to know that password, he can compromise all accounts of that user. So, choosing a strong password can help a user safeguard their account and profile from unauthorized access [ 120 ].
Limit location sharing: nowadays sharing location has become a trend. Many social networking sites have also introduced the feature of geotagging which automatically tags the geographical location of the user when the user uploads any multimedia on social media [ 121 ]. The user has to switch it to manual so that it does not tag location automatically. Sharing location online makes a user vulnerable to real-life crimes like robbery. So, to mitigate this risk, the user can post his location at a later point of time post completion of the visit [ 122 ]. Users must upload their multimedia content online very carefully as it may contain sensitive metadata and it is recommended to switch geotagging to manual mode in all their mobile devices and accounts. Also suggested is the use of software that removes such metadata from the pictures before uploading.
Be selective with friend requests: it is seen that many users accept friend requests without analyzing the complete profile of the requester. People generally accept friend request based on mutual friends. If the requester has some mutual friends, then they accept it [ 123 ]. Sometimes attackers make their profile attractive deliberately or they may impersonate an account. So, if the person sending a friend request is unknown, one should ignore that friend request. It could be a fake account attempting to steal sensitive information.
Be careful about what you share: users should be careful about their posts as it may reveal their personal information and sometimes others also. Many organizations keep strict rules and regulations for sharing information and multimedia content. There are many reports of people getting fired from their job due to sharing information illegally. This situation can be avoided if employees are well informed about the protocols of the organization they are working in regarding pictures, videos, and messages that they post online. Sharing information illegitimately can harm an organization’s reputation in the market along with its data and intellectual property also.
Be aware of links and third-party applications: illegitimate users can get access to someone’s account and get sensitive information by sharing a malicious link. Nowadays shortened URLs are becoming very popular on various social media platforms. These shortened URLs may be obfuscated with malicious code or script. These scripts try to gather the personal and confidential information of a user which may breach the privacy of that user. Moreover, hackers may take advantage of vulnerabilities present in a third-party application that is integrated with many popular social networks [ 124 ]. An example of such a third-party application happens to be games that are playable on online social networks which ask for user’s public information to consume their services. This gathered information may be provided to outsiders or third-party interventions. To avoid this risk, user should be careful while installing third-party applications in their profile.
Install internet security software: some threats whose pattern is known may easily be detected through anti-viruses. Threats like cyber grooming, cyberbullying can be detected to some extent by using anti-virus software [ 125 ]. Many malicious links can be shared by our friends unknowingly which redirects the user to some phishing website. Anti-virus software should be kept updated regularly due to the presence of many viruses created by hackers on a daily basis. Some social networking sites also have their own security tools which can be used by users to protect themselves from cyber-attacks.
Platform-wise
For professional networks.
Professional networks are primarily used to create contacts and increase perceptibility to potential recruitment companies [ 126 ]. So, to be safe on professional networks, one should look for the details provided by other users before adding them to one’s contact list. Generally, an adversary does not provide many details about his career.
A user should check if there are any spelling or grammar mistakes in someone's profile because if someone is applying for some job, it should be very well written and should be free from any spelling or grammar mistakes [ 127 ]. It should contain good information about that person.
Checking for consistency in a person’s career can be a good practice if a user wants to be safe on a professional network. A profile which continually and definitely changes over a short span of time is the most used part as a draw by the invader. At the point when the fraudster needs to target one sort of organization or vertical, he simply adds a new position that could be pertinent to his targets.
One should also cross-check information. If a person claims to be from the employer’s company, the user can check the company’s directory and should not hesitate to verify from his company’s human resource department.
For multimedia sharing platform
One should not post sensitive information in their photos or caption [ 3 ]. Exposing too much private information in a profile can be dangerous.
Sharing current locations on social media should be avoided. Geotagging services provided by different multimedia platforms should be turned off manually. There have been plenty of cases of thieves that were tipped off to rob homes. Suspects use social media to gather information about victims who share their location online. People who leave for a short holiday and brag about it online may come home to find the place emptied.
If an application is not in use for a long period, it is better to revoke access to that application. There are so many third-party applications which use social media account to log-in. For security and privacy concerns, one should allow access to applications that are trustworthy [ 4 ].
Enable two-step authentication for all your social media accounts wherever possible. This provides an extra layer of security to the account. In case an adversary finds out the password of a user, he will still need a second factor to authenticate himself. The second factor consists of a unique, time-sensitive code that users receive via text on their mobile phone.
For social connection platform
Users should learn about the privacy and security setting for different social media platforms and use them [ 128 ]. Each platform has its own privacy and security setting. Every platform provides settings, configuration, and privacy sections to limit who and what groups can see various aspects of the user’s profile. The privacy setting provided by the sites as default should not be adopted as it is.
The more details provided, the easier it is for an adversary to use that information to steal identity or to commit other cybercrimes. Thus, information sharing should be limited.
Before accepting a friend request, one should completely check the profile of the requester. One can make different groups for sharing different kinds of information like a different group for colleagues and family.
Before posting any information on the profile, employees should know their company’s policy over sharing any content online on social networks.
For discussion forums
One should pay attention while clicking on links given by various authors. It may be some suspicious site trying to get the credentials of the user.
Users should always keep an eye on the site’s URL. Noxious sites may look compellingly indistinguishable from a real one, however, the URL may contain slight inconsistencies like the variety in spelling or an alternate domain (e.g., .com versus.net) [ 129 ].
Be careful about communications that requests the client to act promptly, offers something that sounds unrealistic or requests personal information.
Open research issues and challenges
Scientists and researchers have found many methods and solutions to secure users on social media but there are still some issues which are not resolved. In this section, we discuss some of those issues and challenges.
Unfortunately, social networking sites are the easiest way for an attacker to lie about his identity and target the victim. They can lie about their age, looks, and can project themselves as a completely different identity according to their target. Child predators are taking advantage of this drawback in social networking sites, as children are a very easy target on these social platforms. These platforms have millions of users and monitoring each user can be very difficult. Therefore, there is a need for some system which can detect child predators effectively. Although the research community is trying to solve this issue, we need a good and effective system which can stop cyber grooming more efficiently. One possible addition to the already existing systems would be to incorporate artificial intelligence. The chat system can be improved to analyze conversations and derive meaningful inferences to support decision-making.
Social networking sites make money by allowing other companies to show advertisements on their website. Every time a user clicks an advertisement, it takes the user to a page where the user can buy a product and the social networking site get a percentage of that sale. These sites collect data of the users each time they use them so that they can show the advertisements as per the user’s interest. In this way, these social networking sites are collecting a huge amount of personal data of the user which can be sold to hundreds of businesses without user's knowledge. Hence, the user’s personal data is at risk. One possible way to thwart such data leaks is to inform the user of the data being shared. This would involve non-technical aspects to enforce a law or contract that all advertisements should abide by. From a technical standpoint there is not much control as to what the parent site decides to share with the advertising agency. Client-side browser restrictions could also provide wrapper-level security.
Nowadays surveys and games are becoming very popular on social media [ 130 ]. Generally, these surveys involve entering credentials which are supposed to enable the data for the survey to be gathered or the results to be shared. And while these surveys are collecting credentials, adversaries can skim those details to compromise user’s account.
Due to character count limitations on Twitter, people use shortened URLs to share their multimedia content. Adversaries can easily obfuscate malicious sites on these shortened URLs. This is an alarming situation since other social media applications like WhatsApp also have users who have started sharing shortened URLs. However, some social networking sites are working on this issue and have given solutions, but it is as yet conceivable that URL redirection can be used to hop from a safe landing point to a risky landing point. Again, a central repository of phishing sites could be leveraged by the client browser to warn the user when landing on the suspicious website. Further research could be conducted towards preemptive solutions that can parse URLs and warn the user even before clicking. A system is needed which can detect the malicious site from the shortened URLs effectively leveraging the already existing solutions.
Business-oriented networks contain significant business data that can be utilized to perform social engineering attacks. Some LinkedIn invitation update messages have been referred to be utilized as URL redirectors which can divert clients to some vindictive pages. This issue should be resolved so that users can be protected from a targeted attack. Here, intelligent language parsers could be trained to detect sensitive information and warn the originator of the information. Content detection can be applied to such platforms to find malicious activity. It can detect the number of posts posted through a profile because generally, the adversary posts similar messages.
There is a need to secure users on discussion forums also. Users can be easily fooled on discussion forums through phishing attacks which could result in deteriorating user trust on these forums. URL detection and filtering can be applied for these forums also to protect a user from malicious activity. Although such scenarios usually inform the user that they are moving out of the parent domain. The cost to reward ratio here is poor for any forum to implement parsers to parse external links. An incentive-based solution can be thought of to reward sites that scan external links.
Online social networks have become a vital part of the vast internet penetrated world. The paradigm shift has enabled social networks to engage with users on a daily basis. The increased rate of social media usage has solicited the need to make its users aware of the pitfalls, threats, attacks, and privacy issues in them. With the advancement in technology, social media has taken various forms. Individuals can connect to each other in a myriad of ways. Through professional sites, discussion forums, multimedia sharing networks, and many more, netizens can find themselves at the pinnacle of connectivity. Unfortunately, lack of awareness among users regarding security and privacy has the potential to lead to various cyber-attacks through social media. Although academia has come up with innovative solutions to address the security measures that are concerned with social media security, they suffer from a lack of real-world implementation and feasibility. Thus, there is a compelling need to continuously and iteratively review security issues in social networks keeping in pace with technological advancement. In this paper, we presented different scenarios related to online social network threats and their solutions using different models, frameworks, and encryption techniques that protect the social network users against various attacks. We have outlined different solutions and comparative analysis of different survey for better clarity about our survey. However, many of these privacy issues are not yet resolved. In addition to the defensive solutions, parents must monitor the kids actively when they are using internet services like OSNs. Overall, researchers can play a significant role in the defensive approach against these attacks in OSNs but still, some issues need to be resolved by using some hybrid approach, framework, and threat detection tools.
