IEEE.org | IEEE Xplore Digital Library | IEEE Standards | IEEE Spectrum | More Sites


Regular Papers
Volume 109, Issue 7
Scanning the Issue
6g wireless systems: vision, requirements, challenges, insights, and opportunities.
By H. Tataria, M. Shafi, A. F. Molisch, M. Dohler, H. Sjöland, and F. Tufvesson
This article aims to provide a holistic top-down view of sixth-generation wireless system design and proposes fundamental changes that are required in the core networks of the future.
New Trends in Stochastic Geometry for Wireless Networks: A Tutorial and Survey
By Y. Hmamouche, M. Benjillali, S. Saoudi, H. Yanikomeroglu, and M. Di Renzo
This article reviews novel stochastic geometric models and techniques developed during the last decade for the evaluation of wireless networks.
Wide Bandgap DC–DC Converter Topologies for Power Applications
By M. Parvez, A. T. Pereira, N. Ertugrul, N. H. E. Weste, D. Abbott, and S. F. Al-Sarawi
This article reviews new WBG architectures and new WBG semiconductor technologies, with respect to their application in the field of power electronics.
Point of View
Swarm robotics: past, present, and future.
By M. Dorigo, G. Theraulaz, and V. Trianni

11 Comments
- Pingback: สล็อต PG เว็บตรง แตกหนัก 2023
- Pingback: AE Gaming โหมดพิเศษสำหรับเกม บาคาร่า 2024
- Pingback: สล็อตเว็บตรง
- Pingback: ชั้นวางสินค้าอุตสาหกรรม
- Pingback: psilocybin mushroom shop
- Pingback: ปัง ปัง สล็อต
- Pingback: เลสิค
- Pingback: ติดตั้ง ais fiber
- Pingback: ข่าวบอล
- Pingback: ทะเบียนสวย
- Pingback: trustbet
Comments are closed.
- IEEE Xplore Digital Library
- IEEE Standards
- IEEE Spectrum Online
- More IEEE Sites

