Cyber Security Threats and Vulnerabilities: A Systematic Mapping Study
- Research Article - Computer Engineering and Computer Science
- Published: 06 January 2020
- Volume 45 , pages 3171–3189, ( 2020 )

Cite this article

- Mamoona Humayun 1 ,
- Mahmood Niazi 2 ,
- NZ Jhanjhi ORCID: orcid.org/0000-0001-8116-4733 3 ,
- Mohammad Alshayeb 2 &
- Sajjad Mahmood 2
15k Accesses
131 Citations
Explore all metrics
There has been a tremendous increase in research in the area of cyber security to support cyber applications and to avoid key security threats faced by these applications. The goal of this study is to identify and analyze the common cyber security vulnerabilities. To achieve this goal, a systematic mapping study was conducted, and in total, 78 primary studies were identified and analyzed. After a detailed analysis of the selected studies, we identified the important security vulnerabilities and their frequency of occurrence. Data were also synthesized and analyzed to present the venue of publication, country of publication, key targeted infrastructures and applications. The results show that the security approaches mentioned so far only target security in general, and the solutions provided in these studies need more empirical validation and real implementation. In addition, our results show that most of the selected studies in this review targeted only a few common security vulnerabilities such as phishing, denial-of-service and malware. However, there is a need, in future research, to identify the key cyber security vulnerabilities, targeted/victimized applications, mitigation techniques and infrastructures, so that researchers and practitioners could get a better insight into it.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others

Cyber risk and cybersecurity: a systematic review of data availability

AI-Driven Cybersecurity: An Overview, Security Intelligence Modeling and Research Directions
Artificial intelligence (AI) cybersecurity dimensions: a comprehensive framework for understanding adversarial and offensive AI
Lun, Y.Z.; et al.: Cyber-physical systems security: a systematic mapping study. arXiv:1605.09641 (2016)
Razzaq, A.; et al.: Cyber security: threats, reasons, challenges, methodologies and state of the art solutions for industrial applications. In: 2013 IEEE Eleventh International Symposium on Autonomous Decentralized Systems (ISADS). IEEE (2013)
Von Solms, R.; Van Niekerk, J.: From information security to cyber security. Comput. Secur. 38 , 97–102 (2013)
Article Google Scholar
Benson, V.; McAlaney, J.; Frumkin, L.A.: Emerging threats for the human element and countermeasures in current cyber security landscape. Psychological and Behavioral Examinations in Cyber Security, pp. 266–271. IGI Global, Hershey (2018)
Chapter Google Scholar
Bada, M.; Sasse, A.M.; Nurse, J.R.: Cyber security awareness campaigns: why do they fail to change behaviour? arXiv:1901.02672 (2019)
Floyd, D.H.; Shelton, J.W.; Bush, J.E.: Systems and methods for detecting a security breach in an aircraft network. Google Patents (2018)
Taha, A.F.; et al.: Risk mitigation for dynamic state estimation against cyber attacks and unknown inputs. IEEE Trans. Smart Grid 9 (2), 886–899 (2018)
Valeriano, B.; Maness, R.C.: International relations theory and cyber security. In: Brown, C., Eckersley, R. (eds.) The Oxford Handbook of International Political Theory, p. 259. Oxford University Press, Oxford (2018)
Google Scholar
von Solms, B.; von Solms, R.: Cybersecurity and information security—what goes where? Inf. Comput. Secur. 26 (1), 2–9 (2018)
Ron, M.: Situational status of global cybersecurity and cyber defense according to global indicators. Adaptation of a model for ecuador. In: Developments and Advances in Defense and Security: Proceedings of the Multidisciplinary International Conference of Research Applied to Defense and Security (MICRADS 2018). Springer (2018)
Al Mazari, A.; et al.: Cyber terrorism taxonomies: definition, targets, patterns, risk factors, and mitigation strategies. Cyber Security and Threats: Concepts, Methodologies, Tools, and Applications, pp. 608–621. IGI Global, Hershey (2018)
Hansen, L.; Nissenbaum, H.: Digital disaster, cyber security, and the Copenhagen School. Int. Stud. Q. 53 (4), 1155–1175 (2009)
Kuehl, D.T.: From cyberspace to cyberpower: Defining the problem. Cyberpower and National Security, vol. 30. National Defense University Press, Washington, D.C (2009)
Benedickt, M.: Cyberspace: First Steps. MIT Press, Cambridge (1991)
Gunkel, D.J.: Hacking Cyberspace. Routledge, Abingdon (2018)
Book Google Scholar
Abomhara, M.; Køien, G.M.: Cyber security and the internet of things: vulnerabilities, threats, intruders and attacks. J. Cyber Secur. 4 (1), 65–88 (2015)
Mittal, S.; et al.: Cybertwitter: using twitter to generate alerts for cybersecurity threats and vulnerabilities. In: Proceedings of the 2016 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining. IEEE Press (2016)
Johnson, C.; et al.: Guide to cyber threat information sharing. NIST Spec. Publ. 800 , 150 (2016)
Rid, T.; Buchanan, B.: Attributing cyber attacks. J. Strateg. Stud. 38 (1–2), 4–37 (2015)
Banks, W.C.: Cyber espionage and electronic surveillance: beyond the media coverage. Emory L. J. 66 , 513 (2016)
Zhang, H.; et al.: Optimal denial-of-service attack scheduling with energy constraint. IEEE Trans. Autom. Control 60 (11), 3023–3028 (2015)
Article MathSciNet Google Scholar
Kustarz, C.: et al.: System and method for denial of service attack mitigation using cloud services. Google Patents (2016)
Niemelä, J.; Hyppönen, M.; Kangas, S.: Malware protection. Google Patents (2016)
Choo, K.-K.R.: The cyber threat landscape: challenges and future research directions. Comput. Secur. 30 (8), 719–731 (2011)
Parmar, B.: Protecting against spear-phishing. Comput. Fraud Secur. 2012 (1), 8–11 (2012)
Dodge Jr., R.C.; Carver, C.; Ferguson, A.J.: Phishing for user security awareness. Comput. Secur. 26 (1), 73–80 (2007)
Sharma, P.; Johari, R.; Sarma, S.: Integrated approach to prevent SQL injection attack and reflected cross site scripting attack. Int. J. Syst. Assur. Eng. Manag. 3 (4), 343–351 (2012)
Choraś, M.; et al.: Correlation approach for SQL injection attacks detection. In: International Joint Conference CISIS’12-ICEUTE´12-SOCO´12 Special Sessions. Springer (2013)
Brar, H.S.; Kumar, G.: Cybercrimes: a proposed taxonomy and challenges. J. Comput. Netw. Commun. 2018 , Article ID 1798659 (2018)
Gill, R.S.; Smith, J.; Looi, M.H.; Clark, A.J.: Passive techniques for detecting session hijacking attacks in IEEE 802.11 wireless networks. In: Clark, A.J., Kerr, K., Mohay, G.M. (eds.) AusCERT Asia Pacific Information Technology Security Conference: Refereed R&D Stream, 22–26 May 2005, Gold Coast, Australia (2005)
Wassermann, G.; Su, Z.: Static detection of cross-site scripting vulnerabilities. In: Proceedings of the 30th International Conference on Software Engineering. ACM (2008)
Kieyzun, A.; et al.: Automatic creation of SQL injection and cross-site scripting attacks. In: Proceedings of the 31st International Conference on Software Engineering. IEEE Computer Society (2009)
Nguyen, P.H.; Ali, S.; Yue, T.: Model-based security engineering for cyber-physical systems: a systematic mapping study. Inf. Softw. Technol. 83 , 116–135 (2017)
Hydara, I.; et al.: Current state of research on cross-site scripting (XSS)—a systematic literature review. Inf. Softw. Technol. 58 , 170–186 (2015)
Muccini, H.; Sharaf, M.; Weyns, D.:. Self-adaptation for cyber-physical systems: a systematic literature review. In: Proceedings of the 11th International Symposium on Software Engineering for Adaptive and Self-managing Systems. ACM (2016)
Mishna, F.; et al.: Interventions to prevent and reduce cyber abuse of youth: a systematic review. Res. Soc. Work Pract. 21 (1), 5–14 (2011)
Lewis, G.; Lago, P.: Architectural tactics for cyber-foraging: results of a systematic literature review. J. Syst. Softw. 107 , 158–186 (2015)
Rahim, N.H.A.; et al.: A systematic review of approaches to assessing cybersecurity awareness. Kybernetes 44 (4), 606–622 (2015)
Enoch, S.Y.; et al.: A systematic evaluation of cybersecurity metrics for dynamic networks. Comput. Netw. 144 , 216–229 (2018)
Ramaki, A.A.; Rasoolzadegan, A.; Bafghi, A.G.: A systematic mapping study on intrusion alert analysis in intrusion detection systems. ACM Comput. Surv. (CSUR) 51 (3), 55 (2018)
Chockalingam, S.; et al.: Bayesian network models in cyber security: a systematic review. In: Nordic Conference on Secure IT Systems. Springer (2017)
Alguliyev, R.; Imamverdiyev, Y.; Sukhostat, L.: Cyber-physical systems and their security issues. Comput. Ind. 100 , 212–223 (2018)
Franke, U.; Brynielsson, J.: Cyber situational awareness—a systematic review of the literature. Comput. Secur. 46 , 18–31 (2014)
Budgen, D.; Brereton, P.: Performing systematic literature reviews in software engineering. In: Proceedings of the 28th International Conference on Software Engineering. ACM (2006)
Kitchenham, B.A.; Budgen, D.; Brereton, O.P.: The value of mapping studies-A participant-observer case study. In: EASE (2010)
Petersen, K.; Vakkalanka, S.; Kuzniarz, L.: Guidelines for conducting systematic mapping studies in software engineering: an update. Inf. Softw. Technol. 64 , 1–18 (2015)
Niazi, M.: Do systematic literature reviews outperform informal literature reviews in the software engineering domain? An initial case study. Arab. J. Sci. Eng. 40 (3), 845–855 (2015)
Chong, R.: Quick reference guide to endnote (2018)
Beecham, S.; et al.: Using an expert panel to validate a requirements process improvement model. J. Syst. Softw. 76 (3), 251–275 (2005)
Mohammed, N.M.; et al.: Exploring software security approaches in software development lifecycle: a systematic mapping study. Comput. Stand. Interfaces 50 , 107–115 (2017)
Mufti, Y.; et al.: A readiness model for security requirements engineering. IEEE Access 6 , 28611–28631 (2018)
Download references
Acknowledgements
The authors would like to acknowledge the support provided by the Deanship of Scientific Research via the project number IN161024 at King Fahd University of Petroleum and Minerals, Saudi Arabia. In addition, we are grateful to the participants who evaluated the proposed model and recommended improvements.
Author information
Authors and affiliations.
Department of Information systems, College of Computer and Information Sciences, Jouf University, Al-Jouf, Saudi Arabia
Mamoona Humayun
Information and Computer Science Department, King Fahd University of Petroleum and Minerals (KFUPM), Dhahran, Saudi Arabia
Mahmood Niazi, Mohammad Alshayeb & Sajjad Mahmood
SoCIT, Taylor’s University, Subang Jaya, Malaysia
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to NZ Jhanjhi .
Appendix A: Data Extraction Form
Appendix b: finally selected papers.
Khandpur, Rupinder Paul, et al. “Crowdsourcing cybersecurity: Cyber attack detection using social media.” Proceedings of the 2017 ACM on Conference on Information and Knowledge Management. ACM, 2017.
Li, Zhen, Deqing Zou, Shouhuai Xu, Hai Jin, Hanchao Qi, and Jie Hu. “VulPecker: an automated vulnerability detection system based on code similarity analysis.” In Proceedings of the 32nd Annual Conference on Computer Security Applications , pp. 201–213. ACM, 2016.
Cheng, Maggie, Mariesa Crow, and Robert F. Erbacher. “Vulnerability analysis of a smart grid with monitoring and control system.” Proceedings of the Eighth Annual Cyber Security and Information Intelligence Research Workshop . ACM, 2013.
Zanero, Stefano. “Ulisse, a network intrusion detection system.” In Proceedings of the 4th annual workshop on Cyber security and information intelligence research: developing strategies to meet the cyber security and information intelligence challenges ahead , p. 20. ACM, 2008.
Werner, Gordon, Shanchieh Yang, and Katie McConky. “Time series forecasting of cyber attack intensity.” In Proceedings of the 12th Annual Conference on cyber and information security research , p. 18. ACM, 2017.
Masi, Denise, Martin J. Fischer, John F. Shortle, and Chun-Hung Chen. “Simulating network cyber attacks using splitting techniques. ACM” In Proceedings of the Winter Simulation Conference , pp. 3217–3228. Winter Simulation Conference, 2011.
Okutan, Ahmet, Shanchieh Jay Yang, and Katie McConky. “Predicting cyber attacks with bayesian networks using unconventional signals.” In Proceedings of the 12th Annual Conference on Cyber and Information Security Research , p. 13. ACM, 2017.
Farraj, Abdallah, Eman Hammad, and Deepa Kundur. “Impact of Cyber Attacks on Data Integrity in Transient Stability Control.” In Proceedings of the 2nd Workshop on Cyber - Physical Security and Resilience in Smart Grids , pp. 29–34. ACM, 2017.
Kuhl, Michael E., Jason Kistner, Kevin Costantini, and Moises Sudit. “Cyber attack modeling and simulation for network security analysis.” In Proceedings of the 39th Conference on Winter Simulation: 40 years! The best is yet to come , pp. 1180–1188. ACM Press, 2007.
Gudo, Munyaradzi, and Keshnee Padayachee. “SpotMal: A hybrid malware detection framework with privacy protection for BYOD.” In Proceedings of the 2015 Annual Research Conference on South African Institute of Computer Scientists and Information Technologists , p. 18. ACM, 2015.
Kim, Ikkyun, Daewon Kim, Byunggoo Kim, Yangseo Choi, Seongyong Yoon, Jintae Oh, and Jongsoo Jang. “A case study of unknown attack detection against Zero-day worm in the honeynet environment.” In 2009 11th International Conference on Advanced Communication Technology , vol. 3, pp. 1715–1720. IEEE, 2009.
Ahmadloo, Fatemeh, and Farzad Rajaei Salmasi. “A cyber-attack on communication link in distributed systems and detection scheme based on H-infinity filtering.” In 2017 IEEE International Conference on Industrial Technology (ICIT) , pp. 698–703. IEEE, 2017.
Aishwarya, R., and S. Malliga. “Intrusion detection system-An efficient way to thwart against Dos/DDos attack in the cloud environment.” In 2014 International Conference on Recent Trends in Information Technology , pp. 1–6. IEEE, 2014.
Al-Dabbagh, Ahmad W., Yuzhe Li, and Tongwen Chen. “An intrusion detection system for cyber attacks in wireless networked control systems.” IEEE Transactions on Circuits and Systems II: Express Briefs 65, no. 8 (2017): 1049–1053.
Alom, Md Zahangir, and Tarek M. Taha. “Network intrusion detection for cyber security on neuromorphic computing system.” In 2017 International Joint Conference on Neural Networks (IJCNN) , pp. 3830–3837. IEEE, 2017.
Aparicio-Navarro, Francisco J., Konstantinos G. Kyriakopoulos, Yu Gong, David J. Parish, and Jonathon A. Chambers. “Using pattern-of-life as contextual information for anomaly-based intrusion detection systems.” IEEE Access 5 (2017): 22177–22193.
Bhadre, Parvati, and Deepali Gothawal. “Detection and blocking of spammers using SPOT detection algorithm.” In 2014 First International Conference on Networks & Soft Computing (ICNSC2014) , pp. 97–101. IEEE, 2014.