Benson V, Saridakis G, Tennakoon H, Ezingeard JN (2015) The role of security notices and online consumer behaviour: an empirical study of social networking users. Int J Hum Comput Stud 80:36–44
Google Scholar
Fosso Wamba S, Akter S (2016) Impact of perceived connectivity on intention to use social media: modelling the moderation effects of perceived risk and security. pp 219–227
Sahoo SR, Gupta BB (2020) Fake profile detection in multimedia big data on online social networks. Int J Inf Comput Secur 12(2–3):303–331
Bailey M, Cooke E, Jahanian F, Xu Y, Karir M A survey of botnet technology and defenses
Ahmed M, Mahmood AN, Hu J (2016) A survey of network anomaly detection techniques. J Netw Comput Appl 60:19–31
Mislove A, Viswanath B, Gummadi KP, Druschel P (2010) You are who you know. In: Proceedings of the third ACM international conference on Web search and data mining—WSDM ’10, p 251
Sahoo SR, Gupta BB (2021) Multiple features based approach for automatic fake news detection on social networks using deep learning. Appl Soft Comput 100:106983
Jain AK, Gupta BB (2018) Detection of phishing attacks in financial and e-banking websites using link and visual similarity relation. Int J Inf Comp Secur 10(4):398–417
Number of social media users worldwide 2010–2021 | Statista [Online]. https://www.statista.com/statistics/278414/number-of-worldwide-social-network-users/ . Accessed 14 Dec 2020
Gupta BB, Sahoo SR (2021) Online social networks security: principles, algorithm, applications, and perspectives. CRC Press
Top 15 Most Popular Social Networking Sites and Apps [August 2018] @DreamGrow [Online]. https://www.dreamgrow.com/top-15-most-popular-social-networking-sites/ . Accessed 14 Dec 2020
Digital Marketing Consultants—SEO Consulting—Zephoria Inc. [Online]. https://zephoria.com/ . Accessed 13 Dec 2020
Internet Live Stats—Internet Usage & Social Media Statistics [Online]. http://www.internetlivestats.com/ . Accessed 14 Dec 2020
Data breach causes worldwide 2016 | Statistic [Online]. https://www.statista.com/statistics/263303/proportion-of-the-most-common-causes-for-possible-identity-theft/ . Accessed 22 Jan 2021
Heimdal Security—Proactive Cyber Security Software [Online]. https://heimdalsecurity.com/en/ . Accessed 13 Dec 2018
Aggarwal A, Rajadesingan A, Kumaraguru P (2012) PhishAri: automatic realtime phishing detection on twitter. eCrime Res. Summit, eCrime pp 1–12
Rathore S, Loia V, Park JH (2018) SpamSpotter: an efficient spammer detection framework based on intelligent decision support system on facebook. Appl Soft Comput 67:920–932
Michalopoulos D, Mavridis I, Jankovic M (2014) GARS: Real-time system for identification, assessment and control of cyber grooming attacks. Comput Secur 42:177–190
Balduzzi M, Egele M, Kirda E, Balzarotti D, Kruegel C (2010) A solution for the automated detection of clickjacking attacks. Asiaccs 4(2):135
Sahoo SR, Gupta BB (2020) Popularity-based detection of malicious content in facebook using machine learning approach. In: First international conference on sustainable technologies for computational intelligence. Springer, Singapore, pp 163–176
Al-Qurishi M et al (2018) SybilTrap: a graph-based semi-supervised Sybil defense scheme for online social networks. Concurr Comput 30(5):1–10
Xu W, Zhang F, Zhu S (2010) Toward worm detection in online social networks. In: Annu. Comput. Secur. Appl. Conf., pp 11–20
Biggest online data breaches worldwide 2018 | Statistic [Online]. https://www.statista.com/statistics/290525/cyber-crime-biggest-online-data-breaches-worldwide/ . Accessed 2 Feb2019
Facebook to contact 87 million users affected by data breach | Technology | The Guardian [Online]. https://www.theguardian.com/technology/2018/apr/08/facebook-to-contact-the-87-million-users-affected-by-data-breach . Accessed 22 Jan 2021
MySpace becomes every hackers’ space with top breach in 2016, report says | CSO Online [Online]. https://www.csoonline.com/article/3166846/data-breach/myspace-becomes-every-hackers-space-with-top-breach-in-2016-report-says.html . Accessed 22 Jan 2021
FriendFinder Networks hack reportedly exposed over 412 million accounts | TechCrunch [Online]. https://techcrunch.com/2016/11/13/friendfinder-hack-412-million-accounts-breached/ . Accessed 22 Jan 2021
SR Sahoo, BB Gupta (2018) Security issues and challenges in online social networks (OSNs) based on user perspective. In: Computer and cyber security, pp 591–606
The Positive Impact of Social Networking Sites on Society [Online]. https://www.makeuseof.com/tag/positive-impact-social-networking-sites-society-opinion/ . Accessed 24 Jan 2019
Nyaribo YM, Munene AG (2018) Effect of social media pertication in the workplace on employee productivity. IJAME
de Vries L, Gensler S, Leeflang PSH (2012) Popularity of brand posts on brand fan pages: an investigation of the effects of social media marketing. J Interact Mark 26(2):83–91
Colicev A, Malshe A, Pauwels K, O’Connor P (2018) Improving consumer mindset metrics and shareholder value through social media: the different roles of owned and earned media. J Mark 82(1):37–56
Liu F, Xu D (2018) Social roles and consequences in using social media in disasters: a structurational perspective. Inf Syst Front 20(4):693–711
MathSciNet Google Scholar
The Positive and Negative Effects of Social Networking | Techwalla.com [Online]. https://www.techwalla.com/articles/the-positive-and-negative-effects-of-social-networking . Accessed 23 Jan 2021
7 Negative Effects of Social Media on People and Users [Online]. https://www.makeuseof.com/tag/negative-effects-social-media/ . Accessed 24 Jan 2021
Rook KS (1984) The negative side of social interaction: impact on psychological well-being. J Pers Soc Psychol 46(5):1097–1108
Zhu Y, Xu B, Shi X, Wang Y (2013) A survey of social-based routing in delay tolerant networks: positive and negative social effects. IEEE Commun Surv Tutorials 15(1):387–401
Rook KS (2015) Social networks in later life. Curr Dir Psychol Sci 24(1):45–51
Wolniewicz CA, Tiamiyu MF, Weeks JW, Elhai JD (2018) Problematic smartphone use and relations with negative affect, fear of missing out, and fear of negative and positive evaluation. Psychiatry Res 262:618–623
Faris H et al (2019) An intelligent system for spam detection and identification of the most relevant features based on evolutionary random weight networks. Inf Fusion 48:67–83
Bhat SY, Abulaish M (2013) Community-based features for identifying spammers in online social networks. In: Proceedings of the 2013 IEEE/ACM international conference on advances in social networks analysis and mining—ASONAM ’13, pp 100–107
Whang JJ, Jeong YS, Dhillon IS, Kang S, Lee J (2018) Fast Asynchronous Anti-TrustRank for Web Spam Detection
Grosse K, Papernot N, Manoharan P, Backes M, McDaniel P (2017) Adversarial examples for malware detection. Springer, Cham, pp 62–79
Kayes I, Iamnitchi A (2017) Privacy and security in online social networks: a survey. Online Soc Netw Media 3–4:1–21
Zhang Z, Gupta BB (2018) Social media security and trustworthiness: overview and new direction. Futur Gener Comput Syst 86:914–925
Fire M, Goldschmidt R, Elovici Y (2014) Online social networks: threats and solutions. IEEE Commun Surv Tutorials 16(4):2019–2036
Chen J, Mishler S, Hu B, Li N, Proctor RW (2018) The description-experience gap in the effect of warning reliability on user trust and performance in a phishing-detection context. Int J Hum Comput Stud 119:35–47
Jakobsson M (2018) Two-factor inauthentication—the rise in SMS phishing attacks. Comput Fraud Secur 2018(6):6–8
What is identity theft?—Definition from WhatIs.com.[Online]. Available: https://searchsecurity.techtarget.com/definition/identity-theft . Accessed 14 Dec 2018
Jain AK, Gupta BB (2021) A survey of phishing attack techniques, defence mechanisms and open research challenges. Enterprise Information Systems, pp 1–39
Identity Theft: The Various Types and Solutions [Online]. https://www.forbes.com/identity-theft/id-theft-and-types.html . Accessed 15 Dec 2020
Chaudhary P, Gupta BB (2018) Plague of cross-site scripting on web applications: a review, taxonomy and challenges. Int J Web Based Communit 14(1):64
Steffens M, Rossow C, Johns M, Stock B Don’t trust the locals: investigating the prevalence of persistent client-side cross-site scripting in the wild
Bukhari SN, Ahmad Dar M, Iqbal U (2018) Reducing attack surface corresponding to Type 1 cross-site scripting attacks using secure development life cycle practices. In 2018 fourth international conference on advances in electrical, electronics, information, communication and bio-informatics (AEEICB), pp 1–4
Kaubiyal J, Jain AK (2019) A feature based approach to detect fake profiles in Twitter. In: Proceedings of the 3rd international conference on big data and internet of things, pp 135–139
Facebook - Social Media Security | Protecting from Security Threats on Social Media: Facebook, LinkedIn, Twitter and Google Plus - Data Threat Detection and Prevention | Sophos Security Topics - Virus, Malware, Web, Antivirus and Social Media Security Trends [Online]. https://www.sophos.com/en-us/security-news-trends/security-trends/social-networking-security-threats/facebook.aspx . Accessed 2 Jan 2019
Bilge L, Strufe T, Balzarotti D, Kirda E (2009) All your contacts are belong to us. In: Proceedings of the 18th international conference on World wide web—WWW ’09, p 551
Kaur R, Singh S, Kumar H (2018) Rise of spam and compromised accounts in online social networks: a state-of-the-art review of different combating approaches. J Netw Comput Appl 112:53–88
Xin Y, Zhao C, Zhu H, Gao M (2018) A Survey of Malicious Accounts Detection in Large-Scale Online Social Networks. In: 2018 IEEE 4th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing, (HPSC) and IEEE International Conference on Intelligent Data and Security (IDS), pp 155–158
Sathish MMK, Indrani B (2018) A study on web hijacking techniques and browser attacks
Gao H, Hu J, Huang T (2011) Security issues in online social networks. In: IEEE Internet Comput , pp 56–63
Zhang W, Lin Y, Wu J, Zhou T (2018) Inference attack-resistant e-healthcare cloud system with fine-grained access control. In: IEEE Trans. Serv. Comput, pp 1–1
Mei B, Xiao Y, Li R, Li H, Cheng X, Sun Y (2018) Image and attribute based convolutional neural network inference attacks in social networks. In: IEEE Trans. Netw. Sci. Eng., pp 1–1
Jan MA, Nanda P, He X, Liu RP (2018) A Sybil attack detection scheme for a forest wildfire monitoring application. Futur Gener Comput Syst 80:613–626
Mishra AK, Tripathy AK, Puthal D, Yang LT (2019) Analytical model for sybil attack phases in internet of things. IEEE Internet Things J 6(1):379–387
Sinha R, Uppal D, Rathi R, Kanwar K (2018) Combating clickjacking using content security policy and aspect oriented programming. Springer, Singapore, pp 323–331