Accepted Paper List [Main Conference]
List of Accepted Papers in IEEE INFOCOM 2021 Main Conference
- 6GAN: IPv6 Multi-Pattern Target Generation via Generative Adversarial Nets with Reinforcement Learning
Tianyu Cui (Institute of Information Engineering, University of Chinese Academy of Sciences, China); Gaopeng Gou (Institute of Information EngineeringChinese Academy of Sciences, China); Gang Xiong, Chang Liu, Peipei Fu and Zhen Li (Institute of Information Engineering, Chinese Academy of Sciences, China)
- 6Hit: A Reinforcement Learning-based Approach to Target Generation for Internet-wide IPv6 Scanning
Bingnan Hou and Zhiping Cai (National University of Defense Technology, China); Kui Wu (University of Victoria, Canada); Jinshu Su (National University of Defence Technology, China); Yinqiao Xiong (National University of Defense Technology, China)
- 802.11ad in Smartphones: Energy Efficiency, Spatial Reuse, and Impact on Applications
Shivang Aggarwal (University at Buffalo, SUNY, USA); Moinak Ghoshal (Universiy at Buffalo, SUNY, NY, Buffalo, USA); Piyali Banerjee (University at Buffalo, USA); Dimitrios Koutsonikolas (University at Buffalo, SUNY, USA); Joerg Widmer (IMDEA Networks Institute, Spain)
- A Deep-Learning-based Link Adaptation Design for eMBB/URLLC Multiplexing in 5G NR
Yan Huang, Thomas Hou and Wenjing Lou (Virginia Tech, USA)
- A Fast-Convergence Routing of the Hot-Potato
Jean-Romain Luttringer and Quentin Bramas (University of Strasbourg, France); Cristel Pelsser (University of Strasbourg); Pascal Mérindol (Université de Strasbourg, France)
- A Lightweight Integrity Authentication Approach for RFID-enabled Supply Chains
Xin Xie (Hong Kong Polytechnic University, Hong Kong); Xiulong Liu (Tianjin University, China); Song Guo (Hong Kong Polytechnic University, Hong Kong); Heng Qi (Dalian University of Technology, China); Keqiu Li (Tianjin University, China)
- A Measurement-Based Study of the Privacy of Europe's Covid-19 Contact Tracing Apps
Douglas Leith and Stephen Farrell (Trinity College Dublin, Ireland)
- A Sum-of-Ratios Multi-Dimensional-Knapsack Decomposition for DNN Resource Scheduling
Menglu Yu (Iowa State University, USA); Chuan Wu (The University of Hong Kong, Hong Kong); Bo Ji (Virginia Tech, USA); Jia Liu (The Ohio State University, USA)
- A Universal Transcoding and Transmission Method for Livecast with Networked Multi-Agent Reinforcement Learning
Xingyan Chen and Changqiao Xu (Beijing University of Posts and Telecommunications, China); Mu Wang (State Key Laboratory of Networking and Switching Technology, China); Zhonghui Wu and Shujie Yang (Beijing University of Posts and Telecommunications, China); Lujie Zhong (Capital Normal University, China); Gabriel-Miro Muntean (Dublin City University, Ireland)
- A Weak Consensus Algorithm and Its Application to High-Performance Blockchain
Qin Wang (Swinburne University of Technology & CSIRO Data61, Australia); Rujia Li (University of Birmingham, United Kingdom (Great Britain))
- A Worst-Case Approximate Analysis of Peak Age-of-Information Via Robust Queueing Approach
Zhongdong Liu (Virginia Tech, USA); Yu Sang (Temple University, USA); Bin Li (University of Rhode Island, USA); Bo Ji (Virginia Tech, USA)
- Accelerating LSH-based Distributed Search with In-network Computation
Penghao Zhang, Heng Pan and Zhenyu Li (Institute of Computing Technology, Chinese Academy of Sciences, China); Peng He (Institute of Computing Technology Chinese Academy of Sciences, China); Zhibin Zhang (Institute of Computing Technology, Chinese Academy of Sciences, China); Gareth Tyson (Queen Mary, University of London, United Kingdom (Great Britain)); Gaogang Xie (Computer Network Information Center, Chinese Academy of Science, China)
- AdaPDP: Adaptive Personalized Differential Privacy
Ben Niu (Institute of Information Engineering, Chinese Academy of Sciences, China); Yahong Chen (Institute of Information Engineering, CAS & School of Cyber Security, UCAS, China); Boyang Wang (University of Cincinnati, USA); Zhibo Wang (Wuhan University, China); Fenghua Li (Institute of Information Engineering, CAS & School of Cyber Security, UCAS, China); Jin Cao (Xidian University, China)
- Adaptive Batch Update in TCAM: How Collective Optimization Beats Individual Ones
Ying Wan (Tsinghua University, China); Haoyu Song (Futurewei Technologies, USA); Yang Xu (Fudan University, China); Chuwen Zhang (Tsinghua University, China); Yi Wang (Southern University of Science and Technology, China); Bin Liu (Tsinghua University, China)
- Adaptive Clustering-based Malicious Traffic Classification at the Network Edge
Alec F Diallo (The University of Edinburgh, United Kingdom (Great Britain)); Paul Patras (University of Edinburgh, United Kingdom (Great Britain))
- Age of Information in Random Access Networks with Stochastic Arrivals
Igor Kadota (Columbia University, USA); Eytan Modiano (MIT, USA)
- Age-Dependent Distributed MAC for Ultra-Dense Wireless Networks
Dheeraj Narasimha (Arizona State University, USA); Srinivas G Shakkottai (Texas A&M University, USA); Lei Ying (University of Michigan, USA)
- Aion: A Bandwidth Optimized Scheduler with AoI Guarantee
Qingyu Liu, Chengzhang Li, Thomas Hou and Wenjing Lou (Virginia Tech, USA); Sastry Kompella (Naval Research Laboratory, USA)
- AMIS: Edge Computing Based Adaptive Mobile Video Streaming
Phil K Mu, Jinkai Zheng, Tom H. Luan and Lina Zhu (Xidian University, China); Mianxiong Dong (Muroran Institute of Technology, Japan); Zhou Su (Shanghai University, China)
- AMT: Acoustic Multi-target Tracking with Smartphone MIMO System
Chao Liu, Penghao Wang and Ruobing Jiang (Ocean University of China, China); Yanmin Zhu (Shanghai Jiao Tong University, China)
- An Experience Driven Design for IEEE 802.11ac Rate Adaptation based on Reinforcement Learning
Syuan-Cheng Chen, Chi-Yu Li and Chui-Hao Chiu (National Chiao Tung University, Taiwan)
- An Incentive Mechanism for Cross-Silo Federated Learning: A Public Goods Perspective
Ming Tang and Vincent W.S. Wong (University of British Columbia, Canada)
- Analyzing Age of Information in Multiaccess Networks by Fluid Limits
Zhiyuan Jiang (Shanghai University, China)
- Analyzing Learning-Based Networked Systems with Formal Verification
Arnaud Dethise and Marco Canini (KAUST, Saudi Arabia); Nina Narodytska (VMware Research Group, USA)
- Asynchronous Deep Reinforcement Learning for Data-Driven Task Offloading in MEC-Empowered Vehicular Networks
Penglin Dai, Kaiwen Hu, Xiao Wu and Huanlai Xing (Southwest Jiaotong University, China); Zhaofei Yu (Peking University, China)
- Attack Resilience of Cache Replacement Policies
Tian Xie (Pennsylvania State University, USA); Ting He (Penn State University, USA); Patrick McDaniel and Namitha Nambiar (Pennsylvania State University, USA)
- Auction-Based Combinatorial Multi-Armed Bandit Mechanisms with Strategic Arms
Guoju Gao and He Huang (Soochow University, China); Mingjun Xiao (University of Science and Technology of China, China); Jie Wu (Temple University, USA); Yu-e Sun (Soochow University, China); Sheng Zhang (Nanjing University, China)
- AutoML for Video Analytics with Edge Computing
Apostolos Galanopoulos, Jose A. Ayala-Romero and Douglas Leith (Trinity College Dublin, Ireland); George Iosifidis (Delft University of Technology, The Netherlands)
- AWash: Handwashing Assistance for the Elderly With Dementia via Wearables
Yetong Cao, Huijie Chen, Fan Li and Song Yang (Beijing Institute of Technology, China); Yu Wang (Temple University, USA)
- Bandit Learning with Predicted Context: Regret Analysis and Selective Context Query
Jianyi Yang and Shaolei Ren (University of California, Riverside, USA)
- Bandwidth Isolation Guarantee for SDN Virtual Networks
Gyeongsik Yang, Yeonho Yoo and Minkoo Kang (Korea University, Korea (South)); Heesang Jin (ETRI, Korea (South)); Chuck Yoo (Korea University, Korea (South))
- Bayesian Online Learning for Energy-Aware Resource Orchestration in Virtualized RANs
Jose A. Ayala-Romero (Trinity College Dublin, Ireland); Andres Garcia-Saavedra (NEC Labs Europe, Germany); Xavier Costa-Perez (NEC Laboratories Europe, Germany); George Iosifidis (Delft University of Technology, The Netherlands)
- Beyond Value Perturbation: Local Differential Privacy in the Temporal Setting
Qingqing Ye (The Hong Kong Polytechnic University, Hong Kong); Haibo Hu (Hong Kong Polytechnic University, Hong Kong); Ninghui Li (Purdue University, USA); Meng Xiaofeng (Renmin University of China, USA); Huadi Zheng and Haotian Yan (The Hong Kong Polytechnic University, Hong Kong)
- Bipartite Graph Matching Based Secret Key Generation
Hongbo Liu (University of Electronic Science and Technology of China, China); Yan Wang (Temple University, USA); Yanzhi Ren (University of Electronic Science and Technology of China, China); Yingying Chen (Rutgers University, USA)
- BlendVLC: A Cell-free VLC Network Architecture Empowered by Beamspot Blending
Jona Beysens (KU Leuven, Belgium); Qing Wang (Delft University of Technology, The Netherlands); Maxim Van den Abeele and Sofie Pollin (KU Leuven, Belgium)
- BLESS: BLE-aided Swift Wi-Fi Scanning in Multi-protocol IoT Networks
Wonbin Park (SNU, Korea (South)); Dokyun Ryoo (Seoul National University, Korea (South)); Changhee Joo (Korea University, Korea (South)); Saewoong Bahk (Seoul National University, Korea (South))
- Blind Optimal User Association in Small-Cell Networks
Livia E. Chatzieleftheriou (Athens University of Economics and Business, Greece); Apostolos Destounis (Huawei Technologies France Research Center, France); Georgios Paschos (Amazon, Luxembourg); Iordanis Koutsopoulos (Athens University of Economics and Business, Greece)
- Bound Inference and Reinforcement Learning-based Path Construction in Bandwidth Tomography
Cuiying Feng, Jianwei An and Kui Wu (University of Victoria, Canada); Jianping Wang (City University of Hong Kong, Hong Kong)
- Bringing Fairness to Actor-Critic Reinforcement Learning for Network Utility Optimization
Jingdi Chen and Yimeng Wang (The George Washington University, USA); Tian Lan (George Washington University, USA)
- Camel: Context-Aware Magnetic MIMO Wireless Power Transfer with In-band Communication
Hao Zhou, Zhao Chen, Wangqiu Zhou, Haisheng Tan, Panlong Yang and Xiang-Yang Li (University of Science and Technology of China, China)
- Can You Fix My Neural Network? Real-Time Adaptive Waveform Synthesis for Resilient Wireless Signal Classification
Salvatore D'Oro, Francesco Restuccia and Tommaso Melodia (Northeastern University, USA)
- CanalScan: Tongue-Jaw Movement Recognition via Ear Canal Deformation Sensing
Yetong Cao, Huijie Chen and Fan Li (Beijing Institute of Technology, China); Yu Wang (Temple University, USA)
- Characterizing Ethereum's Mining Power Decentralization at a Deeper Level
Liyi Zeng (Tsinghua University, China); Yang Chen (Microsoft Research Asia, China); Shuo Chen (Microsoft Research, USA); Xian Zhang and Zhongxin Guo (Microsoft Research Asia, China); Wei Xu (Tsinghua University, China); Thomas Moscibroda (Microsoft Research, USA)
- Cocktail Edge Caching: Ride Dynamic Trends of Content Popularity with Ensemble Learning
Tongyu Zong, Chen Li, Yuanyuan Lei and Guangyu Li (New York University, USA); Houwei Cao (New York Institute of Technology, USA); Yong Liu (New York University, USA)
- Code is the (F)Law: Demystifying and Mitigating Blockchain Inconsistency Attacks Caused by Software Bugs
Guorui Yu (Peking University, China); Shibin Zhao (State Key Laboratory of Mathematical Engineering and Advanced Computing, China); Chao Zhang (Institute for Network Sciences and Cyberspace, Tsinghua University, China); Zhiniang Peng (Qihoo 360 Core Security, China); Yuandong Ni (Institute for Network Science and Cyberspace of Tsinghua University, China); Xinhui Han (Peking University, China)
- Coexistence of Wi-Fi 6E and 5G NR-U: Can We Do Better in the 6 GHz Bands?
Gaurang Naik and Jung-Min (Jerry) Park (Virginia Tech, USA)
- Combining Regularization with Look-Ahead for Competitive Online Convex Optimization
Ming Shi and Xiaojun Lin (Purdue University, USA); Lei Jiao (University of Oregon, USA)
- Comparison of Decentralized and Centralized Update Paradigms for Remote Tracking of Distributed Dynamic Sources
Sunjung Kang and Atilla Eryilmaz (The Ohio State University, USA); Changhee Joo (Korea University, Korea (South))
- Competing Epidemics on Graphs - Global Convergence and Coexistence
Vishwaraj Doshi, Shailaja Mallick and Do Young Eun (North Carolina State University, USA)
- Context-aware Website Fingerprinting over Encrypted Proxies
Xiaobo Ma, Mawei Shi, Bingyu An and Jianfeng Li (Xi'an Jiaotong University, China); Daniel Xiapu Luo (The Hong Kong Polytechnic University, Hong Kong); Junjie Zhang (Wright State University, USA); Xiaohong Guan (Xi’an Jiaotong University & Tsinghua University, China)
- Cost-Driven Data Caching in the Cloud: An Algorithmic Approach
Yang Wang (Shenzhen Institute of Advanced Technology, China); Yong Zhang (SIAT, CAS, China); Xinxin Han and Pengfei Wang (Shenzhen Institutes of Advanced Technology, China); Cheng-Zhong Xu (University of Macau, China); Joseph Horton (University of New Brunswick, Canada); Joseph Culberson (University of Alberta, Canada)
- Cost-Effective Federated Learning Design
Bing Luo (Shenzhen Institute of Artificial Intelligence and Robotics for Society & The Chinese University of Hong Kong, Shenzhen, China); Xiang Li (The Chinese University of Hong Kong, Shenzhen, China); Shiqiang Wang (IBM T. J. Watson Research Center, USA); Jianwei Huang (The Chinese University of Hong Kong, Shenzhen, China); Leandros Tassiulas (Yale University, USA)
- Counter-Collusion Smart Contracts for Watchtowers in Payment Channel Networks
Yuhui Zhang and Dejun Yang (Colorado School of Mines, USA); Guoliang Xue (Arizona State University, USA); Ruozhou Yu (North Carolina State University, USA)
- Crowdsourcing System for Numerical Tasks based on Latent Topic Aware Worker Reliability
Zhuan Shi, Shanyang Jiang and Lan Zhang (University of Science and Technology of China, China); Yang Du (Soochow University, China); Xiang-Yang Li (University of Science and Technology of China, China)
- CryptoEyes: Privacy Preserving Classification over Encrypted Images
Wenbo He, Shusheng Li and Wenbo Wang (McMaster University, Canada); Muheng Wei and Bohua Qiu (ZhenDui Industry Artificial Intelligence Co, Ltd, China)
- CTF: Anomaly Detection in High-Dimensional Time Series with Coarse-to-Fine Model Transfer
Ming Sun and Ya Su (Tsinghua University, China); Shenglin Zhang, Yuanpu Cao and Yuqing Liu (Nankai University, China); Dan Pei and Wenfei Wu (Tsinghua University, China); Yongsu Zhang, Xiaozhou Liu and Junliang Tang (ByteDance, China)
- DC2: Delay-aware Compression Control for Distributed Machine Learning
Ahmed M. Abdelmoniem and Marco Canini (KAUST, Saudi Arabia)
- De-anonymizing Social Networks Under Partial Overlap: An F-score Based Approach
Jiapeng Zhang and Luoyi Fu (Shanghai Jiao Tong University, China); Xinbing Wang (Shanghai Jiaotong University, China); Guihai Chen (Shanghai Jiao Tong University, China)
- DeepLoRa: Learning Accurate Path Loss Model for Long Distance Links in LPWAN
Li Liu, Yuguang Yao, Zhichao Cao and Mi Zhang (Michigan State University, USA)
- DeepReserve: Dynamic Edge Server Reservation for Connected Vehicles with Deep Reinforcement Learning
Jiawei Zhang, Suhong Chen and Xudong Wang (Shanghai Jiao Tong University, China); Yifei Zhu (Simon Fraser University, Canada)
- DeepSense: Fast Wideband Spectrum Sensing Through Real-Time In-the-Loop Deep Learning
Daniel Uvaydov, Salvatore D'Oro, Francesco Restuccia and Tommaso Melodia (Northeastern University, USA)
- Delay-Tolerant Constrained OCO with Application to Network Resource Allocation
Juncheng Wang and Ben Liang (University of Toronto, Canada); Min Dong (Ontario Tech University, Canada); Gary Boudreau and Hatem Abou-zeid (Ericsson, Canada)
- Detecting Localized Adversarial Examples: A Generic Approach using Critical Region Analysis
Fengting Li, Xuankai Liu, XiaoLi Zhang and Qi Li (Tsinghua University, China); Kun Sun (George Mason University, USA); Kang Li (University of Georgia, USA)
- Device Sampling for Heterogeneous Federated Learning: Theory, Algorithms, and Implementation
Su Wang (Purdue University, USA); Mengyuan Lee (Zhejiang University, China); Seyyedali Hosseinalipour (Purdue University, USA); Roberto Morabito (Ericsson Research & Princeton University, Finland); Mung Chiang (Purdue University, USA); Christopher G. Brinton (Purdue University & Zoomi Inc., USA)
- Distributed Neighbor Distribution Estimation with Adaptive Compressive Sensing in VANETs
Yunxiang Cai, Hongzi Zhu and Xiao Wang (Shanghai Jiao Tong University, China); Shan Chang (Donghua University, China); Jiangang Shen and Minyi Guo (Shanghai Jiao Tong University, China)
- Privacy Preserving and Resilient RPKI
Kris Shrishak (Technische Universität Darmstadt, Germany); Haya Shulman (Fraunhofer SIT, Germany)
- Distributed Threshold-based Offloading for Large-Scale Mobile Cloud Computing
Xudong Qin and Bin Li (University of Rhode Island, USA); Lei Ying (University of Michigan, USA)
- DRL-OR: Deep Reinforcement Learning-based Online Routing for Multi-type Service Requirements
Chenyi Liu, Mingwei Xu, Yuan Yang and Nan Geng (Tsinghua University, China)
- Dual Attention-Based Federated Learning for Wireless Traffic Prediction
Chuanting Zhang and Shuping Dang (King Abdullah University of Science and Technology, Saudi Arabia); Basem Shihada (KAUST, Saudi Arabia); Mohamed-Slim Alouini (King Abdullah University of Science and Technology (KAUST), Saudi Arabia)
- DyLoc: Dynamic Localization for Massive MIMO Using Predictive Recurrent Neural Networks
Farzam Hejazi, Katarina Vuckovic and Nazanin Rahnavard (University of Central Florida, USA)
- Dynamically Choosing the Candidate Algorithm with Ostasos in Online Optimization
Weirong Chen, Jiaqi Zheng and Haoyu Yu (Nanjing University, China)
- ECLAT: An ECN Marking System for Latency Guarantee in Cellular Networks
Junseon Kim (Ulsan National Institute of Science and Technology (UNIST), Korea (South)); Youngbin Im (Ulsan National Institute of Science and Technology, Korea (South)); Kyunghan Lee (Seoul National University, Korea (South))
- Edge-assisted Online On-device Object Detection for Real-time Video Analytics
Mengxi Hanyao, Yibo Jin, Zhuzhong Qian, Sheng Zhang and Sanglu Lu (Nanjing University, China)
- EdgeDuet: Tiling Small Object Detection for Edge Assisted Autonomous Mobile Vision
Xu Wang, Zheng Yang, Jiahang Wu and Yi Zhao (Tsinghua University, China); Zimu Zhou (Singapore Management University, Singapore)
- EdgeSharing: Edge Assisted Real-time Localization and Object Sharing in Urban Streets
Luyang Liu (Google Research, USA); Marco Gruteser (WINLAB / Rutgers University, USA)
- Efficient and Verifiable Proof of Replication with Fast Fault Localization
Haoran Yuan and Xiaofeng Chen (Xidian University, China); Guowen Xu (University of Electronic Science and Technology of China, China); Jianting Ning (Singapore Management University, China); Joseph Liu (Monash University, Australia); Robert Deng (Singapore Management University, Singapore)
- Efficient Association of Wi-Fi Probe Requests under MAC Address Randomization
Jiajie Tan and S.-H. Gary Chan (The Hong Kong University of Science and Technology, China)
- Efficient Learning-based Scheduling for Information Freshness in Wireless Networks
Bin Li (University of Rhode Island, USA)
- Enabling Edge-Cloud Video Analytics for Robotics Applications
Yiding Wang and Weiyan Wang (Hong Kong University of Science and Technology, Hong Kong); Duowen Liu (Hong Kong University of Science & Technology, Hong Kong); Xin Jin (Johns Hopkins University, USA); Junchen Jiang (University of Chicago, USA); Kai Chen (Hong Kong University of Science and Technology, China)
- Energy-Efficient Orchestration of Metro-Scale 5G Radio Access Networks
Rajkarn Singh (University of Edinburgh, United Kingdom (Great Britain)); Cengis Hasan (University of Luxembourg & Interdisciplinary Centre for Security, Reliability and Trust (SNT), Luxembourg); Xenofon Foukas (Microsoft Research, United Kingdom (Great Britain)); Marco Fiore (IMDEA Networks Institute, Spain); Mahesh K Marina (The University of Edinburgh, United Kingdom (Great Britain)); Yue Wang (Samsung Electronics, USA)
- Enhanced Flooding-Based Routing Protocol for Swarm UAV Networks: Random Network Coding Meets Clustering
Hao Song, Lingjia Liu and Bodong Shang (Virginia Tech, USA); Scott M Pudlewski (Georgia Tech Research Institute, USA); Elizabeth Serena Bentley (AFRL, USA)
- Expectile Tensor Completion to Recover Skewed Network Monitoring Data
Kun Xie and Siqi Li (Hunan University, China); Xin Wang (Stony Brook University, USA); Gaogang Xie (Institute of Computing Technology, Chinese Academy of Sciences, China); Yudian Ouyang (Hunan University, China)
- Experimental UAV Data Traffic Modeling and Network Performance Analysis
Aygün Baltaci (Airbus & Technical University of Munich, Germany); Markus Klügel, Fabien Geyer and Svetoslav Duhovnikov (Airbus, Germany); Vaibhav Bajpai and Jörg Ott (Technische Universität München, Germany); Dominic A. Schupke (Airbus, Germany)
- Exploiting Simultaneous Communications to Accelerate Data Parallel Distributed Deep Learning
Shaohuai Shi (The Hong Kong University of Science and Technology, Hong Kong); Xiaowen Chu (Hong Kong Baptist University, Hong Kong); Bo Li (Hong Kong University of Science and Technology, Hong Kong)
- Exploring Layered Container Structure for Cost Efficient Microservice Deployment
Lin Gu (Huazhong University of Science and Technology, China); Deze Zeng (China University of Geosciences, China); Jie Hu and Hai Jin (Huazhong University of Science and Technology, China); Song Guo (Hong Kong Polytechnic University, Hong Kong); Albert Zomaya (The University of Sydney, Australia)
- Failure Localization through Progressive Network Tomography
Viviana Arrigoni (Sapienza, University of Rome, Italy); Novella Bartolini (Sapienza University of Rome, Italy); Annalisa Massini (Sapienza Università di Roma, Italy); Federico Trombetti (Sapienza, University of Rome, Italy)
- FAIR: Quality-Aware Federated Learning with Precise User Incentive and Model Aggregation
Yongheng Deng (Tsinghua University, China); Feng Lyu and Ju Ren (Central South University, China); Yi-Chao Chen (Shanghai Jiao Tong University, China); Peng Yang (Huazhong University of Science and Technology, China); Yuezhi Zhou and Yaoxue Zhang (Tsinghua University, China)
- Fault-Tolerant Energy Management for Real-Time Systems with Weakly Hard QoS Assurance
Linwei Niu (Howard University, USA)
- Federated Learning over Wireless Networks: A Band-limited Coordinated Descent Approach
Junshan Zhang (Arizona State University, USA); Na Li (Harvard University, USA); Mehmet Dedeoglu (Arizona State University, USA)
- FedSens: A Federated Learning Approach for Smart Health Sensing with Class Imbalance in Resource Constrained Edge Computing
Daniel Zhang, Ziyi Kou and Dong Wang (University of Notre Dame, USA)
- FedServing: A Federated Prediction Serving Framework Based on Incentive Mechanism
Jia Si Weng, Jian Weng and Hongwei Huang (Jinan University, China); Chengjun Cai and Cong Wang (City University of Hong Kong, Hong Kong)
- Finding Critical Files from a Packet
JunNyung Hur, Hahoon Jeon, Hyeon gy Shon, Young Jae Kim and MyungKeun Yoon (Kookmin University, Korea (South))
- First-Order Efficient General-Purpose Clean-label Data Poisoning
Tianhang Zheng and Baochun Li (University of Toronto, Canada)
- Fix with P6: Verifying Programmable Switches at Runtime
Apoorv Shukla (Huawei Munich Research Center, Germany); Kevin Hudemann (SAP, Germany); Zsolt Vági (SWISSCOM, Switzerland); Lily Hügerich (TU Berlin, Germany); Georgios Smaragdakis (TU Berlin and Max Planck Institute for Informatics, Germany); Artur Hecker (Huawei, Germany); Stefan Schmid (University of Vienna, Austria); Anja Feldmann (Max Planck Institute for Informatics & Saarland Informatics Campus / TU Berlin, Germany)
- Flow Algebra: Towards an Efficient, Unifying Framework for Network Management Tasks
Christopher Leet, Robert Soulé and Y. Richard Yang (Yale University, USA); Ying Zhang (Facebook, USA)
- Fresh Caching for Dynamic Content
Bahman Abolhassani (The Ohio State University, USA); John Tadrous (Gonzaga University, USA); Atilla Eryilmaz (The Ohio State University, USA); Edmund Yeh (Northeastern University, USA)
- Going the Extra Mile with Disaster-Aware Network Augmentation
Jorik Oostenbrink (TU Delft, The Netherlands); Fernando A. Kuipers (Delft University of Technology, The Netherlands)
- GOLDIE: Harmonization and Orchestration Towards a Global Directory for IoT
Luoyao Hao and Henning Schulzrinne (Columbia University, USA)
- GPU-Ether: GPU-native packet I/O for GPU applications on commodity Ethernet
Changue Jung, Suhwan Kim, Ikjun Yeom and Honguk Woo (Sungkyunkwan University, Korea (South)); Younghoon Kim (SungKyunKwan University, Korea (South))
- GRADES: Gradient Descent for Similarity Caching
Anirudh Sabnis (University of Massachusetts Amherst, USA); Tareq Si Salem and Giovanni Neglia (Inria, France); Michele Garetto (Università di Torino, Italy); Emilio Leonardi (Politecnico di Torino, Italy); Ramesh K Sitaraman (University of Massachusetts, Amherst & Akamai Technologies, USA)
- Grafting Arborescences for Extra Resilience of Fast Rerouting Schemes
Klaus-Tycho Foerster (University of Vienna, Austria); Andrzej Kamisiński (AGH University of Science and Technology, Poland); Yvonne-Anne Pignolet (DFINITY, Switzerland); Stefan Schmid (University of Vienna, Austria); Gilles Tredan (LAAS-CNRS, France)
- HAVS: Hardware-accelerated Shared-memory-based VPP Network Stack
Shujun Zhuang and Jian Zhao (ShangHaiJiaoTong University, China); Jian Li (Shanghai Jiao Tong University, China); Ping Yu and Yuwei Zhang (Intel, China); Haibing Guan (Shanghai Jiao Tong University, China)
- HearFit: Fitness Monitoring on Smart Speakers via Active Acoustic Sensing
Yadong Xie, Fan Li and Yue Wu (Beijing Institute of Technology, China); Yu Wang (Temple University, USA)
- Heuristic Algorithms for Co-scheduling of Edge Analytics and Routes for UAV Fleet Missions
Aakash Khochare and Yogesh Simmhan (Indian Institute of Science, India); Francesco Betti Sorbelli (Missouri Science and Technology, USA); Sajal K. Das (Missouri University of Science and Technology, USA)
- INCdeep: Intelligent Network Coding with Deep Reinforcement Learning
Qi Wang (Institute of Computing Technology, Chinese Academy of Sciences, China); Jianmin Liu (Institute of Computing Technology Chinese Academy of Sciences, China); Katia Jaffrès-Runser (University of Toulouse - Toulouse INP & IRIT Laboratory, France); Yongqing Wang, ChenTao He, Cunzhuang Liu and Yongjun Xu (Institute of Computing Technology, Chinese Academy of Sciences, China)
- Incentive Mechanism Design for Distributed Coded Machine Learning
Ningning Ding (The Chinese University of Hong Kong, Hong Kong); Zhixuan Fang (Tsinghua University, China); Lingjie Duan (Singapore University of Technology and Design (SUTD), Singapore); Jianwei Huang (The Chinese University of Hong Kong, Shenzhen, China)
- Individual Load Forecasting for Multi-Customers with Distribution-aware Temporal Pooling
Eunju Yang and Chan-Hyun Youn (Korea Advanced Institute of Science and Technology, Korea (South))
- INT-label: Lightweight In-band Network-Wide Telemetry via Interval-based Distributed Labelling
Enge Song, Tian Pan and Chenhao Jia (Beijing University of Posts and Telecommunications, China); Wendi Cao (Peking University, China); Jiao Zhang, Tao Huang and Yunjie Liu (Beijing University of Posts and Telecommunications, China)
- Invisible Poison: A Blackbox Clean Label Backdoor Attack to Deep Neural Networks
Rui Ning, Jiang Li, ChunSheng Xin and Hongyi Wu (Old Dominion University, USA)
- ITE: A Structural Entropy Based Approach for Source Detection
Chong Zhang, Qiang Guo, Luoyi Fu and Xiaoying Gan (Shanghai Jiao Tong University, China); Xinbing Wang (Shanghai Jiaotong University, China)
- Jamming of LoRa PHY and Countermeasure
Ningning Hou (The Hong Kong Polytechnique University, Hong Kong); Xianjin Xia and Yuanqing Zheng (The Hong Kong Polytechnic University, Hong Kong)
- Jellyfish: Locality-sensitive Subflow Sketching
Yongquan Fu (National University of Defense Technology, China); Lun An (Beijing University of Posts and Telecommunications, China); Siqi Shen (Xiamen University, China); Kai Chen (Hong Kong University of Science and Technology, China); Pere Barlet-Ros (Universitat Politècnica de Catalunya, Spain)
- Joint Age of Information and Self Risk Assessment for Safer 802.11p based V2V Networks
Biplav Choudhury (Virginia Tech, USA); Vijay K. Shah (Virginia Tech & Wireless@VT Lab, USA); Avik Dayal and Jeffrey Reed (Virginia Tech, USA)
- Joint Cache Size Scaling and Replacement Adaptation for Small Content Providers
Jiahui Ye, Zichun Li, Zhi Wang and Zhuobin Zheng (Tsinghua University, China); Han Hu (Beijing Institute of Technology, China); Wenwu Zhu (Tsinghua University, China)
- Launching Smart Selective Jamming Attacks in WirelessHART Networks
Xia Cheng, Junyang Shi and Mo Sha (State University of New York at Binghamton, USA); Linke Guo (Clemson University, USA)
- Layer Aware Microservice Placement and Request Scheduling at the Edge
Lin Gu (Huazhong University of Science and Technology, China); Deze Zeng (China University of Geosciences, China); Jie Hu (Huazhong University of Science and Technology, China); Bo Li (Hong Kong University of Science and Technology, Hong Kong); Hai Jin (Huazhong University of Science and Technology, China)
- Learning for Learning: Predictive Online Control of Federated Learning with Edge Provisioning
Yibo Jin (Nanjing University, China); Lei Jiao (University of Oregon, USA); Zhuzhong Qian, Sheng Zhang and Sanglu Lu (Nanjing University, China)
- Learning the unknown: Improving modulation classification performance in unseen scenarios
Erma Perenda and Sreeraj Rajendran (KU Leuven, Belgium); Gérôme Bovet (Armasuisse, Switzerland); Sofie Pollin (KU Leuven, Belgium); Mariya Zheleva (UAlbany SUNY, USA)
- Learning-Driven Decentralized Machine Learning in Resource-Constrained Wireless Edge Computing
Zeyu Meng, Hongli Xu and Min Chen (University of Science and Technology of China, China); Yang Xu (University of Science and Technology of China & School of Computer Science and Technology, China); Yangming Zhao and Chunming Qiao (University at Buffalo, USA)
- Let's Share VMs: Optimal Placement and Pricing across Base Stations in MEC Systems
Marie Siew (SUTD, Singapore); Kun Guo (Singapore University of Technology and Design, Singapore); Desmond Cai (Institute of High Performance Computing, Singapore); Lingxiang Li (University of Electronic Science and Technology of China, China); Tony Q. S. Quek (Singapore University of Technology and Design, Singapore)
- Leveraging Domain Knowledge for Robust Deep Reinforcement Learning in Networking
Ying Zheng, Haoyu Chen, Qingyang Duan and Lixiang Lin (Fudan University, China); Yiyang Shao and Wei Wang (Huawei, China); Xin Wang and Yuedong Xu (Fudan University, China)
- Leveraging Public-Private Blockchain Interoperability for Closed Consortium Interfacing
Bishakh Chandra Ghosh and Tanay Bhartia (Indian Institute of Technology Kharagpur, India); Sourav Kanti Addya (National Institute of Technology Karnataka, India); Sandip Chakraborty (Indian Institute of Technology Kharagpur, India)
- Leveraging Website Popularity Differences to Identify Performance Anomalies