Bottazzi, Giovanni, Emiliano Casalicchio, Davide Cingolani, Fabio Marturana, and Marco Piu. “MP-Shield: a framework for phishing detection in mobile devices.” In 2015 IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing , pp. 1977–1983. IEEE, 2015.
Chen, Chia-Mei, Han-Wei Hsiao, Peng-Yu Yang, and Ya-Hui Ou. “Defending malicious attacks in cyber physical systems.” In 2013 IEEE 1st International Conference on Cyber - Physical Systems, Networks, and Applications (CPSNA) , pp. 13–18. IEEE, 2013.
Chen, Chia-Mei, Ya-Hui Ou, and Yu-Chou Tsai. “Web botnet detection based on flow information.” In 2010 International Computer Symposium (ICS2010) , pp. 381–384. IEEE, 2010.
Chonka, Ashley, and Jemal Abawajy. “Detecting and mitigating HX-DoS attacks against cloud web services.” In 2012 15th International Conference on Network - Based Information Systems , pp. 429–434. IEEE, 2012.
Devi, BS Kiruthika, G. Preetha, G. Selvaram, and S. Mercy Shalinie. “An impact analysis: Real time DDoS attack detection and mitigation using machine learning.” In 2014 International Conference on Recent Trends in Information Technology , pp. 1–7. IEEE, 2014.
Eslahi, Meisam, Habibah Hashim, and Nooritawati Md Tahir. “An efficient false alarm reduction approach in HTTP-based botnet detection.” In 2013 IEEE Symposium on Computers & Informatics (ISCI) , pp. 201–205. IEEE, 2013.
Gantsou, Dhavy. “On the use of security analytics for attack detection in vehicular ad hoc networks.” In 2015 International Conference on Cyber Security of Smart Cities, Industrial Control System and Communications (SSIC) , pp. 1–6. IEEE, 2015.
Hesar, Amin Danandeh, and Mahmoud Ahmadian Attari. “Simulating and analysis of cyber attacks on a BLPC network.” In 2014 Smart Grid Conference (SGC) , pp. 1–6. IEEE, 2014.
Hong, Junho, Chen-Ching Liu, and Manimaran Govindarasu. “Integrated anomaly detection for cyber security of the substations.” IEEE Transactions on Smart Grid 5, no. 4 (2014): 1643–1653.
Hu, Xin, Jiyong Jang, Marc Ph Stoecklin, Ting Wang, Douglas L. Schales, Dhilung Kirat, and Josyula R. Rao. “BAYWATCH: robust beaconing detection to identify infected hosts in large-scale enterprise networks.” In 2016 46th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN) , pp. 479–490. IEEE, 2016.
Ichise, Hikaru, Yong Jin, and Katsuyoshi Iida. “Analysis of via-resolver DNS TXT queries and detection possibility of botnet communications.” In 2015 IEEE Pacific Rim Conference on Communications, Computers and Signal Processing (PACRIM) , pp. 216–221. IEEE, 2015.
Indre, Ionut, and Camelia Lemnaru. “Detection and prevention system against cyber attacks and botnet malware for information systems and Internet of Things.” In 2016 IEEE 12th International Conference on Intelligent Computer Communication and Processing (ICCP) , pp. 175–182. IEEE, 2016.
Jakaria, A. H. M., Wei Yang, Bahman Rashidi, Carol Fung, and M. Ashiqur Rahman. “Vfence: A defense against distributed denial of service attacks using network function virtualization.” In 2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC) , vol. 2, pp. 431–436. IEEE, 2016.
Jin, Guang, Fei Zhang, Yuan Li, Honghao Zhang, and Jiangbo Qian. “A Hash-based Path Identification Scheme for DDoS Attacks Defense.” In 2009 Ninth IEEE International Conference on Computer and Information Technology , vol. 2, pp. 219–224. IEEE, 2009.
Jing, Tao, Jun Li, and Rong Xing. “Research on malicious links detection system based on script text analysis.” In 2012 14th International Conference on Advanced Communication Technology (ICACT) , pp. 439–442. IEEE, 2012.
Khan, Mohiuddin Ali, Sateesh Kumar Pradhan, and Huda Fatima. “Applying data mining techniques in cyber crimes.” In 2017 2nd International Conference on Anti - Cyber Crimes (ICACC) , pp. 213–216. IEEE, 2017.
Khan, Muhammad Salman, Ken Ferens, and Witold Kinsner. “A chaotic measure for cognitive machine classification of distributed denial of service attacks.” In 2014 IEEE 13th International Conference on Cognitive Informatics and Cognitive Computing , pp. 100–108. IEEE, 2014.
Kong, Xinling, Yonghong Chen, Hui Tian, Tian Wang, Yiqiao Cai, and Xin Chen. “A novel botnet detection method based on preprocessing data packet by graph structure clustering.” In 2016 International Conference on Cyber - Enabled Distributed Computing and Knowledge Discovery (CyberC) , pp. 42–45. IEEE, 2016.
Misra, Sudip, P. Venkata Krishna, Harshit Agarwal, Antriksh Saxena, and Mohammad S. Obaidat. “A learning automata based solution for preventing distributed denial of service in internet of things.” In 2011 International Conference on Internet of Things and 4th International Conference on Cyber, Physical and Social Computing , pp. 114–122. IEEE, 2011.
Sanchez, Fernando, and Zhenhai Duan. “A sender-centric approach to detecting phishing emails.” In 2012 International Conference on Cyber Security , pp. 32–39. IEEE, 2012.
Shitharth, S., and D. Prince Winston. “A novel IDS technique to detect DDoS and sniffers in smart grid.” In 2016 World Conference on Futuristic Trends in Research and Innovation for Social Welfare (Startup Conclave) , pp. 1–6. IEEE, 2016.
Sun, Jia-Hao, Tzung-Han Jeng, Chien-Chih Chen, Hsiu-Chuan Huang, and Kuo-Sen Chou. “MD-Miner: Behavior-Based Tracking of Network Traffic for Malware-Control Domain Detection.” In 2017 IEEE Third International Conference on Big Data Computing Service and Applications (BigDataService) , pp. 96–105. IEEE, 2017.
Velauthapillai, Thaneswaran, Aaron Harwood, and Shanika Karunasekera. “Global detection of flooding-based DDoS attacks using a cooperative overlay network.” In 2010 Fourth International Conference on Network and System Security , pp. 357–364. IEEE, 2010.
Sun, Cong, Jiao Liu, Xinpeng Xu, and Jianfeng Ma. “A privacy-preserving mutual authentication resisting DoS attacks in VANETs.” IEEE Access 5 (2017): 24012–24022.
Fan, Lejun, Yuanzhuo Wang, Xueqi Cheng, and Shuyuan Jin. “Privacy Theft Malware Detection with Privacy Petri Net.” In 2012 13th International Conference on Parallel and Distributed Computing, Applications and Technologies , pp. 195–200. IEEE, 2012.
Cui, Helei, Yajin Zhou, Cong Wang, Qi Li, and Kui Ren. “Towards Privacy-Preserving Malware Detection Systems for Android.” In 2018 IEEE 24th International Conference on Parallel and Distributed Systems (ICPADS) , pp. 545–552. IEEE, 2018.
Xu, Lei, Chunxiao Jiang, Nengqiang He, Zhu Han, and Abderrahim Benslimane. “Trust-based collaborative privacy management in online social networks.” IEEE Transactions on Information Forensics and Security 14, no. 1 (2018): 48–60.
Shitharth, S., and D. Prince Winston. “A comparative analysis between two countermeasure techniques to detect DDoS with sniffers in a SCADA network.” Procedia Technology 21 (2015): 179–186. ScienceDirect.
Spyridopoulos, Theodoros, G. Karanikas, Theodore Tryfonas, and Georgios Oikonomou. “A game theoretic defence framework against DoS/DDoS cyber attacks.” Computers & Security 38 (2013): 39–50. ScienceDirect.
Shon, Taeshik, and Jongsub Moon. “A hybrid machine learning approach to network anomaly detection.” Information Sciences 177, no. 18 (2007): 3799–3821. ScienceDirect.
Wang, Fei, Hailong Wang, Xiaofeng Wang, and Jinshu Su. “A new multistage approach to detect subtle DDoS attacks.” Mathematical and Computer Modelling 55, no. 1–2 (2012): 198–213. ScienceDirect.
Varshney, Gaurav, Manoj Misra, and Pradeep K. Atrey. “A phish detector using lightweight search features.” Computers & Security 62 (2016): 213–228. ScienceDirect.
Liu, Ting, Yanan Sun, Yang Liu, Yuhong Gui, Yucheng Zhao, Dai Wang, and Chao Shen. “Abnormal traffic-indexed state estimation: A cyber–physical fusion approach for smart grid attack detection.” Future Generation Computer Systems 49 (2015): 94–103. ScienceDirect.
Qiu, Yue, Maode Ma, and Shuo Chen. “An anonymous authentication scheme for multi-domain machine-to-machine communication in cyber-physical systems.” Computer Networks 129 (2017): 306–318. ScienceDirect.
Kumara, Ajay, and C. D. Jaidhar. “Automated multi-level malware detection system based on reconstructed semantic view of executables using machine learning techniques at VMM.” Future Generation Computer Systems 79 (2018): 431–446. ScienceDirect.
Zhao, David, Issa Traore, Bassam Sayed, Wei Lu, Sherif Saad, Ali Ghorbani, and Dan Garant. “Botnet detection based on traffic behavior analysis and flow intervals.” Computers & Security 39 (2013): 2–16. ScienceDirect.
Noor, Muzzamil, Haider Abbas, and Waleed Bin Shahid. “Countering cyber threats for industrial applications: An automated approach for malware evasion detection and analysis.” Journal of Network and Computer Applications 103 (2018): 249–261. ScienceDirect.
Huda, Shamsul, Suruz Miah, Mohammad Mehedi Hassan, Rafiqul Islam, John Yearwood, Majed Alrubaian, and Ahmad Almogren. “Defending unknown attacks on cyber-physical systems by semi-supervised approach and available unlabeled data.” Information Sciences 379 (2017): 211–228. ScienceDirect.
Alajeely, Majeed, Robin Doss, and Vicky Mak-Hau. “Defense against packet collusion attacks in opportunistic networks.” Computers & Security 65 (2017): 269–282. ScienceDirect.
Maciá-Fernández, Gabriel, Rafael A. Rodríguez-Gómez, and Jesús E. Díaz-Verdejo. “Defense techniques for low-rate DoS attacks against application servers.” Computer Networks 54, no. 15 (2010): 2711–2727. ScienceDirect.
Kiss, Istvan, Piroska Haller, and Adela Bereş. “Denial of Service attack Detection in case of Tennessee Eastman challenge process.” Procedia Technology 19 (2015): 835–841. ScienceDirect.
Abbaspour, Alireza, Kang K. Yen, Shirin Noei, and Arman Sargolzaei. “Detection of fault data injection attack on uav using adaptive neural network.” Procedia computer science 95 (2016): 193–200. ScienceDirect.
Stevanovic, Dusan, Natalija Vlajic, and Aijun An. “Detection of malicious and non-malicious website visitors using unsupervised neural network learning.” Applied Soft Computing 13, no. 1 (2013): 698–708. ScienceDirect.
Li, Beibei, Rongxing Lu, Wei Wang, and Kim-Kwang Raymond Choo. “Distributed host-based collaborative detection for false data injection attacks in smart grid cyber-physical system.” Journal of Parallel and Distributed Computing 103 (2017): 32–41. ScienceDirect.
Yu, Wei, Sriram Chellappan, Xun Wang, and Dong Xuan. “Peer-to-peer system-based active worm attacks: Modeling, analysis and defense.” Computer Communications 31, no. 17 (2008): 4005–4017. ScienceDirect.
Abdelhamid, Neda, Aladdin Ayesh, and Fadi Thabtah. “Phishing detection based associative classification data mining.” Expert Systems with Applications 41, no. 13 (2014): 5948–5959. ScienceDirect.
Alazab, Mamoun. “Profiling and classifying the behavior of malicious codes.” Journal of Systems and Software 100 (2015): 91–102. ScienceDirect.
Song, Jungsuk, Hiroki Takakura, Yasuo Okabe, and Koji Nakao. “Toward a more practical unsupervised anomaly detection system.” Information Sciences 231 (2013): 4–14. ScienceDirect.
Saini, Anil, Manoj Singh Gaur, Vijay Laxmi, and Mauro Conti. “Colluding browser extension attack on user privacy and its implication for web browsers.” Computers & Security 63 (2016): 14–28. ScienceDirect.
Choi, Sang‐soo, Jungsuk Song, Seokhun Kim, and Sookyun Kim. “A model of analyzing cyber threats trend and tracing potential attackers based on darknet traffic.” Security and Communication Networks 7, no. 10 (2014): 1612–1621. Wiley.
Rubio‐Hernan, Jose, Luca De Cicco, and Joaquin Garcia‐Alfaro. “Adaptive control‐theoretic detection of integrity attacks against cyber‐physical industrial systems.” Transactions on Emerging Telecommunications Technologies 29, no. 7 (2018): e3209. Wiley.
Zhang, Jian, Phillip Porras, and Johannes Ullrich. “Gaussian process learning for cyber‐attack early warning.” Statistical Analysis and Data Mining: The ASA Data Science Journal 3, no. 1 (2010): 56–68. Wiley.
Fan, Lejun, Yuanzhuo Wang, Xueqi Cheng, Jinming Li, and Shuyuan Jin. “Privacy theft malware multi‐process collaboration analysis.” Security and Communication Networks 8, no. 1 (2015): 51–67. Wiley.
Wu, Yu-Sung, Vinita Apte, Saurabh Bagchi, Sachin Garg, and Navjot Singh. “Intrusion detection in voice over IP environments.” International Journal of Information Security 8, no. 3 (2009): 153–172. Springer.
Deepa, G., P. Santhi Thilagam, Furqan Ahmed Khan, Amit Praseed, Alwyn R. Pais, and Nushafreen Palsetia. “Black-box detection of XQuery injection and parameter tampering vulnerabilities in web applications.” International Journal of Information Security 17, no. 1 (2018): 105–120. Springer.
Gowtham, R., and Ilango Krishnamurthi. “PhishTackle—a web services architecture for antiphishing.” Cluster computing 17, no. 3 (2014): 1051–1068. Springer.
Saha, Sujoy, Subrata Nandi, Rohit Verma, Satadal Sengupta, Kartikeya Singh, Vivek Sinha, and Sajal K. Das. “Design of efficient lightweight strategies to combat DoS attack in delay tolerant network routing.” Wireless Networks 24, no. 1 (2018): 173–194. Springer.
Gupta, Shashank, and B. B. Gupta. “XSS-SAFE: a server-side approach to detect and mitigate cross-site scripting (XSS) attacks in JavaScript code.” Arabian Journal for Science and Engineering 41, no. 3 (2016): 897–920. Springer.
Jain, Ankit Kumar, and Brij B. Gupta. “A novel approach to protect against phishing attacks at client side using auto-updated white-list.” EURASIP Journal on Information Security 2016, no. 1 (2016): 9. Springer.
Ahmad, Farhan Habib, Komal Batool, and Azhar Javed. “Detection of Privacy Threat by Peculiar Feature Extraction in Malwares to Combat Targeted Cyber Attacks.” In Advanced Computer and Communication Engineering Technology , pp. 1237–1247. Springer, Cham, 2016.
Saini, Anil, Manoj Singh Gaur, Vijay Laxmi, Tushar Singhal, and Mauro Conti. “Privacy leakage attacks in browsers by colluding extensions.” In International Conference on Information Systems Security , pp. 257–276. Springer, Cham, 2014.