Albladi SM, Weir GRS (2018) A semi-automated security advisory system to resist cyber-attack in social networks. Springer, Cham, pp 146–156
Clickjacking - OWASP [Online]. https://www.owasp.org/index.php/Clickjacking . Accessed 14 Dec 2018
Protecting Your Users Against Clickjacking [Online]. https://www.hacksplaining.com/prevention/click-jacking . Accessed 15 Dec 2018
Tian W, Mao J, Jiang J, He Z, Zhou Z, Liu J (2018) Deeply understanding structure-based social network de-anonymization. Procedia Comput Sci 129:52–58
Mao J, Tian W, Jiang J, He Z, Zhou Z, Liu J (2018) Understanding structure-based social network de-anonymization techniques via empirical analysis. EURASIP J Wirel Commun Netw 2018(1):279
Jiang H et al (2017) SA framework based de-anonymization of social networks
Wondracek G, Holz T, Kirda E, Kruegel C (2010) A practical attack to de-anonymize social network users. Proc.—IEEE Symp. Secur. Priv., no. January, pp 223–238
What is Cyber Espionage? | Cyber Espionage Definition | Carbon Black [Online]. https://www.carbonblack.com/resources/definitions/what-is-cyber-espionage/ . Accessed 15 Dec 2018
Ghalaty NF, Ben Salem M (2018) A Hierarchical Framework to Detect Targeted Attacks using Deep Neural Network. In: 2018 IEEE International Conference on Big Data (Big Data), pp 5021–5026
5 Crucial Ways To Neutralize Cyber-Espionage [Online]. https://tech.co/5-crucial-ways-neutralize-cyber-espionage-2015-09 . Accessed 15 Dec 2018
Baldry AC, Sorrentino A, Farrington DP (2018) Post-traumatic stress symptoms among Italian preadolescents involved in school and cyber bullying and victimization. J Child Fam Stud pp 1–7
Holfeld B, Mishna F (2018) Longitudinal associations in youth involvement as victimized, bullying, or witnessing cyberbullying . Cyberpsychol Behav Soc Netw 21(4):234–239
What is Cyberbullying?—Definition from Techopedia [Online] https://www.techopedia.com/definition/2389/cyberbullying . Accessed 14 Dec 2018
What Is Cyberbullying | StopBullying.gov [Online] https://www.stopbullying.gov/cyberbullying/what-is-it/index.html . Accessed 15 Dec 2018
Smith PK, Mahdavi J, Carvalho M, Fisher S, Russell S, Tippett N (2008) Cyberbullying: its nature and impact in secondary school pupils. J Child Psychol Psychiatry 49(4):376–385
Ngejane C, Mabuza-Hocquet G, Eloff JH, Lefophane S (2018) Mitigating online sexual grooming cybercrime on social media using machine learning: a desktop survey. In 2018 international conference on advances in Big Data, computing and data communication systems (icABCD) pp 1–6
de Santisteban P, del Hoyo J, Alcázar-Córcoles MÁ, Gámez-Guadix M (2018) Progression, maintenance, and feedback of online child sexual grooming: a qualitative analysis of online predators. Child Abuse Negl 80:203–215
Internet Safety 101: Grooming [Online]. https://internetsafety101.org/grooming . Accessed 15 Dec 2018
Sahoo SR, Gupta BB (2019) Classification of various attacks and their defence mechanism in online social networks: a survey. Enterp Inf Syst 13(6):832–864
Cyberstalking | Get Safe Online [Online]. https://www.getsafeonline.org/protecting-yourself/cyberstalking/ . Accessed 15 Dec 2018
How To Protect Yourself From Cyberstalkers [Online]. https://us.norton.com/internetsecurity-how-to-how-to-protect-yourself-from-cyberstalkers.html . Accessed 15 Dec 2018
How to avoid becoming a cyberstalking victim | Association for Progressive Communications [Online]. https://www.apc.org/en/pubs/issue/how-avoid-becoming-cyberstalking-victim . Accessed 15 Dec 2018
What is Social Media Security | ZeroFOX. [Online]. https://www.zerofox.com/social-media-security/ . Accessed 3 Jan 2019
What is Digital Risk Monitoring? [Online]. https://www.zerofox.com/blog/what-is-digital-risk-monitoring/ . Accessed 8 Jan 2019
Sahoo SR, Gupta BB (2019) Hybrid approach for detection of malicious profiles in twitter. Comput Electr Eng 76:65–81
Dinakar K, Picard R, Lieberman H (2015) Common sense reasoning for detection, prevention, and mitigation of cyberbullying. IJCAI Int Jt Conf Artif Intell 3:4168–4172
Srinandhini B, Sheeba JI (2015) Online social network bullying detection using intelligence techniques. Procedia Comput Sci 45:485–492
Van Royen K, Poels K, Daelemans W, Vandebosch H (2014) Automatic monitoring of cyberbullying on social networking sites: from technological feasibility to desirability. Telemat Inform 32(1):89–97
Reynolds K, Kontostathis A, Edwards L (2011) Using machine learning to detect cyberbullying. Proc.—10th Int. Conf. Mach. Learn. Appl. ICMLA, vol 2, pp 241–244
Escalante HJ, Villatoro-Tello E, Garza SE, López-Monroy AP, Montes-y-Gómez M, Villaseñor-Pineda L (2017) Early detection of deception and aggressiveness using profile-based representations. Expert Syst Appl 89:99–111
Anas A, Khatab S, Salah A (2018) Hovering Patterns: Clickjacking Defense Technique, vol 18, no. 2, pp 130–137
Rydstedt G, Bursztein E, Boneh D, Jackson C (2010) Busting frame busting: a study of clickjacking vulnerabilities on popular sites. In: IEEE Oakl. Web 2.0 Secur. Priv. Work . , p 6
Eterovic-Soric B, Choo KKR, Ashman H, Mubarak S (2017) Stalking the stalkers—detecting and deterring stalking behaviours using technology: a review. Comput Secur 70:278–289
Frommholz I, Al-Khateeb HM, Potthast M, Ghasem Z, Shukla M, Short E (2016) On textual analysis and machine learning for cyberstalking detection. Datenbank-Spektrum 16(2):127–135
Bendovschi A (2015) Cyber-attacks—trends, patterns and security countermeasures. Procedia Econ Financ 28(April):24–31
Ramalingam D, Chinnaiah V (2018) Fake profile detection techniques in large-scale online social networks: a comprehensive review. Comput Electr Eng 65(3):165–177
Khan RU, Zhang X, Kumar R, Sharif A, Golilarz NA, Alazab M (2019) An adaptive multi-layer botnet detection technique using machine learning classifiers. Appl Sci 9(11):2375
Hakak S, Alazab M, Khan S, Gadekallu TR, Maddikunta PKR, Khan WZ (2021) An ensemble machine learning approach through effective feature extraction to classify fake news. Futur Gener Comput Syst 117:47–58
Numan M, Subhan F, Khan WZ, Hakak S, Haider S, Reddy GT, Jolfaei A, Alazab M (2020) A systematic review on clone node detection in static wireless sensor networks. IEEE Access 8:65450–65461
Al-Qurishi M, Alrubaian M, Rahman SMM, Alamri A, Hassan MM (2018) A prediction system of Sybil attack in social network using deep-regression model. Futur Gener Comput Syst 87:743–753
Faghani MR, Saidi H (2009) Malware propagation in online social networks. In: 2009 4th Int. Conf. Malicious Unwanted Software, MALWARE, pp 8–14
Mostafi S, Khan F, Chakrabarty A, Suh DY, Piran MJ (2019) An algorithm for mapping a traffic domain into a complex network: a social internet of things approach. IEEE Access 7:40925–40940
Borrego C, Amadeo M, Molinaro A, Jhaveri RH (2019) Privacy-preserving forwarding using homomorphic encryption for information-centric wireless Ad hoc networks. IEEE Commun Lett 23(10):1708–1711
Rathee G, Garg S, Kaddoum G, Jayakody DNK, Piran J, Muhammad G (2020) A trusted social network using hypothetical mathematical model and decision-based scheme. IEEE Access
Pandey B, Bhanodia PK, Khamparia A, Pandey DK (2019) A comprehensive survey of edge prediction in social networks: techniques, parameters and challenges. Expert Syst Appl 124:164–181. https://doi.org/10.1016/j.eswa.2019.01.040
Article Google Scholar
Peng S, Zhou Y, Cao L, Yu S, Niu J, Jia W (2018) Influence analysis in social networks: a survey. J Netw Comput Appl 106:17–32. https://doi.org/10.1016/j.jnca.2018.01.005
Dakiche N, Tayeb FBS, Slimani Y, Benatchba K (2019) Tracking community evolution in social networks: a survey. Inf Process Manage 56(3):1084–1102
De Salve A, Mori P, Ricci L (2018) A survey on privacy in decentralized online social networks. Comput Sci Rev 27:154–176. https://doi.org/10.1016/j.cosrev.2018.01.001
Ramalingam D, Chinnaiah V (2018) Fake profile detection techniques in large-scale online social networks: a comprehensive review. Comput Electr Eng 65:165–177. https://doi.org/10.1016/j.compeleceng.2017.05.020
Sarmah U, Bhattacharyya DK, Kalita JK (2018) A survey of detection methods for XSS attacks. J Netw Comput Appl 118:113–143. https://doi.org/10.1016/j.jnca.2018.06.004
Song J, Jamous N, Turowski K (2019) A dynamic perspective: local interactions driving the spread of social networks. Enterp Inf Syst 13(2):219–235. https://doi.org/10.1080/17517575.2018.1499133
Maleszka M (2018) Application of collective knowledge diffusion in a social network environment. Enterp Inf Syst 1–23
Tse YK, Loh H, Ding J, Zhang M (2018) An investigation of social media data during a product recall scandal. Enterp Inf Syst 12(6):733–751. https://doi.org/10.1080/17517575.2018.1455110
10 Tips to Stay Safe on Social Media - Information Technology Services [Online]. https://carleton.ca/its/2016/social-media-safety/ . Accessed 14 Dec 2018
Foroughi F, Luksch P (2018) Observation measures to profile user security behaviour. In: 2018 International conference on cyber security and protection of digital services (Cyber Security), pp 1–6
Thakur K, Hayajneh T, Tseng J (2019) Cyber security in social media: challenges and the way forward. IT Prof 21(2):41–49
Harden BJ, Dowd KL, Webb MB, Landsverk J, Testa M (2010) Child welfare and child well-being: new perspectives from the national survey of child and adolescent well-being. Child Welf. Child Well-Being New Perspect. From Natl. Surv. Child Adolesc. Well-Being, vol 421, pp 1–448
Sahoo SR, Gupta BB (2020) Real-time detection of fake account in twitter using machine-learning approach. In: Advances in computational intelligence and communication technology. Springer, Singapore, pp 149–159
8 Social Media Security Tips to Mitigate Risks [Online]. https://blog.hootsuite.com/social-media-security-for-business/ . Accessed 14 Dec 2018
Byrne E, Vessey JA, Pfeifer L (2018) Cyberbullying and social media: information and interventions for school nurses working with victims, students, and families. J Sch Nurs 34(1):38–50
Security Weak Points: Social Media | SolarWinds MSP [Online]. https://www.solarwindsmsp.com/blog/security-weak-points-social-media . Accessed 13 Jan 2019
Social Media Security - Security News - Trend Micro USA [Online]. https://www.trendmicro.com/vinfo/us/security/news/social-media-security . Accessed 13 Jan 2019
12 tips for safe social networking | Network World [Online]. https://www.networkworld.com/article/2346606/microsoft-subnet/microsoft-subnet-12-tips-for-safe-social-networking.html . Accessed 13 Jan 2019
Social Media - Stay Safe Online [Online]. https://staysafeonline.org/stay-safe-online/securing-key-accounts-devices/social-media/ . Accessed 7 Jan 2019
Security Weak Points: Social Media | SolarWinds MSP [Online]. https://www.solarwindsmsp.com/blog/security-weak-points-social-media . Accessed 19 Jan 2019
Download references
Author information
Authors and affiliations.