Giulio Grassi (INRIA, France); Renata Teixeira (Inria, France); Chadi Barakat (Université Côte d'Azur, Inria, France); Mark Crovella (Boston University, USA)
- Lifesaving with RescueChain: Energy-Efficient and Partition-Tolerant Blockchain Based Secure Information Sharing for UAV-Aided Disaster Rescue
Yuntao Wang (Xi'an Jiaotong University, China); Zhou Su and Qichao Xu (Shanghai University, China); Ruidong Li (National Institute of Information and Communications Technology (NICT), Japan); Hao Luan (Xidian University, China)
- Live Gradient Compensation for Evading Stragglers in Distributed Learning
Jian Xu (Tsinghua University, China); Shao-Lun Huang (Tsinghua-Berkeley Shenzhen Institute, China); Linqi Song (City University of Hong Kong, Hong Kong); Tian Lan (George Washington University, USA)
- LiveMap: Real-Time Dynamic Map in Automotive Edge Computing
Qiang Liu (The University of North Carolina at Charlotte, USA); Tao Han and Linda Jiang Xie (University of North Carolina at Charlotte, USA); BaekGyu Kim (Toyota InfoTechnology Center, USA)
- LoFi: Enabling 2.4GHz LoRa and WiFi Coexistence by Detecting Extremely Weak Signals
Gonglong Chen, Wei Dong and Jiamei Lv (Zhejiang University, China)
- Looking for the Maximum Independent Set: A New Perspective on the Stable Path Problem
Yichao Cheng and Ning Luo (Yale University, USA); Jingxuan Zhang (Tongji University, China); Timos Antonopoulos, Ruzica Piskac and Qiao Xiang (Yale University, USA)
- Low Cost Sparse Network Monitoring Based on Block Matrix Completion
Kun Xie and Jiazheng Tian (Hunan University, China); Gaogang Xie (Institute of Computing Technology, Chinese Academy of Sciences, China); Guangxing Zhang (Institute of Computing Technology Chinese Academy of Sciences, China); Dafang Zhang (Hunan University, China)
- Low Sample and Communication Complexities in Decentralized Learning: A Triple Hybrid Approach
Xin Zhang (Iowa State University, USA); Jia Liu (The Ohio State University, USA); Zhengyuan Zhu (Iowa State University, USA); Elizabeth Serena Bentley (AFRL, USA)
- Low-Power Downlink for the Internet of Things using IEEE 802.11-compliant Wake-Up Receivers
Johannes Blobel (TU Berlin, Germany); Vu Tran (SMU, Singapore); Archan Misra (Singapore Management University, Singapore); Falko Dressler (TU Berlin, Germany)
- Making Multi-String Pattern Matching Scalable and Cost-Efficient with Programmable Switching ASICs
Shicheng Wang, Menghao Zhang, Guanyu Li, Chang Liu and Ying Liu (Tsinghua University, China); Xuya Jia (Huawei Technologies Co. Ltd., China); Mingwei Xu (Tsinghua University, China)
- MANDA: On Adversarial Example Detection for Network Intrusion Detection System
Ning Wang (Virginia Tech, USA); Yimin Chen (Virginia Polytechnic Institute and State University, USA); Yang Hu (Virgina Tech, USA); Wenjing Lou and Thomas Hou (Virginia Tech, USA)
- Maximizing the Benefit of RDMA at End Hosts
Xiaoliang Wang (Nanjing University, China); Hexiang Song (NJU, China); Cam-Tu Nguyen (Nanjing University, Vietnam); Dongxu Cheng and Tiancheng Jin (NJU, China)
- mCore: Achieving Sub-millisecond Scheduling for 5G MU-MIMO Systems
Yongce Chen, Yubo Wu, Thomas Hou and Wenjing Lou (Virginia Tech, USA)
- Medley: Predicting Social Trust in Time-Varying Online Social Networks
Wanyu Lin and Baochun Li (University of Toronto, Canada)
- MIERank: Co-ranking Individuals and Communities with Multiple Interactions in Evolving Networks
Shan Qu (Shanghai Jiaotong University, China); Luoyi Fu (Shanghai Jiao Tong University, China); Xinbing Wang (Shanghai Jiaotong University, China)
- Minimizing Entropy for Crowdsourcing with Combinatorial Multi-Armed Bandit
Yiwen Song and Haiming Jin (Shanghai Jiao Tong University, China)
- Minimizing the Number of Deployed UAVs for Delay-bounded Data Collection of IoT Devices
Junqi Zhang, Zheng Li, Wenzheng Xu and Jian Peng (Sichuan University, China); Weifa Liang (The Australian National University, Australia); Zichuan Xu (Dalian University of Technology, China); Xiaojiang Ren (Xidian University, China); Xiaohua Jia (City University of Hong Kong, Hong Kong)
- Minimizing the Sum of Age of Information and Transmission Cost under Stochastic Arrival Model
Kumar Saurav (Tata Institute of Fundamental Research, India); Rahul Vaze (TIFR Mumbai, India)
- Mobile Crowdsensing for Data Freshness: A Deep Reinforcement Learning Approach
Zipeng Dai, Hao Wang, Chi Harold Liu and Rui Han (Beijing Institute of Technology, China); Jian Tang (Syracuse University, USA); Guoren Wang (Northeastern University, China)
- Mobility- and Load-Adaptive Controller Placement and Assignment in LEO Satellite Networks
Long Chen, Feilong Tang and Xu Li (Shanghai Jiao Tong University, China)
- Modeling Communication Reliability in LoRa Networks with Device-level Accuracy
Verónica Toro-Betancur and Gopika Premsankar (Aalto University, Finland); Mariusz Slabicki (Institute of Theoretical and Applied Informatics, Polish Academy of Sciences, Poland); Mario Di Francesco (Aalto University, Finland)
- Modeling the Cost of Flexibility in Communication Networks
Alberto Martínez Alba (Technische Universität München, Germany); Péter Babarczi (Budapest University of Technology and Economics, Hungary & Technische Universität München, Germany); Andreas Blenk and Mu He (Technische Universität München, Germany); Patrick Kalmbach (Technical University of Munich, Germany); Johannes Zerwas and Wolfgang Kellerer (Technische Universität München, Germany)
- Monitoring Cloud Service Unreachability at Scale
Kapil Agrawal (Microsoft Research, India); Viral Mehta (Google, India); Sundararajan Renganathan (Stanford, USA); Sreangsu Acharyya (Microsoft Research, India); Liting Zhao (Microsoft, China); Chakri Kotipalli (Microsoft, USA); Venkata N. Padmanabhan (Microsoft Research, USA)
- Motion-Prediction-based Wireless Scheduling for Multi-User Panoramic Video Streaming
Jiangong Chen, Xudong Qin and Guangyu Zhu (University of Rhode Island, USA); Bo Ji (Virginia Tech, USA); Bin Li (University of Rhode Island, USA)
- MTP: Avoiding Control Plane Overload with Measurement Task Placement
Xiang Chen (Peking University, Pengcheng Lab, and Fuzhou University, China); Qun Huang (Peking University, China); Wang Peiqiao (Fuzhou China, China); Hongyan Liu (Zhejiang University, China); Yuxin Chen (University of Science and Technology of China, China); Dong Zhang (Fuzhou University, China); Haifeng Zhou (Zhejiang University, and Zhejiang Lab, China); Chunming Wu (Zhejiang Lab, and Zhejiang University, China)
- Multi-Agent Reinforcement Learning for Urban Crowd Sensing with For-Hire Vehicles
Rong Ding (Shanghai Jiao TongUniversity, China); Zhaoxing Yang, Yifei Wei and Haiming Jin (Shanghai Jiao Tong University, China); Xinbing Wang (Shanghai Jiaotong University, China)
- Multicast Communications with Varying Bandwidth Constraints
Yuval Emek and Shay Kutten (Technion, Israel); Mordechai Shalom (Tel-Hai College & Technion, Israel); Shmuel Zaks (Technion, Israel)
- Multi-Robot Path Planning for Mobile Sensing through Deep Reinforcement Learning
Yongyong Wei and Rong Zheng (McMaster University, Canada)
- Near Optimal and Dynamic Mechanisms Towards a Stable NFV Market in Multi-Tier Cloud Networks
Zichuan Xu and Haozhe Ren (Dalian University of Technology, China); Weifa Liang (The Australian National University, Australia); Qiufen Xia (Dalian University of Technology, China); Wanlei Zhou (University of Technology Sydney, Australia); Guowei WU (Dalian University of Technology, China); Pan Zhou (Huazhong University of Science and Technology, China)
- Near-Optimal Topology-adaptive Parameter Synchronization in Distributed DNN Training
Zhe Zhang and Chuan Wu (The University of Hong Kong, Hong Kong); Zongpeng Li (Wuhan University & University of Calgary, China)
- NetMARKS: Network Metrics-AwaRe Kubernetes Scheduler Powered by Service Mesh
Łukasz Wojciechowski (Samsung R&D Institute Poland, Poland); Krzysztof Opasiak and Jakub Latusek (Warsaw University of Technology & Samsung R&D Institute Poland, Poland); Maciej Wereski (Samsung R&D Institute Poland, Poland); Victor Morales (Samsung Research America, USA); Taewan Kim (Samsung Research, Samsung Electronics Co., Ltd., Korea (South)); Moonki Hong (Samsung Electronics, Co., Ltd., Korea (South))
- NFD: Using Behavior Models to Develop Cross-Platform Network Functions
Hongyi Huang and Wenfei Wu (Tsinghua University, China); Yongchao He (Tsinghua University & ByteDance Company, China); Bangwen Deng (Tsinghua University, China); Ying Zhang (Facebook, USA); Yongqiang Xiong (Microsoft Research Asia, China); Guo Chen (Hunan University, China); Yong Cui (Tsinghua University, China); Peng Cheng (Microsoft Research, China)
- NFReducer: Redundant Logic Elimination for Network Functions with Runtime Configurations
Bangwen Deng and Wenfei Wu (Tsinghua University, China)
- On Network Topology Augmentation for Global Connectivity under Regional Failures
János Tapolcai, Zsombor László Hajdú and Alija Pašić (Budapest University of Technology and Economics, Hungary); Pin-Han Ho (University of Waterloo, Canada); Lajos Rónyai (Budapest University of Technology and Economics (BME), Hungary)
- On Scheduling with AoI Violation Tolerance
Chengzhang Li, Qingyu Liu, Shaoran Li, Yongce Chen, Thomas Hou and Wenjing Lou (Virginia Tech, USA)
- On the Performance of Pipelined HotStuff
Jianyu Niu and Fangyu Gai (The University of British Columbia, Canada); Mohammad Jalalzai (The University of British Columbia); Chen Feng (University of British Columbia, Canada)
- On the Reliability of IEEE 802.1CB FRER
Doğanalp Ergenç and Mathias Fischer (University Hamburg, Germany)
- Online Joint Optimization on Traffic Engineering and Network Update in Software-defined WANs
Jiaqi Zheng, Yimeng Xu and Li Wang (Nanjing University, China); Haipeng Dai (Nanjing University & State Key Laboratory for Novel Software Technology, China); Guihai Chen (Shanghai Jiao Tong University, China)
- Optimal Multicast Scheduling for Millimeter Wave Networks Leveraging Directionality and Reflections
In Sop Cho and Seung Jun Baek (Korea University, Korea (South))
- Optimal Online Balanced Graph Partitioning
Maciej Pacut (University of Vienna, Poland); Mahmoud Parham and Stefan Schmid (University of Vienna, Austria)
- Optimal Rack-Coordinated Updates in Erasure-Coded Data Centers
Guowen Gong, Zhirong Shen and Suzhen Wu (Xiamen University, China); Xiaolu Li and Patrick Pak-Ching Lee (The Chinese University of Hong Kong, Hong Kong)
- Optimal Resource Allocation for Statistical QoS Provisioning in Supporting mURLLC Over FBC-Driven 6G Terahertz Wireless Nano-Networks
Xi Zhang and Jingqing Wang (Texas A&M University, USA); H. Vincent Poor (Princeton University, USA)
- Optimal Wireless Scheduling for Remote Sensing through Brownian Approximation
Daojing Guo and I-Hong Hou (Texas A&M University, USA); Ping-Chun Hsieh (National Chiao Tung University, Taiwan)
- Owl: Congestion Control with Partially Invisible Networks via Reinforcement Learning
Alessio Sacco (Politecnico di Torino, Italy & Saint Louis University, USA); Matteo Flocco and Flavio Esposito (Saint Louis University, USA); Guido Marchetto (Politecnico di Torino, Italy)
- PALMAR: Towards Adaptive Multi-inhabitant Activity Recognition in Point-Cloud Technology
Mohammad Arif Ul Alam (University of Massachusetts Lowell, USA & Cognitive Ubiquitous Computing and Systems, Bangladesh); Md Mahmudur Rahman and Jared Widberg (University of Massachusetts Lowell, USA)
- PCL: Packet Classification with Limited knowledge
Vitalii Demianiuk (Ariel University, Israel); Chen Hajaj (Ariel University & Data Science and Artificial Intelligence Research Center, Israel); Kirill Kogan (Ariel University, Israel)
- P-FedAvg: Parallelizing Federated Learning with Theoretical Guarantees
Zhicong Zhong (Sun Yat-sen University, China); Yipeng Zhou (Macquarie University, Australia); Di Wu (Sun Yat-Sen University, China); Xu Chen (Sun Yat-sen University, China); Min Chen (Huazhong University of Science and Technology, China); Chao Li (Tencent, China); Quan Z. Sheng (Macquarie University, Australia)
- Physical Layer Key Generation between Backscatter Devices over Ambient RF Signals
Pu Wang (Xidian University, China); Long Jiao and Kai Zeng (George Mason University, USA); Zheng Yan (Xidian University & Aalto University, China)
- Physical Layer Secure Communications Based on Collaborative Beamforming for UAV Networks: A Multi-objective Optimization Approach
Jiahui Li (Jilin University, China); Hui Kang (JiLin University, China); Geng Sun, Shuang Liang and Yanheng Liu (Jilin University, China); Ying Zhang (Georgia Institute of Technology, USA)
- PolarTracker: Attitude-aware Channel Access for Floating Low Power Wide Area Networks
Yuting Wang, Xiaolong Zheng, Liang Liu and Huadong Ma (Beijing University of Posts and Telecommunications, China)
- POLO: Localizing RFID-Tagged Objects for Mobile Robots
Dianhan Xie, Xudong Wang, Aimin Tang and Hongzi Zhu (Shanghai Jiao Tong University, China)
- Popularity-Aware 360-Degree Video Streaming
Xianda Chen, Tianxiang Tan and Guohong Cao (The Pennsylvania State University, USA)
- Practical Analysis of Replication-Based Systems
Florin Ciucu (University of Warwick, United Kingdom (Great Britain)); Felix Poloczek (University of Warwick / TU Berlin, Germany); Lydia Y. Chen (IBM Zurich Research Laboratory, Switzerland); Martin Chan (University of Warwick, Germany)
- Primus: Fast and Robust Centralized Routing for Large-scale Data Center Networks
Guihua Zhou, Guo Chen, Fusheng Lin, Tingting Xu, Dehui Wei and Jianbing Wu (Hunan University, China); Li Chen (Huawei, Hong Kong); Yuanwei Lu and Andrew Qu (Tencent, China); Hua Shao (Tsinghua University & Tencent, China); Hongbo Jiang (Hunan University, China)
- Prison Break of Android Reflection Restriction and Defense
Zhen Ling and Ruizhao Liu (Southeast University, China); Yue Zhang (Jinan University, China); Kang Jia (Southeast University, China); Bryan Pearson (University of Central Florida, USA); Xinwen Fu (University of Massachusetts Lowell, USA); Luo Junzhou (Southeast University, China)
- Privacy Budgeting for Growing Machine Learning Datasets
Weiting Li, Liyao Xiang, Zhou Zhou and Feng Peng (Shanghai Jiao Tong University, China)
- Privacy-Preserving Learning of Human Activity Predictors in Smart Environments
Sharare Zehtabian (University of Central Florida, USA); Siavash Khodadadeh (University of Central Flordia, USA); Ladislau Bölöni and Damla Turgut (University of Central Florida, USA)
- Privacy-Preserving Outlier Detection with High Efficiency over Distributed Datasets
Guanghong Lu, Chunhui Duan, Guohao Zhou and Xuan Ding (Tsinghua University, China); Yunhao Liu (Tsinghua University & The Hong Kong University of Science and Technology, China)
- PROCESS: Privacy-Preserving On-Chain Certificate Status Service
Meng Jia (School of Cyber Science and Engineering, Wuhan University, China); Kun He, Jing Chen, Ruiying Du and Weihang Chen (Wuhan University, China); Zhihong Tian (Guangzhou University, China); Shouling Ji (Zhejiang University, China & Georgia Institute of Technology, USA)
- Programmable Switches for in-Networking Classification
Bruno Missi Xavier and Rafael Silva Guimaraes (Federal Institute of Espirito Santo - Campus Cachoeiro de Itapemirim, Brazil); Giovanni Comarela (Universidade Federal do Espírito Santo, Brazil); Magnos Martinello (Federal University of Espirito Santo, Brazil)
- ProHiCo: A Probabilistic Framework to Hide Communities in Large Networks
Xuecheng Liu and Luoyi Fu (Shanghai Jiao Tong University, China); Xinbing Wang (Shanghai Jiaotong University, China); John Hopcroft (Cornell University, USA)
- Proximity-Echo: Secure Two Factor Authentication Using Active Sound Sensing
Yanzhi Ren, Ping Wen, Hongbo Liu and Zhourong Zheng (University of Electronic Science and Technology of China, China); Yingying Chen (Rutgers University, USA); Pengcheng Huang and Hongwei Li (University of Electronic Science and Technology of China, China)
- Push the Limit of Device-Free Acoustic Sensing on Commercial Mobile Devices
Cheng Haiming and Wei Lou (The Hong Kong Polytechnic University, Hong Kong)
- Pyramid: A Layered Sharding Blockchain System
Zicong Hong (Sun Yat-sen University, China); Song Guo (The Hong Kong Polytechnic University, Hong Kong); Peng Li (The University of Aizu, Japan); Chen Wuhui (Sun Yat-sen university, China)
- Pyramid: Real-Time LoRa Collision Decoding with Peak Tracking
Zhenqiang Xu, Pengjin Xie and Jiliang Wang (Tsinghua University, China)
- Radio Frequency Fingerprint Identification for LoRa Using Spectrogram and CNN
Guanxiong Shen, Junqing Zhang and Alan Marshall (University of Liverpool, United Kingdom (Great Britain)); Linning Peng (Southeast University, China); Xianbin Wang (Western University, Canada)
- Randomized Scheduling of Real-Time Traffic in Wireless Networks Over Fading Channels
Christos Tsanikidis and Javad Ghaderi (Columbia University, USA)
- RapidRider: Efficient WiFi Backscatter with Uncontrolled Ambient Signals
Qiwei Wang (University of Science and Technology of China, China); Si Chen and Jia Zhao (Simon Fraser University, Canada); Wei Gong (University of Science and Technology of China, China)
- Rate Allocation and Content Placement in Cache Networks
Khashayar Kamran, Armin Moharrer, Stratis Ioannidis and Edmund Yeh (Northeastern University, USA)
- Rate Region of Scheduling a Wireless Network with Discrete Propagation Delays
Jun Ma, Yanxiao Liu and Shenghao Yang (The Chinese University of Hong Kong, Shenzhen, China)
- Real-time sampling and estimation on random access channels: Age of Information and Beyond
Xingran Chen, Xinyu Liao and Shirin Saeedi Bidokhti (University of Pennsylvania, USA)
- Redundant Entanglement Provisioning and Selection for Throughput Maximization in Quantum Networks
Yangming Zhao and Chunming Qiao (University at Buffalo, USA)
- Reliability-aware Dynamic Service Chain Scheduling in 5G Networks based on Reinforcement Learning
Junzhong Jia and Lei Yang (South China University of Technology, China); Jiannong Cao (Hong Kong Polytechnical University, Hong Kong)
- Resource-Efficient Federated Learning with Hierarchical Aggregation in Edge Computing
Zhiyuan Wang, Hongli Xu and Jianchun Liu (University of Science and Technology of China, China); He Huang (Soochow University, China); Chunming Qiao and Yangming Zhao (University at Buffalo, USA)
- RespTracker: Multi-user Room-scale Respiration Tracking with Commercial Acoustic Devices
Haoran Wan, Shuyu Shi, Wenyu Cao, Wei Wang and Guihai Chen (Nanjing University, China)
- Reusing Backup Batteries as BESS for Power Demand Reshaping in 5G and Beyond
Guoming Tang (Peng Cheng Laboratory, China); Hao Yuan and Deke Guo (National University of Defense Technology, China); Kui Wu (University of Victoria, Canada); Yi Wang (Southern University of Science and Technology, China)
- Reversible Models for Wireless Multi-Channel Multiple Access
Michael Neely (University of Southern California, USA)
- RFace: Anti-Spoofing Facial Authentication Using COTS RFID
Weiye Xu (Zhejiang University, China); Jianwei Liu (Zhejiang University & Xi'an Jiaotong University, China); Shimin Zhang (Zhejiang University, China); Yuanqing Zheng (The Hong Kong Polytechnic University, Hong Kong); Feng Lin (Zhejiang University, China); Jinsong Han (Zhejiang University & School of Cyber Science and Technology, China); Fu Xiao (Nanjing University of Posts and Telecommunications, China); Kui Ren (Zhejiang University, China)
- Robust 360◦ Video Streaming via Non-Linear Sampling
Mijanur R Palash, Voicu Popescu, Amit Sheoran and Sonia Fahmy (Purdue University, USA)
- Robust Online Learning against Malicious Manipulation with Application to Network Flow Classification
Yupeng Li and Ben Liang (University of Toronto, Canada); Ali Tizghadam (TELUS Communications, Canada)
- Robust Service Mapping in Multi-Tenant Clouds
Jingzhou Wang, Gongming Zhao and Hongli Xu (University of Science and Technology of China, China); He Huang (Soochow University, China); Luyao Luo (University of Science and Technology of China, China); Yongqiang Yang (Huawei Technologies Co., Ltd, China)
- Ruledger: Ensuring Execution Integrity in Trigger-Action IoT Platforms
Jingwen Fan (Sichuan Changhong Electric Co., Ltd., China); Yi He (Tsinghua University, China); Bo Tang (Sichuan Changhong Electric Co., Ltd., China); Qi Li (Tsinghua University, China); Ravi Sandhu (University of Texas at San Antonio, USA)
- Safety Critical Networks using Commodity SDNs
Ashish Kashinath (University of Illinois at Urbana-Champaign, USA); Monowar Hasan (University of Illinois Urbana-Champaign, USA); Rakesh Kumar (University of Illinois, Urbana-Champaign, USA); Sibin Mohan (University of Illinois at Urbana-Champaign, USA); Rakesh B. Bobba (Oregon State University, USA); Smruti Padhy (University of Texas at Austin, USA)
- Sample-level Data Selection for Federated Learning
Anran Li, Lan Zhang, Juntao Tan, Yaxuan Qin, Junhao Wang and Xiang-Yang Li (University of Science and Technology of China, China)
- Scalable On-Switch Rate Limiters for the Cloud
Yongchao He (Tsinghua University & ByteDance Company, China); Wenfei Wu (Tsinghua University, China); Xuemin Wen and Haifeng Li (Huawei, China); Yongqiang Yang (Huawei Technologies Co., Ltd, China)
- ScreenID: Enhancing QRCode Security by Fingerprinting Screens
Yijie Li and Yi-Chao Chen (Shanghai Jiao Tong University, China); Xiaoyu Ji (Zhejiang University, China); Hao Pan, Lanqing Yang, Guangtao Xue and Jiadi Yu (Shanghai Jiao Tong University, China)
- Self-Adaptive Sampling for Network Traffic Measurement
Yang Du, He Huang and Yu-e Sun (Soochow University, China); Shigang Chen (University of Florida, USA); Guoju Gao (Soochow University, China)
- Self-adjusting Advertisement of Cache Indicators with Bandwidth Constraints
Itamar Cohen (Politecnico di Torino, Italy); Gil Einziger (Ben-Gurion University Of The Negev, Israel); Gabriel Scalosub (Ben-Gurion University of the Negev, Israel)
- Sequential Resource Access: Theory and Algorithm
Lin Chen (Sun Yat-sen University, China); Anastasios Giovanidis (Sorbonne Université & CNRS-LIP6, France); Wei Wang (Zhejiang University, China); Shan Lin (Stony Brook University, USA)
- Setting the Record Straighter on Shadow Banning
Erwan Le Merrer (Inria, France); Benoit Morgan (IRIT-ENSEEIHT, University of Toulouse, France); Gilles Tredan (LAAS-CNRS, France)
- ShakeReader: 'Read' UHF RFID using Smartphone
Kaiyan Cui (Xi'an Jiaotong University, China); Yanwen Wang and Yuanqing Zheng (The Hong Kong Polytechnic University, Hong Kong); Jinsong Han (Zhejiang University & School of Cyber Science and Technology, China)
- Signal Detection and Classification in Shared Spectrum: A Deep Learning Approach
Wenhan Zhang, Mingjie Feng, Marwan Krunz and Amir Hossein Yazdani Abyaneh (University of Arizona, USA)
- SILoc: A Speed Inconsistency-Immune Approach to Mobile RFID Robot Localization
Jiuwu Zhang and Xiulong Liu (Tianjin University, China); Tao Gu (Macquarie University, Australia); Xinyu Tong, Sheng Chen and Keqiu Li (Tianjin University, China)
- SmartDistance: A Mobile-based Positioning System for Automatically Monitoring Social Distance
Li Li (Shenzhen Institutes Of Advanced Technology Chinese Academy Of Sciences, China); Xiaorui Wang (The Ohio State University, USA); Wenli Zheng (Shanghai Jiaotong University, China); Cheng-Zhong Xu (University of Macau, China)
- SOBA: Session optimal MDP-based network friendly recommendations
Theodoros Giannakas (EURECOM, France); Anastasios Giovanidis (Sorbonne Université & CNRS-LIP6, France); Thrasyvoulos Spyropoulos (EURECOM, France)
- SODA: Similar 3D Object Detection Accelerator at Network Edge for Autonomous Driving
Wenquan Xu (Tsinghua University, China); Haoyu Song (Futurewei Technologies, USA); LinYang Hou (Tsinghua University, China); Hui Zheng (Wuhan University, China); Xinggong Zhang (Peking University, China); Chuwen Zhang (Tsinghua University, China); Wei Hu (Peking University, China); Yi Wang (Southern University of Science and Technology, China); Bin Liu (Tsinghua University, China)
- Statistical Delay and Error-Rate Bounded QoS Provisioning for 6G mURLLC Over AoI-Driven and UAV-Enabled Wireless Networks
- SteaLTE: Private 5G Cellular Connectivity as a Service with Full-stack Wireless Steganography
Leonardo Bonati, Salvatore D'Oro, Francesco Restuccia, Stefano Basagni and Tommaso Melodia (Northeastern University, USA)
- Store Edge Networked Data (SEND): A Data and Performance Driven Edge Storage Framework
Adrian-Cristian Nicolaescu (University College London (UCL), United Kingdom (Great Britain)); Spyridon Mastorakis (University of Nebraska, Omaha, USA); Ioannis Psaras (University College London, United Kingdom (Great Britain))
- Strategic Information Revelation in Crowdsourcing Systems Without Verification
Chao Huang (The Chinese University of Hong Kong, Hong Kong); Haoran Yu (Beijing Institute of Technology, China); Jianwei Huang (The Chinese University of Hong Kong, Shenzhen, China); Randall A Berry (Northwestern University, USA)
- Tailored Learning-Based Scheduling for Kubernetes-Oriented Edge-Cloud System
Yiwen Han, Shihao Shen and Xiaofei Wang (Tianjin University, China); Shiqiang Wang (IBM T. J. Watson Research Center, USA); Victor C.M. Leung (University of British Columbia, Canada)
- Taming Time-Varying Information Asymmetry in Fresh Status Acquisition
Zhiyuan Wang (The Chinese University of Hong Kong, Hong Kong); Lin Gao (Harbin Institute of Technology (Shenzhen), China); Jianwei Huang (The Chinese University of Hong Kong, Shenzhen, China)
- The Effect of Ground Truth Accuracy on the Evaluation of Localization Systems
Chen Gu (Google, USA); Ahmed Shoukry (Wireless Research Center, E-JUST, Egypt); Moustafa Youssef (Alexandria University, Egypt)
- The Impact of Baseband Functional Splits on Resource Allocation in 5G Radio Access Networks
Iordanis Koutsopoulos (Athens University of Economics and Business, Greece)
- Threshold-based rerouting and replication for resolving job-server affinity relations
Youri Raaijmakers and Onno Boxma (Eindhoven University of Technology, The Netherlands); Sem Borst (Eindhoven University of Technology & Nokia Bell Labs, USA)
- TiBroco: A Fast and Secure Distributed Learning Framework for Tiered Wireless Edge Networks
Dong-Jun Han (KAIST, Korea (South)); Jy-yong Sohn (Korea Advanced Institute of Science and Technology, Korea (South)); Jaekyun Moon (KAIST, Korea (South))
- Time-Varying Resource Graph Based Resource Model for Space-Terrestrial Integrated Networks
Long Chen and Feilong Tang (Shanghai Jiao Tong University, China); Zhetao Li (Xiangtan University, China); Laurence T. Yang (St. Francis Xavier University, Canada); Jiadi Yu and Bin Yao (Shanghai Jiao Tong University, China)
- To Talk or to Work: Flexible Communication Compression for Energy Efficient Federated Learning over Heterogeneous Mobile Edge Devices
Liang Li (Xidian University, China); Dian Shi (University of Houston, USA); Ronghui Hou and Hui Li (Xidian University, China); Miao Pan and Zhu Han (University of Houston, USA)
- ToP: Time-dependent Zone-enhanced Points-of-interest Embedding-based Explainable Recommender system
En Wang, Yuanbo Xu, Yongjian Yang, Fukang Yang, Chunyu Liu and Yiheng Jiang (Jilin University, China)
- Tornadoes In The Cloud: Worst-Case Attacks on Distributed Resources Systems
Jhonatan Tavori (Tel-Aviv University, Israel); Hanoch Levy (Tel Aviv University, Israel)
- Towards Cross-Modal Forgery Detection and Localization on Live Surveillance Videos
Yong Huang, Xiang Li, Wei Wang and Tao Jiang (Huazhong University of Science and Technology, China); Qian Zhang (Hong Kong University of Science and Technology, Hong Kong)
- Towards Fine-Grained Spatio-Temporal Coverage for Vehicular Urban Sensing Systems
Guiyun Fan, Yiran Zhao, Ziliang Guo, Haiming Jin and Xiaoying Gan (Shanghai Jiao Tong University, China); Xinbing Wang (Shanghai Jiaotong University, China)
- Towards Minimum Fleet for Ridesharing-Aware Mobility-on-Demand Systems
Chonghuan Wang, Yiwen Song, Yifei Wei, Guiyun Fan and Haiming Jin (Shanghai Jiao Tong University, China); Fan Zhang (Shenzhen Institutes of Advanced Technology, Chinese Academy of Sciences, China)
- Towards the Fairness of Traffic Policer
Danfeng Shan and Peng Zhang (Xi'an Jiaotong University, China); Wanchun Jiang (Central South University, China); Hao Li (Xi'an Jiaotong University, China); Fengyuan Ren (Tsinghua University, China)
- Towards Video Streaming Analysis and Sharing for Multi-Device Interaction with Lightweight DNNs
Yakun Huang, Hongru Zhao and Xiuquan Qiao (Beijing University of Posts and Telecommunications, China); Jian Tang (Syracuse University, USA); Ling Liu (Georgia Tech, USA)
- TrackSign: Guided Web Tracking Discovery
Ismael Castell-Uroz (Universitat Politècnica de Catalunya, Spain); Josep Solé-Pareta (UPC, Spain); Pere Barlet-Ros (Universitat Politècnica de Catalunya, Spain)
- Traffic-aware Buffer Management in Shared Memory Switches
Sijiang Huang, Mowei Wang and Yong Cui (Tsinghua University, China)
- Train Once, Locate Anytime for Anyone: Adversarial Learning based Wireless Localization
Danyang Li, Jingao Xu, Zheng Yang, Yumeng Lu and Qian Zhang (Tsinghua University, China); Xinglin Zhang (South China University of Technology, China)
- Trust Trackers for Computation Offloading in Edge-Based IoT Networks
Matthew Bradbury, Arshad Jhumka and Tim Watson (University of Warwick, United Kingdom (Great Britain))
- Turbocharging Deep Backscatter Through Constructive Power Surges with a Single RF Source
Zhenlin An, Qiongzheng Lin and Qingrui Pan (The Hong Kong Polytechnic University, Hong Kong); Lei Yang (The Hong Kong Polytechnic University, China)
- Ultra-Wideband Swarm Ranging
Feng Shan, Jiaxin Zeng, Zengbao Li, Luo Junzhou and Weiwei Wu (Southeast University, China)
- Uplink Multi-User Beamforming on Single RF Chain mmWave WLANs
Keerthi Priya Dasala (Rice University, USA); Josep M Jornet (Northeastern University, USA); Edward W. Knightly (Rice University, USA)
- vGaze: Implicit Saliency-Aware Calibration for Continuous Gaze Tracking on Mobile Devices
Songzhou Yang, Yuan He and Meng Jin (Tsinghua University, China)
- VideoLoc: Video-based Indoor Localization with Text Information
Shusheng Li and Wenbo He (McMaster University, Canada)
- Web-LEGO: Trading Content Strictness for Faster Webpages
Pengfei Wang (Dalian University of Technology, China); Matteo Varvello (Telefonica, unknown); Chunhe Ni (Amazon, USA); Ruiyun Yu (Northeastern University, China); Aleksandar Kuzmanovic (Northwestern University, USA)
- WebMythBusters: An In-depth Study of Mobile Web Experience
Seonghoon Park and Yonghun Choi (Yonsei University, Korea (South)); Hojung Cha (Yonsei University, S. Korea, Korea (South))
- WiProg: A WebAssembly-based Approach to Integrated IoT Programming
Borui Li, Wei Dong and Yi Gao (Zhejiang University, China)
- Your Home is Insecure: Practical Attacks on Wireless Home Alarm Systems
Tao Li (IUPUI, USA); Dianqi Han, Jiawei Li, Ang Li and Yan Zhang (Arizona State University, USA); Rui Zhang (University of Delaware, USA); Yanchao Zhang (Arizona State University, USA)
- π-ROAD: a Learn-as-You-Go Framework for On-Demand Emergency Slices in V2X Scenarios
Armin Okic (Politecnico di Milano, Italy); Lanfranco Zanzi (NEC Laboratories Europe & Technische Universität Kaiserslautern, Germany); Vincenzo Sciancalepore (NEC Laboratories Europe GmbH, Germany); Alessandro E. C. Redondi (Politecnico di Milano, Italy); Xavier Costa-Perez (NEC Laboratories Europe, Germany)