Rights and permissions
Reprints and permissions
About this article
Humayun, M., Niazi, M., Jhanjhi, N. et al. Cyber Security Threats and Vulnerabilities: A Systematic Mapping Study. Arab J Sci Eng 45 , 3171–3189 (2020). https://doi.org/10.1007/s13369-019-04319-2
Download citation
Received : 09 May 2019
Accepted : 26 December 2019
Published : 06 January 2020
Issue Date : April 2020
DOI : https://doi.org/10.1007/s13369-019-04319-2
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cyber security
- Vulnerabilities
- Find a journal
- Publish with us
- Track your research
Accessibility Links
- Skip to content
- Skip to search IOPscience
- Skip to Journals list
- Accessibility help
- Accessibility Help
Click here to close this panel.
Purpose-led Publishing is a coalition of three not-for-profit publishers in the field of physical sciences: AIP Publishing, the American Physical Society and IOP Publishing.
Together, as publishers that will always put purpose above profit, we have defined a set of industry standards that underpin high-quality, ethical scholarly communications.
We are proudly declaring that science is our only shareholder.
Web Security and Vulnerability: A Literature Review
H Yulianton 1,2 , H L H S Warnars 1 , B Soewito 1 , F L Gaol 1 and E Abdurachman 1
Published under licence by IOP Publishing Ltd Journal of Physics: Conference Series , Volume 1477 , Computer and Mathematics Citation H Yulianton et al 2020 J. Phys.: Conf. Ser. 1477 022028 DOI 10.1088/1742-6596/1477/2/022028
Article metrics
1646 Total downloads
Share this article
Author e-mails.
Author affiliations
1 Computer Science Department, BINUS Graduate Program - Doctor of Computer Science, Bina Nusantara University, Jakarta, Indonesia 11480
2 Faculty of Information Technology, Universitas Stikubank, Semarang, Indonesia 50243
Buy this article in print
The web continues to grow and attacks against the web continue to increase. This paper focuses on the literature review on scanning web vulnerabilities and solutions to mitigate web attacks. Vulnerability scanning methods will be reviewed as well as frameworks for improving web security. This research is the basis for future work that will end with the elaboration of web scanning and security with the aim of proposing better innovations.
Export citation and abstract BibTeX RIS
Content from this work may be used under the terms of the Creative Commons Attribution 3.0 licence . Any further distribution of this work must maintain attribution to the author(s) and the title of the work, journal citation and DOI.
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

Cyber Security -Literature Review

It discusses some of academic articles related to cyber security issue.
Related Papers
Robert Dewar
In the field of cyber security, ill-defined concepts and inconsistently applied terminology are further complicating an already complex issue. This causes difficulties for policy-makers, strategists and academics. Using national cyber security strategies to support current literature, this paper undertakes three tasks with the goal of classifying and defining terms to begin the development of a lexicon of cyber security terminology. The first task is to offer for consideration a definition of “active cyber defence” (ACD). This definition is based upon a number of characteristics identified in current academic and policy literature. ACD is defined here as the proactive detection, analysis and mitigation of network security breaches in real-time combined with the use of aggressive countermeasures deployed outside the victim network. Once defined, ACD is contextualised alongside two further approaches to cyber defence and security. These are fortified and resilient cyber defence, predicated upon defensive perimeters and ensuring continuity of services respectively. This contextualisation is postulated in order to provide more clarity to non-active cyber defence measures than is offered by the commonly used term “passive cyber defence”. Finally, it is shown that these three approaches to cyber defence and security are neither mutually exclusive nor applied independently of one another. Rather they operate in a complementary triptych of policy approaches to achieving cyber security.
Marion Kokel
With the introduction of cybersecurity in its 2010 Strategic concept and its 2011 Policy on Cyber Defence, the North Atlantic Treaty Organisation (NATO) has implicitly introduced this aspect on the international agenda as an essential security issue. Since the creation of the Internet in the late 1960s, cybersecurity gradually sparked people’s interest for concerns regarding the development of cyberspace activities. However, it is only recently that this complex field has been extensively analysed and debated by scholars, policy makers, think tanks and international organisations. The present thesis argues that NATO’s narratives on cybersecurity are representing something more than an abstract buzzword: their content illustrates security practices constitutive of the Alliance’s identity formation. In this regard, it is argued that the transatlantic partnership might be transforming into an enlarged security organisation through its engagement in cybersecurity. To study this possibility, discursive practices of different NATO sources are examined through content analysis. Building on the Copenhagen School’s approach to security, the present study endorses the view that cybersecurity is theorised as a sixth sector of security, which frames particular referent objects, threats, key actors of security and the specific functions performed by these actors. We argue that mapping these different units in NATO’s discourse demonstrates that the Alliance is expanding the perimeter of its security activities. Following a thorough evaluation of the results obtained, the present research highlights that NATO, through its cybersecurity speech act, is remodelling its identity and maturing into a greater collective security organisation without militarising the “fifth battlefield”.
Miftahul Ulum
The objective of this research is to investigate the impact of the Indonesian citizen " s cyber culture on the Indonesian cyber security policy. It also identifies and potentially fills gaps in the Indonesian cyber security policy. In order to achieve this objective, the study commences with a comprehensive review of the research and relevant government documents. A number of in-depth interviews were conducted with seven sources representing a variety of cyber security stakeholders in Indonesia. Using content analysis and the application of Cyber Security Civic Discourse, Three Tenets of Cyber Security, and Copenhagen " s Securitization Theory, this research highlights two important points. Firstly, there are two ways the negative impacts of the Indonesian cyber security culture affect the Indonesian cyber security policy; firstly as the primary source of cyber threats and secondly as the most vulnerable part in the cyber security system. Secondly, all of interviewees believed that cyber culture is the most important element of cyber security policy, however this research finds it has not been addressed optimally within the policy. This study contributes to the existing body of knowledge in two major ways. Firstly, it broadens knowledge about cyber security culture to help address the lack of research on the cyber security issue in developing countries. Secondly, it strengthens the previous finding on the significance of cyber security culture as the main pillar of cyber security policy strategy. Finally, this study provides potential future related study needs.
Eldar Šaljić
Abstract: In modern times, ensuring security in cyberspace is the main task of national security for most states. States have different approaches to cybersecurity from the aspect of national security policies. They can be divided into two categories: those that regard cybersecurity as a civilian task and those that involve their militaries in creating or implementing cybersecurity policies. Those states that have incorporated cyber warfare into their military planning and organization perceive cyberattacks as a threat to their national security, while states that charge their civilian agencies with domestic cybersecurity missions classify cyber intrusions as security risks for only particular sectors. Adopting the framework of securitization theory, this chapter theorizes both civil and military approaches to cybersecurity and threat perceptions and their sources. The theoretical framework is then applied to a study of the cybersecurity policies of Eastern European countries and the Baltic states. Keywords : Cybersecurity, Cyber space, National security
Debora Halbert
Karsten Friis , Erik Reichborn
Chapter 2 in Friis and Ringsmose eds.: Conflict in Cyber Space: Theoretical, Strategic and Legal Perspectives, London: Routledge, 2016.
Stuart Macdonald , Lee Jarvis
This article explores constructions of cyberterrorism within the global news media between 2008 and 2013. It begins by arguing that the preoccupation with questions of definition, threat and response in academic literature on cyberterrorism is problematic, for two reasons. First, because it neglects the constitutivity of representations of cyberterrorism in the news media and beyond; and, second, because it prioritises policy-relevant research. To address this, the article then provides a discursive analysis of original empirical research into 31 news media outlets across the world. Although there is genuine heterogeneity in representations of cyberterrorism therein, we argue that constructions of this threat rely heavily on two strategies. First, appeals to authoritative or expert ‘witnesses’ and their institutional or epistemic credibility. And, second, generic or historical analogies, which help shape understandings of the likelihood and consequences of cyberterrorist attack. These discursive strategies are particularly important, we argue, given the lack of readily available empirical examples of the ‘reality’ of cyberterrorism. This is the original, submitted version of a manuscript subsequently accepted for publication (on 18 December 2015), and now forthcoming in the Taylor & Francis journal Global Society: http://www.tandfonline.com/action/journalInformation?show=aimsScope&journalCode=cgsj20#.VoD6zjY_Wu4.
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
- Open access
- Published: 05 May 2023
A systematic literature review of indicators measuring food security
- Ioannis Manikas 1 ,
- Beshir M. Ali ORCID: orcid.org/0000-0002-5865-8468 1 &
- Balan Sundarakani 1
Agriculture & Food Security volume 12 , Article number: 10 ( 2023 ) Cite this article
21k Accesses
14 Citations
1 Altmetric
Metrics details
Measurement is critical for assessing and monitoring food security. Yet, it is difficult to comprehend which food security dimensions, components, and levels the numerous available indicators reflect. We thus conducted a systematic literature review to analyse the scientific evidence on these indicators to comprehend the food security dimensions and components covered, intended purpose, level of analysis, data requirements, and recent developments and concepts applied in food security measurement. Data analysis of 78 articles shows that the household-level calorie adequacy indicator is the most frequently used (22%) as a sole measure of food security. The dietary diversity-based (44%) and experience-based (40%) indicators also find frequent use. The food utilisation (13%) and stability (18%) dimensions were seldom captured when measuring food security, and only three of the retrieved publications measured food security by considering all the four food security dimensions. The majority of the studies that applied calorie adequacy and dietary diversity-based indicators employed secondary data whereas most of the studies that applied experience-based indicators employed primary data, suggesting the convenience of collecting data for experience-based indicators than dietary-based indicators. We confirm that the estimation of complementary food security indicators consistently over time can help capture the different food security dimensions and components, and experience-based indicators are more suitable for rapid food security assessments. We suggest practitioners to integrate food consumption and anthropometry data in regular household living standard surveys for more comprehensive food security analysis. The results of this study can be used by food security stakeholders such as governments, practitioners and academics for briefs, teaching, as well as policy-related interventions and evaluations.
Introduction
Providing sufficient, affordable, nutritious, and safe food for the growing global population remains a challenge for human society; this task is made further difficult when governments are expected to provide food security without causing climate change, degrading water and land resources, and eroding biodiversity [ 1 ]. As long as food self-sufficiency and citizens’ wellbeing depend on sustainable food security, food security will remain a global priority [ 2 , 3 ]. According to the 1996 World Food Summit definition, food security is achieved ‘when all people, at all times, have physical and economic access to sufficient, safe and nutritious food to meet their dietary needs and food preferences for an active and healthy life’ [ 4 ].
This definition by the Food and Agriculture Organization has laid the foundation for the four food security dimensions [ 5 ]: availability , access , utilisation , and stability . Relatedly, any kind of food security analysis, programme, and monitoring, with respect to predefined targets, requires valid and reliable food security measurement. However, measuring such a non-observable concept as a latent construct has remained challenging because of its complex and evolving nature: it has many dimensions and components [ 6 ], and involves a continuum of situations , invalidating the application of dichotomous/binary measures [ 7 ]. Food security measurement poses two fundamental yet distinct problems [ 8 ]: determining what is being measured and how it is measured . The what question refers to the use of appropriate indicators for the different dimensions (availability, access, utilisation, and stability) and components (quantity, quality, safety, and cultural acceptability/preference), while the how question refers to the methodology applied for computing the indicators (i.e. data, methods, and models).
Scholars have proposed a variety of indicators to measure food security. Over this time, the definition and operational concept of food security has changed as well, and, with it, the type of indicators and methodologies used to gauge it. One such important change is the paradigm shift ‘from the global and the national to the household and the individual, from a food-first perspective to a livelihood perspective, and from objective indicators to subjective perception’ [ 6 ]. Despite the call to harmonize measurements for better coordination and partnerships, to date, there remains no consensus among governments, quasi-legal agencies, or researchers on the indicators and methodologies that should be applied for measuring and monitoring food security at global, national, household, and individual levels [ 9 ]. Instead, an overabundance of indicators makes it difficult to ascertain which indicators reflect which dimensions (availability, access, utilization, or stability), components (quantity, quality, safety, cultural acceptability/preferences), and levels (global, national, regional, household or individual) of food security [ 10 ]. The number of food security dimensions or components assessed also greatly vary in the literature. Indicators that assess only a specific dimension or component oversimplify the outcomes and do not reveal the full extent of food insecurity, for example. Although such highly specific indicators do help conceptualise and reveal food insecurity, they still fail to accurately show trade-offs among the different dimensions, components, and intervention strategies. There is ultimately a possibility of shifting the food insecurity problem from one dimension/component to another.
The practical limitations of existing food security measurements were once again exposed by 2019 coronavirus pandemic (COVID-19), the Scientific Group for the United Nations Food Systems Summit [ 11 ] that ‘the world does not have a singular source of information to provide real-time assessments of people facing acute food insecurity with the geographic scale to cover any country of concern, the ability to update forecasts frequently and consistently in near real-time’. They further stated that current early warning systems lack suitable indicators to monitor the degradation of food systems. Aggravating this problem, these measurement indicators are not standardised, making comparisons among indicators over space and time complicated [ 9 ]. First, some of the indicators are composite indicators measuring two or more food security dimensions, whereas others measure individual dimensions. Second, some of the indicators focus on factors contributing to food security than on food security outcomes. Third, some indicators are quantitative, whereas others are qualitative measures based on individuals’ perceptions. Fourth, the levels of analysis greatly vary as well because some indicators are global and national measures, whereas others are household and individual measures. Fifth, the intended purposes of the indicators range from advocacy tools to monitoring and evaluating progress towards defined policy targets.
Although numerous food security indicators have been developed for use in research, there is no agreement on the single ‘best’ food security indicator among scientists or practitioners for measuring, analysing, and monitoring food security [ 12 , 9 ]. The different international agencies also use their own sets of food security indicators (e.g. World Food Programme: Food Consumption Score (FCS), United States Agency for International Development (USAID): Household Food Insecurity Access Scale (HFIAS); FAO: Prevalence of Undernourishment (POU) and Food Insecurity Experience Scale (FIES); and Economic Intelligence Unit (EIU): Global Food Security Index (GFSI)). An ideal food security indicator should capture all the four food security dimensions at individual level (rather than at national or regional or household levels) to reflect the 1996 World Food Summit definition of food security. However, most of the available indicators are measures of food access at the household level. Footnote 1 In practical use, only a few indicators that ‘satisfactorily capture each requisite dimension of food security and that are relatively easy to collect can be identified and adopted at little detriment to a broader agenda’ [ 9 ], which we attempt herein. In the light of the foregoing discussion, the main objective of this study was to critically review food security indicators and methodologies published in scientific articles using systematic literature review (SLR). The specific objectives were as follows:
To identify and characterize food security indicators with respect to dimensions and components covered, methods and models of measurement, level of analysis, data requirements and sources, intended purpose of application, and strengths and weaknesses;
To review and summarise the scientific articles published since the last decade by the indicators used, intended purpose, level of analysis, study region/country, and data source;
To quantitatively characterize the food security dimensions and components covered in the literature, and to review scientific articles that measured all the four food security dimensions; and
To identify and review recent developments and concepts applied in food security measurement.
Although there exist a few review studies on food security measurement in the literature (e.g. [ 8 , 10 , 13 , 14 , 15 ], the present study is more comprehensive as it covers a wide range of food security indicators, levels of measurement, and analysis of data requirements and sources. Moreover, unlike the existing review studies in the literature, the current study applies the SLR methodology to the analysis of food security indicators and measurement.