National Institute of Technology Kurukshetra, Kurukshetra, India
Ankit Kumar Jain & Jyoti Kaubiyal
Vellore Institute of Technology Andhra Pradesh, Amaravati, India
Somya Ranjan Sahoo
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Ankit Kumar Jain .
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Jain, A.K., Sahoo, S.R. & Kaubiyal, J. Online social networks security and privacy: comprehensive review and analysis. Complex Intell. Syst. 7 , 2157–2177 (2021). https://doi.org/10.1007/s40747-021-00409-7
Download citation
Received : 01 March 2021
Accepted : 19 May 2021
Published : 01 June 2021
Issue Date : October 2021
DOI : https://doi.org/10.1007/s40747-021-00409-7
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Online social network
- Security and privacy
- Social threats
- Find a journal
- Publish with us
- Track your research
A Review on Social Network Analysis Methods and Algorithms
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
- Open access
- Published: 16 March 2020
Exploring the role of social media in collaborative learning the new domain of learning
- Jamal Abdul Nasir Ansari 1 &
- Nawab Ali Khan 1
Smart Learning Environments volume 7 , Article number: 9 ( 2020 ) Cite this article
378k Accesses
178 Citations
19 Altmetric
Metrics details
This study is an attempt to examine the application and usefulness of social media and mobile devices in transferring the resources and interaction with academicians in higher education institutions across the boundary wall, a hitherto unexplained area of research. This empirical study is based on the survey of 360 students of a university in eastern India, cognising students’ perception on social media and mobile devices through collaborative learning, interactivity with peers, teachers and its significant impact on students’ academic performance. A latent variance-based structural equation model approach was followed for measurement and instrument validation. The study revealed that online social media used for collaborative learning had a significant impact on interactivity with peers, teachers and online knowledge sharing behaviour.
Additionally, interactivity with teachers, peers, and online knowledge sharing behaviour has seen a significant impact on students’ engagement which consequently has a significant impact on students’ academic performance. Grounded to this finding, it would be valuable to mention that use of online social media for collaborative learning facilitate students to be more creative, dynamic and research-oriented. It is purely a domain of knowledge.
Introduction
The explosion of Information and Communication Technology (ICT) has led to an increase in the volume and smoothness in transferring course contents, which further stimulates the appeasement of Digital Learning Communities (DLCs). The millennium and naughtiness age bracket were Information Technology (IT) centric on web space where individual and geopolitical disperse learners accomplished their e-learning goals. The Educause Center for Applied Research [ECAR] ( 2012 ) surveyed students in higher education mentioned that students are pouring the acceptance of mobile computing devices (cellphones, smartphones, and tablet) in Higher Education Institutions (HEIs), roughly 67% surveyed students accepted that mobile devices and social media play a vital role in their academic performance and career enhancement. Mobile devices and social media provide excellent educational e-learning opportunities to the students for academic collaboration, accessing in course contents, and tutors despite the physical boundary (Gikas & Grant, 2013 ). Electronic communication technologies accelerate the pace of their encroachment of every aspect of life, the educational institutions incessantly long decades to struggle in seeing the role of such devices in sharing the contents, usefulness and interactivity style. Adoption and application of mobile devices and social media can provide ample futuristic learning opportunities to the students in accessing course contents as well as interaction with peers and experts (Cavus & Ibrahim, 2008 , 2009 ; Kukulska-Hulme & Shield, 2008 ; Nihalani & Mayrath, 2010 ; Richardson & Lenarcic, 2008 , Shih, 2007 ). Recently Pew Research Center reported that 55% American teenage age bracket of 15–17 years using online social networking sites, i.e. Myspace and Facebook (Reuben, 2008 ). Social media, the fast triggering the mean of virtual communication, internet-based technologies changed the life pattern of young youth.
Use of social media and mobile devices presents both advantages as well as challenges, mostly its benefits seen in terms of accessing course contents, video clip, transfer of the instructional notes etc. Overall students feel that social media and mobile devices are the cheap and convenient tools of obtaining relevant information. Studies in western countries have confronted that online social media use for collaborative learning has a significant contribution to students’ academic performance and satisfaction (Zhu, 2012 ). The purpose of this research project was to explore how learning and teaching activities in higher education institutions were affected by the integration and application of mobile devices in sharing the resource materials, interaction with colleagues and students’ academic performance. The broad goal of this research was to contemporise the in-depth perspectives of students’ perception of mobile devices and social media in learning and teaching activities. However, this research paper paid attention to only students’ experiences, and their understanding of mobile devices and social media fetched changes and its competency in academic performance. The fundamental research question of this research was, what are the opinions of students on social media and mobile devices when it is integrating into higher education for accessing, interacting with peers.
A researcher of the University of Central Florida reported that electronic devices and social media create an opportunity to the students for collaborative learning and also allowed the students in sharing the resource materials to the colleagues (Gikas & Grant, 2013 ). The result of the eight Egyptian universities confirmed that social media have the significant impact on higher education institutions especially in term of learning tools and teaching aids, faculty members’ use of social media seen at a minimum level due to several barriers (internet accessibility, mobile devices etc.).
Social media and mobile devices allow the students to create, edit and share the course contents in textual, video or audio forms. These technological innovations give birth to a new kind of learning cultures, learning based on the principles of collective exploration and interaction (Selwyn, 2012 ). Social media the phenomena originated in 2005 after the Web2.0 existence into the reality, defined more clearly as “a group of Internet-based applications that build on the ideological and technological foundation of web 2.0 and allow creation and exchange of user-generated contents (Kaplan & Haenlein, 2010 ). Mobile devices and social media provide opportunities to the students for accessing resources, materials, course contents, interaction with mentor and colleagues (Cavus & Ibrahim, 2008 , 2009 ; Richardson & Lenarcic, 2008 ).
Social media platform in academic institutions allows students to interact with their mentors, access their course contents, customisation and build students communities (Greenhow, 2011a , 2011b ). 90% school going students currently utilise the internet consistently, with more than 75% teenagers using online networking sites for e-learning (DeBell & Chapman, 2006 ; Lenhart, Arafeh, & Smith, 2008 ; Lenhart, Madden, & Hitlin, 2005 ). The result of the focus group interview of the students in 3 different universities in the United States confirmed that use of social media created opportunities to the learners for collaborative learning, creating and engaging the students in various extra curriculum activities (Gikas & Grant, 2013 ).
Research background and hypotheses
The technological innovation and increased use of the internet for e-learning by the students in higher education institutions has brought revolutionary changes in communication pattern. A report on 3000 college students in the United States revealed that 90% using Facebook while 37% using Twitter to share the resource materials as cited in (Elkaseh, Wong, & Fung, 2016 ). A study highlighted that the usage of social networking sites in educational institutions has a practical outcome on students’ learning outcomes (Jackson, 2011 ). The empirical investigation over 252 undergraduate students of business and management showed that time spent on twitter and involvement in managing social lives and sharing information, course-related influences their performance (Evans, 2014 ).
Social media for collaborative learning, interactivity with teachers, interactivity with peers
Many kinds of research confronted on the applicability of social media and mobile devices in higher education for interaction with colleagues.90% of faculty members use some social media in courses they were usually teaching or professional purposes out of the campus life. Facebook and YouTube are the most visited sites for the professional outcomes, around 2/3rd of the all-faculty use some medium fora class session, and 30% posted contents for students engagement in reading, view materials (Moran, Seaman, & Tinti-Kane, 2011 ). Use of social media and mobile devices in higher education is relatively new phenomena, completely hitherto area of research. Research on the students of faculty of Economics at University of Mortar, Bosnia, and Herzegovina reported that social media is already used for the sharing the materials and exchanges of information and students are ready for active use of social networking site (slide share etc.) for educational purposes mainly e-learning and communication (Mirela Mabić, 2014 ).
The report published by the U.S. higher education department stated that the majority of the faculty members engaged in different form of the social media for professional purposes, use of social media for teaching international business, sharing contents with the far way students, the use of social media and mobile devices for sharing and the interactive nature of online and mobile technologies build a better learning environment at international level. Responses on 308 graduate and postgraduate students in Saudi Arabia University exhibited that positive correlation between chatting, online discussion and file sharing and knowledge sharing, and entertainment and enjoyment with students learning (Eid & Al-Jabri, 2016 ). The quantitative study on 168 faculty members using partial least square (PLS-SEM) at Carnegie classified Doctoral Research University in the USA confirmed that perceived usefulness, external pressure and compatibility of task-technology have positive effect on social media use, the higher the degree of the perceived risk of social media, the less likely to use the technological tools for classroom instruction, the study further revealed that use of social media for collaborative learning has a positive effect on students learning outcome and satisfaction (Cao, Ajjan, & Hong, 2013 ). Therefore, the authors have hypothesized:
H1: Use of social media for collaborative learning is positively associated with interactivity with teachers.