Student Travel Grant Sponsors


is Mainsite

- Search all IEEE websites
- Mission and vision
- IEEE at a glance
- IEEE Strategic Plan
- Organization of IEEE
- Diversity, Equity, & Inclusion
- Organizational Ethics
- Annual Report
- History of IEEE
- Volunteer resources
- IEEE Corporate Awards Program
- Financials and Statistics
- IEEE Future Directions
- IEEE for Industry (Corporations, Government, Individuals)
- IEEE Climate Change
- Humanitarian and Philanthropic Opportunities
- Select an option
- Get the latest news
- Access volunteer resources (Code of Ethics, financial forms, tools and templates, and more)
- Find IEEE locations
- Get help from the IEEE Support Center
- Recover your IEEE Account username and password
- Learn about the IEEE Awards program and submit nomination
- View IEEE's organizational structure and leadership
- Apply for jobs at IEEE
- See the history of IEEE
- Learn more about Diversity, Equity & Inclusion at IEEE
- Join an IEEE Society
- Renew your membership
- Member benefits
- IEEE Contact Center
- Connect locally
- Memberships and Subscriptions Catalog
- Member insurance and discounts
- Member Grade Elevation
- Get your company engaged
- Access your Account
- Learn about membership dues
- Learn about Women in Engineering (WIE)
- Access IEEE member email
- Find information on IEEE Fellows
- Access the IEEE member directory
- Learn about the Member-Get-a-Member program
- Learn about IEEE Potentials magazine
- Learn about Student membership
- Affinity groups
- IEEE Societies
- Technical Councils
- Technical Communities
- Geographic Activities
- Working groups
- IEEE Regions
- IEEE Collabratec®
- IEEE Resource Centers
- IEEE DataPort
- See the IEEE Regions
- View the MGA Operations Manual
- Find information on IEEE Technical Activities
- Get IEEE Chapter resources
- Find IEEE Sections, Chapters, Student Branches, and other communities
- Learn how to create an IEEE Student Chapter
- Upcoming conferences
- IEEE Meetings, Conferences & Events (MCE)
- IEEE Conference Application
- IEEE Conference Organizer Education Program
- See benefits of authoring a conference paper
- Search for 2025 conferences
- Search for 2024 conferences
- Find conference organizer resources
- Register a conference
- Publish conference papers
- Manage conference finances
- Learn about IEEE Meetings, Conferences & Events (MCE)
- Visit the IEEE SA site
- Become a member of the IEEE SA
- Find information on the IEEE Registration Authority
- Obtain a MAC, OUI, or Ethernet address
- Access the IEEE 802.11™ WLAN standard
- Purchase standards
- Get free select IEEE standards
- Purchase standards subscriptions on IEEE Xplore®
- Get involved with standards development
- Find a working group
- Find information on IEEE 802.11™
- Access the National Electrical Safety Code® (NESC®)
- Find MAC, OUI, and Ethernet addresses from Registration Authority (regauth)
- Get free IEEE standards
- Learn more about the IEEE Standards Association
- View Software and Systems Engineering Standards
- IEEE Xplore® Digital Library
- Subscription options
- IEEE Spectrum
- The Institute
- Proceedings of the IEEE
- IEEE Access®
- Author resources
- Get an IEEE Xplore Digital Library trial for IEEE members
- Review impact factors of IEEE journals
- Request access to the IEEE Thesaurus and Taxonomy
- Access the IEEE copyright form
- Find article templates in Word and LaTeX formats
- Get author education resources
- Visit the IEEE Xplore digital library
- Find Author Digital Tools for IEEE paper submission
- Review the IEEE plagiarism policy
- Get information about all stages of publishing with IEEE
- IEEE Learning Network (ILN)
- IEEE Credentialing Program
- Pre-university
- IEEE-Eta Kappa Nu
- Accreditation
- Access continuing education courses on the IEEE Learning Network
- Find STEM education resources on TryEngineering.org
- Learn about the TryEngineering Summer Institute for high school students
- Explore university education program resources
- Access pre-university STEM education resources
- Learn about IEEE certificates and how to offer them
- Find information about the IEEE-Eta Kappa Nu honor society
- Learn about resources for final-year engineering projects
- Access career resources
IEEE Resources for Final-Year Engineering Projects
- Constitutional Amendments
- IEEE Annual Election Home
- Annual Election Candidates
- Candidate Nominations
- Petition Process
- Previous Elections
- Voter Eligibility
- IEEE Assembly Election
- Election Campaign Resources
- Annual Election FAQ
- Candidate Campaign Forums
- IEEE Governing Documents
- Board 30-Day Review/Approval Process
- Initiatives
- IEEE New Initiative Program
- IEEE New Initiatives Committee
- IEEE New Initiative Program Frequently Asked Questions
- Public Visibility
- Public Visibility Home
- Public Visibility Bylaw and Charter Documents
- Technical Expert Form
- Technical Expert Resources
- Report Archive (IEEE Account Required)
- Committee Members and Staff Contacts
- Nominations
- Nominations and Appointments Committee Home
- IEEE Committee Position Descriptions
- Guidelines for Nominating Candidates
- Nominations Form
- IEEE N&A Activity Schedule
- Compliance Related Information
- Membership Discount Promotion Codes
- About National Society Agreements
- IEEE - Establishing a Technical/Sister Society Agreement
- IEEE - Establishing a National Society Agreement
- Board of Directors and Executive Staff
- IEEE Industry Engagement Committee
- IEEE Industry Engagement Committee Events and Activities: Calls for Proposals
- Organization
- Media Resources
- IEEE in the News
- Conflict of Interest
- Principles of Business Conduct and Conflict of Interest Home
- Combined POBC/COI form
- Tax Administration
- VAT and GST Information
- Independent Contractors
- Form 1099 Requirements
- Tax Information for IEEE Conferences Held in Canada
- US Sales Tax Exemptions
- Tax Management Home
- Related Tax Information
- Tax and Corporate Information
- Income Tax Treaty Information
- Risk Insurance
- Business Continuity Management
- Conference Insurance Program
- IEEE Enterprise Risk Management (ERM) Program
- IEEE Risk and Insurance Management Services
- Corporate Insurance Program
- IEEE Activities with Children
- Registration Form
- Insurance for IEEE Organizational Units
- Ethics and Member Conduct Home
- Student Ethics Competition
- IEEE Award for Distinguished Ethical Practices
- Committee Vision and Mission
- Ethics Resources and Organizations
- Ethics and Member Conduct Committee
- Position Paper on Ethical Conduct Awareness
- History Center Home
- History Center: Location & Contact Information
- Newsletters
- History Center: History of the History Center
- History Center: Programs & Projects
- Support the History Center
- IEEE History Committee
- Programs/Projects
- History of the History Center
- Location & Contact Information
- History Center: Events
- IEEE Assembly Election Candidates
Tools for authoring and formatting IEEE papers
Sample Article from the IEEE Xplore Digital Library " Final year projects in electrical and information engineering: Tips for students and supervisors " (Full-text access available with subscription. Check with your academic institution's librarian to see if you have access. Subscription options available at www.ieee.org/innovate )
IEEE Xplore Digital Library Subscription Options IEEE has multiple subscription options available to access IEEE Xplore for individuals or organizations of varying size or need. Determining the optimum way for you to access the IEEE Xplore digital library depends on your research needs and whether you rely on an organization for access or research independently of an organization.
- Author Digital Tools
- Article Templates and Instructions
- Manuscript Templates for Conference Proceedings