Review methodology
We followed a two-stage approach in this review. First, we identified the commonly used food security indicators based on recent (review) articles on food security measurement [ 8 , 9 , 10 , 14 , 15 ]. Using the retrieved information from these articles (and their references), the identified indicators were characterised (in terms of the dimensions and components covered, methods of measurement, level of analysis, intended uses, validity and reliability, and data requirements and sources). Tables 1 , 2 , 3 , 4 present the summary of the characterisation of the identified food security indicators: experience-based indicators (Table 1 ), national-level indicators (Table 2 ), dietary intake, diversity and expenditure-based indicators (Table 3 ), and indicators reflecting coping strategies and anthropometry measures (Table 4 ). This first-stage analysis was used to address the first objective of the study. In the second stage, the SLR was conducted.
Literature searching and screening processes
We applied the SLR methodology to systematically search, filter, and analyse scientific articles on food security measurement. The SLR is a commonly applied and accepted research methodology in the literature [ 39 ]. Although the SLR methodology is widely applied in different disciplines such as the health and life sciences, its application in economics is limited. However, it has recently been applied in agricultural economics (e.g. [ 40 – 43 ]. In this study, we closely followed the six steps of a systematic review process [ 39 ], namely, (a) defining research questions, (b) formulating search strings, (c) filtering studies based on inclusion and exclusion criteria, (d) conducting quality assessment of the filtered studies, (e) collecting data from the studies that passed quality assessment, and (f) analysing the data. The literature screening process that we followed is also in line with the guidelines in the Preferred Reporting Items for Systematic Reviews and Meta-Analyses Statement (PRISMA) [ 44 ].
The bibliographic databases of Scopus and Web of Science (WoS) were used to search scientific articles on food security measurement (i.e. indicators, data, and methods) and help us answer the research question ‘How has food in/security been measured in the literature?’ Two categories of search strings were applied: One focussing on food security indicators ( Category A ), and another one on data requirement and sources of food security measurement ( Category B ). Specifically, the search strings (“food security” OR “food insecurity” OR “food availability” OR “food affordability” OR “food access” OR “food utilization” OR “food utilisation” OR “food stability” OR “nutrition security” OR “nutrition insecurity”) AND (“measurement” OR “indicators” OR “metrics” OR “index” OR “assessment” OR “scales”) were used for Category A . For Category B , we used (“food security” OR “food insecurity” OR “food availability” OR “food affordability” OR “food access” OR “food utilization” OR “food utilisation” OR “food stability” OR “nutrition security” OR “nutrition insecurity”) AND (“data” OR “big data” OR “datasets” OR “survey” OR “questionnaire”). The retrieved articles together with some of the inclusion and exclusion criteria, and the number of retrieved articles at each step, are presented in Fig. 1 . The following inclusion and exclusion criteria were also used during the literature searching and screening process in addition to those criteria presented in Fig. 1 : (a) Search field: title–abstract–keywords (Scopus); topic (WoS), (b) Time frame: 2010–09/03/2021, (c) Language: English, (d) Field of research: Agricultural and Biological Sciences Footnote 2 ; Economics, Econometrics and Finance (Scopus); Agricultural Economics Policy; Food Sciences Technology (WoS), and (e) Type: journal articles ( Category A ); journal articles, data, survey, database ( Category B ). We limited our literature search to publications from 2010 onwards since it was during this period that due attention has been given to the harmonisation of food security measurement. Footnote 3 This was also evident from the 2013 special issue of Global Food Security journal on the theme Measuring Food and Nutrition Security . Footnote 4
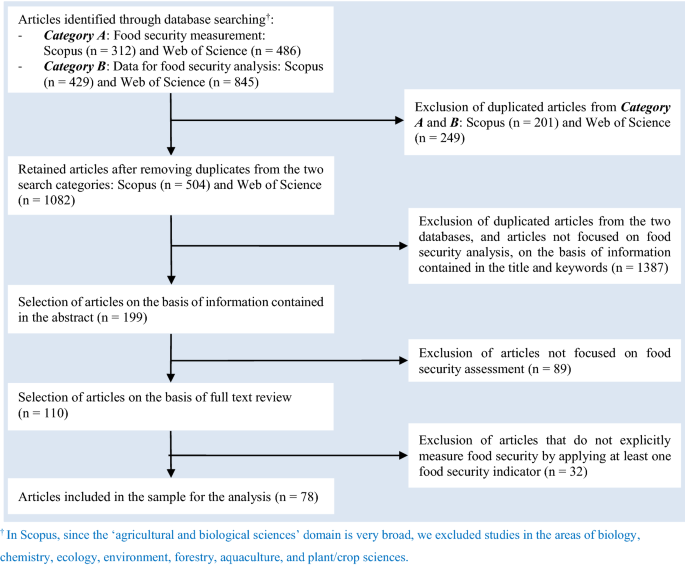
Literature searching and screening criteria
As we noted above, an ideal food security indicator should capture all the four food security dimensions at individual level to reflect the 1996 World Food Summit definition of food security. We reviewed only those articles that have explicitly measured food in/security by applying at least one food security indicator. These indicators, measuring at least one of the four food security dimensions, were identified based on recent (review) articles on food security measurement [ 8 , 9 , 10 , 14 , 15 ]. A total of 110 articles were selected for full content review after the pre-screening process based on title, keyword and abstract review (Fig. 1 ). After the full content review, 32 articles were further excluded. Fourteen of these were excluded, as they did not measure food security explicitly (e.g. [ 45 , 46 ] or the food security indicator/method of measurement was not described (e.g. [ 47 ] or they used ‘inappropriate’ indicators that do not capture at least one of the four food security dimensions (e.g. [ 48 ]. For example, Koren and Bagozzi [ 48 ] used per capita cropland as a food security measure, which is not a valid indicator for the multidimensional food security concept (it cannot even fully capture the food availability dimension). Thirteen publications that we classified as methodological, two review articles [ 49 , 50 ], and three articles on seed insecurity [ 51 ], marine food insecurity [ 52 ] and political economy of food security [ 53 ] were also excluded. Finally, we reviewed, analysed, and summarised the scientific evidence of 78 articles on food security measurement (see Additional file 1 for the list of the articles and the data). The validity and reliability of the SLR have been ensured by specifying the SLR setting following Kitchenham et al. [ 39 ], and by providing sufficient information regarding the literature extraction and screening processes. Moreover, the three authors have double-checked the correctness of the processes such as definitions of search strings and inclusion–exclusion criteria, and confirming the retrieved data and data interpretation to reduce bias. The limitations of the study are also discussed (see under the “ Discussion ” section).
Review of articles by region, indicators used, intended purpose, and level of analysis
Following the exclusion of the non-pertinent articles (Fig. 1 ), 78 articles were included in our food security measurement dataset for the analysis (Additional file 1 ). Relatively, more publications were retrieved from the years 2019 and 2020 whereas there were no articles from 2010. Footnote 5 The journals of Food Security (33%) and Food Policy (14%) are the main sources of the retrieved articles (Fig. 2 ). The journals in the field of agricultural economics are also important sources of the retrieved articles (15%). Figure 3 depicts the distribution of the retrieved articles by region/country of study focus. Sub-Sahara Africa has been the main focus of the studies, followed by Asia. At country level, USA (8 studies) and Ethiopia (7 studies) were the most studied countries. Besides the studies represented in Fig. 3 , we identified nine other studies focusing at global and regional levels: global [ 7 , 12 , 54 , 55 ], developing countries (Slimane et al. [ 56 ]), Middle East and North Africa (MENA) region [ 57 ], Latin America and Caribbean [ 58 ], and Sub Sahara Africa [ 59 , 23 ]. Despite food insecurity being a global issue, there is lack of studies covering the different parts of the world (e.g. MENA region, Latin America and Europe).
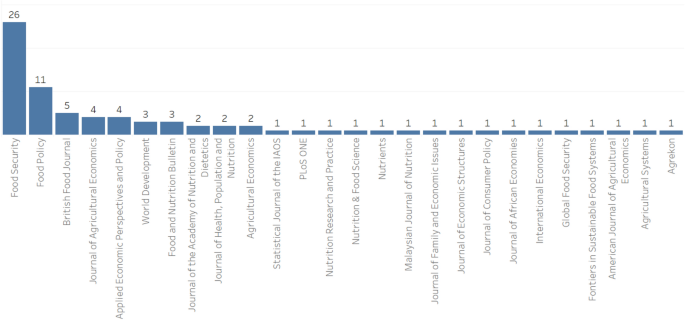
Number of articles per journal (total number of articles: 78)
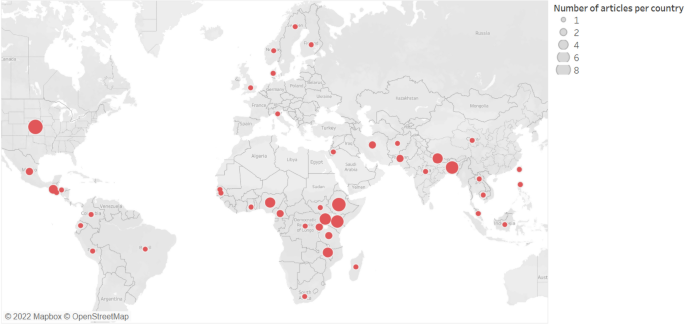
Summary of articles by country (Note: Some articles focus on more than one country, resulting in 89 articles by study area)
Figure 4 shows the summary of the number of articles by the type of food security indicator that they applied. Seventeen articles applied the household-level calorie adequacy (i.e. undernourishment) indicator, making it the most frequently used one. This indicator measures calorie availability relative to the calorie requirement of the household by accounting for age and sex differences of the household members (note that this indicator is different from FAO’s Prevalence of Undernourishment (POU) indicator (Table 2 ; [ 13 ]). A household is considered as food insecure if the available calorie is lower than the household’s calorie requirement. This indicator has been used in the literature to assess the prevalence of food insecurity [ 35 , 36 , 60 , 61 , 62 , 63 , 64 , 65 , 66 , 67 ], for programme evaluation [ 68 , 66 ], and to analyse food security determinants [ 35 , 60 , 66 , 67 , 69 , 70 , 71 ]. Some studies addressed the main drawback of the calorie adequacy indicator (its failure to account for diet quality) by measuring both calorie and micronutrient adequacy [ 54 , 65 , 70 , 72 ].
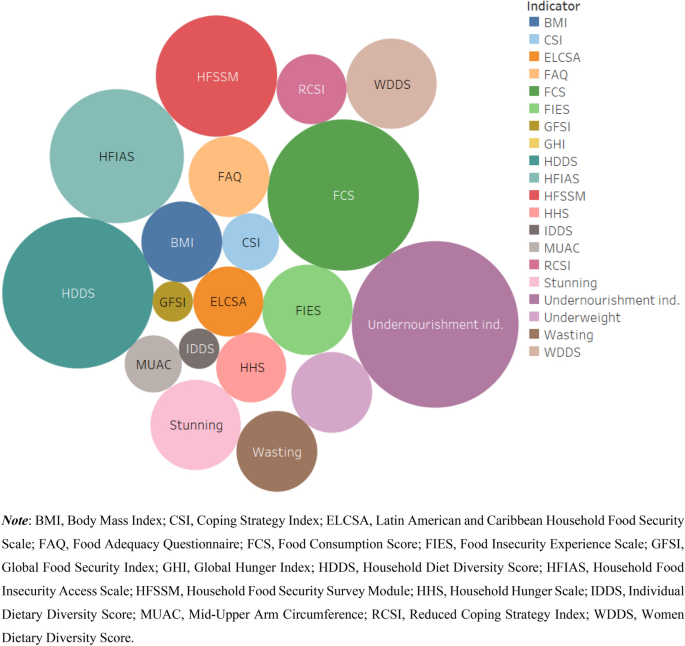
Summary of the publications by the type of food security indicators employed
Out of the 17 studies that applied the calorie adequacy indicator, three articles [ 35 , 69 , 71 ] classified households into food secure and food insecure based on the amount of expenditure on food that is required to purchase the minimum caloric requirement. A household is classified as food insecure if the expenditure on food is less than the predetermined threshold amount required for achieving the minimum caloric requirement. This measure allows us to account for the effect of food price inflation on household’s food access.
A subjective (self-reported) version of the household calorie adequacy indicator, the Food Adequacy Questionnaire (FAQ), was also used in 4 of the 78 articles (Fig. 4 ). Tambo et al. [ 73 ] and Smith and Frankenberger [ 74 ] measured food insecurity as the number of months of inadequate food provisioning during the last year owing to lack of resources. Bakhtsiyarava et al. [ 75 ] used FAQ to derive a binary measure of food security based on self-reported shortage of food in the last year, whereas Verpoorten et al. [ 23 ] measured food security using the question ‘Over the past year, how often, if ever, have you or anyone in your family gone without enough food to eat? Never/Just once or twice/Several times/Many times/Always’. Although these simple food security measures based on FAQ can usefully capture a household’s experience of food insecurity and for conducting preliminary assessments, they are prone to subjective biases [ 24 ]. A comparison of studies is complicated because FAQ’s measures are not standardised (e.g. differences in phrases and scales used in the questions).
The dietary diversity indicators Household Diet Diversity Score (HDDS), Women Diet Diversity Score (WDDS), Individual Diet Diversity Score (IDDS), and Food Consumption Score (FCS) were also frequently used in the literature (Fig. 4 ). About 44% of the publications used diet diversity indicators for measuring food security. (Additional file 2 : Tables S1, S2) summarise the studies that applied the dietary diversity score measures (HDDS, WDDS, IDDS) and FCS. Most of the studies applied the diversity score indicators for estimating food insecurity prevalence (Additional file 2 : Table S1). Bakhtsiyarava et al. [ 75 ], Bolarinwa et al. [ 76 ], Islam et al. [ 77 ], and Sibhatu and Qaim [ 78 ] applied HDDS when analysing the determinants of food security. Tambo et al. [ 73 ] and Islam et al. [ 68 ] used HDDS as a measure of food security for program evaluation.
The main weakness of the dietary diversity measures is that they do not account for the quantity and quality of the consumed diet (nutritional value); for instance, consumption of very small quantities of certain foods would raise the diversity score without contributing much to a household’s/individual’s nutritional and micronutrient supply [ 78 ]. HDDS does not also account for intra-household diet diversity. Thus, a higher diet diversity score does not necessarily mean a better household/individual food security. Most of the retrieved articles addressed these drawbacks by combining diversity measures with other food security indicators (Additional file 2 : Table S1). For example, Sibhatu and Qaim [ 78 ] applied HDDS and WDDS in combination with measures of calorie and micronutrient adequacy. Tambo et al. [ 73 ] combined HDDS and WDDS with the Food Insecurity Experience Scale (FIES) and FAQ, whereas Bolarinwa et al. [ 76 ] integrated HDDS and per capita food expenditure.
There is also a difference in the literature regarding the recall period used when measuring dietary diversity, namely, 7 days vs 24 h (Additional file 2 : Table S1). A 7 day recall period leads to higher diversity scores than a 24 h recall period because it considers the daily variation in food consumption [ 78 ]. Although the 7 day recall period is associated with higher respondent bias, conclusions drawn from a 24 h recall period may also be misleading, as some relevant food groups might not be considered in the food security assessment (e.g. livestock products that food insecure households seldom consume daily) [ 78 ]. It is therefore important to consider the differences in recall periods when designing measurement.
About 57% of the studies that employed FCS (Additional file 2 : Table S2) used it to estimate food insecurity prevalence [ 36 , 65 , 70 , 71 ,, 79 , 80 , 81 , 83 , 84 ]. Four other studies applied FCS to analyse the determinants of food security [ 85 – 88 ], whereas two used it for impact evaluation [ 89 , 90 ].