Additionally, Madden and Zickuhr ( 2011 ) concluded that 83% of internet user within the age bracket of 18–29 years adopting social media for interaction with colleagues. Kabilan, Ahmad, and Abidin ( 2010 ) made an empirical investigation on 300 students at University Sains Malaysia and concluded that 74% students found to be the same view that social media infuses constructive attitude towards learning English (Fig. 1 ).
Research Model
Reuben ( 2008 ) concluded in his study on social media usage among professional institutions revealed that Facebook and YouTube used over half of 148 higher education institutions. Nevertheless, a recent survey of 456 accredited United States institutions highlighted 100% using some form of social media, notably Facebook 98% and Twitter 84% for e-learning purposes, interaction with mentors (Barnes & Lescault, 2011 ).
Information and communication technology (ICT), such as web-based application and social networking sites enhances the collaboration and construction of knowledge byway of instruction with outside experts (Zhu, 2012 ). A positive statistically significant relationship was found between student’s use of a variety of social media tools and the colleague’s fellow as well as the overall quality of experiences (Rutherford, 2010 ). The potential use of social media leads to collaborative learning environments which allow students to share education-related materials and contents (Fisher & Baird, 2006 ). The report of 233 students in the United States higher educations confirmed that more recluse students interact through social media, which assist them in collaborative learning and boosting their self-confidence (Voorn & Kommers, 2013 ). Thus hypotheses as
H2: Use of social media for collaborative learning is positively associated with interactivity with peers.
Social media for collaborative learning, interactivity with peers, online knowledge sharing behaviour and students’ engagement
Students’ engagement in social media and its types represent their physical and mental involvement and time spent boost to the enhancement of educational Excellency, time spent on interaction with peers, teachers for collaborative learning (Kuh, 2007 ). Students’ engagement enhanced when interacting with peers and teacher was in the same direction, shares of ideas (Chickering & Gamson, 1987 ). Engagement is an active state that is influenced by interaction or lack thereof (Leece, 2011 ). With the advancement in information technology, the virtual world becomes the storehouse of the information. Liccardi et al. ( 2007 ) concluded that 30% students were noted to be active on social media for interaction with their colleagues, tutors, and friends while more than 52% used some social media forms for video sharing, blogs, chatting, and wiki during their class time. E-learning becomes now sharp and powerful tools in information technology and makes a substantial impact on the student’s academic performance. Sharing your knowledge will make you better. Social network ties were shown to be the best predictors of online knowledge sharing intention, which in turn associated with knowledge sharing behaviour (Chen, Chen, & Kinshuk, 2009 ). Social media provides the robust personalised, interactive learning environment and enhances in self-motivation as cited in (Al-Mukhaini, Al-Qayoudhi, & Al-Badi, 2014 ). Therefore, it was hypothesised that:
H3: Use of social media for collaborative learning is positively associated with online knowledge sharing behaviour.
Broadly Speaking social media/sites allow the students to interact, share the contents with colleagues, also assisting in building connections with others (Cain, 2008 ). In the present era, the majority of the college-going students are seen to be frequent users of these sophisticated devices to keep them informed and updated about the external affair. Facebook reported per day 1,00,000 new members join; Facebook is the most preferred social networking sites among the students of the United States as cited in (Cain, 2008 ). The researcher of the school of engineering, Swiss Federal Institute of Technology Lausanne, Switzerland, designed and developed Grasp, a social media platform for their students’ collaborative learning, sharing contents (Bogdanov et al., 2012 ). The utility and its usefulness could be seen in the University of Geneva and Tongji University at both two educational places students were satisfied and accept ‘ Grasp’ to collect, organised and share the contents. Students use of social media will interact ubiquity, heterogeneous and engaged in large groups (Wankel, 2009 ). So we hypotheses
H4: More interaction with teachers leads to higher students’ engagement.
However, a similar report published on 233 students revealed that social media assisted in their collaborative learning and self-confidence as they prefer communication technology than face to face communication. Although, the students have the willingness to communicate via social media platform than face to face (Voorn & Kommers, 2013 ). The potential use of social media tools facilitates in achieving higher-level learning through collaboration with colleagues and other renewed experts in their field (Junco, Heiberger, & Loken, 2011 ; Meyer, 2010 ; Novak, Razzouk, & Johnson, 2012 ; Redecker, Ala-Mutka, & Punie, 2010 ). Academic self-efficacy and optimism were found to be strongly related to performance, adjustment and consequently both directly impacted on student’s academic performance (Chemers, Hu, & Garcia, 2001 ). Data of 723 Malaysian researchers confirmed that both male and female students were satisfied with the use of social media for collaborative learning and engagement was found positively affected with learning performance (Al-Rahmi, Alias, Othman, Marin, & Tur, 2018 ). Social media were seen as a powerful driver for learning activities in terms of frankness, interactivity, and friendliness.
Junco et al. ( 2011 ) conducted research on the specific purpose of the social media; how Twitter impacted students’ engagement, found that it was extent discussion out of class, their participation in panel group (Rodriguez, 2011 ). A comparative study conducted by (Roblyer, McDaniel, Webb, Herman, & Witty, 2010 ) revealed that students were more techno-oriented than faculty members and more likely using Facebook and such similar communication technology to support their class-related task. Additionally, faculty members were more likely to use traditional techniques, i.e. email. Thus hypotheses framed is that:
H5: More interaction with peers ultimately leads to better students’ engagement.
Social networking sites and social media are closely similar, which provide a platform where students can interact, communicate, and share emotional intelligence and looking for people with other attitudes (Gikas & Grant, 2013 ). Facebook and YouTube channel use also increased in the skills/ability and knowledge and outcomes (Daniel, Isaac, & Janet, 2017 ). It was highlighted that 90% of faculty members were using some sort of social media in their courses/ teaching. Facebook was the most visited social media sites as per study, 40% of faculty members requested students to read and views content posted on social media; majority reports that videos, wiki, etc. the primary source of acquiring knowledge, social networking sites valuable tool/source of collaborative learning (Moran et al., 2011 ). However, more interestingly, in a study which was carried out on 658 faculty members in the eight different state university of Turkey, concluded that nearly half of the faculty member has some social media accounts.
Further reported that adopting social media for educational purposes, the primary motivational factor which stimulates them to use was effective and quick means of communication technology (Akçayır, 2017 ). Thus hypotheses formulated is:
H6: Online knowledge sharing behaviour is positively associated with the students’ engagement.
Using multiple treatment research design, following act-react to increase students’ academic performance and productivity, it was observed when self–monitoring record sheet was placed before students and seen that students engagement and educational productivity was increased (Rock & Thead, 2007 ). Student engagement in extra curriculum activities promotes academic achievement (Skinner & Belmont, 1993 ), increases grade rate (Connell, Spencer, & Aber, 1994 ), triggering student performance and positive expectations about academic abilities (Skinner & Belmont, 1993 ). They are spending time on online social networking sites linked to students engagement, which works as the motivator of academic performance (Fan & Williams, 2010 ). Moreover, it was noted in a survey of over 236 Malaysian students that weak association found between the online game and student’s academic performance (Eow, Ali, Mahmud, & Baki, 2009 ). In a survey of 671 students in Jordan, it was revealed that student’s engagement directly influences academic performance, also seen the indirect effect of parental involvement over academic performance (Al-Alwan, 2014 ). Engaged students are perceptive and highly active in classroom activities, ready to participate in different classroom extra activities and expose motivation to learn, which finally leads in academic achievement (Reyes, Brackett, Rivers, White, & Salovey, 2012 ). A mediated role of students engagement seen in 1399 students’ classroom emotional climate and grades (Reyes et al., 2012 ). A statistically significant relation was noticed between online lecture and exam performance.
Nonetheless, intelligence quotient, personality factors, students must be engaged in learning activities as cited in (Bertheussen & Myrland, 2016 ). The report of the 1906 students at 7 universities in Colombia confirmed that the weak correlation between collaborative learning, students faculty interaction with academic performance (Pineda-Báez et al., 2014 ) Thus, the hypothesis
H7: Student's Engagement is positively associated with the student's academic performance.
Methodology
To check the students’ perception on social media for collaborative learning in higher education institutions, Data were gathered both offline and online survey administered to students from one public university in Eastern India (BBAU, Lucknow). For the sake of this study, indicators of interactivity with peers and teachers, the items of students engagement, the statement of social media for collaborative learning, and the elements of students’ academic performance were adopted from (AL-Rahmi & Othman, 2013 ). The statement of online knowledge sharing behaviour was taken from (Ma & Yuen, 2011 ).
The indicators of all variables which were mentioned above are measured on the standardised seven-point Likert scale with the anchor (1-Strongly Disagree, to 7-Strongly Agree). Interactivity with peers was measured using four indicators; the sample items using social media in class facilitates interaction with peers ; interactivity with teachers was measured using four symbols, the sample item is using social media in class allows me to discuss with the teacher. ; engagement was measured using three indicators by using social media I felt that my opinions had been taken into account in this class ; social media for collaborative learning was measured using four indicators collaborative learning experience in social media environment is better than in a face-to-face learning environment ; students’ academic performance was measured using five signs using social media to build a student-lecturer relationship with my lecturers, and this improves my academic performance ; online knowledge sharing behaviour was assessed using five symbols the counsel was received from other colleague using social media has increased our experience .
Procedure and measurement
A sample of 360 undergraduate students was collected by convenience sampling method of a public university in Eastern India. The proposed model of study was measured and evaluated using variance based structured equation model (SEM)-a latent multi variance technique which provides the concurrent estimation of structural and measurement model that does not meet parametric assumption (Coelho & Duarte, 2016 ; Haryono & Wardoyo, 2012 ; Lee, 2007 ; Moqbel, Nevo, & Kock, 2013 ; Raykov & Marcoulides, 2000 ; Williams, Rana, & Dwivedi, 2015 ). The confirmatory factor analysis (CFA) was conducted to ensure whether the widely accepted criterion of discriminate and convergent validity met or not. The loading of all the indicators should be 0.50 or more (Field, 2011 ; Hair, Anderson, Tatham, & Black, 1992 ). And it should be statistically significant at least at the 0.05.
Demographic analysis (Table 1 )
The majority of the students in this study were females (50.8%) while male students were only 49.2% with age 15–20 years (71.7%). It could be pointed out at this juncture that the majority of the students (53.9%) in BBAU were joined at least 1–5 academic pages for their getting information, awareness and knowledge. 46.1% of students spent 1–5 h per week on social networking sites for collaborative learning, interaction with teachers at an international level. The different academic pages followed for accessing material, communication with the faculty members stood at 44.4%, there would be various forms of the social networking sites (LinkedIn, Slide Share, YouTube Channel, Researchgate) which provide the facility of online collaborative learning, a platform at which both faculty members and students engaged in learning activities.