Let's stay connected.
Download today
More detail about papers and their associated presentations will be released with the virtual website. What follows is a list of papers groups by session.
Tuesday, October 26 10:00-11:30AM CDT (UTC-5) Best Papers Session Chair: Bongshin Lee, Silvia Miksch, Anders Ynnerman
Simultaneous Matrix Orderings for Graph Collections Authors: Nathan van Beusekom, Wouter Meulemans, Bettina Speckmann
IRVINE: Using Interactive Clustering and Labeling to Analyze Correlation Patterns: A Design Study from the Manufacturing of Electrical Engines Authors: Joscha Eirich, Jakob Bonart, Dominik Jäckle, Michael Sedlmair, Ute Schmid, Kai Fischbach, Tobias Schreck, Jürgen Bernard
Perception! Immersion! Empowerment! Superpowers as Inspiration for Visualization Authors: Wesley Willett, Bon Adriel Aseniero, Sheelagh Carpendale, Pierre Dragicevic, Yvonne Jansen, Lora Oehlberg, Petra Isenberg
Feature Curves and Surfaces of 3D Asymmetric Tensor Fields Authors: Shih-Hsuan Hung, Yue Zhang, Harry Yeh, Eugene Zhang
Jurassic Mark: Inattentional Blindness for a Datasaurus Reveals that Visualizations are Explored, not Seen Authors: Tal Boger, Steven Most, Steven Franconeri
Wednesday, October 27 08:00-09:30AM CDT (UTC-5) Explainable AI and Machine Learning Session Chair: Hendrik Strobelt
AffectiveTDA: Using Topological Data Analysis for Improved Explainability in Affective Computing Authors: Hamza Elhamdadi, Shaun Canavan, Paul Rosen
Human-in-the-loop Extraction of Interpretable Concepts in Deep Learning Models Authors: Zhenge Zhao, Panpan Xu, Carlos Scheidegger, Liu Ren
Towards Visual Explainable Active Learning for Zero-Shot Classification Authors: Shichao Jia, zeyu li, Nuo Chen, Jiawan Zhang
M^2Lens: Visualizing and Explaining Multimodal Models for Sentiment Analysis Authors: Xingbo Wang, Jianben He, Zhihua Jin, Muqiao Yang, Yong Wang, Huamin Qu
NeuroCartography: Scalable Automatic Visual Summarization of Concepts in Deep Neural Networks Authors: Haekyu Park, Nilaksh Das, Rahul Duggal, Austin Wright, Omar Shaikh, Fred Hohman, Duen Horng Chau
Visual Analytics for RNN-Based Deep Reinforcement Learning Authors: Junpeng Wang, Wei Zhang, Hao Yang, Chin-Chia Michael Yeh, Liang Wang
Wednesday, October 27 08:00-09:30AM CDT (UTC-5) Interaction Session Chair: Christian Tominski
Task-Based Effectiveness of Interactive Contiguous Area Cartograms Authors: Ian K. Duncan, Shi Tingsheng, Simon T. Perrault, Michael T. Gastner
Nebula: A Coordinating Grammar of Graphics Authors: Ran Chen, Xinhuan Shu, Jiahui Chen, Di Weng, Junxiu Tang, Siwei Fu, Yingcai Wu
Rotate or Wrap? Interactive Visualisations of Cyclical Data on Cylindrical or Toroidal Topologies Authors: Kun-Ting Chen, Tim Dwyer, Benjamin Bach, Kim Marriott
DIEL: Interactive Visualization Beyond the Here and Now Authors: Yifan Wu, Remco Chang, Joseph Hellerstein, Arvind Satyanarayan, Eugene Wu
VizSnippets: Compressing Visualization Bundles Into Representative Previews for Browsing Visualization Collections Authors: Michael Oppermann, Tamara Munzner
Interactive Dimensionality Reduction for Comparative Analysis Authors: Takanori Fujiwara, Xinhai Wei, Jian Zhao, Kwan-Liu Ma
Wednesday, October 27 08:00-09:30AM CDT (UTC-5) Surfaces and Volumes Session Chair: Koji Koyamada
Real-Time Denoising of Volumetric Path Tracing for Direct Volume Rendering Authors: Jose A. Iglesias-Guitian, Prajita Mane, Bochang Moon
Learning Adaptive Sampling and Reconstruction for Volume Visualization Authors: Sebastian Weiss, Mustafa Isik, Justus Thies, Rüdiger Westermann
STNet: An End-to-End Generative Framework for Synthesizing Spatiotemporal Super-Resolution Volumes Authors: Jun Han, Hao Zheng, Danny Chen, Chaoli Wang
Interactive Exploration of Physically-Observable Objective Vortices in Unsteady 2D Flow Authors: Xingdi Zhang, Markus Hadwiger, Thomas Theussl, Peter Rautek
3D Virtual Pancreatography Authors: Shreeraj Jadhav, Konstantin Dmitriev, Joseph Marino, Matthew Barish, Arie E. Kaufman
Visual Analysis of Multi-Parameter Distributions across Ensembles of 3D Fields Authors: Alexander Kumpf, Josef Stumpfegger, Patrick Fabian Härtl, Rüdiger Westermann
Wednesday, October 27 08:00-09:30AM CDT (UTC-5) Graphical Perception and Coloring Session Chair: Danielle Albers Szafir
Context Matters: A Theory of Semantic Discriminability for Perceptual Encoding Systems Authors: Kushin Mukherjee, Brian Yin, Brianne Sherman, Laurent Lessard, Karen Schloss
Conceptual Metaphor and Graphical Convention Influence the Interpretation of Line Graphs Authors: Greg Woodin, Bodo Winter, Lace Padilla
Rethinking the Ranks of Visual Channels Authors: Caitlyn McColeman, Fumeng Yang, Timothy F. Brady, Steven Franconeri
Affective Congruence in Visualization Design: Influences on Reading Categorical Maps Authors: Cary L. Anderson, Anthony C. Robinson
Modeling Just Noticeable Differences in Charts Authors: Min Lu, Joel Lanir, Chufeng Wang, Yucong Yao, Wen Zhang, Oliver Deussen, Hui Huang
Augmenting Parallel Coordinates Plots with Color-coded Stacked Histograms Authors: Jinwook Bok, Bohyoung Kim, Jinwook Seo
Wednesday, October 27 08:00-09:30AM CDT (UTC-5) Short Papers: Social Sciences, Software Tools, Journalism, and Storytelling Session Chair: Siming Chen
GeoSneakPique: Visual autocompletion for geospatial queries Authors: Vidya Setlur, Sarah Battersby, Tracy Kam Hung Wong
Atlas: Grammar-based Procedural Generation of Data Visualizations Authors: Zhicheng Liu, Chen Chen, Francisco Morales, Yishan Zhao
On The Potential of Zines as a Medium for Visualization Authors: Andrew M McNutt
Narrative Sensemaking: Strategies for Narrative Maps Construction Authors: Brian Felipe Keith Norambuena, Tanushree Mitra, Chris North
Text Visualization and Close Reading for Journalism with Storifier Authors: Nicole Sultanum, Anastasia Bezerianos, Fanny Chevalier
Conceptualizing Visual Analytic Interventions for Content Moderation Authors: Sahaj Vaidya, Jie Cai, Soumyadeep Basu, Azadeh Naderi, Donghee Yvette Wohn, Aritra Dasgupta
How Learners Sketch Data Stories Authors: Rahul Bhargava, Dee Williams, Catherine D’Ignazio
Gemini²: Generating Keyframe-Oriented Animated Transitions Between Statistical Graphics Authors: Younghoon Kim, Jeffrey Heer
Wednesday, October 27 10:00-11:30AM CDT (UTC-5) Perspectives and Reflections Session Chair: Kwan-Liu Ma
Seek for Success: A Visualization Approach for Understanding the Dynamics of Academic Careers Authors: Yifang Wang, Tai-Quan Peng, Huihua Lu, Haoren Wang, Xiao Xie, Huamin Qu, Yingcai Wu
VitaLITy: Promoting Serendipitous Discovery of Academic Literature with Transformers & Visual Analytics Authors: Arpit Narechania, Alireza Karduni, Ryan Wesslen, Emily Wall
VIS30K: A Collection of Figures and Tables From IEEE Visualization Conference Publications Authors: Jian Chen, Meng Ling, Rui Li, Petra Isenberg, Tobias Isenberg, Michael Sedlmair, Torsten Möller, Robert S. Laramee, Han-Wei Shen, Katharina Wüsche, Qiru Wang
Gender in 30 Years of IEEE Visualization Authors: Natkamon Tovanich, Pierre Dragicevic, Petra Isenberg
E-ffective: A Visual Analytic System for Exploring the Emotion and Effectiveness of Inspirational Speeches Authors: Kevin Maher, Zeyuan Huang, Jiancheng Song, Xiaoming Deng, Yu-Kun Lai, Cuixia Ma, Hao Wang, Yong-Jin Liu, Hongan Wang
Explanatory Journeys: Visualising to Understand and Explain Administrative Justice Paths of Redress Authors: Jonathan Roberts, Peter Butcher, Ann Sherlock, Sarah Nason
Wednesday, October 27 10:00-11:30AM CDT (UTC-5) Decision Making Session Chair: Daniel Archambault
The Unmet Data Visualization Needs of Decision Makers within Organizations Authors: Evanthia Dimara, Harry Zhang, Melanie Tory, Steven Franconeri
Knowledge Rocks: Adding Knowledge Assistance to Visualization Systems Authors: Anna-Pia Lohfink, Simon Duque Anton, Heike Leitte, Christoph Garth
A Critical Reflection on Visualization Research: Where Do Decision Making Tasks Hide? Authors: Evanthia Dimara, John Stasko
From Jam Session to Concert Hall: Synchronous Communication and Collaboration Around Data in Organizations Authors: Matthew Brehmer, Robert Kosara
Causal Support: Modeling Causal Inferences with Visualizations Authors: Alex Kale, Yifan Wu, Jessica Hullman
Sibyl: Understanding and Addressing the Usability Challenges of Machine Learning In High-Stakes Decision Making Authors: Alexandra Zytek, Dongyu Liu, Rhema Vaithianathan, Kalyan Veeramachaneni
Wednesday, October 27 10:00-11:30AM CDT (UTC-5) Multi-View and Visual Environments Session Chair: Christophe Hurter
Semantic Snapping for Guided Multi-View Visualization Design Authors: Yngve S. Kristiansen, Laura Garrison, Stefan Bruckner
SightBi: Exploring Cross-View Data Relationships with Biclusters Authors: Maoyuan Sun, Abdul Rahman Shaikh, Hamed Alhoori, Jian Zhao
matExplorer: Visual Exploration on Predicting of Ionic Conductivity for Solid-State Electrolytes Authors: Jiansu Pu, Hui Shao, Boyang Gao, Zhengguo Zhu, Yanlin Zhu, Yunbo Rao, Yong Xiang
TimeTubesX: A Query-Driven Visual Exploration of Observable, Photometric, and Polarimetric Behaviors of Blazars Authors: Naoko Sawada, Makoto Uemura, Johanna Beyer, Hanspeter Pfister, Issei Fujishiro
Towards replacing physical testing of granular materials with a Topology-based Model Authors: Aniketh Venkat, Attila Gyulassy, Graham Kosiba, Amitesh Maiti, Henry Reinstein, Richard Gee, Peer-Timo Bremer, Valerio Pascucci
Tracking Internal Frames of Reference for Consistent Molecular Distribution Functions Authors: Robin Skånberg, Martin Falk, Mathieu Linares, Anders Ynnerman, Ingrid Hotz
Wednesday, October 27 10:00-11:30AM CDT (UTC-5) CG&A Papers: Data Physicalization Session Chair: Trevor Hogan
What we talk about when we talk about data physicality Authors: Dietmar Offenhuber
Data Badges: Making an Academic Profile through a DIY wearable physicalisation Authors: Georgia Panagiotidou, Sinem Görücü, Andrew Vande Moere
Move&Find: The value of kinesthetic experience in a casual data representation Authors: Jörn Hurtienne, Franzisca Maas, Astrid Carolus, Daniel Reinhardt, Cordula Baur, Carolin Wienrich
Slave Voyages:reflections on data sculptures Authors: Doris Kosminsky, Douglas Thomaz de Oliveira
Narrative Physicalisation: Supporting Interactive Engagement with Personal Data Authors: Maria Karyda, Danielle Wilde, Mette Gislev Kjærsgaard
Data Clothing and BigBarChart: designing physical data reports on indoor pollutants for individuals and communities Authors: Laura J. Perovich, Phoebe Cai, Amber Guo, Kristin Zimmerman, Katherine Paseman, Dayanna Espinoza Silva, Julia G. Brody
Wednesday, October 27 10:00-11:30AM CDT (UTC-5) Short Papers: AI+VIS Session Chair: Aritra Dasgupta
CloudFindr: A Deep Learning Cloud Artifact Masker for Satellite DEM Data Authors: Kalina Borkiewicz, Viraj Shah, J.P. Naiman, Chuanyue Shen, Stuart Levy, Jeffrey D Carpenter
An Exploration And Validation of Visual Factors in Understanding Classification Rule Sets Authors: Jun Yuan, Oded Nov, Enrico Bertini
Fast & Accurate Gaussian Kernel Density Estimation Authors: Jeffrey Heer
“Why did my AI agent lose?”: Visual Analytics for Scaling Up AAR/AI Authors: Delyar Tabatabai, Anita Ruangrotsakun, Jed Irvine, Jonathan Dodge, Zeyad Shureih, Kin-Ho Lam, Margaret Burnett, Alan Paul Fern, Minsuk Kahng
VAINE: Visualization and AI for Natural Experiments Authors: Grace Guo, Maria Glenski, Zhuanyi Huang, Emily Saldanha, Alex Endert, Svitlana Volkova, Dustin L Arendt
Semantic Explanation of Interactive Dimensionality Reduction Authors: Yali Bian, Chris North, Eric Krokos, Sarah Joseph
AdViCE: Aggregated Visual Counterfactual Explanations for Machine Learning Model Validation Authors: Steffen Holter, Oscar Alejandro Gomez, Jun Yuan, Enrico Bertini
Contrastive Identification of Covariate Shift in Image Data Authors: Matthew Olson, Thuy-Vy Nguyen, Gaurav Dixit, Neale Ratzlaff, Weng-Keen Wong, Minsuk Kahng
Wednesday, October 27 12:00-01:30PM CDT (UTC-5) Recommendation and Automation Session Chair: Torsten Möller
InfoColorizer: Interactive Recommendation of Color Palettes for Infographics Authors: Lin-Ping Yuan, Ziqi Zhou, Jian Zhao, Yiqiu Guo, Fan Du, Huamin Qu
A Mixed-Initiative Approach to Reusing Infographic Charts Authors: Weiwei Cui, Jinpeng Wang, He Huang, Yun Wang, Chin-Yew Lin, Haidong Zhang, Dongmei Zhang
Kori: Interactive Synthesis of Text and Charts in Data Documents Authors: Shahid Latif, Zheng Zhou, Yoon Kim, Fabian Beck, Nam Wook Kim
Deconstructing Categorization in Visualization Recommendation: A Taxonomy and Comparative Study Authors: Doris Jung-Lin Lee, Vidya Setlur, Melanie Tory, Karrie Karahalios, Aditya Parameswaran
KG4Vis: A Knowledge Graph-Based Approach for Visualization Recommendation Authors: Haotian Li, Yong Wang, Songheng Zhang, Yangqiu Song, Huamin Qu
VizLinter: A Linter and Fixer Framework for Data Visualization Authors: Qing Chen, Fuling Sun, Xinyue Xu, Zui Chen, Jiazhe Wang, Nan Cao
Wednesday, October 27 12:00-01:30PM CDT (UTC-5) Immersive Environments, Personal Vis, and Dashboards Session Chair: Yalong Yang
Propagating Visual Designs to Numerous Plots and Dashboards Authors: Saiful Khan, Phong Nguyen, Alfie Abdul-Rahman, Benjamin Bach, Min Chen, Euan Freeman, Cagatay Turkay
Exploring the Personal Informatics Analysis Gap: “There’s a Lot of Bacon” Authors: Jimmy Moore, Pascal Goffin, Jason Wiese, Miriah Meyer
What’s the Situation with Situated Visualization? A Survey and Perspectives on Situatedness Authors: Nathalie Bressa, Henrik Korsgaard, Aurélien Tabard, Steven Houben, Jo Vermeulen
TIVEE: Visual Exploration and Explanation of Badminton Tactics in Immersive Visualizations Authors: Xiangtong Chu, Xiao Xie, Shuainan Ye, Haolin Lu, Hongguang Xiao, Zeqing Yuan, Zhutian Chen, Hui Zhang, Yingcai Wu
Touch and Beyond: Comparing Physical and Virtual Reality Visualizations Authors: Kurtis Danyluk, Teoman Ulusoy, Wei Wei, Wesley Willett
An Automated Approach to Reasoning About Task-Oriented Visualization Insights in Responsive Visualization Authors: Hyeok Kim, Ryan Rossi, Abhraneel Sarma, Dominik Moritz, Jessica Hullman
Wednesday, October 27 12:00-01:30PM CDT (UTC-5) Multi-Dimensional Data Session Chair: Michael Sedlmair
Imma Sort by Two or More Attributes With Interpretable Monotonic Multi-Attribute Sorting Authors: Yan Lyu, Fan Gao, I-Shuen Wu, Brian Y. Lim
Integrated Dual Analysis of Quantitative and Qualitative High-Dimensional Data Authors: Juliane Müller, Laura Garrison, Philipp Ulbrich, Stefanie Schreiber, Stefan Bruckner, Helwig Hauser, Steffen Oeltze-Jafra
Revisiting Dimensionality Reduction Approaches for Visual Cluster Analysis: An Empirical Study Authors: Jiazhi Xia, Yuchen Zhang, Jie Song, Yang Chen, Yunhai Wang, Shixia Liu
DimLift: Interactive Hierarchical Data Exploration through Dimensional Bundling Authors: Laura Garrison, Juliane Müller, Stefanie Schreiber, Steffen Oeltze-Jafra, Helwig Hauser, Stefan Bruckner
Attribute-based Explanations of Non-Linear Embeddings of High-Dimensional Data Authors: Jan-Tobias Sohns, Michaela Schmitt, Fabian Jirasek, Hans Hasse, Heike Leitte
Measuring and Explaining the Inter-Cluster Reliability of Multidimensional Projections Authors: Hyeon Jeon, Hyung-Kwon Ko, Jaemin Jo, Youngtaek Kim, Jinwook Seo
Wednesday, October 27 12:00-01:30PM CDT (UTC-5) CG&A Papers: Visualizing big issues: Culture, Climate Change, and Communities Session Chair: Kai Xu
Dynamic 3D Visualization of Climate Model Development and Results Authors: Jeremy Walton, Samantha Adams, Wolfgang Hayek, Piotr Florek, Harold Dyson
Exploring the Design Space of Sankey Diagrams for the Food-Energy-Water Nexus Authors: Brandon Mathis, Yuxin Ma, Michelle Mancenido, Ross Maciejewski
QuteVis: Visually Studying Transportation Patterns Using Multi-Sketch Query of Joint Traffic Situations Authors: Shamal AL-Dohuki, Ye Zhao, Farah Kamw, Jing Yang, Xinyue Ye, Wei Chen
Many Views Are Not Enough: Designing for Synoptic Insights in Cultural Collections Authors: Florian Windhager, Saminu Salisu, Roger A. Leite, Velitchko Filipov, Silvia Miksch, Günther Schreder, Eva Mayr
CLEVis: A Semantic Driven Visual Analytics System for Community Level Events Authors: Chao Ma, Ye Zhao, Andrew Curtis, Farah Kamw, Shamal AL-Dohuki, Jing Yang, Suphanut Jamonnak, Ismael Ali
Thursday, October 28 08:00-09:30AM CDT (UTC-5) Sports, Commerce, and Social Media Session Chair: Romain Vuillemot
Augmenting Sports Videos with VisCommentator Authors: Zhutian Chen, Shuainan Ye, Xiangtong Chu, Haijun Xia, Hui Zhang, Huamin Qu, Yingcai Wu
TacticFlow: Visual Analytics of Ever-Changing Tactics in Racket Sports Authors: Jiang Wu, Dongyu Liu, Ziyang Guo, Qingyang Xu, Yingcai Wu
VideoModerator: A Risk-aware Framework for Multimodal Video Moderation in E-Commerce Authors: Tan Tang, Yanhong Wu, Lingyun Yu, Yuhong Li, Yingcai Wu
A Visualization Approach for Monitoring Order Processing in E-Commerce Warehouse Authors: Junxiu Tang, Yuhua Zhou, Tan Tang, Di Weng, Boyang Xie, Lingyun Yu, Huaqiang Zhang, Yingcai Wu
MiningVis: Visual Analytics of the Bitcoin Mining Economy Authors: Natkamon Tovanich, Nicolas Soulié, Nicolas Heulot, Petra Isenberg
Real-Time Visual Analysis of High-Volume Social Media Posts Authors: Johannes Knittel, Steffen Koch, Tan Tang, Wei Chen, Yingcai Wu, Shixia Liu, Thomas Ertl
Thursday, October 28 08:00-09:30AM CDT (UTC-5) Studies and Evaluation Methodology Session Chair: Cindy Xiong
CoUX: Collaborative Visual Analysis of Think-Aloud Usability Test Videos for Digital Interfaces Authors: Ehsan Jahangirzadeh Soure, Emily Kuang, Mingming Fan, Jian Zhao
Professional Differences: A Comparative Study of Visualization Task Performance and Spatial Ability Across Disciplines Authors: Kyle Hall, Anthony Kouroupis, Anastasia Bezerianos, Danielle Albers Szafir, Christopher Collins
Rainbow Dash: Intuitiveness, Interpretability and Memorability of the Rainbow Color Scheme in Visualization Authors: Izabela Golebiowska, Arzu Çöltekin
Understanding Data Visualization Design Practice Authors: Paul Parsons
Learning Objectives, Insights, and Assessments: How Specification Formats Impact Design Authors: Elsie Lee, Shiqing He, Eytan Adar
Untidy Data: The Unreasonable Effectiveness of Tables Authors: Lyn Bartram, Michael Correll, Melanie Tory
Thursday, October 28 08:00-09:30AM CDT (UTC-5) Accessible Visualization and Natural Language Session Chair: Melanie Tory
Accessible Visualization via Natural Language Descriptions: A Four-Level Model of Semantic Content Authors: Alan Lundgard, Arvind Satyanarayan
Towards Understanding Sensory Substitution for Accessible Visualization: An Interview Study Authors: Pramod Chundury, Biswaksen Patnaik, Yasmin Reyazuddin, Christine Tang, Jonathan Lazar, Niklas Elmqvist
Communicating Visualizations without Visuals: Investigation of Visualization Alternative Text for People with Visual Impairments Authors: Crescentia Jung, Shubham Mehta, Atharva Kulkarni, Yuhang Zhao, Yea-Seul Kim
Natural Language to Visualization by Neural Machine Translation Authors: Yuyu Luo, Nan Tang, Guoliang Li, Jiawei Tang, Chengliang Chai, Xuedi Qin
GenNI: Human-AI Collaboration for Data-Backed Text Generation Authors: Hendrik Strobelt, Jambay Kinley, Robert Krüger, Johanna Beyer, Hanspeter Pfister, Alexander Rush
Words of Estimative Correlation: Studying Verbalizations of Scatterplots Authors: Rafael Henkin, Cagatay Turkay
Thursday, October 28 08:00-09:30AM CDT (UTC-5) Flow, Topology, and Fields Session Chair: Gerik Scheuermann
FTK: A Simplicial Spacetime Meshing Framework for Robust and Scalable Feature Tracking Authors: Hanqi Guo, David Lenz, Jiayi Xu, Xin Liang, Wenbin He, Iulian R. Grindeanu, Han-Wei Shen, Tom Peterka, Todd Munson, Ian Foster
A Progressive Approach to Scalar Field Topology Authors: Jules Vidal, Pierre Guillou, Julien Tierny
Unordered Task-Parallel Augmented Merge Tree Construction Authors: Kilian Werner, Christoph Garth
Wasserstein Distances, Geodesics and Barycenters of Merge Trees Authors: Mathieu Pont, Jules Vidal, Julie Delon, Julien Tierny
Optimization and Augmentation for Data Parallel Contour Trees Authors: Hamish A. Carr, Oliver Rübel, Gunther H. Weber, James P. Ahrens
A Domain-Oblivious Approach for Learning Concise Representations of Filtered Topological Spaces for Clustering Authors: Yu Qin, Brittany Terese Fasy, Carola Wenk, Brian Summa
Thursday, October 28 10:00-11:30AM CDT (UTC-5) Grammar and Learning Session Chair: Dominik Moritz
ChartSeer: Interactive Steering Exploratory Visual Analysis with Machine Intelligence Authors: Jian Zhao, Mingming Fan, Mi Feng
Net2Vis - A Visual Grammar for Automatically Generating Publication-Tailored CNN Architecture Visualizations Authors: Alex Bäuerle, Christian van Onzenoodt, Timo Ropinski
Gosling: A Grammar-based Toolkit for Scalable and Interactive Genomics Data Visualization Authors: Sehi L’Yi, Qianwen Wang, Fritz Lekschas, Nils Gehlenborg
THALIS: Human-Machine Analysis of Longitudinal Symptoms in Cancer Therapy Authors: Carla Floricel, Md Nafiul Nipu, Mikayla Biggs, Andrew Wentzel, Guadalupe Canahuate, Lisanne van Dijk, Abdallah Mohamed, Clifton David Fuller, G. Elisabeta Marai
MultiVision: Designing Analytical Dashboards with Deep Learning Based Recommendation Authors: Aoyu Wu, Yun Wang, Mengyu Zhou, Xinyi He, Haidong Zhang, Huamin Qu, Dongmei Zhang
Interactive Graph Construction for Graph-Based Semi-Supervised Learning Authors: Changjian Chen, Zhaowei Wang, Jing Wu, Xiting Wang, Lan-Zhe Guo, Yu-Feng Li, Shixia Liu
Thursday, October 28 10:00-11:30AM CDT (UTC-5) Autonomous Driving, Urban, and Spatiotemporal Data Session Chair: Cagatay Turkay
Geo-Context Aware Study of Vision-Based Autonomous Driving Models and Spatial Video Data Authors: Suphanut Jamonnak, Ye Zhao, Xinyi Huang, Md Amiruzzaman
Visual Evaluation for Autonomous Driving Authors: Yijie Hou, Chengshun Wang, Junhong Wang, Xiangyang Xue, Xiaolong Zhang, Jun Zhu, Dongliang Wang, Siming Chen
Where Can We Help? A Visual Analytics Approach to Diagnosing and Improving Semantic Segmentation of Movable Objects Authors: Wenbin He, Lincan Zou, Shekar Arvind Kumar, Liang Gou, Liu Ren
Compass: Towards Better Causal Analysis of Urban Time Series Authors: Zikun Deng, Di Weng, Xiao Xie, Jie Bao, Yu Zheng, Mingliang Xu, Wei Chen, Yingcai Wu
Visual Cascade Analytics of Large-scale Spatiotemporal Data Authors: Zikun Deng, Di Weng, Yuxuan Liang, Jie Bao, Yu Zheng, Tobias Schreck, Mingliang Xu, Yingcai Wu
DDLVis: Real-time Visual Query of Spatiotemporal Data Distribution via Density Dictionary Learning Authors: Chenhui Li, George Baciu, Yunzhe WANG, Junjie Chen, Changbo Wang
Thursday, October 28 10:00-11:30AM CDT (UTC-5) Scalability and Rendering Session Chair: Hanqi Guo
Interactive Focus+Context Rendering for Hexahedral Mesh Inspection Authors: Christoph Neuhauser, Junpeng Wang, Rüdiger Westermann
Differentiable Direct Volume Rendering Authors: Sebastian Weiss, Rüdiger Westermann
Accelerating Unstructured Mesh Point Location with RT Cores Authors: Nate Morrical, Ingo Wald, Will Usher, Valerio Pascucci
Probabilistic Occlusion Culling using Confidence Maps for High-Quality Rendering of Large Particle Data Authors: Mohamed Ibrahim, Peter Rautek, Guido Reina, Marco Agus, Markus Hadwiger
A Memory Efficient Encoding for Ray Tracing Large Unstructured Data Authors: Ingo Wald, Nate Morrical, Stefan Zellmann
Pyramid-based Scatterplots Sampling for Progressive and Streaming Data Visualization Authors: Xin Chen, Jian Zhang, Chi-Wing Fu, Jean-Daniel Fekete, Yunhai Wang
Thursday, October 28 10:00-11:30AM CDT (UTC-5) Short Papers: Graphs, Charts, and Perception Session Chair: Tanja Blascheck
TimeElide: Visual Analysis of Non-Contiguous Time Series Slices Authors: Michael Oppermann, Luce Liu, Tamara Munzner
Semantic Resizing of Charts Through Generalization: A Case Study with Line Charts Authors: Vidya Setlur, Haeyong Chung
Bayesian Modelling of Alluvial Diagram Complexity Authors: Anjana Arunkumar, Shashank Ginjpalli, Chris Bryan
When Red Means Good, Bad, or Canada: Exploring People’s Reasoning for Choosing Color Palettes Authors: Jarryullah Ahmad, Elaine Huynh, Fanny Chevalier
Does the Layout Really Matter? A Study on Visual Model Accuracy Estimation Authors: Nicolas Grossmann, Jürgen Bernard, Michael Sedlmair, Manuela Waldner
Histogram binning revisited with a focus on human perception Authors: Raphael Sahann, Torsten Möller, Johanna Schmidt
Fixation and Creativity in Data Visualization Design: Experiences and Perspectives of Practitioners Authors: Paul Parsons, Prakash Chandra Shukla, Chorong Park
Towards a Survey on Static and Dynamic Hypergraph Visualizations Authors: Maximilian T. Fischer, Alexander Frings, Daniel Keim, Daniel Seebacher
Thursday, October 28 12:00-01:30PM CDT (UTC-5) Time Series and Events Session Chair: Wolfgang Aigner
Interactive Visual Exploration of Longitudinal Historical Career Mobility Data Authors: Yifang Wang, Hongye Liang, Xinhuan Shu, Jiachen Wang, Ke Xu, Zikun Deng, Cameron Campbell, Bijia Chen, Yingcai Wu, Huamin Qu
KD-Box: Line-segment-based KD-tree for Interactive Exploration of Large-scale Time-Series Data Authors: Yue Zhao, Jian Zhang, Chi-Wing Fu, Mingliang Xu, Dominik Moritz, Yunhai Wang
Sequen-C: A Multilevel Overview of Temporal Event Sequences Authors: Jessica Magallanes, Tony Stone, Paul Morris, Suzanne Mason, Steven Wood, Maria-Cruz Villa-Uriol
EVis: Visually Analyzing Environmentally Driven Events Authors: Tinghao Feng, Jing Yang, Martha-Cary Eppes, Zhaocong Yang, Faye Moser
HisVA: a Visual Analytics System for Learning History Authors: Dongyun Han, Gorakh Parsad, Hwiyeon Kim, Jaekyom Shim, Oh-Sang Kwon, Kyung Son, Jooyoung Lee, Isaac Cho, Sungahn Ko
SSR-TVD: Spatial Super-Resolution for Time-Varying Data Analysis and Visualization Authors: Jun Han, Chaoli Wang
Thursday, October 28 12:00-01:30PM CDT (UTC-5) Graphs and Trees Session Chair: Jean-Daniel Fekete
Multi-level Area Balancing of Clustered Graphs Authors: Hsiang-Yun Wu, Martin Nöllenburg, Ivan Viola
Understanding Missing Links in Bipartite Networks with MissBiN Authors: Jian Zhao, Maoyuan Sun, Francine Chen, Patrick Chiu
A State-of-the-Art Survey of Tasks for Tree Design and Evaluation with a Curated Task Dataset Authors: Aditeya Pandey, Uzma Syeda, Chaitya Shah, John Alexis Guerra Gomez, Michelle A. Borkin
Edge-Path Bundling: A Less Ambiguous Edge Bundling Approach Authors: Markus Wallinger, Daniel Archambault, David Auber, Martin Nöllenburg, Jaakko Peltonen
STRATISFIMAL LAYOUT: A Modular Optimization Model for Laying Out Layered Node-link Network Visualizations Authors: Sara Di Bartolomeo, Mirek Riedewald, Wolfgang Gatterbauer, Cody Dunne
Interactive Visual Pattern Search on Graph Data via Graph Representation Learning Authors: Huan Song, Zeng Dai, Panpan Xu, Liu Ren
Thursday, October 28 12:00-01:30PM CDT (UTC-5) Mitigating Bias Session Chair: Evanthia Dimara
Left, Right, and Gender: Exploring Interaction Traces to Mitigate Human Biases Authors: Emily Wall, Arpit Narechania, Adam Coscia, Jamal Paden, Alex Endert
VisQA: X-raying Vision and Language Reasoning in Transformers Authors: Theo Jaunet, Corentin Kervadec, Romain Vuillemot, Grigory Antipov, Moez Baccouche, Christian Wolf
The Weighted Average Illusion: Biases in Perceived Mean Position in Scatterplots Authors: Matt-Heun Hong, Jessica Witt, Danielle Albers Szafir
Impact of Cognitive Biases on Progressive Visualization Authors: Marianne Procopio, Ab Mosca, Carlos Scheidegger, Eugene Wu, Remco Chang
Improving Visualization Interpretation Using Counterfactuals Authors: Smiti Kaul, David Borland, Nan Cao, David Gotz
Lumos: Increasing Awareness of Analytic Behavior during Visual Data Analysis Authors: Arpit Narechania, Adam Coscia, Emily Wall, Alex Endert
Thursday, October 28 12:00-01:30PM CDT (UTC-5) Short Papers: Applications Session Chair: Michael Krone
A Visual Analytics System for Water Distribution System Optimization Authors: Yiran Li, Erin Musabandesu, Takanori Fujiwara, Frank J. Loge, Kwan-Liu Ma
CellProfiler Analyst Web (CPAW) - Exploration, analysis, and classification of biological images on the web Authors: Bella Baidak, Yahiya Hussain, Emma Kelminson, Thouis Ray Jones, Loraine Franke, Daniel Haehn
Inspecting the Process of Bank Credit Rating via Visual Analytics Authors: Qiangqiang Liu, Tangzhi Ye, Zhihua Zhu, Xiaojuan Ma, Quan Li
Where and Why is My Bot Failing? A Visual Analytics Approach for Investigating Failures in Chatbot Conversation Flows Authors: Avi Yaeli, Sergey Zeltyn
AiR: An Augmented Reality Application for Visualizing Air Pollution Authors: Noble Saji Mathews, Sridhar Chimalakonda, Suresh Jain
ConVIScope: Visual Analytics for Exploring Patient Conversations Authors: Raymond Li, Enamul Hoque, Giuseppe Carenini, Richard Lester, Raymond Chau
Visually Connecting Historical Figures Through Event Knowledge Graphs Authors: Shahid Latif, Shivam Agarwal, Simon Gottschalk, Carina Chrosch, Yanick Christian Tchenko, Felix Feit, Johannes Jahn, Tobias Braun, Elena Demidova, Fabian Beck
Understanding the Effects of Visualizing Missing Values on Visual Data Exploration Authors: Hayeong Song, Yu Fu, Bahador Saket, John Stasko
Friday, October 29 08:00-09:30AM CDT (UTC-5) Data-Driven Communication and Storytelling Session Chair: Zhicheng Liu
A Design Space for Applying the Freytag’s Pyramid Structure to Data Stories Authors: Leni Yang, Xian XU, Xingyu Lan, Ziyan Liu, Shunan Guo, Yang Shi, Huamin Qu, Nan Cao
Kineticharts: Augmenting Affective Expressiveness of Charts in Data Stories with Animation Design Authors: Xingyu Lan, Yang Shi, Yanqiu Wu, Xiaohan Jiao, Nan Cao
Interactive Data Comics Authors: Zezhong Wang, Hugo Romat, Fanny Chevalier, Nathalie Henry Riche, Dave Murray-Rust, Benjamin Bach
Declutter and Focus: Empirically Evaluating Design Guidelines for Effective Data Communication Authors: Kiran Ajani, Elsie Lee, Cindy Xiong, Cole Knaflic, William Kemper, Steven Franconeri
Showing Data about People: A Design Space of Anthropographics Authors: Luiz Morais, Yvonne Jansen, Nazareno Andrade, Pierre Dragicevic
Visual Arrangements of Bar Charts Influence Comparisons in Viewer Takeaways Authors: Cindy Xiong, Vidya Setlur, Benjamin Bach, Kylie Lin, Eunyee Koh, Steven Franconeri
Friday, October 29 08:00-09:30AM CDT (UTC-5) Glyphs and Sets Session Chair: Johannes Fuchs
Generative Design Inspiration for Glyphs with Diatoms Authors: Matthew Brehmer, Robert Kosara, Carmen Hull
GlyphCreator: Towards Automatic Generation of Example-based Circular Glyphs Authors: Lu Ying, Tan Tang, Yuzhe Luo, Lvkesheng Shen, Xiao Xie, Lingyun Yu, Yingcai Wu
Shape-driven Coordinate Ordering for Star Glyph Sets via Reinforcement Learning Authors: Ruizhen Hu, Bin Chen, Juzhan Xu, Oliver van Kaick, Oliver Deussen, Hui Huang
F2-Bubbles: Faithful Bubble Set Construction and Flexible Editing Authors: Yunhai Wang, Da Cheng, Zhirui Wang, Jian Zhang, Liang Zhou, Gaoqi He, Oliver Deussen
spEuler: Semantics-preserving Euler Diagrams Authors: Rebecca Kehlbeck, Jochen Görtler, Yunhai Wang, Oliver Deussen
Visualization of 3D Stress Tensor Fields Using Superquadric Glyphs on Displacement Streamlines Authors: Mohak Patel, David H. Laidlaw
Friday, October 29 08:00-09:30AM CDT (UTC-5) Uncertainty Session Chair: Matthew Kay
Visualizing Uncertainty in Probabilistic Graphs with Network Hypothetical Outcome Plots (NetHOPs) Authors: Dongping Zhang, Eytan Adar, Jessica Hullman
Implicit Error, Uncertainty and Confidence in Visualization: an Archaeological Case Study Authors: Georgia Panagiotidou, Ralf Vandam, Jeroen Poblome, Andrew Moere
Examining Effort in 1D Uncertainty Communication Using Individual Differences in Working Memory and NASA-TLX Authors: Spencer Castro, Helia Hosseinpour, P. Samuel Quinan, Lace Padilla
Can Visualization Alleviate Dichotomous Thinking? Effects of Visual Representations on the Cliff Effect Authors: Jouni Helske, Satu Helske, Matthew Cooper, Anders Ynnerman, Lonni Besançon
Effect of Uncertainty Visualizations on Myopic Loss Aversion and Equity Premium Puzzle in Retirement Investment Decisions Authors: Ryan Wesslen, Alireza Karduni, Doug Markant, Wenwen Dou
Visualization Equilibrium Authors: Paula Kayongo, Glenn Sun, Jason Hartline, Jessica Hullman
Friday, October 29 08:00-09:30AM CDT (UTC-5) Short Papers: Mathematics, Topology, and Rendering Session Chair: Bei Wang
Time-Varying Fuzzy Contour Trees Authors: Anna-Pia Lohfink, Frederike Gartzky, Florian Wetzels, Luisa Vollmer, Christoph Garth
Ray-traced Shell Traversal of Tetrahedral Meshes for Direct Volume Visualization Authors: Alper Şahıstan, Serkan Demirci, Nate Morrical, Stefan Zellmann, Aytek Aman, Ingo Wald, Ugur Gudukbay
Segmentation driven Peeling for Visual Analysis of Electronic Transitions Authors: Mohit Sharma, Talha Bin Masood, Signe Sidwall Thygesen, Mathieu Linares, Ingrid Hotz, Vijay Natarajan
Exact Analytical Parallel Vectors Authors: Hanqi Guo, Tom Peterka
Uncertainty Visualization of the Marching Squares and Marching Cubes Topology Cases Authors: Tushar M. Athawale, Sudhanshu Sane, Chris R. Johnson
Intercept Graph: An Interactive Radial Visualization for Comparison of State Changes Authors: Shaolun Ruan, Yong Wang, Qiang Guan
Automatic Y-axis Rescaling in Dynamic Visualizations Authors: Jacob Fisher, Remco Chang, Eugene Wu
A Mixed-Initiative Visual Analytics Approach for Qualitative Causal Modeling Authors: Fahd Husain, Pascale Proulx, Meng-Wei Chang, Rosa Romero-Gómez, Holland Marie Vasquez
Friday, October 29 10:00-11:30AM CDT (UTC-5) Model Evaluation Session Chair: Adam Perer
Inspecting the Running Process of Horizontal Federated Learning via Visual Analytics Authors: Quan Li, Xiguang Wei, Huanbin Lin, Yang Liu, Tianjian Chen, Xiaojuan Ma
An Evaluation-Focused Framework for Visualization Recommendation Algorithms Authors: Zehua Zeng, Phoebe Moh, Fan Du, Jane Hoffswell, Tak Yeon Lee, Sana Malik, Eunyee Koh, Leilani Battle
Visual Analysis of Hyperproperties for Understanding Model Checking Results Authors: Tom Horak, Norine Coenen, Niklas Metzger, Christopher Hahn, Tamara Flemisch, Julián Méndez, Dennis Dimov, Bernd Finkbeiner, Raimund Dachselt
FairRankVis: A Visual Analytics Framework for Exploring Algorithmic Fairness in Graph Mining Models Authors: Tiankai Xie, Yuxin Ma, Jian Kang, Hanghang Tong, Ross Maciejewski
embComp: Visual Interactive Comparison of Vector Embeddings Authors: Florian Heimerl, Christoph Kralj, Torsten Möller, Michael Gleicher
VBridge: Connecting the Dots Between Features and Data to Explain Healthcare Models Authors: Furui Cheng, Dongyu Liu, Fan Du, Yanna Lin, Alexandra Zytek, Haomin Li, Huamin Qu, Kalyan Veeramachaneni
Friday, October 29 10:00-11:30AM CDT (UTC-5) Biological and Medical Visualization Session Chair: Barbora Kozlikova
COVID-view: Diagnosis of COVID-19 using Chest CT Authors: Shreeraj Jadhav, Gaofeng Deng, Marlene Zawin, Arie E. Kaufman
ThreadStates: State-based Visual Analysis of Disease Progression Authors: Qianwen Wang, Tali Mazor, Theresa Harbig, Ethan Cerami, Nils Gehlenborg
Loon: Using Exemplars to Visualize Large Scale Microscopy Data Authors: Devin Lange, Eddie Polanco, Robert Judson-Torres, Thomas Zangle, Alexander Lex
Scope2Screen: Focus+Context Techniques for Pathology Tumor Assessment in Multivariate Image Data Authors: Jared Jessup, Robert Krüger, Simon Warchol, John Hoffer, Jeremy Muhlich, Cecily C. Ritch, Giorgio Gaglia, Shannon Coy, Yu-An Chen, Jia-Ren Lin, Sandro Santagata, Peter Sorger, Hanspeter Pfister
Multiscale Unfolding: Illustratively Visualizing the Whole Genome at a Glance Authors: Sarkis Halladjian, David Kouril, Haichao Miao, Eduard Gröller, Ivan Viola, Tobias Isenberg
Friday, October 29 10:00-11:30AM CDT (UTC-5) Efficient Representation and Layout Session Chair: Markus Hadwiger
Rapid Labels: Point-Feature Labeling on GPU Authors: Václav Pavlovec, Ladislav Čmolík
Scalable Scalable Vector Graphics: Automatic Translation of Interactive SVGs to a Multithread VDOM for Fast Rendering Authors: Michail Schwab, David Saffo, Nicholas Bond, Shash Sinha, Cody Dunne, Jeff Huang, James Tompkin, Michelle A. Borkin
Probabilistic Data-Driven Sampling via Multi-Criteria Importance Analysis Authors: Ayan Biswas, Soumya Dutta, Earl Lawrence, John Patchett, Jon C. Calhoun, James P. Ahrens
An Efficient Dual-Hierarchy tSNE Minimization Authors: Mark van de Ruit, Markus Billeter, Elmar Eisemann
Joint t-SNE for Comparable Projections of Multiple High-Dimensional Datasets Authors: Yinqiao Wang, Lu Chen, Jaemin Jo, Yunhai Wang
Automatic Polygon Layout for Primal-Dual Visualization of Hypergraphs Authors: Botong Qu, Eugene Zhang, Yue Zhang
A Review of the Hand Gesture Recognition System: Current Progress and Future Directions
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
IEEE PAPER 2021, ENGINEERING RESEARCH FREE DOWNLOAD
Cse 2021 ieee paper, electronics-ece 2021, eee-electrical-electronics-engineering 2021, medical 2020, mechanical engineering 2020 most popular civil engineering basic science.
Wireless networks use radio waves to connect devices such as laptops to the Internet, the business network and applications. When laptops are connected to Wi-Fi hot spots in public places, the connection is established to that business’s wireless network. three different types of wireless networks – WAN, LAN and PAN: Wireless Wide Area Networks (WWAN): […]
An online voting system is a software platform that allows groups to securely conduct votes and elections. High-quality online voting systems balance ballot security, accessibility, and the overall requirements of an organization’s voting event. Online voting tools and online election voting systems help you make important decisions by gathering the input of your group in […]
Big Data is a collection of data that is huge in volume, yet growing exponentially with time. It is a data with so large size and complexity that none of traditional data management tools can store it or process it efficiently. Big data is also a data but with huge size. Big Data helps the […]
A 3D hologram displays products, objects, and animated sequences three-dimensionally and enables seemingly real objects or animations to appear to float completely freely in space.This method of using 3D holograms opens up a completely new, revolutionary way of presenting products Holograms are photographic recordings of 3D scenes. Unlike a camera, which captures one view through […]
Human-computer interaction studies the design and use of computer technology, focused on the interfaces between people and computers. Researchers in the field of HCI observe the ways in which humans interact with computers and they design technologies that let humans interact with computers in novel ways Human-computer interaction (HCI) is a multidisciplinary subject that focuses […]
Cloud computing is the on-demand availability of computer system resources, especially data storage and computing power, without direct active management by the user. The term is generally used to describe data centers available to many users over the Internet Cloud computing is the delivery of different services through the Internet. These resources include tools and […]
an attack is any attempt to expose, alter, disable, destroy, steal or gain information through unauthorized access to or make unauthorized use of an asset. Common types of cyber attacks Malware. Malware is a term used to describe malicious software, including spyware, ransomware, viruses, and worms. Phishing. Man-in-the-middle attack. Denial-of-service attack. SQL injection. Zero-day exploit. […]
One of the main ways cloud providers can cut down on energy consumption is through saving energy from their data centers. Data centers play a significant role in the reduction of energy consumption as they are also the leading powerhouse for cloud resources Cloud computing is the well-known technology for scaling of extensive data and […]
Arduino is an open-source hardware and software company, project and user community that designs and manufactures single-board microcontrollers and microcontroller kits for building digital devices and interactive objects that can sense and control both physically and digitally. AUTOMATIC IRRIGATION SYSTEM USING ARDUINO free downloadNowadays, the increase in population has led to water scarcity in most […]
Very large-scale integration is the process of creating an integrated circuit by combining millions of MOS transistors onto a single chip. VLSI began in the 1970s when MOS integrated circuit chips were widely adopted, enabling complex semiconductor and telecommunication technologies to be developed. VLSI circuits are used everywhere, real applications include microprocessors in a personal […]
Wireless Sensor Networks (WSNs) can be defined as a self-configured and infrastructure-less wireless networks to monitor physical or environmental conditions, such as temperature, sound, vibration, pressure, motion or pollutants and to cooperatively pass their data through the network to a main location or sink where Applications of WSN Internet of Things (IOT) Surveillance and Monitoring […]
Renewable energy is useful energy that is collected from renewable resources, which are naturally replenished on a human timescale, including carbon neutral sources like sunlight, wind, rain, tides, waves, and geothermal heat Solar. Wind Energy. Hydroelectric. Ocean Energy. Geothermal Energy. Biomass. Hydrogen. A renewable energy source means energy that is sustainable – something that can’t […]
hybrid electric scooter model developed and simulated using Matlab/Simulink. This hybrid scooter modeled has a parallel hybrid structure. The main propulsion units consist of a two stroke internal combustion engine and a hub motor attached to the front wheel of the scooter. The methodology used to optimize the energy and fuel consumption of the hybrid […]
The main task of a circuit breaker is to interrupt fault currents and to isolate faulted parts of the system. A circuit breaker must also be able to interrupt a wide variety of other currents at system voltage such as capacitive currents, small inductive currents, and load currents. Air circuit breakers are commonly used in […]
After collection and transportation to recycling facilities, materials in the e-waste stream must be processed and separated into clean commodities that can be used to make new products. Efficient separation of materials is the foundation of electronics recycling. E-waste recyclers use processes such as open incineration and acid-leeching. This situation could be improved by creating […]
The automatic detection of cold steel weapons handled by one or multiple persons in surveillance videos can help reducing crimes. However, the detection of these metallic objects in videos faces an important problem: their surface reflectance under medium to high illumination conditions blurs their shapes in the image and hence makes their detection impossible. The […]
AutoX makes retail-based autonomous vehicles. The company’s vehicles combine AI software, sensors, real-time cameras and thousands of test miles, both virtual and real, to ensure safe decisions on the road Artificial Intelligence has the power to completely reform automotive manufacturing and make processes quicker and more efficient. The rising intelligence of robots may soon lead […]
CSE-2021-COMPUTER SCIENCE ENGINEERING
Free ieee paper, ieee projects 2022, seminar reports, free ieee projects ieee papers.