D'Souza and Jolliffe [ 85 ] showed how applying two different food security indicators (per capita daily caloric intake and FCS) could lead to different conclusions when analysing the effect of food price shock on household food security. They estimated the marginal effects of wheat price increase on per capita daily caloric intake and FCS using unconditional quantile regression for each decile of the food security distribution. They found that households with lower calorie intake (food insecure households) did not exhibit a decline in per capita calorie intake because of the wheat price increase. However, households with higher calorie intake (food secure households) exhibited a higher reduction in per capita calorie intake in response to the price increase. On the other hand, the FCS estimation results showed that the most vulnerable households exhibited larger reductions in dietary diversity (FCS) in response to higher wheat prices compared with the households at the top of the FCS distribution (households with higher FCS). Thus, the most vulnerable households might maintain their calorie intake by compromising diet quality. These results imply that food security monitoring or impact assessments based solely on calorie intake could be misleading, and may have severe long-term implications for households’ well-being. In this regard, analysis based on dietary diversity-based measures (e.g. FCS) provides more insights into the effects of shocks on household food security (diet quality) across the entire food security distribution [ 85 ]. However, Ibok et al. [ 36 ] noted that FCS (and per capita calorie adequacy) are not good indicators of household’s vulnerability to food insecurity compared with CSI. In response, they developed the Vulnerability to Food Insecurity Index.
About 40% of the retrieved publications used experience-based indicators (Household Food Insecurity Access Scale [HFIAS], Household Hunger Scale [HHS], Household Food Security Survey Module [HFSSM], Latin American and Caribbean Household Food Security Scale [ELCSA], Food Insecurity Experience Scale [FIES]) for measuring food security (Fig. 4 ). HFIAS is the most widely used experience-based indicator (11 articles), followed by HFSSM (9 articles) and FIES (5 times). ELCSA and HHS have been used three times each. HFIAS was primarily used for estimating the prevalence of food insecurity, whereas its adapted version HHS was mainly used for analysing the determinants of food insecurity (Additional file 2 : Table S3). The HFSSM was mainly used to analyse the determinants of household level food security in the US (six articles) (Additional file 2 : Table S4). Courtemanche et al. [ 91 ] and Burke et al. [ 19 ] used HFSSM for program evaluation, respectively, to analyse the effects of Walmart Supercenters (which increase food availability at lower food prices) on household food security and school-based nutrition assistance programs on child food security (Additional file 2 : Table S4).
Romo-Aviles and Ortiz-Hernández [ 92 ] used the ELCSA food security indicator to analyse the differences in food, energy, and nutrients supplies among Mexican households according to their food insecurity status (Additional file 2 : Table S4). In the first stage, they applied an ordinal regression model to analyse the determinants of household food insecurity status. In the second stage, they analysed the effect of food insecurity (i.e. a household’s food insecurity state as an independent variable) on household’s energy and nutrient supplies by using the ordinary least squares (OLS) model. Sandoval et al. [ 66 ] compared ELCSA and the household calorie adequacy indicator in food security analysis: prevalence estimation, determinants analysis, and program evaluation. They concluded that the two indicators provided very different food insecurity prevalence estimates, and the determinants were shown to vary significantly. The results of the programme evaluation also showed that the magnitude of the effect of a cash transfer program was significantly larger when using the ‘objective’ undernourishment indicator than the ‘subjective’ ELCSA food security indicator.
The majority of the five studies that used the FAO’s FIES indicator analysed the determinants of food security at regional and global levels, whereas one study [ 73 ] used it for program evaluation to assess the effect of provisions of a plant health service on food insecurity prevalence among farming households (Additional file 2 : Table S5).
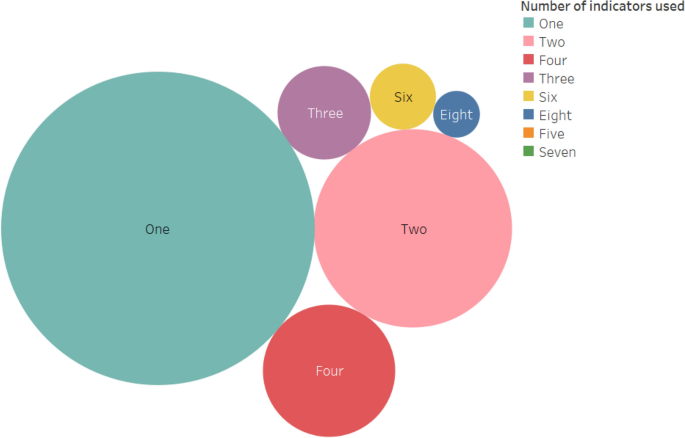
Figure 5 summarises the data on the proportion of articles according to the number of indicators used per article. About 58% of the 78 articles used only one indicator in their food security analysis. The HFSSM and household calorie adequacy indicator have respectively been used eight and seven times as the sole food security indicator in food security analyses. HFIAS (four times), FIES (three times), and FCS (three times) were also used as the only measures of food security. The experience-based indicators (HFSSM, HFIAS, and FIES) are the most frequently used indicators as a single measure of food security in the literature, whereas the other categories of food security indicators (dietary diversity, anthropometric, and coping strategy) are mostly used in combination with other indicators.
Summary articles by the number of indicators used per article ( N = 78 )
Three studies (out of the 78 articles) applied at least six food security indicators (one study used eight indicators while the other two studies used six indicators each). Islam et al. [ 68 ] applied eight food security indicators to analyse the effects of microcredit programme participation on household food security. They applied the calorie adequacy indicator, HDDS (number of food groups consumed), Food Variety Score (FVS, number of food items consumed), three child anthropometry measures (stunning, wasting, underweight), and two women anthropometry measures (body mass index [BMI] and mid-upper arm circumference [MUAC]) as measures of food security. Bühler et al. [ 79 ] applied six indicators (FCS, Reduced Coping Strategy Index [RCSI], HFIAS, and child stunning, wasting and underweight) to evaluate the relationship between household’s food security status and individual’s nutritional outcomes. The indicators FCS, RCSI, and HFIAS were used to measure a household’s food security status, whereas the anthropometry measures were used as indicators of individual’s nutritional outcomes. Maxwell et al. [ 83 ] also applied six food security indicators (Coping Strategy Index [CSI], RCSI, FCS, HDDS, HFIAS, and HHS) to compare the estimates of food insecurity prevalence over seasons of the most frequently used indicators.
About 45% and 37% of the retrieved articles applied food security indicators to analyse food security determinants and for food insecurity prevalence estimation, respectively. The calorie adequacy indicator (11 articles), FCS (8 articles), HDDS (7 articles), HFSSM (7 articles), and HFIAS (7 articles) were the most frequently used indicators in this regard. The calorie adequacy indicator (11 articles), FCS (10 articles), HDDS (8 articles), and HFIAS (7 articles) were the most applied indicators for estimating food insecurity prevalence.
About 60% of the retrieved studies measured food security at household-level while 20% of them assessed food security at individual-level. The most frequently used household-level indicators were the calorie adequacy indicator (14 articles), FCS (13 articles), and HDDS (12 articles). The experience-based household food security indicators HFIAS and HFSSM were also used nine and seven times, respectively. For individual-level analyses, the following child anthropometry measures were mostly used: stunning (four times), wasting (three times), and underweight (three times). The individual-level food security indicators WDDS and BMI were also used four times each.
Summary of indicators by study region and data source
As shown in Fig. 3 , the main focus areas of the 78 publications were Sub Sahara Africa and South (east) Asia. These studies employed different indicators in different countries. The type of FS indicator employed in these studies by country is summarised in Fig. 6 (reported only for those countries where at least two indicators were used). The HFSSM indicator was used 7 times in the USA (the highest at country level), which is expected as the HFSSM is used for monitoring household-level food security in the USA. The HDDS was used four times in Kenya whereas the calorie adequacy indicator and HDDS were used three-times each in Ethiopia and Bangladesh.
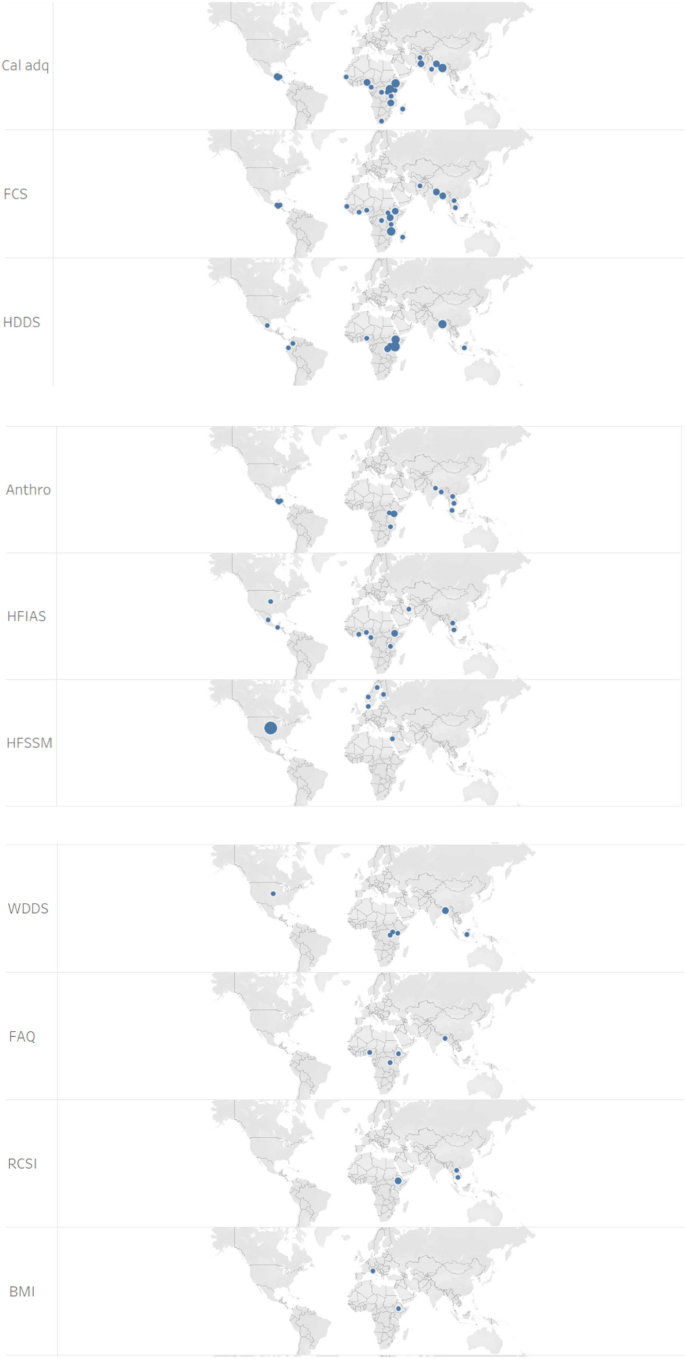
Summary of studies by country and indicators applied [Note: Multiple indicators could be used per study, and a study may cover multiple countries]
About 42% of the 78 studies employed primary data. The majority of these 33 studies applied experience-based indicators: HFIAS (9 articles), HFSSM (6 articles), and other experience-based indicators (4 articles). Dietary diversity-based indicators (12 articles) and calorie adequacy indicator (8 articles) were also applied frequently by studies that employed primary data (Fig. 7 ). The distributions of the 33 studies that employed primary data by region is as follow: Africa (15 articles), Asia (7 articles), Central and South America (4 articles), Europe (2 articles) and North America (5 articles). The USA and Ethiopia are the countries with the highest number of studies by country (5 and 4 studies, respectively) (Fig. 7 ). The majority of the studies that applied calorie adequacy indicator and FCS have employed secondary data whereas most of the studies that applied experience-based indicators have employed primary data (Fig. 8 ). This may imply the fact that collecting data for experience-based indicators is convenient compared to the other type indicators such as the dietary-based ones.

Summary of indicators used by country and data source [Note: Multiple indicators could be used per study, and a study may cover multiple countries]
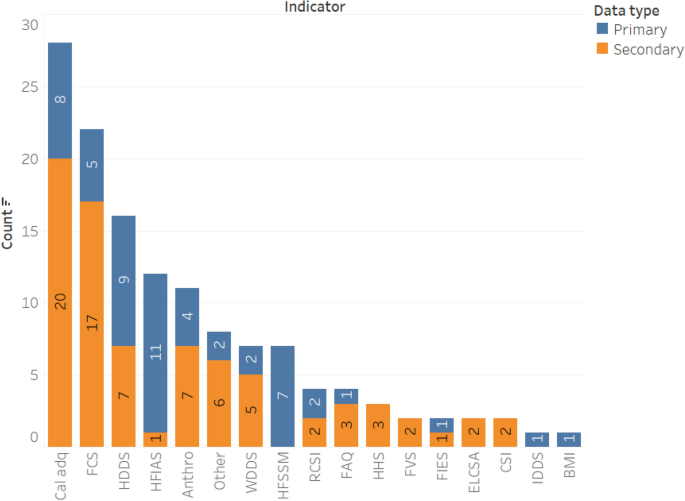
Summary of indicators used by data source [Note: Multiple indicators could be used per study]

Quantitative characterization of food security dimensions and components
An ideal food security indicator should capture all the four food security dimensions (availability, access, utilization and stability) and components (quantity, quality, safety and preference). Because ‘measuring food security explicitly’ was one of our inclusion criteria for selecting articles (Fig. 1 ), and as the most commonly used food security indicators in the literature are measures of food access (Tables 1 , 2 , 3 , 4 ), all the 78 articles measured the food access dimension. However, the utilisation (13%) and stability (18%) dimensions of food security were seldomly captured. For measuring food utilisation, six of the ten articles applied anthropometry measures [ 64 , 68 , 79 , 93 , 94 , 95 , 96 ]. Izraelov and Silber [ 7 ] applied the Global Food Security Index (GFSI), which allows measuring food utilisation as a construct using 11 indicators. Slimane et al. [ 56 ] derived an indicator of food utilisation from ‘ access to improved water sources and access to improved sanitation facilities ’, which are two of the ten indicators of the food utilisation dimension in FAO’s Suite of Food Security Index (Table 2 ; [ 29 ]. In the literature, the stability dimension has commonly been captured by using (i) composite indices [ 7 , 12 ], (ii) the concepts of vulnerability [ 35 , 36 , 61 , 69 , 86 ] and resilience [ 74 , 88 , 90 ], (iii) econometric approaches [ 76 , 88 , 96 ] (iv) dynamic farm household optimisation model [ 97 ], and (v) measuring food security over time/seasons [ 76 , 83 ].
Almost all the studies analysed the quantity and quality components of food security, whereas the food safety and preference/cultural acceptability components were rarely captured during food security measurements. Although these components are critical in achieving food security according to the 1996 World Food Summit definition of food security, only 2 and 18 studies (out of the 78 articles) captured the food safety and preference components, respectively. Most of the studies (11 articles) that captured the preference component applied the HFIAS indicator, as the second question of the HFIAS 9-items questionnaire addresses the preference food security component. On the other hand, Izraelov and Silber [ 7 ] using the GFSI and Ambikapathi et al. [ 98 ] using an experience-based food security indicator captured the food safety component.
Only 3 of the 78 publications employed a comprehensive food security measurement, where they measured food security by explicitly considering all the four food security dimensions [ 7 , 12 , 96 ]. Caccavale and Giuffrida [ 12 ] and Izraelov and Silber [ 7 ] used composite food security indices to capture the four food security dimensions, while Upton et al. [ 96 ] applied a moment-based panel data econometric approach to the concept of development resilience in food security measurement. Caccavale and Giuffrida [ 12 ] developed the Proteus Composite Index (PCI) for measuring food security at national level. PCI can be used to monitor the food security progresses of countries by comparing within (over time) and between countries. It addresses the shortcomings of other composite indicators in terms of weighting, normalisation, and sensitivity. The PCI is constructed from 21 indicators: availability (2 indicators), access (7 indicators), utilisation (2 indicators), and stability (10 indicators) (Table 5 ). Eleven of these indicators were adopted from FAO’s Suite of food security Index [ 30 ].