As per report (Nasir, Khatoon, & Bharadwaj, 2018 ), most of the social media user in India are college-going students, 33% girls followed by 27% boys students, and this reports also forecasted that India is going to become the highest 370.77 million internet users in 2022. Additionally, the majority of the faculty members use smartphone 44% to connect with the students for sharing material content. Technological advantages were the pivotal motivational force which stimulates faculty members and students to exploits the opportunities of resource materials (Nasir & Khan, 2018 ) (Fig. 2 ).
Reasons for Using Social Media
When the students were asked for what reason did they use social media, it was seen that rarely using for self-promotion, very frequently using for self-education, often used for passing the time with friends, and so many fruitful information the image mentioned above depicting.
Instrument validation
The structural model was applied to scrutinize the potency and statistically significant relationship among unobserved variables. The present measurement model was evaluated using Confirmatory Factor Analysis (CFA), and allied procedures to examine the relationship among hypothetical latent variables has acceptable reliability and validity. This study used both SPSS 20.0 and AMOS to check measurement and structural model (Field, 2013 ; Hair, Anderson, et al., 1992 ; Mooi & Sarstedt, 2011 ; Norusis, 2011 ).
The Confirmatory Factor Analysis (CFA) was conducted to ensure whether the widely accepted criterion of discriminant and convergent validity met or not. The loading of all the indicators should be 0.70 or more it should be statistically significant at least at the 0.05 (Field, 2011 ; Hair, Anderson, et al., 1992 ).
CR or CA-based tests measured the reliability of the proposed measurement model. The CA provides an estimate of the indicators intercorrelation (Henseler & Sarstedt, 2013 . The benchmark limits of the CA is 0.7 or more (Nunnally & Bernstein, 1994 ). As per Table 2 , all latent variables in this study above the recommended threshold limit. Although, Average Variance Extracted (AVE) has also been demonstrated which exceed the benchmark limit 0.5. Thus all the above-specified values revealed that our instrument is valid and effective. (See Table 2 for the additional information) (Table 3 ).
In a nutshell, the measurement model clear numerous stringent tests of convergent validity, discriminant validity, reliability, and absence of multi-collinearity. The finding demonstrated that our model meets widely accepted data validation criteria. (Schumacker & Lomax, 2010 ).
The model fit was evaluated through the Chi-Square/degree of freedom (CMIN/DF), Root Mean Residual (RMR), Root Mean Square Error of Approximation (RMSEA), Comparative Fit Index (CFI), and Goodness of fit index (GFI) and Tucker-Lewis Index (TLI). The benchmark limit of the CFI, TLI, and GFI 0.90or more (Hair et al., 2016 ; Kock, 2011 ). The model study demonstrated in the table, as mentioned above 4 that the minimum threshold limit was achieved (See Table 4 for additional diagnosis).
Path coefficient of several hypotheses has been demonstrated in Fig. 3 , which is a variable par relationship. β (beta) Coefficients, standardised partial regression coefficients signify the powers of the multivariate relationship among latent variables in the model. Remarkably, it was observed that seven out of the seven proposed hypotheses were accepted and 78% of the explained variance in students’ academic performance, 60% explained variance in interactivity with teachers, 48% variance in interactivity with peers, 43% variance in online knowledge sharing behaviour and 79% variance in students’ engagement. Social media collaborative learning has a significant association with teacher interactivity(β = .693, P < 0.001), demonstrating that there is a direct effect on interaction with the teacher by social media when other variables are controlled. On the other hand, use of social media for collaborative learning has noticed statistically significant positive relationship with peers interactivity (β = .704, p < 0.001) meaning thereby, collaborative learning on social media by university students, leads to the high degree of interaction with peers, colleagues. Implied 10% rise in social media use for learning purposes, expected 7.04% increase in interaction with peers.
Path Diagram
Use of social media for collaborating learning has a significant positive association with online knowledge sharing behaviour (β = .583, p < 0.001), meaning thereby that the more intense use of social media for collaborative learning by university students, the more knowledge sharing between peers and colleagues. Also, interaction with the teacher seen the significant statistical positive association with students engagement (β = .450, p < 0.001), telling that the more conversation with teachers, leads to a high level of students engagement. Similarly, the practical interpretation of this result is that there is an expected 4.5% increase in student’s participation for every 10% increase in interaction with teachers. Interaction with peers has a significant positive association with students engagement (β = .210, p < 0.001). Practically, the finding revealed that 10% upturn in student’s involvement, there is a 2.1% increase in peer’s interaction. There is a significant positive association between online knowledge sharing behaviour and students engagement (β = 0.247, p < 0.001), and finally students engagement has been a statistically significant positive relationship with students’ academic performance (β = .972, p < 0.001), this is the clear indication that more engaged students in collaborative learning via social media leads to better students’ academic performance.
Discussion and implication
There is a continuing discussion in the academic literature that use of such social media and social networking sites would facilitate collaborative learning. It is human psychology generally that such communication media technology seems only for entertainment, but it should be noted here carefully that if such communication technology would be followed with due attention prove productive. It is essential to acknowledge that most university students nowadays adopting social media communication to interact with colleagues, teachers and also making the group be in touch with old friends and even a convenient source of transferring the resources. In the present era, the majority of the university students having diversified social media community groups like Whatsapp, Facebook pages following different academic web pages to upgrade their knowledge.
Practically for every 10% rise in students’ engagement, expected to be 2.1% increase in peer interaction. As the study suggested that students engage in different sites, they start discussing with colleagues. More engaged students in collaborative learning through social media lead better students’ academic performance. The present study revealed that for every 10% increase in student’s engagement, there would be an expected increase in student academic performance at a rate of 9.72. This extensive research finding revealed that the application of online social media would facilitate the students to become more creative, dynamics and connect to the worldwide instructor for collaborative learning.
Accordingly, the use of online social media for collaborative learning, interaction with mentors and colleagues leadbetter student’s engagement which consequently affects student’s academic performance. The higher education authority should provide such a platform which can nurture the student’s intellectual talents. Based on the empirical investigation, it would be said that students’ engagement, social media communication devices facilitate students to retrieve information and interact with others in real-time regarding sharing teaching materials contents. Additionally, such sophisticated communication devices would prove to be more useful to those students who feel too shy in front of peers; teachers may open up on the web for the collaborative learning and teaching in the global scenario and also beneficial for physically challenged students. It would also make sense that intensive use of such sophisticated technology in teaching pedagogical in higher education further facilitates the teachers and students to interact digitally, web-based learning, creating discussion group, etc. The result of this investigation confirmed that use of social media for collaborative learning purposes, interaction with peers, and teacher affect their academic performance positively, meaning at this moment that implementation of such sophisticated communication technology would bring revolutionary, drastic changes in higher education for international collaborative learning (Table 5 ).
Limitations and future direction
Like all the studies, this study is also not exempted from the pitfalls, lacunas, and drawbacks. The first and foremost research limitation is it ignores the addiction of social media; excess use may lead to destruction, deviation from the focal point. The study only confined to only one academic institution. Hence, the finding of the project cannot be generalised as a whole. The significant positive results were found in this study due to the fact that the social media and mobile devices are frequently used by the university going students not only as a means of gratification but also for educational purposes.
Secondly, this study was conducted on university students, ignoring the faculty members, it might be possible that the faculty members would not have been interested in interacting with the students. Thus, future research could be possible towards faculty members in different higher education institutions. To the authors’ best reliance, this is the first and prime study to check the usefulness and applicability of social media in the higher education system in the Indian context.
Concluding observations
Based on the empirical investigation, it could be noted that application and usefulness of the social media in transferring the resource materials, collaborative learning and interaction with the colleagues as well as teachers would facilitate students to be more enthusiastic and dynamic. This study provides guidelines to the corporate world in formulating strategies regarding the use of social media for collaborative learning.
Availability of data and materials
The corresponding author declared here all types of data used in this study available for any clarification. The author of this manuscript ready for any justification regarding the data set. To make publically available of the data used in this study, the seeker must mail to the mentioned email address. The profile of the respondents was completely confidential.
Akçayır, G. (2017). Why do faculty members use or not use social networking sites for education? Computers in Human Behavior, 71 , 378–385.
Article Google Scholar
Al-Alwan, A. F. (2014). Modeling the relations among parental involvement, school engagement and academic performance of high school students. International Education Studies, 7 (4), 47–56.
Al-Mukhaini, E. M., Al-Qayoudhi, W. S., & Al-Badi, A. H. (2014). Adoption of social networking in education: A study of the use of social networks by higher education students in Oman. Journal of International Education Research, 10 (2), 143–154.
Google Scholar
Al-Rahmi, W. M., Alias, N., Othman, M. S., Marin, V. I., & Tur, G. (2018). A model of factors affecting learning performance through the use of social media in Malaysian higher education. Computers & Education, 121 , 59–72.
Al-Rahmi, W. M., & Othman, M. S. (2013). Evaluating student’s satisfaction of using social media through collaborative learning in higher education. International Journal of Advances in Engineering & Technology, 6 (4), 1541–1551.
Arbuckle, J. (2008). Amos 17.0 user's guide . Chicago: SPSS Inc..
Barnes, N. G., & Lescault, A. M. (2011). Social media adoption soars as higher-ed experiments and reevaluates its use of new communications tools . North Dartmouth: Center for Marketing Research. University of Massachusetts Dartmouth.
Bertheussen, B. A., & Myrland, Ø. (2016). Relation between academic performance and students’ engagement in digital learning activities. Journal of Education for Business, 91 (3), 125–131.
Bogdanov, E., Limpens, F., Li, N., El Helou, S., Salzmann, C., & Gillet, D. (2012). A social media platform in higher education. In Proceedings of the 2012 IEEE Global Engineering Education Conference (EDUCON) (pp. 1–8). IEEE.
Byrne, B. M. (1994). Structural equation modeling with EQS and EQS/windows: basic concepts, applications, and programming . Thousand Oaks: Sage.
Cain, J. (2008). Online social networking issues within academia and pharmacy education. American Journal of Pharmaceutical Education. https://doi.org/10.5688/aj720110 .
Cao, Y., Ajjan, H., & Hong, P. (2013). Using social media applications for educational outcomes in college teaching: a structural equation analysis. British Journal of Educational Technology, 44 (4), 581–593. https://doi.org/10.1111/bjet.12066 .