Call for Journal Papers
Important dates.
- September 2, 2020 : Abstracts due (REQUIRED)
- September 9, 2020 : Submissions due
- October 31, 2020 : Notification of first review cycle results
- December 15, 2020 : Revised paper submissions due to second review cycle
- January 8, 2021 : Final notifications
- January 22, 2021 : Camera-ready material due from authors of accepted papers
Paper abstracts complete papers must be submitted electronically through the online submission system: https://new.precisionconference.com/~vr
All VR Journal Papers submissions should be formatted using the IEEE Computer Society TVCG journal format described at http://junctionpublishing.org/vgtc/Tasks/camera_tvcg.html
IEEE VR 2021 seeks original, high-quality papers in all areas related to virtual reality (VR), including augmented reality (AR), mixed reality (MR), and 3D user interfaces (3DUIs).
Inquiries contact: journalpapers2021 [at] ieeevr.org
Submission Guidelines
Paper abstracts and complete papers must be submitted electronically through the online submission system: https://new.precisionconference.com/~vr
Each research paper should provide a validated contribution covering one or more of the following categories: methodological, technology, applications, and systems.
- Methodological papers should describe advances in theories and methods of AR/VR/MR and 3DUI, such as ethical issues, theories on presence, or human factors.
- Technology papers should describe advancements in algorithms or devices critical to AR/VR/MR and 3DUI development such as input, display, user interaction, or tracking.
- Application papers provide an important insight to the community by explaining how the authors built upon existing ideas and applied them to solve an interesting problem in a novel way. Each paper should include an evaluation of the success of the use of AR/VR/MR and/or 3DUI in the given application domain.
- System papers should indicate how the developers integrated techniques and technologies to produce an effective system, and convey any lessons learned in the process.
Each paper should include an evaluation of its contributions, such as user studies, benchmarking and/or comparison with existing systems/techniques/methods. We appreciate that due to the COVID-19 situation, in-person user studies may not be possible to perform in the necessary timescale for submission. We encourage authors to think about other ways to validate their contribution, such as qualitative studies with fewer users, expert review, online studies, etc. We encourage potential authors to engage with ongoing community discussions around these topics as they are common to many of us.
Further Details Regarding Submissions. We welcome paper submissions not exceeding 9 pages, excluding references. References may not exceed two additional pages. Continuing our cooperation with the IEEE Transactions on Visualization and Computer Graphics (TVCG), all accepted paper submissions will automatically be published in a special issue of IEEE TVCG. To meet TVCG standards, papers recommended for inclusion to TVCG will undergo a two-stage review process (see SUBMISSION DEADLINES below). Authors of papers that are determined to be acceptable to the journal subject to minor revisions during the first review cycle will be invited to submit a revised version for a second review cycle. Only papers that are accepted in this second cycle will appear in the journal issue. Papers that fail to pass the second round of reviews may proceed through further revisions to appear in a future regular issue of TVCG.
Review Duties for Authors. The increasing numbers of submissions for IEEE VR makes us all dependent on a large number of good reviewers who are willing to provide expert feedback and engage with authors on their work. To expand the reviewing pool and promote quality reviews, one author will be required to register to review up to three papers through PCS at the time of submission. Additionally, senior authors are encouraged to ask experienced junior authors to register in PCS to review papers, and then to mentor the junior author during the review process.
Ethics and Responsibility. All submissions describing research experiments with human participants must follow the appropriate ethical guidelines required by your affiliation, and authors are required to secure and report their approval by the relevant ethics commission. An approval by any ethical review board, if required by your affiliation, needs to be indicated via the submission system.
Conference Presentation. All accepted papers must be orally presented at the conference. Presentation should be in person if possible, though given the current situation with COVID-19 we expect to support authors presenting remotely. There is also the possibility for authors of relevant previously published TVCG papers (accepted within the last year) to present their work at IEEE VR 2021. Interested authors should contact the program chairs for more details.
Abstract Submission. Note that a paper abstract must be uploaded a week prior to the actual paper submission deadline. This facilitates the process of assigning reviewers, as the review process operates on a very tight schedule.
- 3D and volumetric display and projection technology
- 3D authoring
- 3D user interaction
- 3DUI metaphors
- Accessibility of immersive interfaces
- Audio interfaces and rendering
- Collaborative interactions
- Computer graphics techniques
- Crowd simulation
- Diversity and gender issues
- Embodied agents, virtual humans and (self-)avatars
- Ethical issues
- Evaluation methods
- Haptic interfaces and rendering
- Human factors and ergonomics
- Immersive / 360° video
- Immersive analytics and visualization
- Immersive games
- Input devices
- Locomotion and navigation
- Mediated and diminished reality
- Mobile, desktop or hybrid 3DUIs
- Modeling and simulation
- Multi-user and distributed systems
- Multimodal capturing and reconstruction
- Multimodal/cross-modal interaction and perception
- Multisensory interfaces and rendering
- Perception and cognition
- Presence, body ownership, and agency
- Scene description and management issues
- Software architectures, toolkits, and engineering
- Teleoperation and telepresence
- Therapy and rehabilitation
- Touch, tangible and gesture interfaces
- Tracking and sensing
- User experience and usability
Additional Submission Guidelines
All paper submissions must be in English.
Paper submissions must not have been previously published. A manuscript is considered to have been previously published if it has appeared in a peer-reviewed journal, magazine, book, or meeting proceedings that is reliably and permanently available afterward in print or electronic form to non-attendees, regardless of the language of that publication. A paper identical or substantially similar in content (in its entirety or in part) to one submitted to VR should not be simultaneously under consideration for another conference or journal during any part of the VR review process, from the submission deadline until notifications of decisions are emailed to authors.
In some situations a submission may build upon prior work. In order to fully explain the relationship between the submitted paper and prior work, authors may upload additional papers as well as a non-anonymous letter of explanation that highlights the significant changes or advances; these materials will only be seen by the primary reviewer.
Submissions will be checked for plagiarism using IEEE Crosscheck. Detection of significant plagiarism will lead to rejection. For more information about definitions of plagiarism and IEEE policies in this area, please see the IEEE plagiarism FAQ and the IEEE Publication Services and Products Board Operations Manual.
IEEE VR uses a DOUBLE-BLIND review process. This means that both the authors and the reviewers must remain anonymous to each other. Submissions ( including citations and optional videos ) must not contain information that identifies the authors, their institutions, funding sources, or their places of work. Relevant previous work by the authors must be cited in the third person to preserve anonymity. Authors should work diligently to ensure that their submissions do not expose their identities either through carelessness or intentionally. Authors that have questions/issues around the double-blind submission policy should contact the program chairs.
Failure to make reasonable attempts to adhere to the double-blind policy will result in desk rejection.
Videos. Authors are encouraged to submit videos to aid the program committee in reviewing their submissions. Videos must be submitted according to the instructions at the submission website. Videos submitted with papers will automatically be considered for possible inclusion in the video proceedings (video submissions may also be made independently, as described in the separate Call for Videos). When submitted as supporting material, videos must be free of any identifying information prior to reviewing as per the double-blind submission policy. If accepted for the video proceedings, a revised version of the materials will be requested.
Submission Deadlines
Each deadline is 23:59:59 AoE (Anywhere on Earth) == GMT/UTC-12:00 on the stated day, no matter where the submitter is located. A convenient tool to see when AoE is for your local time is setting your location at 1 and Baker Island (which uses AoE) for: https://www.timeanddate.com/worldclock/meeting.html
The submission deadlines will be strictly enforced. Requests for extensions will not be honored.
- October 30, 2020 : Notification of first review cycle results
LaTeX Templates Word Templates Sample PDF paper
- Stephan Lukosch, HIT Lab NZ, University of Canterbury, NZ
- Maud Marchal, Univ. Rennes, INSA/IRISA, FRA
- Tabitha Peck, Davidson College, USA
- Anthony Steed, University College London, UK
- Xubo Yang, Shanghai Jiao Tong University, CN