Izraelov and Silber [ 7 ] is the only study (out of the 78 publications) that applied the GFSI for measuring food security at national level. Like FAO’s Suite of Food Security Index, the GFSI is a composite food security indicator that measures all the four dimensions of food security. Because the GFSI primarily assesses and monitors food security at a national level (i.e. ranking of countries based on the GFSI score), Izraelov and Silber [ 7 ] investigated the sensitiveness of the rankings of countries to the list of indicators used for the different dimensions and to the set of weights elicited from the panel of experts of the Economic Intelligence Unit by employing PCA and/or data envelopment analysis (DEA) methods. The authors concluded that the rankings based on the GFSI are robust in relation to both the expert weights used and the choice of indicators. The Economist Intelligence Unit (EIU) (2021) produces the GFSI index each year by using 69 indicators covering the four dimensions of food security: availability, affordability (accessibility), quality and safety (utilization), and natural resources and resilience (stability).
Upton et al.’s [ 96 ] defined four axioms that an ideal food security measure must reflect. Relying on the 1996 World Food Summit food security definition [ 4 ], they defined the following four axioms:
Scale axiom: it addresses both individuals and households at different scale of aggregation (e.g. regions) reflecting ‘all people’;
Time axiom: reflecting ‘at all times’, it captures the food stability dimension to account for both predictable and unpredictable variability of food security over time;
Access axiom: derived from ‘physical, social and economic access’, it captures the food access (and implicitly the availability) dimensions; and
Outcomes axiom: reflecting on “an active and healthy life”, it reflects the food utilization dimension, which captures the dietary, nutrition, and/or health outcomes.
Upton et al. [ 96 ] did note that no food security measure at the time satisfied all these four axioms in the literature. In response, they employed a stochastic dynamic measure of well-being based on the concept of development resilience [ 99 ]. Barrett and Constas [ 99 ] defined development resilience as ‘the capacity over time of a person/household... to avoid poverty in the face of various stressors and in the wake of myriad shocks. If and only if that capacity is and remains high over time, then the unit is resilient’ (p. 14). [ 100 , 101 ] demonstrated the econometric implementation of the stochastic dynamic measure of well-being at multiple scales using household or individual survey data. They showed how a measure of household or individual well-being and resilience can be estimated, and aggregated at regional or national level using a system of conditional moment functions. By adopting the [ 100 , 101 ] moments-based (dynamic) panel data econometric approach, Upton et al. [ 96 ] used the resilience concept in food security measurement to reflect the above four axioms as follows:
The scale axiom is satisfied by estimating food security at the individual or household level, and then by aggregating it into higher-level groups (e.g. regions).
The time/stability axiom is captured by using [ 100 , 101 ] dynamic approach.
The access axiom is considered by conditioning the moments of the food security distribution regarding economic, physical, and social factors that influence food access.
The outcome (utilisation) axiom is considered by using nutritional status indicators as dependent variables in the econometric model. Upton et al. [ 96 ] used HDDS and child MUAC as outcome indicators.
Recent developments in food security measurement
The concepts of vulnerability and resilience have only recently been introduced in food security measurement and analysis. Rather than directly measuring food security or food insecurity, researchers have been seeking to measure vulnerability to food insecurity and food security resilience, and their respective determinants/drivers. Out of the 78 publications, 5 and 4 articles respectively employed the concepts of vulnerability [ 35 , 36 , 61 , 69 , 86 ] and resilience [ 74 , 88 , 90 , 96 ] in their food security measurement and analysis.
Ibok et al. [ 36 ] developed the Vulnerability to Food Insecurity Index (VFII) for measuring the vulnerability of households to food insecurity, and validated it by comparing the estimates of vulnerability to food insecurity with the traditional food insecurity measures (calorie adequacy, CSI, FCS). The VFII is a composite index constructed from three dimensions (Table 6 ): exposure (probability of covariate shock occurring), sensitivity (previous/accumulative experience of food insecurity), and adaptive capacity (how households respond, exploit opportunities, resist or recover from food insecurity shocks, which is the coping ability of households). A set of indicators are used for each of the three dimensions (Table 6 ). By defining thresholds, Ibok et al. [ 36 ] assigned households into one of the three categories: highly vulnerable, mildly vulnerable, and not vulnerable to food insecurity. The results showed that VFII has a weak positive correlation with FCS and per capita calorie adequacy, whereas it has a negative correlation with CSI. Some of the households with poor calorie per capita consumption were classified as not vulnerable to food insecurity, whereas some households with acceptable calorie per capita consumption were identified as highly vulnerable to food insecurity. The authors concluded that a household’s vulnerability to food insecurity can be better measured using CSI than using FCS and per capita calorie adequacy (using the VFII as a benchmark).
[ 86 ] analysed the effects of households’ vulnerability to different climatic hazards on their food access by employing a generalised linear regression model. They used FCS as a measure of household food access, concluding that households that are vulnerable to flood were found to be more likely to be food insecure (i.e. to have a low FCS) than less vulnerable households.
Vaitla et al. [ 88 ] and Upton et al. [ 96 ] employed dynamic panel data modelling to measure the food security resilience of households. They analysed the determinants of food security status at a point in time, and its food security resilience by using different food security indicators. They defined resilience as ‘the probability that a household is truly above a chosen food security cut-off, given its underlying assets, demographic characteristics, and past food security status’. Similar to Upton et al. [ 96 ], they used the moments (mean and variance) of the food security score over time to estimate resilience as the probability of attaining a given level of food security. Vaitla et al. [ 88 ] used FCS and RCSI as a dependent variable in their dynamic panel data model. They concluded that the determinants of a household’s food security status and food security resilience are different. They also showed that the drivers of food security resilience vary across the two food security measures used as dependent variables.
Lascano Galarza [ 90 ] investigated the effects of food assistance on a household’s food security status at a point in time, and its food security resilience, by applying FAO’s Resilience Index Measurement and Analysis II framework. The author used FCS and food expenditure as measures of food security when evaluating the effects of the food assistance program and the household’s resilience on food security status. Factor analysis and multiple indicators multiple causes models were used to construct the resilience score and to analyse its effect on food security. The resilience score was derived from four indicators: assets, access to basic services, social safety nets, and adaptive capacity. The author ultimately found a significant positive association of food assistance programmes with a household’s food security status and food security resilience.
Smith and Frankenberger [ 74 ] analysed the effects of resilience capacity in reducing the effect of shocks on household food security using HHS and FAQ (number of months of inadequate household food access) as measures of food security. The results of their fixed effect panel data model showed that resilience capacity enhancing attributes such as household assets, human capital, social capital, information access, women empowerment, diversity of livelihood, safety nets, and market access reduce the negative effect of flooding on household food security.
Which food security indicator is the best?
Although numerous food security indicators have been developed for use in research, there is no agreement on the single ‘best’ food security indicator among scientists or practitioners for measuring, analysing, and monitoring food security [ 9 , 12 ]. The different international agencies also use their own sets of food security indicators (e.g. World Food Programme: FCS, USAID: HFIAS; FAO: POU and FIES; and EIU: GFSI). Figure 9 summarises the most applied food security indicators according to the level of analysis and the food security dimensions that they intend to reflect. The level of analysis ranges from macro (e.g. national) to micro (e.g. individual) levels, and the measured food security dimension from availability to utilisation. An ideal food security indicator should capture all the four food security dimensions at individual level to reflect the 1996 World Food Summit definition of food security. However, most of the available indicators are measures of food access at the household level (Fig. 9 ). Only a few composite and anthropometry indicators can measure food utilisation (besides availability and access) at national and individual levels, respectively. On the other hand, the stability dimension can be captured by estimating food security indicators over time or as described above in ‘‘ Quantitative characterization of food security dimensions and components ’’ Sect. The three composite indicators GFSI [ 26 ], Suite of Food Security Index [ 29 ], and PCI [ 12 ] can allow to directly measure the stability dimension of food security while also capturing the other three food security dimensions at national level.
Summary of the retrieved indicators according to the level of analysis and food security dimensions
In general, there exist an inherent trade-off when choosing one indicator over another type of indicator because the various classes of food security indicators reflect different aspects of food security [ 96 ] such as dimensions, components, levels of analysis (e.g. national vs individual), and data requirement (subjective vs objective; recall period of 1 year vs 24 h). Therefore, most of the commonly used indicators can be considered as mutually complementary than substitutes for one another. The subjective experience-based indicators, for example, measure a household’s experience of anxiety/worry/hunger arising from lack of food access, whereas the objective dietary diversity-based indicators measure a household’s access to diverse food, reflecting a household’s caloric intake and diet quality. Household dietary diversity-based and caloric adequacy indicators also complement each other because sufficient calorie might be achieved with low food quality (without diversified diet), whereas a diverse diet might not be enough to meet a household’s caloric requirement. Noting this complementarity, Bolarinwa et al. [ 76 ] classified households into three categories of food insecurity (food secure, partially food insecure, and completely food insecure) by integrating two indicators: HDDS and per capita food expenditure (where the food expenditure reflects caloric adequacy).
Data requirements of food security measurement
The most critical challenge of a comprehensive food security measurement and analysis is generating reliable data consistently for estimating complementary food security indicators (at the individual level) [ 13 ]. Measuring food security with a high frequency consistently over time (e.g. quarterly instead of annually) at the individual level by applying a set of complementary indicators (e.g. calorie/nutrient adequacy and anthropometry measures) can help us better analyse and monitor food security (Fig. 10 ). A national level food security measurement at a point in time (e.g. using POU) is less informative for decision-making compared with measuring food security every year (or ideally in real-time) at the household level (e.g. using calorie adequacy). Integrating food consumption and anthropometry information in regular national household living standard surveys can also be crucial to eliminating the limitations of current measurement approaches, especially because nutrition, food consumption, health, and income are interrelated [ 13 ].

High frequency food security measurement for better food security analysis.
De Haen et al. [ 13 ] rightly remind us that to improve the reliability and accuracy of a nation’s food security measurement and analysis, ‘the focus should be on generating more timely, comprehensive, and consistent household surveys that cover food consumption and anthropometry, [which] allow much better assessment of the prevalence of food insecurity and undernutrition, as well as of trends and driving forces.’ That is, first, generating data from a nationally representative sample through comprehensive household surveys allows us to estimate a set of complementary indicators reflecting the different aspects of food security measurement (dimensions, components, outcomes, behavioural responses, coping mechanisms) (Fig. 10 ). Second, comprehensive surveys help measure both the prevalence of food insecurity and its drivers/determinants. Third, it is critical to generate these data consistently over time so that the progress towards food security can be monitored, drivers can be analysed over time, and food insecurity can be detected well in advance. This approach could address the UN Scientific Group’s criticism [ 11 ] that ‘existing early warning systems lack indicators to adequately monitor degradation of food systems.’ Fourth, the data allow us to analyse and evaluate the effects of programmes and interventions (over time) at different levels (individual, household, and national). It also opens opportunities to conduct development research in food, nutrition, health, and poverty [ 13 ].
In summary, we suggest the following points in the light of the above discussions for a comprehensive food security measurement:
Food security should be measured at the individual (or at least at household) level by applying a set of complementary food security indicators to capture the availability, access, and utilisation dimensions of food security. Combining anthropometry measures with other objective food security indicators (e.g. calorie adequacy or dietary diversity indicators) will further allow us to capture these three dimensions.
The fourth dimension of food security, i.e. the stability dimension, can be captured by producing the estimates of the complementary food security indicators over time or in real time. A repeated high frequency food security measurement (if possible by using near real-time data) is thus preferable, as it can also help to identify the onset of food insecurity in time, to evaluate interventions/programs, and to monitor food security progresses.
The behavioural aspects of food insecurity and the cultural acceptability of food can be measured by using one of the experience-based measures. For example, FAO’s FIES can be applied to estimate the prevalence and severity of food insecurity at individual level. Because the FIES has been applied in more than 100 countries, countries can compare their respective food security states with each other.
The use of experience-based indicators (e.g. FIES) allows conducting rapid food security assessments as the data collection is easier compared to the objective food security indicators (e.g. calorie adequacy).
Integrating food consumption (intake, expenditure, and diet diversity) and anthropometry information in regular national household living standard surveys enables us to collect complete and consistent data for estimating complementary food security indicators in food security analyses.
Study limitations and future research
In this study, we identified and characterized the most commonly applied food security indicators in the literature with respect to the dimensions and components covered, methods and models of measurement, level of analysis, data requirements and sources, intended purpose of application, and strengths and weaknesses. Subsequently, we analysed data on food security measurement from 78 peer-reviewed articles, and suggested the estimation of complementary food security indicators consistently over time for conducting a comprehensive analysis by taking all the four food security dimensions and components into account. In order to select the set of these complementary food security indicators that would be applicable to a specific context (e.g. country or region), we recommend to conduct a Delphi study by involving food security experts, policy-makers and other relevant stakeholders. In addition, we limited the literature search to two databases (Scopus and WoS) and included only peer-reviewed articles in this study. Therefore, we suggest to extend this study by broadening the literature type by including the grey literature (e.g. reports, book chapters and conference proceedings) and by searching from other databases, which reduce the publication bias. Moreover, we followed the 1996 World Food Summit definition of food security [ 5 ], which provided the foundation for the four food security dimensions ( availability , access , utilisation , and stability ). Accordingly, in this study, we organised the literature review on food security measurement over these four dimensions. However, food system researchers have recently noted the need to update the definition of food security in reference to sustainable food systems, for example, by including new food security dimensions [ 102 – 104 ]. Clapp et al. [ 103 ], for example, proposed the inclusion of two extra dimensions ( sustainability and agency ) to improve the framework of food security analyses. The inclusion of these two extra dimensions guarantees that every human being has access to healthy and nutritious food, not only now but also in the future. In this regard, sustainability can be considered as a pre-requisite for long-term food security [ 103 , 104 ]. Therefore, we recommend future research to operationalize literature reviews according to the six food security dimensions (i.e. availability , access , utilisation , stability , sustainability and agency ). Furthermore, most existing studies about food security measurement in the literature are based on the 1996 World Food Summit definition of food security [ 5 ]. Food security analyses based on this definition narrows the scope of the food security concept, and do not support system level analysis by considering other components of the food system. For example, food security is a subset (component) of the Food Systems Approach, which takes food environments, food supply chains, individual factors, external food system drivers, consumer behaviour, and food system outcomes (e.g. food security and health outcomes) into account [ 105 – 108 ]. Therefore, given the increasing attention to the Food Systems Approach and system level analyses in the literature, the Food Systems Approach can be used as a framework for operationalising future literature reviews on food security.
We critically reviewed numerous food security indicators and methodologies published in scientific articles since the last decade using the SLR methodology. We reviewed, analysed, and summarised the results of 78 articles on food security measurement. We found that the household-level calorie adequacy measure was the most frequently used indicator in the literature as a sole measure of food security. Dietary diversity indicators (HDDS, WDDS, IDDS, and FCS) and experience-based indicators (HFSSM, FIES, HFIAS, HHS, ELCSA) were almost equally in use and popular. In terms of the food security dimensions, food utilisation (13%) and stability (18%) were seldom captured. Caccavale and Giuffrida [ 12 ], Izraelov and Silber [ 7 ], and Upton et al. [ 96 ] are the only studies that measured food security by considering all four dimensions. We also found that the majority of the studies that applied calorie adequacy and dietary diversity-based indicators employed secondary data whereas most of the studies that applied experience-based indicators employed primary data, suggesting the convenience/simplicity of collecting data for experience-based indicators than dietary-based indicators. The use of experience-based indicators allows conducting rapid food security assessments whereas the use of complementary indicators is required for food security monitoring over time. We conclude that the use of complementary food security indicators, instead a single indicator, better capture the different food security dimensions and components,this approach is also beneficial for analyses at different levels. The results of this study, specifically the analysis on data requirements for food security measurement, can be used by food security stakeholders such as governments, practitioners and academics for briefs, teaching, as well as policy-related interventions and evaluations.