Cavus, N., & Ibrahim, D. (2008). A mobile tool for learning English words, Online Submission (pp. 6–9) Retrieved from http://libezproxy.open.ac.uk/login?url=http://search.ebscohost.com/login.aspx?direct=true&db=eric&AN=ED504283&site=ehost-live&scope=site .
Cavus, N., & Ibrahim, D. (2009). M-learning: An experiment in using SMS to support learning new English language words. British Journal of Educational Technology, 40 (1), 78–91.
Chemers, M. M., Hu, L. T., & Garcia, B. F. (2001). Academic self-efficacy and first-year college student performance and adjustment. Journal of Educational Psychology, 93 (1), 55–64. https://doi.org/10.1037/0022-0663.93.1.55 .
Chen, I. Y. L., Chen, N.-S., & Kinshuk. (2009). International forum of Educational Technology & Society Examining the factors influencing participants’ knowledge sharing behavior in virtual learning communities published by : International forum of Educational Technology & Society Examining the factor. Educational Technology & Society, 12 (1), 134–148.
Chickering, A. W., & Gamson, Z. F. (1987). Seven principles for good practise in undergraduate education. AAHE bulletin, 3 , 7.
Coelho, J., & Duarte, C. (2016). A literature survey on older adults' use of social network services and social applications. Computers in Human Behavior, 58 , 187–205.
Connell, J. P., Spencer, M. B., & Aber, J. L. (1994). Educational risk and resilience in African-American youth: Context, self, action, and outcomes in school. Child Development, 65 (2), 493–506.
Daniel, E. A., Isaac, E. N., & Janet, A. K. (2017). Influence of Facebook usage on employee productivity: A case of university of cape coast staff. African Journal of Business Management, 11 (6), 110–116. https://doi.org/10.5897/AJBM2017.8265 .
DeBell, M., & Chapman, C. (2006). Computer and internet use by students in 2003. Statistical analysis report. NCES 2006-065. National Center for education statistics.
Dziuban, C., & Walker, J. D. (2012). ECAR Study of Undergraduate Students and Information Technology, 2012 (Research Report) . Louisville: EDUCAUSE Centre for Applied Research.
Eid, M. I. M., & Al-Jabri, I. M. (2016). Social networking, knowledge sharing, and student learning: The case of university students. Computers and Education, 99 , 14–27. https://doi.org/10.1016/j.compedu.2016.04.007 .
Elkaseh, A. M., Wong, K. W., & Fung, C. C. (2016). Perceived ease of use and perceived usefulness of social media for e-learning in Libyan higher education: A structural equation modeling analysis. International Journal of Information and Education Technology, 6 (3), 192.
Eow, Y. L., Ali, W. Z. b. W., Mahmud, R. b., & Baki, R. (2009). Form one students’ engagement with computer games and its effect on their academic achievement in a Malaysian secondary school. Computers and Education, 53 (4), 1082–1091. https://doi.org/10.1016/j.compedu.2009.05.013 .
Evans, C. (2014). Twitter for teaching: Can social media be used to enhance the process of learning? British Journal of Educational Wiley Online Library, 45 (5), 902–915. https://doi.org/10.1111/bjet.12099 .
Fan, W., & Williams, C. M. (2010). The effects of parental involvement on students’ academic self-efficacy, engagement and intrinsic motivation. Educational Psychology, 30 (1), 53–74. https://doi.org/10.1080/01443410903353302 .
Field, A. (2011). Discovering statistics using SPSS: (and sex and drugs and rock'n'roll) (Vol. 497). London: Sage.
Field, A. (2013). Factor analysis using SPSS. Scientific Research and Essays, 22 (June), 1–26. https://doi.org/10.1016/B978-0-444-52272-6.00519-5 .
Fisher, M., & Baird, D. E. (2006). Making mLearning work: Utilizing mobile technology for active exploration, collaboration, assessment, and reflection in higher education. Journal of Educational Technology Systems, 35 (1), 3–30.
Gikas, J., & Grant, M. M. (2013). Mobile computing devices in higher education: Student perspectives on learning with cellphones, smartphones & social media. Internet and Higher Education Mobile, 19 , 18–26. https://doi.org/10.1016/j.iheduc.2013.06.002 .
Greenhow, C. (2011a). Online social networks and learning. On the horizon, 19 (1), 4–12.
Greenhow, C. (2011b). Youth, learning, and social media. Journal of Educational Computing Research, 45 (2), 139–146. https://doi.org/10.2190/EC.45.2.a .
Hair Anderson, R. E., Tatham, R. L., & Black, W. C. (1992). Multivariate data analysis. International Journal of Pharmaceutics . https://doi.org/10.1016/j.ijpharm.2011.02.019 .
Hair Jr., J. F., Sarstedt, M., Matthews, L. M., & Ringle, C. M. (2016). Identifying and treating unobserved heterogeneity with FIMIX-PLS: part I–method. European Business Review.
Harrington, D. (2009). Confirmatory factor analysis . Oxford university press.
Haryono, S., & Wardoyo, P. (2012). Structural Equation Modeling (Vol. 331).
Henseler, J., & Sarstedt, M. (2013). Goodness-of-fit indices for partial least squares path modeling. Computational Statistics, 28 (2), 565–580.
Jackson, C. (2011). Your students love social media… and so can you. Teaching Tolerance, 39 , 38–41.
Junco, R., Heiberger, G., & Loken, E. (2011). The effect of twitter on college student engagement and grades. Journal of Computer Assisted Learning, 27 (2), 119–132.
Kabilan, M. K., Ahmad, N., & Abidin, M. J. Z. (2010). Facebook: An online environment for learning of English in institutions of higher education? The Internet and Higher Education, 13 (4), 179–187.
Kaplan, A. M., & Haenlein, M. (2010). Users of the world, unite! The challenges and opportunities of social media. Business Horizons, 53 (1), 59–68.
Kock, N. (2011). Using WarpPLS in e-collaboration studies: Mediating effects, control and second order variables, and algorithm choices. International Journal of e-Collaboration (IJeC), 7 (3), 1–13.
Kuh, G. D. (2007). What student engagement data tell us about college readiness. Peer Review, 9 (1), 4–8.
Kukulska-Hulme, A., & Shield, L. (2008). An overview of mobile assisted language learning: From content delivery to supported collaboration and interaction. ReCALL, 20 (3), 271–289.
Lee, S.-Y. (2007). Structural equation modeling: A Bayesian approach (Wiley series in probability and statistics). Ecotoxicology and Environmental Safety, 73 . https://doi.org/10.1016/j.ecoenv.2009.09.012 .
Leece, R. (2011). Engaging students through social media. Journal of the Australian and New Zealand Student Services Association, 38 , 10–14 Retrieved from https://www.researchgate.net/profile/Anthony_Jorm/publication/235003484_Introduction_to_guidelines_for_tertiary_education_institutions_to_assist_them_in_supporting_students_with_mental_health_problems/links/0c96052ba5314e1202000000.pdf#page=67 .
Lenhart, A., Arafeh, S., & Smith, A. (2008). Writing, technology and teens . Pew Internet & American Life Project.
Lenhart, A., Madden, M., & Hitlin, P. (2005). Teens and technology (p. 2008). Washington, DC: Pew Charitable Trusts Retrieved September 29.
Liccardi, I., Ounnas, A., Pau, R., Massey, E., Kinnunen, P., Lewthwaite, S., …, Sarkar, C. (2007). The role of social networks in students’ learning experiences. In ACM Sigcse Bulletin (39, 4, 224–237).
Ma, W. W. K., & Yuen, A. H. K. (2011). Understanding online knowledge sharing: An interpersonal relationship perspective. Computers & Education, 56 (1), 210–219.
Madden, M., & Zickuhr, K. (2011). 65% of online adults use social networking sites. Pew Internet & American Life Project, 1 , 14.
Meyer, K. A. (2010). A comparison of web 2.0 tools in a doctoral course. The Internet and Higher Education, 13 (4), 226–232.
Mirela Mabić, D. G. (2014). Facebook as a learning tool. Igarss, 2014 (1), 1–5. https://doi.org/10.1007/s13398-014-0173-7.2 .
Mooi, E., & Sarstedt, M. (2011). A concise guide to market research: The process, data, and methods using IBM SPSS statistics . Springeringer. https://doi.org/10.1007/978-3-642-12541-6 .
Moqbel, M., Nevo, S., & Kock, N. (2013). Organizational members’ use of social networking sites and job performance. Information Technology & People, 26 (3), 240–264. https://doi.org/10.1108/ITP-10-2012-0110 .
Moran, M., Seaman, J., & Tinti-Kane, H. (2011). Teaching, learning, and sharing: How Today’s higher education faculty use social media (pp. 1–16). Babson survey research group, (April. https://doi.org/10.1016/j.chb.2013.06.015 .
Nasir, J. A., & Khan, N. A. (2018). Faculty member usage of social media and mobile devices in higher education institution. International Journal of Advance and Innovative Research, 6 (1), 17–25.
Nasir, J. A., Khatoon, A., & Bharadwaj, S. (2018). Social media users in India: A futuristic approach. International Journal of Research and Analytical Reviews, 5 (4), 762–765 Retrieved from http://ijrar.com/ .
Nihalani, P. K., & Mayrath, M. C. (2010). Statistics I. Findings from using an iPhone app in a higher education course. In White Paper .
Norusis, M. (2011). IBM SPSS statistics 20 brief guide (pp. 1–170). IBM Corporation Retrieved from http://www.ibm.com/support .
Novak, E., Razzouk, R., & Johnson, T. E. (2012). The educational use of social annotation tools in higher education: A literature review. The Internet and Higher Education, 15 (1), 39–49.
Nunnally, J. C., & Bernstein, I. H. (1994). Psychological theory .
Pineda-Báez, C., José-Javier, B. A., Rubiano-Bello, Á., Pava-García, N., Suárez-García, R., & Cruz-Becerra, F. (2014). Student engagement and academic performance in the Colombian University context. RELIEVE-Revista Electrónica de Investigación y Evaluación Educativa, 20 (2), 1–19.
Raykov, T., & Marcoulides, G. A. (2000). A First Course in Structural Equation Modeling .
Redecker, C., Ala-Mutka, K., & Punie, Y. (2010). Learning 2.0-the impact of social media on learning in Europe. Policy brief. JRC scientific and technical report. EUR JRC56958 EN, Available from http://bit.ly/cljlpq . Accessed 6 Feb 2011.