Conference Sponsors

Doctoral Consortium Sponsors

Conference Partner

© IEEEVR Conference
- IEEE Xplore Digital Library
- IEEE Standards
- IEEE Spectrum

Electric Vehicles
Abstract – This paper gives a mini overview of the recent research and works in the sector of electric vehicles. The paper describes the main part of electric vehicles and their work. The major components are battery, motor, charger, steering, and braking. The paper finally shows basic concepts of electric vehicles with working. There are electric buses in the main focus of this paper. The solar system also can be used for electric busses and this is described in this paper.
Keywords – Electric vehicle, motor, braking system, battery systems, hybrid system
I. INTRODUCTION
Electrical vehicle (EV) based on electro mechanical system. No, any internal combustion engine is used for torque development. All the power which is used is electric power as the energy source. In the electric vehicle main power source is electricity which is stored in the battery. The advantage of the highly efficient in power conversion through its proposition system of electric motor. Now in the world, there are several situations in which we cannot tolerate the environment that why we need to reduce carbon emission. In the sector of the automobile, there is a lot of petroleum used and therefore a lot of carbon emissions are occurring in the environment [1]. Electric busses work on the electricity from the power grid and also can work on the solar plates. There is a battery that can be charged and then used. All the car manufacturers have to develop at least one model in hybrid electric vehicles for the reduction in the carbon footprint. France and Japan are the countries who totally close the production of petrol vehicles by 2030. This is one more step toward pollution control and the improvement in electrical vehicles for a clean environment [2]. The table shows the various types of EVs. Image 1 shows the first electric vehicle in 1943-35 (America).
Table 1

II. MAIN COMPONENTS
There are many components in electric vehicles, some main ones are spark ignited, traction system, thermal cooling system, DC/DC converter, power electronics control, battery, motor, storage, braking system etc. [3]. Image 2 shows the main components of the electric busses. There are various parts with different function and working shown in the figure.
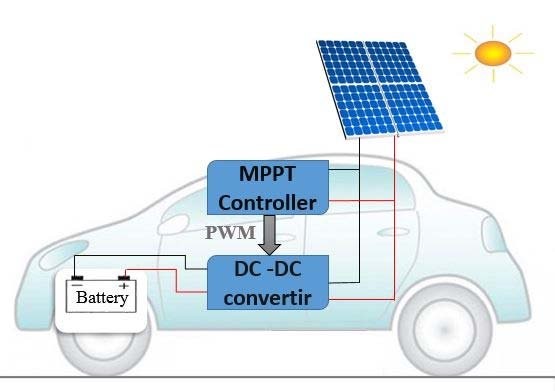
DC to DC converter: A full-bridge DC/DC converter is the frequently implemented converter for fuel-cell power conditioning when electrical isolation is needed. Full bridge DC to DC converter is suitable for high-power electrical transmission because switch voltage is not high and current are also not high [3,5]. Electric Motor Generator : Electric vehicle drive system for plug-in hybrid vehicles the integrated motor-generator set provides electric propulsion for the vehicle in its function as a motor, while work as a generator it converts mechanical braking energy into electrical energy, that is college regenerative braking system. Regenerative Braking system : In the battery-powered electric vehicle system, regenerative braking is the conversion of the electric vehicle's kinetic energy into chemical energy stored in the electric battery system, where it can be used to drive the vehicle. Recharge Station : In these stations, busses can be charged by an electrical charging system and it will convert electrical supply power into battery storage power. Battery Packs : In this battery packs are arranged and this will provide the power to the motor. Which can be charged by the recharge station. The capacity of the battery is for the 120 km distance which can be charged in 1.5 hours (nearly). Solar Cell : Solar cells can be used in an emergency for electric busses. When there is charging not available cell can work for small distances. It can be mounted on the top of the buses and it will charge through the solar system. There is a lot of space on the bus which can be utilized. The solar cell efficiency formula is shown below.
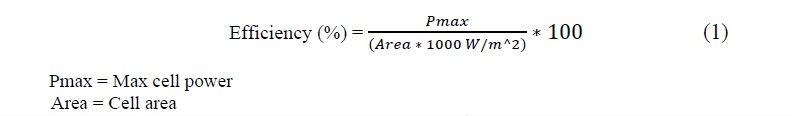
III. The Motor
There are a number of motors available for electric vehicles: DC motors, Induction motors, DC brushless motors, Permanent magnetic synchronous motors and Switched reluctance motors.
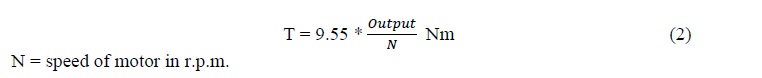
1. 2. Induction motor: It’s a very popular Alternate Current motor. It also has a large market share in controlled speed drive applications such as AC, elevator, or escalator. There are various higher power electric vehicles, for more than 10kW.