Availability of data and materials
All data are available within the paper.
Detailed discussion on this issue can be found in ''Which food security indicator is the best?'' Sect.
In Scopus, since the research field ‘Agricultural and Biological Sciences’ domain is very broad, we excluded studies in the areas of biology, chemistry, ecology, environment, forestry, aquaculture, and plant/crop sciences during the literature search (via “AND NOT”).
In line with this, our final food security measurement dataset does not contain articles from 2010 Additional file 1 .
The call to the special issue can be retrieved from the journal’s website: https://www.sciencedirect.com/journal/global-food-security/special-issue/10F642R6J6K .
This confirms the lack of due attention given to the standardization and harmonisation of food security measurement prior to 2010, and the lack of consensus among researchers, practitioners, or governments on the indicators and methodologies that should be applied for measuring and monitoring food security.
Abu B, Oldewage-Theron W. Food insecurity among college students in West Texas. Br Food J. 2019;121(3):738–54.
Article Google Scholar
Ahn S, Norwood FB. Measuring food insecurity during the COVID-19 pandemic of spring 2020. Appl Econ Perspect Policy. 2021;43(1):162–8.
Ahn S, Smith TA, Norwood FB. Can internet surveys mimic food insecurity rates published by the US government? Appl Econ Perspect Policy. 2020;42(2):187–204.
FAO (2009). Declaration of the world summit on food security. Rome. http://www.fao.org/fileadmin/templates/wsfs/Summit/Docs/Final_Declaration/WSFS09_Declaration.pdf Accessed 24 Feb 2021.
FAO (2006). Food Security: FAO policy brief. http://www.fao.org/forestry/13128-0e6f36f27e0091055bec28ebe830f46b3.pdf . Accessed 25 Feb 2021.
Maxwell S. Food security: a post-modern perspective. Food Policy. 1996;21:155–70.
Izraelov M, Silber J. An assessment of the global food security index. Food Secur. 2019;11:1135–52.
Cafiero C, Melgar-Quiñonez HR, Ballard TJ, Kepple AW. Validity and reliability of food security measures. Ann N Y Acad Sci. 2014;1331:230–48.
Article PubMed Google Scholar
Carletto C, Zezza A, Banerjee R. Towards better measurement of household food security: harmonizing indicators and the role of household surveys. Glob Food Sec. 2013;2:30–40.
Bawadi HA, Tayyem RF, Dwairy AN, Al-Akour N. Prevalence of food insecurity among women in northern Jordan. J Health Popul Nutr. 2012;30(1):49.
Article PubMed PubMed Central Google Scholar
Hertel, TW., Elouafi, I, Ewert, F. and Tanticharoen, M. (2021). Building resilience to vulnerabilities, shocks and stresses–action track 5. https://www.un.org/sites/un2.un.org/files/5-action_track-5_scientific_group_draft_paper_8-3-2021.pdf . Assessed 20 June 2021.
Caccavale OM, Giuffrida V. The Proteus composite index: towards a better metric for global food security. World Dev. 2020;126: 104709.
Beveridge L, Whitfield S, Fraval S, van Wijk M, van Etten J, Mercado L, Hammond J, Davila Cortez L, Gabriel Suchini J, Challinor A. Experiences and drivers of food insecurity in Guatemala’s dry corridor: insights from the integration of ethnographic and household survey data. Frontiers Sustain Food Syst. 2019;3:65.
Pérez-Escamilla R, Gubert MB, Rogers B, Hromi-Fiedler A. Food security measurement and governance: assessment of the usefulness of diverse food insecurity indicators for policy makers. Glob Food Sec. 2017;14:96–104.
Pérez-Escamilla R, Vilar-Compte M, Gaitan-Rossi P. Why identifying households by degree of food insecurity matters for policymaking. Global Food Secur. 2020;26:100459.
Borch A, Kjærnes U. The prevalence and risk of food insecurity in the Nordic Region: preliminary results. J Consum Policy. 2016;39(2):261–74.
Gulliford MC, Nunes C, Rocke B. The 18 Household Food Security Survey items provide valid food security classifications for adults and children in the Caribbean. BMC Public Health 2006;6(1):1–8
FAO. Methods for estimating comparable rates of food insecurity experienced by adults throughout the world. Rome: FAO. 2016.
Burke M, Cabili C, Berman D, Forrestal S, Gleason P. A randomized controlled trial of three school meals and weekend food backpacks on food security in Virginia. J Acad Nutr Diet. 2021;121(1):S34–45.
Salarkia N, Abdollahi M, Amini M, Neyestani TR. An adapted household food insecurity access scale is a valid tool as a proxy measure of food access for use in urban Iran. Food Security. 2014;6(2):275–82.
FAO. Escala Latinoamericana y Caribena de Seguridad Alimentaria (ELCSA): Manual de uso y aplicaciones. Santiago, Chile: FAO Regional Office, Latin America. 2012.
Deitchler M, Ballard T, Swindale A, Coates J. Introducing a simple measure of household hunger for cross-cultural use. Technical Note No. 12. Washington, DC: Food and Nutrition Technical Assistance Project-2. 2011.
Verpoorten M, Arora A, Stoop N, Swinnen J. Self-reported food insecurity in Africa during the food price crisis. Food Policy. 2013;39:51–63.
Headey D. Was the global food crisis really a crisis? Simulations versus self-reporting IFPRI discussion paper No 01087. Washington: International Food Policy Research Institute (IFPRI); 2011.
Google Scholar
Chegere MJ, Lokina R, Mwakaje AG. The impact of hermetic storage bag supply and training on food security in Tanzania. Food Security. 2020;12(6):1299–316.
EIU (Economist Intelligence Unit). Global food security index 2020: addressing structural inequalities to build strong and sustainable food systems. London: Economist Group; 2021.
Pangaribowo EH, Gerber N, Torero M. Food and nutrition security indicators: a review. FOOD SECURE working paper 05. 2013.
Wiesmann D. A Global Hunger Index: Measurement Concept, Ranking of Countries, and Trends. FCND Discussion Paper 212, IFPRI. 2006.
FAO (Food and Agriculture Organization) (2013a). The State of Food Insecurity in the World 2013. The multiple dimensions of food security. FAO, Rome.
FAO, 2013b. New approaches to the measurement of food security. AFCAS 23, 2013. Accessed 13 Apr 2021. http://www.fao.org/fileadmin/templates/ess/documents/afcas23/Presentations/AFCAS_9d_New_approaches_to_the_measurement_of_food_security.pdf .
WFP, World Food Program. Food consumption analysis: calculation and use of the food consumption score in food security analysis. Technical Guidance Sheet. WFP Vulnerability Analysis and Mapping, February 2008. 2008.
Vellema W, Desiere S, D’Haese M. Verifying validity of the household dietary diversity score: an application of rasch modeling. Food Nutr Bull. 2016;37(1):27–41.
Swindale A, Bilinsky P. Household Dietary Diversity Score (HDDS) for measurement of household food access: Indicator Guide (v.2). Washington, DC: FHI 360/Food and Nutrition Technical Assistance Project. 2006.
FAO. Guidelines for measuring household and individual dietary diversity. Rome: Food and Agriculture Organization; 2011.
Bogale A. Vulnerability of smallholder rural households to food insecurity in Eastern Ethiopia. Food Secur. 2012;4(4):581–91.
Ibok OW, Osbahr H, Srinivasan C. Advancing a new index for measuring household vulnerability to food insecurity. Food Policy. 2019;84:10–20.
Maxwell D, Caldwell R. The Coping Strategies Index: Field Methods Manual, second ed. CARE, Atlanta, GA. 2008. https://documents.wfp.org/stellent/groups/public/documents/manual_guide_proced/wfp211058.pdf . Accessed 29 May 2021.
Haysom G, Tawodzera G. “Measurement drives diagnosis and response”: gaps in transferring food security assessment to the urban scale. Food Policy. 2018;74:117–25.
Kitchenham B, Brereton OP, Budgen D, Turner M, Bailey J, Linkman S. Systematic literature reviews in software engineering—a systematic literature review. Inf Softw Technol. 2009;51:7.
Fayet CM, Reilly KH, Van Ham C, Verburg PH. What is the future of abandoned agricultural lands? A systematic review of alternative trajectories in Europe. Land Use Policy. 2022;112: 105833.
Iyer P, Bozzola M, Hirsch S, Meraner M, Finger R. Measuring farmer risk preferences in Europe: a systematic review. J Agric Econ. 2020;71(1):3–26.
Santeramo FG, Lamonaca E. The effects of non-tariff measures on agri-food trade: a review and meta-analysis of empirical evidence. J Agric Econ. 2019;70(3):595–617.
Santeramo FG, Lamonaca E. Evaluation of geographical label in consumers’ decision-making process: a systematic review and meta-analysis. Food Res Int. 2020;131: 108995.
Page MJ, McKenzie JE, Bossuyt PM, Boutron I, Hoffmann TC, Mulrow CD, Moher D. The PRISMA 2020 statement: an updated guideline for reporting systematic reviews. Syst Rev. 2021;10(1):1–11.
Dávila OG. Food security and poverty in Mexico: the impact of higher global food prices. Food Secur. 2010;2(4):383–93.
Natalini D, Bravo G, Jones AW. Global food security and food riots–an agent-based modelling approach. Food Security. 2019;11(5):1153–73.
Gregory CA, Coleman-Jensen A. Do high food prices increase food insecurity in the United States? Appl Econ Perspect Policy. 2013;35(4):679–707.
Koren O, Bagozzi BE. From global to local, food insecurity is associated with contemporary armed conflicts. Food Secur. 2016;8(5):999–1010.
Burchi F, De Muro P. From food availability to nutritional capabilities: advancing food security analysis. Food Policy. 2016;60:10–9.
Guo B. Household assets and food security: evidence from the survey of program dynamics. J Fam Econ Issues. 2011;32(1):98–110.
Mucioki M, Pelletier B, Johns T, Muhammad LW, Hickey GM. On developing a scale to measure chronic household seed insecurity in semi-arid Kenya and the implications for food security policy. Food Security. 2018;10(3):571–87.
Taylor SF, Roberts MJ, Milligan B, Ncwadi R. Measurement and implications of marine food security in the Western Indian Ocean: an impending crisis? Food Secur. 2019;11(6):1395–415.
Woertz E. Food security in Iraq: results from quantitative and qualitative surveys. Food Secur. 2017;9(3):511–22.
Geyik O, Hadjikakou M, Bryan BA. Spatiotemporal trends in adequacy of dietary nutrient production and food sources. Glob Food Sec. 2020;24: 100355.
Smith MD, Rabbitt MP, Coleman-Jensen A. Who are the world’s food insecure? New evidence from the food and Agriculture Organization’s food insecurity experience scale. World Dev. 2017;93:402–12.
Slimane MB, Huchet-Bourdon M, Zitouna H. The role of sectoral FDI in promoting agricultural production and improving food security. Int Econ. 2016;145:50–65.
Omidvar N, Ahmadi D, Sinclair K, Melgar-Quiñonez H. Food security in selected Middle East and North Africa (MENA) countries: an inter-country comparison. Food Secur. 2019;11(3):531–40.
Smith MD, Kassa W, Winters P. Assessing food insecurity in Latin America and the Caribbean using FAO’s food insecurity experience scale. Food Policy. 2017;71:48–61.
Bertelli O. Food security measures in Sub-Saharan Africa A validation of the LSMS-ISA scale. J Afr Econom. 2020;29(1):90–120.
Bashir MK, Schilizzi S. How disaggregated should information be for a sound food security policy? Food Secur. 2013;5(4):551–63.
Bashir MK, Schilizzi S, Sadler R, Ali G. Vulnerability to food insecurity in rural Punjab Pakistan. Bingley: Emerald Publishing Limited; 2018.
Book Google Scholar
Fawole WO, Ozkan B, Ayanrinde FA. Measuring food security status among households in Osun State Nigeria. British Food Journal. Bingley: Emerald Group Publishing Limited; 2016.
Guha S, Chandra H. Measuring disaggregate level food insecurity via multivariate small area modelling: evidence from rural districts of Uttar Pradesh, India. Food Secur. 2021;13:1–19.
Lovon M, Mathiassen A. Are the World Food Programme’s food consumption groups a good proxy for energy deficiency? Food Security. 2014;6(4):461–70.
Marivoet W, Becquey E, Van Campenhout B. How well does the food consumption score capture diet quantity, quality and adequacy across regions in the Democratic Republic of the Congo (DRC)? Food Security. 2019;11(5):1029–49.
Sandoval LA, Carpio CE, Garcia M. Comparison between experience-based and household-undernourishment food security indicators: a cautionary tale. Nutrients. 2020;12(11):3307.
Wichern J, van Wijk MT, Descheemaeker K, Frelat R, van Asten PJ, Giller KE. Food availability and livelihood strategies among rural households across Uganda. Food Secur. 2017;9(6):1385–403.
Islam A, Maitra C, Pakrashi D, Smyth R. Microcredit programme participation and household food security in rural Bangladesh. J Agric Econ. 2016;67(2):448–70.
Sileshi M, Kadigi R, Mutabazi K, Sieber S. Analysis of households’ vulnerability to food insecurity and its influencing factors in east Hararghe Ethiopia. J Econom Struct. 2019;8(1):1–17.
Ogutu SO, Gödecke T, Qaim M. Agricultural commercialisation and nutrition in smallholder farm households. J Agric Econ. 2020;71(2):534–55.
Sinyolo S, Mudhara M, Wale E. Water security and rural household food security: empirical evidence from the Mzinyathi district in South Africa. Food Security. 2014;6(4):483–99.
Arsenault JE, Hijmans RJ, Brown KH. Improving nutrition security through agriculture: an analytical framework based on national food balance sheets to estimate nutritional adequacy of food supplies. Food Secur. 2015;7(3):693–707.
Tambo JA, Uzayisenga B, Mugambi I, Bundi M. Do plant clinics improve household food security? Evidence from Rwanda. J Agric Econ. 2021;72(1):97–116.
Smith LC, Frankenberger TR. Does resilience capacity reduce the negative impact of shocks on household food security? Evidence from the 2014 floods in Northern Bangladesh. World Dev. 2018;102:358–76.
Bakhtsiyarava M, Williams TG, Verdin A, Guikema SD. A nonparametric analysis of household-level food insecurity and its determinant factors: exploratory study in Ethiopia and Nigeria. Food Security. 2021;13(1):55–70.
Bolarinwa OD, Ogundari K, Aromolaran AB. Intertemporal evaluation of household food security and its determinants: evidence from Rwanda. Food Security. 2020;12(1):179–89.
Islam AHMS, von Braun J, Thorne-Lyman AL, Ahmed AU. Farm diversification and food and nutrition security in Bangladesh: empirical evidence from nationally representative household panel data. Food Secur. 2018;10(3):701–20.
Ngome PIT, Shackleton C, Degrande A, Nossi EJ, Ngome F. Assessing household food insecurity experience in the context of deforestation in Cameroon. Food Policy. 2019;84:57–65.
Bühler D, Hartje R, Grote U. Matching food security and malnutrition indicators: evidence from Southeast Asia. Agric Econ. 2018;49(4):481–95.
Hjelm L, Mathiassen A, Wadhwa A. Measuring poverty for food security analysis: consumption-versus asset-based approaches. Food Nutr Bull. 2016;37(3):275–89.