Reuben, B. R. (2008). The use of social Media in Higher Education for marketing and communications : A guide for professionals in higher education (Vol. 5) Retrieved from httpdoteduguru comwpcontentuploads200808socialmediainhighereducation pdf)). https://doi.org/10.1108/S2044-9968(2012)0000005018 .
Book Google Scholar
Reyes, M. R., Brackett, M. A., Rivers, S. E., White, M., & Salovey, P. (2012). Classroom emotional climate, student engagement, and academic achievement. Journal of Educational Psychology, 104 (3), 700–712. https://doi.org/10.1037/a0027268 .
Richardson, J., & Lenarcic, J. (2008). Text Messaging as a Catalyst for Mobile Student Administration: The “Trigger” Experience. International Journal of Emerging Technologies & Society, 6 (2), 140–155.
Roblyer, M. D., McDaniel, M., Webb, M., Herman, J., & Witty, J. V. (2010). Findings on Facebook in higher education: A comparison of college faculty and student uses and perceptions of social networking sites. The Internet and Higher Education, 13 (3), 134–140.
Rock, M. L., & Thead, B. K. (2007). The effects of fading a strategic self-monitoring intervention on students’ academic engagement, accuracy, and productivity. Journal of Behavioral Education, 16 (4), 389–412. https://doi.org/10.1007/s10864-007-9049-7 .
Rodriguez, J. E. (2011). Social media use in higher education : Key areas to consider for educators. MERLOT Journal of Online Learning and Teaching, 7 (4), 539–550 https://doi.org/ISSN1558-9528 .
Rutherford, C. (2010). Using online social media to support Preservice student engagement. MERLOT Journal of Online Learning and Teaching, 6 (4), 703–711 Retrieved from http://jolt.merlot.org/vol6no4/rutherford_1210.pdf .
Schumacker, R. E., & Lomax, R. G. (2010). A Beginner’s Guide to structural equation modeling (3rd ed.). New York: Taylor & Francis Group.
Selwyn, N. (2012). Making sense of young people, education and digital technology: The role of sociological theory. Oxford Review of Education, 38 (1), 81–96.
Shih, Y. E. (2007). Setting the new standard with mobile computing in online learning. The International Review of Research in Open and Distributed Learning, 8 (2), 1–16.
Skinner, E. A., & Belmont, M. J. (1993). Motivation in the classroom: Reciprocal effects of teacher behavior and student engagement across the school year. Journal of educational psychology, 85 (4), 571.
Tabachnick, B. G., Fidell, L. S., & Ullman, J. B. (2007). Using multivariate statistics (Vol. 5). Boston: Pearson.
Voorn, R. J., & Kommers, P. A. (2013). Social media and higher education: Introversion and collaborative learning from the student’s perspective. International Journal of Social Media and Interactive Learning Environments, 1 (1), 59–73.
Wankel, C. (2009). Management education using social media. Organization Management Journal, 6 (4), 251–262.
Williams, M. D., Rana, N. P., & Dwivedi, Y. K. (2015). The unified theory of acceptance and use of technology (UTAUT): a literature review. Journal of Enterprise Information Management, 28 (3), 443–488.
Zhu, C. (2012). Student satisfaction, performance, and knowledge construction in online collaborative learning. Journal of Educational Technology & Society, 15 (1), 127–136.
Download references
Acknowledgements
We want to express our special gratitude to the Almighty who has blessed us with such hidden talent to give the shape of this research paper.
The authors of this manuscript, solemnly declared that no funding agency was supported to execute this research project.
Author information
Authors and affiliations.
Department of Commerce, Aligarh Muslim University, Aligarh, 202002, India
Jamal Abdul Nasir Ansari & Nawab Ali Khan
You can also search for this author in PubMed Google Scholar
Contributions
Jamal Abdul Nasir Ansari: The first author of this manuscript has performed all sorts of necessary works like the collection of data from respondents, administration of the questionnaire. Collection of information from the respondents was quite challenging. The author faced a lot of difficulties while collecting data. The main contribution of the author in this manuscript is that the entire work, like data analysis and its interpretation performed by him. Additionally, the author has tried to explore and usefulness of social media and its applicability in transferring the course contents. Nawab Ali Khan: The second author of this manuscript has checked all types of grammatical issues, and necessary corrections wherever required. The author(s) read and approved the final manuscript.
Corresponding author
Correspondence to Jamal Abdul Nasir Ansari .
Ethics declarations
Competing interests.
The authors declare that they have no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License ( http://creativecommons.org/licenses/by/4.0/ ), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
Reprints and permissions
About this article
Cite this article.
Ansari, J.A.N., Khan, N.A. Exploring the role of social media in collaborative learning the new domain of learning. Smart Learn. Environ. 7 , 9 (2020). https://doi.org/10.1186/s40561-020-00118-7
Download citation
Received : 27 November 2019
Accepted : 18 February 2020
Published : 16 March 2020
DOI : https://doi.org/10.1186/s40561-020-00118-7
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Social media
- Higher education
- Faculty members

IMAGES
VIDEO
COMMENTS
Social networking is a global phenomenon that. has revolution ized how people interact with each other. It. affects nearly every aspect of our life: education, communication, employment, politics ...
Social media are responsible for aggravating mental health problems. This systematic study summarizes the effects of social network usage on mental health. Fifty papers were shortlisted from google scholar databases, and after the application of various inclusion and exclusion criteria, 16 papers were chosen and all papers were evaluated for ...
These issues, however, do not mean that past research cannot be conceptually integrated. Social network sites appeal to their users because humans are social creatures who require connection with others to thrive (Baumeister & Leary, 1995; Leary & Baumeister, 2000), and these sites help people meet this basic need. However, the same social ...
Social media platforms carry a unique ability to connect users, leading to increased emotional well-being. Social connectivity reaps an array of emotions in the form of happiness and pleasure. Among all the social media platforms, Facebook is a well-known communication medium and has become an everyday fabric for society.
These findings support those of Davey et al. (2018), who evidenced that phubbing has a significant influence on adolescents and social health students in India. The findings showed a significant and positive effect of social media use on psychological well-being both through bridging and bonding social capital.
The research papers reviewed in this study exhibit diversity in studying authenticity of reviews for travel sites, social bookmarking and review sites, movie ratings, car manufacturing, and social media check-ins. Studies concur that there has been an exponential increase in the number of fake reviews, which is severely damaging the credibility ...
Social media usage has been associated with anxiety, loneliness, and depression (Dhir et al., ... Given this research gap, this paper's main objective is to shed light on the effect of social media use on psychological well-being. As explained in detail in the next section, this paper explores the mediating effect of bonding and bridging social ...
The remainder of the paper is structured as follows. First, we introduce the background of the study, namely, the role of social media and users' engagement. ... and media sharing (Dolan, Seo, & Kemper, 2019; Zeng & Gerritsen, 2014). Although tourism research in social media context is still in the early stages, scholars (e.g., Luo & Zhong ...
Papers published prior to May 2020 relevant to SMU and SA and/or LO were reviewed. Results. ... With the birth of social media, research naturally transitioned from a focus on more general Internet use to closer look at social uses of the Internet via social media, since social media platforms were inherently created and are used for social ...
The spread of social media platforms enhanced academic and professional debate on social media engagement that attempted to better understand its theoretical foundations and measurements. This paper aims to systematically contribute to this academic debate by analysing, discussing, and synthesising social media engagement literature in the perspective of social media metrics. Adopting a ...
Introduction. The term "social media" (SM) was first used in 1994 on a Tokyo online media environment, called Matisse. 1 It was in these early days of the commercial Internet that the first SM platforms were developed and launched. Over time, both the number of SM platforms and the number of active SM users have increased significantly, making it one of the most important applications of ...
Introduction. The past years have witnessed a staggering increase in empirical studies into the effects of social media use (SMU) on adolescents' mental health (e.g. [1∗∗, 2∗, 3]), defined as the absence of mental illness and the presence of well-being [4].This rapid increase may be due to at least two reasons.
Social media. The term 'social media' refers to the various internet-based networks that enable users to interact with others, verbally and visually (Carr & Hayes, Citation 2015).According to the Pew Research Centre (Citation 2015), at least 92% of teenagers are active on social media.Lenhart, Smith, Anderson, Duggan, and Perrin (Citation 2015) identified the 13-17 age group as ...
The remainder of this SLR is organized as can be seen in Fig. 1. Section 2 discusses some related works and motivation. The research questions, the details of the selection process, and the research methodology are documented in Section 3.Following, Section 4 provides a classification and a detailed study of the selected papers and demonstrates their main ideas, advantages, disadvantages ...
Kaplan and Haenlein (2010) defined social media as "… a group of Internet-based applications that build on the ideological and technological foundations of Web 2.0, and that allow the creation and exchange of User Generated Content" (p. 61). The emergence of social media technologies has been embraced by a growing number of users who post text messages, pictures, and videos online ...
The principle objective of this paper is to give knowledge into the social network's security and protection. It introduces the reader to all the possible dimensions of online social networks and issues related to them. ... As phishing attacks are becoming more and more pervasive in online social networking sites, the research community has ...
Social network-based applications like Facebook, Twitter, and Instagram have been used by people of all age groups and backgrounds for the last few years. It is a rich platform for sharing knowledge amongst users online. This information is shared as feelings, opinions, interests, events, or comments in large volumes and varied forms of data. Many multidisciplinary researchers have conducted ...
1. Introduction. Cyberbullying is an emerging societal issue in the digital era [1, 2].The Cyberbullying Research Centre [3] conducted a nationwide survey of 5700 adolescents in the US and found that 33.8 % of the respondents had been cyberbullied and 11.5 % had cyberbullied others.While cyberbullying occurs in different online channels and platforms, social networking sites (SNSs) are fertile ...
This study is an attempt to examine the application and usefulness of social media and mobile devices in transferring the resources and interaction with academicians in higher education institutions across the boundary wall, a hitherto unexplained area of research. This empirical study is based on the survey of 360 students of a university in eastern India, cognising students' perception on ...
Congruent with the growth of social media use, there are also increasing worries that social media might lead to social anxiety in users (Jelenchick et al., 2013).Social anxiety is one's state of avoiding social interactions and appearing inhibited in such interactions with other people (Schlenker & Leary, 1982).Scholars indicated that social anxiety could arise from managing a large network ...
An International Journal of Social Network Analysis Social Networks is an interdisciplinary and international quarterly. It provides a common forum for representatives of anthropology, sociology, history, social psychology, political science, human geography, biology, economics, communications science and other disciplines who share an interest in the study of the empirical structure of social ...