Hossain M, Mullally C, Asadullah MN. Alternatives to calorie-based indicators of food security: an application of machine learning methods. Food Policy. 2019;84:77–91.
Maxwell D, Vaitla B, Coates J. How do indicators of household food insecurity measure up? An empirical comparison from Ethiopia. Food Policy. 2014;47:107–16.
Tuholske C, Andam K, Blekking J, Evans T, Caylor K. Comparing measures of urban food security in Accra, Ghana. Food Secur. 2020;12:1–15.
D’Souza A, Jolliffe D. Food insecurity in vulnerable populations: coping with food price shocks in Afghanistan. Am J Agr Econ. 2014;96(3):790–812.
Islam MM, Al Mamun MA. Beyond the risks to food availability–linking climatic hazard vulnerability with the food access of delta-dwelling households. Food Secur. 2020;12(1):37–58.
Lokosang LB, Ramroop S, Hendriks SL. Establishing a robust technique for monitoring and early warning of food insecurity in post-conflict South Sudan using ordinal logistic regression. Agrekon. 2011;50(4):101–30.
Vaitla B, Cissé JD, Upton J, Tesfay G, Abadi N, Maxwell D. How the choice of food security indicators affects the assessment of resilience—an example from northern Ethiopia. Food Secur. 2020;12(1):137–50.
Dibba L, Zeller M, Diagne A. The impact of new Rice for Africa (NERICA) adoption on household food security and health in the Gambia. Food Secur. 2017;9(5):929–44.
Lascano Galarza MX. Resilience to food insecurity: Theory and empirical evidence from international food assistance in Malawi. J Agric Econ. 2020;71(3):936–61.
Courtemanche C, Carden A, Zhou X, Ndirangu M. Do Walmart supercenters improve food security? Appl Econ Perspect Policy. 2019;41(2):177–98.
Romo-Aviles M, Ortiz-Hernández L. Energy and nutrient supply according to food insecurity severity among Mexican households. Food Security. 2018;10(5):1163–72.
Chege PM, Ndungu ZW, Gitonga BM. Food security and nutritional status of children under-five in households affected by HIV and AIDS in Kiandutu informal settlement, Kiambu County, Kenya. J Health Popul Nutr. 2016;35(1):1–8.
Hussein FM, Ahmed AY, Muhammed OS. Household food insecurity access scale and dietary diversity score as a proxy indicator of nutritional status among people living with HIV/AIDS, Bahir Dar, Ethiopia, 2017. PLoS ONE. 2018;13(6): e0199511.
Naser IA, Jalil R, Muda WMW, Nik WSW, Shariff ZM, Abdullah MR. Association between household food insecurity and nutritional outcomes among children in Northeastern of Peninsular Malaysia. Nurs Res Pract. 2014;8(3):304.
Upton JB, Cissé JD, Barrett CB. Food security as resilience: reconciling definition and measurement. Agric Econ. 2016;47(S1):135–47.
Nicholson CF, Stephens EC, Kopainsky B, Thornton PK, Jones AD, Parsons D, Garrett J. Food security outcomes in agricultural systems models: case examples and priority information needs. Agric Syst. 2021;188: 103030.
Ambikapathi R, Rothstein JD, Yori PP, Olortegui MP, Lee G, Kosek MN, Caulfield LE. Food purchase patterns indicative of household food access insecurity, children’s dietary diversity and intake, and nutritional status using a newly developed and validated tool in the Peruvian Amazon. Food Secur. 2018;10(4):999–1011.
Barrett CB, Constas MA. Toward a theory of resilience for international development applications. Proc Natl Acad Sci. 2014;111(40):14625–30.
Article CAS PubMed PubMed Central Google Scholar
Cissé, J.D. and Barrett, C.B. (2015). Estimating development resilience a conditional moments based approach Working Paper. Cornell University. Ithaca
Cissé JD, Barrett CB. Estimating development resilience: a conditional moments-based approach. J Dev Econ. 2018;135:272–84.
Berry EM, Dernini S, Burlingame B, Meybeck A, Conforti P. Food security and sustainability: can one exist without the other? Public Health Nutr. 2015;18(13):2293–302.
Clapp J, Moseley WG, Burlingame B, Termine P. The case for a six-dimensional food security framework. Food Policy. 2021;106:102164.
Guiné RDPF, Pato MLDJ, Costa CAD, Costa DDVTAD, Silva PBCD, Martinho VJPD. Food security and sustainability: discussing the four pillars to encompass other dimensions. Foods. 2021;10(11):2732.
Ericksen PJ. Conceptualizing food systems for global environmental change research. Glob Environ Chang. 2008;18(1):234–45.
FAO. Sustainable food systems concept and framework. 2021. Accessed 10 Nov 2021. http://www.fao.org/about/what-we-do/so4 .
Ingram J. A food systems approach to researching food security and its interactions with global environmental change. Food security. 2011;3(4):417–31.
Van Berkum S, Dengerink J, Ruben R. The food systems approach: sustainable solutions for a sufficient supply of healthy food. Wageningen: Wageningen Economic Research; 2018.
Wright BN, Tooze JA, Bailey RL, Liu Y, Rivera RL, McCormack L, Stluka S, Franzen-Castle L, Henne B, Mehrle D, Remley D. Dietary quality and usual intake of underconsumed nutrients and related food groups differ by food security status for rural, midwestern food pantry clients. J Acad Nutr Diet. 2020;120(9):1457–68.
Bickel G, Nord M, Price C, Hamilton W, Cook J. Guide to measuring household food security, revised 2000 [Online]. US Department of Agriculture, Food and Nutrition Service. 2000. Available: https://fnsprod.azureedge.net/sites/default/files/FSGuide.pdf . Accessed 31 Mar 2021.
Coates, Jennifer, Anne Swindale, Paula Bilinsky. Household Food Insecurity Access Scale (HFIAS) for Measurement of Household Food Access: Indicator Guide (v. 3). Washington, D.C.: FHI 360/FANTA. 2007.
FAO. Measurement and Assessment of Food Deprivation and Undernutrition. In: Proceedings of an International Symposium, FAO, Rome. 2003.
Download references
Acknowledgements
We are grateful to Maha AlDhaheri for the support at the initial stage of the literature searching and screening processes.
This study was funded by the Ministry of Education of the United Arab Emirates through the Collaborative Research Program Grant 2019, under the Resilient Agrifood Dynamism through evidence-based policies project [Grant Number: 1733833].
Author information
Authors and affiliations.
Faculty of Business, University of Wollongong in Dubai, Knowledge Park, 20183, Dubai, United Arab Emirates
Ioannis Manikas, Beshir M. Ali & Balan Sundarakani
You can also search for this author in PubMed Google Scholar
Contributions
Conceptualization, IM, BA and BS; methodology, IM, BA and BS; formal analysis, IM, BA and BS; investigation IM and BS; data curation, BA; writing—original draft preparation, IM, BA and BS; writing—review and editing, IM, BA and BS; visualization, BA; supervision, IM and BS; project administration, IM and BS; funding acquisition, IM and BS All authors have read and agreed to the published version of the manuscript. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Beshir M. Ali .
Ethics declarations
Ethics approval and consent to participate.
Not applicable.
Consent for publication
All authors provide their consent for publication.
Competing interests
The authors have no relevant financial or non-financial competing interests to disclose.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Additional file 1:.
Data and list of articles used in the systematic literature review on food security measurement (N = 78).
Additional file 2:
Table S1 . Summary of the publications that applied dietary diversity score indicators. Table S2 . Summary of the publications that used Food Consumption Score (FCS). Table S3 . Summary of the publications that used HFIAS and HHS. Table S4 . Summary of the publications that used HFSSM and ELCSA. Table S5 . Summary of the publications that used FIES.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
Manikas, I., Ali, B.M. & Sundarakani, B. A systematic literature review of indicators measuring food security. Agric & Food Secur 12 , 10 (2023). https://doi.org/10.1186/s40066-023-00415-7
Download citation
Received : 22 August 2022
Accepted : 01 March 2023
Published : 05 May 2023
DOI : https://doi.org/10.1186/s40066-023-00415-7
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Food insecurity
- Measurement
Agriculture & Food Security
ISSN: 2048-7010
- Submission enquiries: [email protected]
- General enquiries: [email protected]
Help | Advanced Search
Computer Science > Computation and Language
Title: text generation: a systematic literature review of tasks, evaluation, and challenges.
Abstract: Text generation has become more accessible than ever, and the increasing interest in these systems, especially those using large language models, has spurred an increasing number of related publications. We provide a systematic literature review comprising 244 selected papers between 2017 and 2024. This review categorizes works in text generation into five main tasks: open-ended text generation, summarization, translation, paraphrasing, and question answering. For each task, we review their relevant characteristics, sub-tasks, and specific challenges (e.g., missing datasets for multi-document summarization, coherence in story generation, and complex reasoning for question answering). Additionally, we assess current approaches for evaluating text generation systems and ascertain problems with current metrics. Our investigation shows nine prominent challenges common to all tasks and sub-tasks in recent text generation publications: bias, reasoning, hallucinations, misuse, privacy, interpretability, transparency, datasets, and computing. We provide a detailed analysis of these challenges, their potential solutions, and which gaps still require further engagement from the community. This systematic literature review targets two main audiences: early career researchers in natural language processing looking for an overview of the field and promising research directions, as well as experienced researchers seeking a detailed view of tasks, evaluation methodologies, open challenges, and recent mitigation strategies.
Submission history
Access paper:.
- HTML (experimental)
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .

IMAGES
VIDEO
COMMENTS
A Systematic Literature Review on the Cyber Security. 1 Dr.Yusuf Perwej, 2 Prof. (Dr.) Syed Qamar Abbas, 3 Jai Pratap Dixit, 4 Dr. Nikhat Akhtar, 5Anurag. Kumar Jaiswal. 1 Professor, Department of ...
In this survey, we conduct a comprehensive review of the literature on the application of LLMs in cybersecurity (LLM4Security). By comprehensively collecting over 30K relevant papers and systematically analyzing 127 papers from top security and software.
In an increasingly digital environment, operating systems have developed to prioritize speed, efficiency, and security in order to satisfy the needs of its users. The importance of operating system security increases as more sensitive data is stored digitally. The DICARe method is used to conduct a systematic literature review in this study. The DICARe stands for define, identify, classify ...
Therefore, a detailed and systematic literature review on "System Security Assurance" has been conducted in this paper. The motive of this paper is to study state-of-the-art, research trends, limitations, and future research directions in security assurance of the ICT and CPSs in a wide range of domains.
For the literature review, the authors used the keywords 'cyber', 'information threats' or 'vulnerability' in connection with the terms 'higher education, 'university' or 'academia'. A similar literature review with a focus on Internet of Things (IoT) cybersecurity was conducted by Lee et al. . The review revealed that ...
This systematic literature review examined articles on usable security from 2005 to 2022. A total of 55 research studies were selected after evaluation. The studies have been broadly categorized into four main clusters, each addressing different aspects: (1) usability of authentication methods, (2) helping security developers improve usability ...
5G wireless security by analyzing and reporting on the vari-ous security issues that affect the availability of information and the integrity of the network. Through our studies, we will also be able to identify new directions in the field. 1.1 Prior research The security of networks is a critical component of the
There has been a tremendous increase in research in the area of cyber security to support cyber applications and to avoid key security threats faced by these applications. The goal of this study is to identify and analyze the common cyber security vulnerabilities. To achieve this goal, a systematic mapping study was conducted, and in total, 78 primary studies were identified and analyzed ...
A systematic literature review is a systematic, explicit and comprehensive process to identify, evaluate and synthesise from results of works produced by researchers, scholars and practitioners. The literature review process has four stages before writing a review; planning, selection, extraction, and execution [6].
security risks that do not form part of the officially established information security spectrum. LITERATURE REVIEW Knowing and being ready is the first line of protection against cyber threats and cybercrimes, e.g. by information security training. Training can take two forms, the first is aimed at security professionals and aims to improve ...
View a PDF of the paper titled Large Language Models for Cyber Security: A Systematic Literature Review, by HanXiang Xu and 7 other authors View PDF HTML (experimental) Abstract: The rapid advancement of Large Language Models (LLMs) has opened up new opportunities for leveraging artificial intelligence in various domains, including cybersecurity.
This paper focuses on the literature review on scanning web vulnerabilities and solutions to mitigate web attacks. Vulnerability scanning methods will be reviewed as well as frameworks for improving web security. This research is the basis for future work that will end with the elaboration of web scanning and security with the aim of proposing ...
A Systematic Literature Review on the Cyber Security. 1Dr.Yusuf Perwej, 2Prof. (Dr.) Syed Qamar Abbas, 3Jai Pratap Dixit, 4Dr. Nikhat Akhtar,5Anurag Kumar Jaiswal. 1Professor, Department of Computer Science & Engineering, Ambalika Institute of Management and Technology, Lucknow, India.
A literature review of cybersecurity technologies through the lens of the IoT architecture helps us have a systematic and integrative view of the IoT cybersecurity. The following is based on Lee's five-layer architecture of enterprise IoT [1] and focuses on the layer-level cybersecurity issues and solutions. 2.1.1.
Information Security Awareness: Literature Review and Integrative Framework. Lennart Jaeger. Published in Hawaii International… 3 January 2018. Computer Science. TLDR. This study synthesizes the relationship between ISA and its antecedents and consequences and identifies consequences of ISA in terms of changes in beliefs, attitudes ...
A thorough examination of cyber security kinds, why cyber security is important, cyber security framework, cyberSecurity tools, and cyber security difficulties is conducted. In recent years, the Internet has become an integral element of people's everyday lifestyles all across the world. Online criminality, on the other hand, has risen in tandem with the growth of Internet activity. Cyber ...
Download Free PDF. View PDF. Cyber Security - Literature Review The issue of cyber security is not new but rather has developed more than a halfcentury. The arrest of an East German spy in IBM's German by West Germany's police in 1968 was acknowledged as the first case of cyber espionage (Warner, 2012, p. 784).
NCHRP 03-127 Task 1 - Security Literature Review and Efforts Report Cybersecurity of Traffic Management Systems Final January 12, 2018 Page 6 of 48 EXEUTIVE SUMMARY This document summarizes a variety of cybersecurity efforts applicable to the development of a state and local agency web based guidance tool and provides a fresh overview of ...
Measurement is critical for assessing and monitoring food security. Yet, it is difficult to comprehend which food security dimensions, components, and levels the numerous available indicators reflect. We thus conducted a systematic literature review to analyse the scientific evidence on these indicators to comprehend the food security dimensions and components covered, intended purpose, level ...
The past review works have discussed industrial control systems attacks, their impact, and exploited vulnerabilities separately and lack comprehension. In this work, an attempt has been made to understand the comprehensive picture of vulnerabilities, attacks, and their impact on industrial control systems.
Sudeshna Maitra for their support in literature review and analysis. We are further grateful to the tremendous support and technical assistance of UNICEF India colleagues in New Delhi, Lucknow and Patna offices, and to all UNICEF colleagues who provided review and valuable feedback on earlier drafts of this working paper.
In this paper, we conducted a systematic literature review (SLR) of cybersecurity for 5G and beyond-enabled IoT. By developing a taxonomy to classify and characterize existing research, we ...
View PDF HTML (experimental) Abstract: Text generation has become more accessible than ever, and the increasing interest in these systems, especially those using large language models, has spurred an increasing number of related publications. We provide a systematic literature review comprising 244 selected papers between 2017 and 2024. This review categorizes works in text generation into ...
• Makes periodic checks of boiler rooms, security lighting, mess hall freezers and other areas as directed. • Performs inspections and operator maintenance on all assigned vehicles and equipment in an effective and safe manner when required. • Dispatches security personnel to scenes of incidents and irregularities.