5. Switched reluctance motor: This motor specification is also good for the use of electric and hybrid vehicles. It has variable reluctance that why this machine [14]. IV. Conclusion
This paper discusses the basics of electric vehicles and the development of electric vehicles, especially electric buses. The electric vehicle is very useful for the reduction of carbon emission and the change of climate. Consumption of petroleum is also reduced due to the use of that. The paper first describes the main components of electric vehicles, it then extends the description of the components with uses. The paper provides a mini overview of electric vehicles. Acknowledgment The author acknowledges the support of various references which is very useful for this paper. References [1] Chikhi, F. El Hadri, A. Cadiou, J.C. “ ABS control design based on wheel-slip peak localization”. Proceedings of the Fifth International Workshop on Robot Motion and Control, Publication Date: 23-25 June 2005, pp.73- 77 URL: http://sersc.org/journals/index.php/IJAST/article/download/14920/7565/ [2] Beier, J. et al, “Integrating on-site Renewable Electricity Generation into a Manufacturing System with Intermittent Battery Storage from Electric Vehicles”, Procedia CIRP, Vol. 48, 2016, pp. 483-488. [3] Rahman, K.M.; Fahimi, B.; Suresh, G.; Rajarathnam, A.V.; Ehsani, M., “Advantages of switched reluctance motor applications to EV and HEV: design and control issues”, IEEE Transactions on Industry Applications, Vol. 36, Issue 1, Jan.-Feb. 2000, pp. 111 – 121. [4] K W E Cheng; “Recent Development on Electric Vehicles”, 3rd International Conference on Power Electronics system and it's application, 2009 [5] M.J. Bradley & Associates. 2013. “Electric Vehicle Grid Integration in the U.S., Europe, and China.” [6] Chan, C.C. (1996), Chau, K.T., Jiang, J.Z., Xia, W., Zhu, M., and Zhang, R., Novel permanent magnet motor drives for electric vehicles. IEEE Transactions on Industrial Electronics, Vol. 43, pp. 331-339. [7] B Smith, M. and J. Castellano. 2015. “Costs Associated with Non-Residential Electric Vehicle Supply Equipment.” [8] C Clint, J., B. Gamboa, B. Henzie, and A. Karasawa. 2015. “Considerations for Corridor Direct Current Fast Charging Infrastructure in California.” [9] Chan, C.C., Jiang, J.Z., Chen, G.H., and Chau, K.T., Computer simulation and analysis of a new polyphase multipole motor drive. IEEE Transactions on Industrial Electronics, Vol. 40, 1993, pp. 570-576. [10] Zhan, Y.J., Chan, C.C., and Chau K.T., A novel sliding-mode observer for indirect position sensing of switched reluctance motor drives, IEEE Transactions on Industrial Electronics, Vol. 46, 1999, pp. 390-397. [11] Nunes, P., M.C. Brito and T. Farias, “Synergies between electric vehicles and solar electricity penetrations in Portugal,” 2013 World Electric Vehicle Symposium and Exhibition, 2013, pp. 1-8. [12] Mwasilu, F. et al., “Electric vehicles and smart grid interaction: A review on vehicle to grid and renewable energy sources integration”, Renewable and Sustainable Energy Reviews, Vol. 34, 2014, pp. 501-516 [13] Ates, M.N. et al., “In Situ Formed Layered-Layered Metal Oxide as Bifunctional Catalyst for Li-Air Batteries”, Journal of the Electrochemical Society, Vol 163, No. 10, 2016, pp. A2464-A2474 [14] Tuffner, F. and M. Kintner-Meyer, Using Electric Vehicles to Meet Balancing Requirements Associated with Wind Power, U.S. Department of Energy Pacific Northwest National Laboratory, 2011
About the Newsletter
Editors-in-chief.

Jin-Woo Ahn Co-Editor-in-Chief

Sheldon Williamson Co-Editor-in-Chief
TEC Call for Articles 2023 - Advances in Charging Systems The TEC eNewsletter is now being indexed by Google Scholar and peer-reviewed articles are being submitted to IEEE Xplore.
To submit an article click here.
- December 2022
- August 2022
- Editorial Board
- Past Issues
Subscribe to the Newsletter
Subscribe Now
For IEEE Members
Ieee spectrum, follow ieee spectrum, support ieee spectrum, enjoy more free content and benefits by creating an account, saving articles to read later requires an ieee spectrum account, the institute content is only available for members, downloading full pdf issues is exclusive for ieee members, downloading this e-book is exclusive for ieee members, access to spectrum 's digital edition is exclusive for ieee members, following topics is a feature exclusive for ieee members, adding your response to an article requires an ieee spectrum account, create an account to access more content and features on ieee spectrum , including the ability to save articles to read later, download spectrum collections, and participate in conversations with readers and editors. for more exclusive content and features, consider joining ieee ., join the world’s largest professional organization devoted to engineering and applied sciences and get access to all of spectrum’s articles, archives, pdf downloads, and other benefits. learn more →, join the world’s largest professional organization devoted to engineering and applied sciences and get access to this e-book plus all of ieee spectrum’s articles, archives, pdf downloads, and other benefits. learn more →, access thousands of articles — completely free, create an account and get exclusive content and features: save articles, download collections, and talk to tech insiders — all free for full access and benefits, join ieee as a paying member., 15 graphs you need to see to understand ai in 2021, the 2021 ai index provides insight into jobs, publications, diversity, and more.
If you haven't had time to read the AI Index Report for 2021 , which clocks in at 222 pages, don't worry—we've got you covered. The massive document, produced by the Stanford Institute for Human-Centered Artificial Intelligence , is packed full of data and graphs, and we've plucked out 15 that provide a snapshot of the current state of AI.
Deeply interested readers can dive into the report to learn more; it contains chapters on R&D, technical performance, the economy, AI education, ethical challenges of AI applications, diversity in AI, and AI policy and national strategies.
1. We’re Living in an AI Summer
AI research is booming: More than 120,000 peer-reviewed AI papers were published in 2019. The report also notes that between 2000 and 2019, AI papers went from being 0.8 percent of all peer-reviewed papers to 3.8 percent in 2019.

2. China Takes Top Citation Honors
It's old news that Chinese researchers are publishing the most peer-reviewed papers on AI—China took that lead in 2017. The news this year is that, as of 2020, papers by Chinese researchers that were published in AI journals are receiving the largest share of citations.
Jack Clark , codirector of the AI Index Steering Committee, tells IEEE Spectrum that the data seems like "an indicator of academic success" for China, and is also a reflection of different AI ecosystems in different countries. "China has a stated policy of getting journal publications," he notes, and government agencies play a larger role in research, whereas in the United States, a good portion of R&D happens within corporations. "If you're an industry, you have less incentive to do journal articles," he says. "It's more of a prestige thing."
3. Faster Training = Better AI
This data comes from MLPerf , an effort to objectively rank the performance of machine learning systems. Image classifier systems from a variety of companies were trained on the standard ImageNet database, and ranked on the amount of time it took to train them. In 2018, it took 6.2 minutes to train the best system; in 2020 it took 47 seconds. This extraordinary improvement was enabled by the adoption of accelerator chips that are specifically designed for machine learning.
The report states the impact of this speedup: "Imagine the difference between waiting a few seconds for a system to train versus waiting a few hours, and what that difference means for the type and volume of ideas researchers explore and how risky they might be."
4. AI Doesn’t Understand Coffee Drinking
In the past years, AI has gotten really, really good at static image recognition; the next frontier in computer vision is video. Researchers are building systems that can recognize various activities from video clips, since that type of recognition could be broadly useful if ported over to the real world (think about self-driving cars, surveillance cameras, and so forth). One benchmark of performance is the ActivityNet data set, which contains nearly 650 hours of footage from a total of 20,000 videos. Of the 200 activities of daily life shown therein, AI systems had the toughest time recognizing the activity of coffee drinking in both 2019 and 2020. This seems like a major problem, since coffee drinking is the fundamental activity from which all other activities flow. Anyway, this is an area to watch over the coming years.
5. Language AI Is So Good, It Needs Harder Tests
The meteoric rise of natural language processing (NLP) seems to be following the trajectory of computer vision, which went from an academic subspecialty to widespread commercial deployment over the past decade. Today's NLP is also powered by deep learning, and Clark of the AI Index says it has inherited strategies from computer vision work, such as training on huge databases and fine-tuning for specific applications. "We're seeing these innovations flow through to another area of AI really quickly," he says.
Measuring the performance of NLP systems has become tricky: "Academics are coming up with metrics they think no one can beat, then a system comes along in six months and beats it," Clark says. This chart shows performance on two versions of a reading comprehension test called SQuAD , in which an AI language model has to answer multiple choice questions based on a paragraph of text. Version 2.0 made the task harder by incorporating unanswerable questions, which the model had to identify as such and abstain from answering. It took 25 months for a model to surpass human performance on the first version, but just 10 months for one to beat humans at the harder task.
6. A Huge Caveat
Yes, language models for tasks like speech recognition and text generation have gotten really good in general. But they have some specific failings that could derail commercial use unless addressed. Many have serious problems with harmful bias, such as performing poorly on a subset of people or generating text that reflects historical prejudice. The example here shows error rates in speech-recognition programs from leading companies.
There's a larger issue with bias here that bedevils all forms of AI, including computer vision and decision-support tools. Researchers test their systems for performance, but few test their systems for harmful bias.
7. The AI Job Market Is Global
Data from LinkedIn shows that Brazil, India, Canada, Singapore, and South Africa had the highest growth in AI hiring from 2016 to 2020. That doesn't mean those countries have the most jobs in absolute terms (the United States and China continue to hold the top spots there), but it will be interesting to see what emerges from those countries pushing hard on AI. LinkedIn found that the global pandemic did not put a dent in AI hiring in 2020.
It's worth noting that a smaller percentage of the workforce in both India and China have profiles on LinkedIn, so data from those countries may not be fully representative.
8. Corporate Investment Can’t Stop, Won’t Stop
The money continues to pour in. Global corporate investment in AI soared to nearly $68 billion in 2020, an increase of 40 percent over the year before.
9. The Startup Frenzy Is Over
The previous graph showed that private investment is still increasing year over year, but at a slower pace. This graph shows that the money is being channeled into fewer AI startups. While the pandemic may have had an impact on startup activity, this decline in the number of startups is a clear trend that began in 2018. It seems to be a signal of a maturing industry.
10. The COVID Effect
While many trends in AI were largely unaffected by the global pandemic, this chart shows that private investment in 2020 skewed toward certain sectors that have played big roles in the world's response to COVID-19. The boom in investment from pharma-related companies is the most obvious, but it also seems possible that the increased funding for edtech and gaming has something to do with the fact that students and adults alike have spent a lot of the last year in front of their computers.
11. Risks? There are Risks?
Corporations are steadily increasing their adoption of AI tools in such industries as telecom, financial services, and automotive. Yet most companies seem unaware or unconcerned about the risks accompanying this new technology. When asked in a McKinsey survey what risks they considered relevant, only cybersecurity had registered with more than half of respondents. Ethical concerns related to AI, such as privacy and fairness, are one of the hottest topics in AI research today, but apparently business hasn't yet gotten the memo.
12. Ph.D.’s Hear the Siren Call of Industry
To be fair, there are only so many academic jobs. While universities have increased the number of AI-related courses on both the undergraduate and graduate level, and the number of tenure-track faculty jobs has increased accordingly, academia still can't absorb the growing number of fresh AI Ph.D.'s released into the world each year. This chart, which only represents Ph.D. graduates in North America, shows that the large majority of those graduates are getting industry jobs.
13. Ethics Matter
Corporations may not care about AI ethics yet, but researchers increasingly do. Many groups are working on issues such as opaque decision making by AI systems (called the explainability problem), embedded bias and discrimination, and privacy intrusion. The chart above shows the rise in ethics-related papers at AI conferences, which the AI Index's Clark sees as an encouraging sign. Since so many students take part in conferences, he notes, "in a few years, there will be a load of people going into industry that have come up in this milieu."
Beyond the increase in conference papers, however, there's not much to measure. The report stresses that quantitative tests of bias in AI systems are only beginning to emerge. Creating these evaluations "feels like a new part of the AI scientific field," Clark says.
14. The Diversity Problem, Part 1
One way to work on embedded bias and discrimination in AI systems is to ensure diversity in the groups that are building them. This is hardly a radical notion. Yet in both academia and industry, the AI workforce "remains predominantly male and lacking in diversity," the report states. This graph, with data from the Computer Research Association's annual survey , shows that women make up only about 20 percent of graduates from AI-related Ph.D. programs in North America.
15. The Diversity Problem, Part 2
Data from that same survey tells a similar story about race/ethnic identity. What's to be done? Well, given that the problem seems quite apparent at the level of graduating Ph.D.s, it probably makes sense to look further up the pipeline. There are any number of excellent STEM programs that focus on girls and underrepresented minorities. AI4ALL comes to mind. Maybe sling them a few dollars, or get involved in some way?
- 12 Graphs That Explain the State of AI in 2022 ›
- 10 Graphs That Sum Up the State of AI in 2023 - IEEE Spectrum ›
Eliza Strickland is a senior editor at IEEE Spectrum , where she covers AI, biomedical engineering, and other topics. She holds a master’s degree in journalism from Columbia University.
Language is so good it needs a harder test? Put the text of the Bible into AI and let it answer questions to see if it can make sense of what is often poorly written and often seems contradictory.
Thank you, Author! For caring about the article information quality.
Build Long-Range IoT Applications Fast With Meshtastic
The forgotten history of chinese keyboards, physics nobel laureate herbert kroemer dies at 95, related stories, 15 graphs that explain the state of ai in 2024, deep learning picks apart dna data-copying puzzles, machine learning turns up covid surprise.
Main Navigation
- Contact NeurIPS
- Code of Ethics
- Code of Conduct
- Create Profile
- Journal To Conference Track
- Diversity & Inclusion
- Proceedings
- Future Meetings
- Exhibitor Information
- Privacy Policy
NeurIPS 2024, the Thirty-eighth Annual Conference on Neural Information Processing Systems, will be held at the Vancouver Convention Center
Monday Dec 9 through Sunday Dec 15. Monday is an industry expo.

Registration
Pricing » Registration 2024 Registration Cancellation Policy » . Certificate of Attendance
Our Hotel Reservation page is currently under construction and will be released shortly. NeurIPS has contracted Hotel guest rooms for the Conference at group pricing, requiring reservations only through this page. Please do not make room reservations through any other channel, as it only impedes us from putting on the best Conference for you. We thank you for your assistance in helping us protect the NeurIPS conference.
Announcements
- The call for High School Projects has been released
- The Call For Papers has been released
- See the Visa Information page for changes to the visa process for 2024.
Latest NeurIPS Blog Entries [ All Entries ]
Important dates.
If you have questions about supporting the conference, please contact us .
View NeurIPS 2024 exhibitors » Become an 2024 Exhibitor Exhibitor Info »
Organizing Committee
General chair, program chair, workshop chair, workshop chair assistant, tutorial chair, competition chair, data and benchmark chair, diversity, inclusion and accessibility chair, affinity chair, ethics review chair, communication chair, social chair, journal chair, creative ai chair, workflow manager, logistics and it, mission statement.
The Neural Information Processing Systems Foundation is a non-profit corporation whose purpose is to foster the exchange of research advances in Artificial Intelligence and Machine Learning, principally by hosting an annual interdisciplinary academic conference with the highest ethical standards for a diverse and inclusive community.
About the Conference
The conference was founded in 1987 and is now a multi-track interdisciplinary annual meeting that includes invited talks, demonstrations, symposia, and oral and poster presentations of refereed papers. Along with the conference is a professional exposition focusing on machine learning in practice, a series of tutorials, and topical workshops that provide a less formal setting for the exchange of ideas.
More about the Neural Information Processing Systems foundation »

Featured Articles
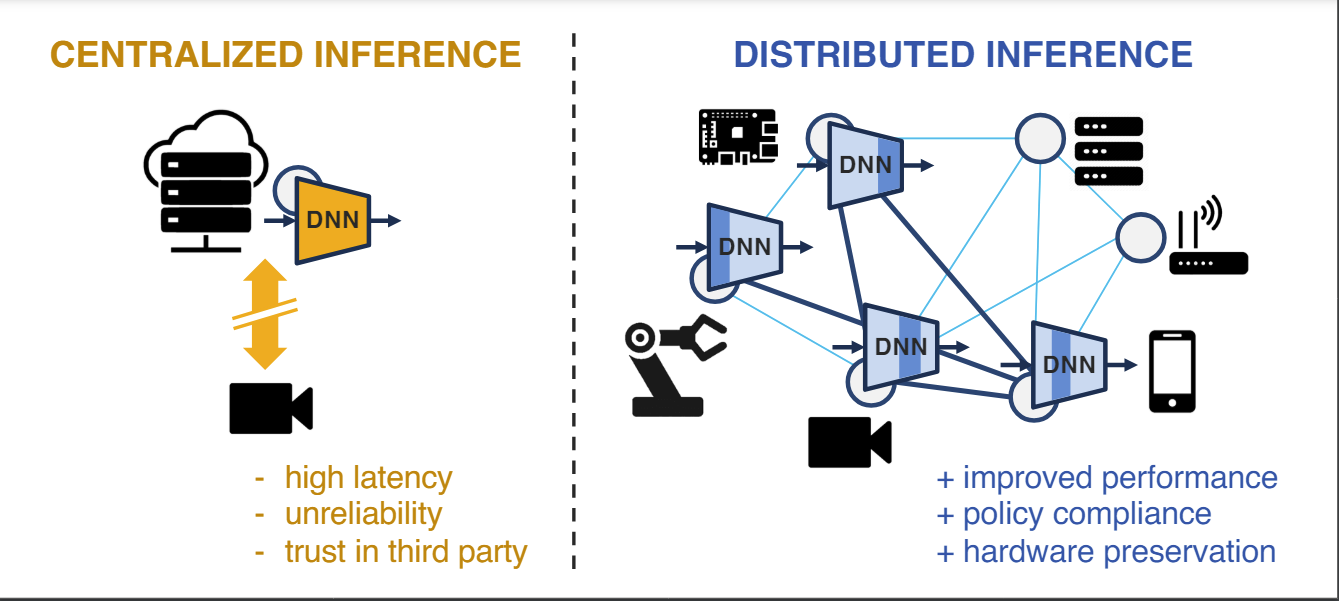
Editor's Choice
DNN Partitioning for Inference Throughput Acceleration at the Edge
Authors: Thomas Feltin, Leo Marcho, Juan-Antonio Cordero-Fuertes, Frank Brockners, Thomas H. Clausen
Published in IEEE Xplore 13 February 2023 View in IEEE Xplore
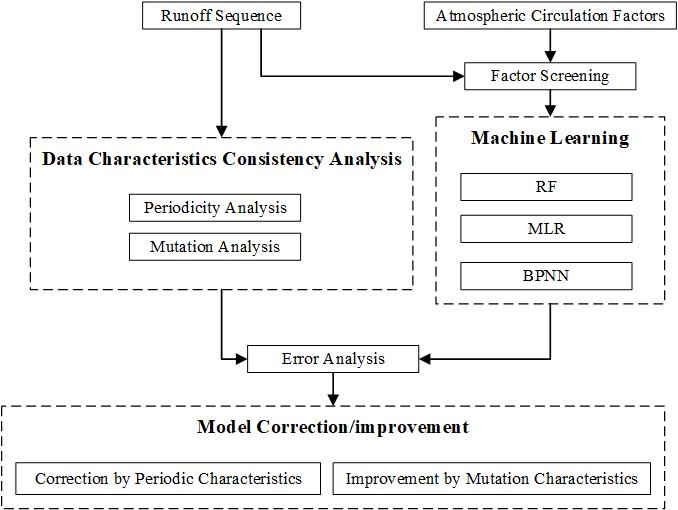
Effect of Data Characteristics Inconsistency on Medium and Long-Term Runoff Forecasting by Machine Learning
Authors: Ping Ai, Chuansheng Xiong, Ke Li, Yanhong Song, Shicheng Gong, Zhaoxin Yue
Published in IEEE Xplore 03 February 2023 View in IEEE Xplore
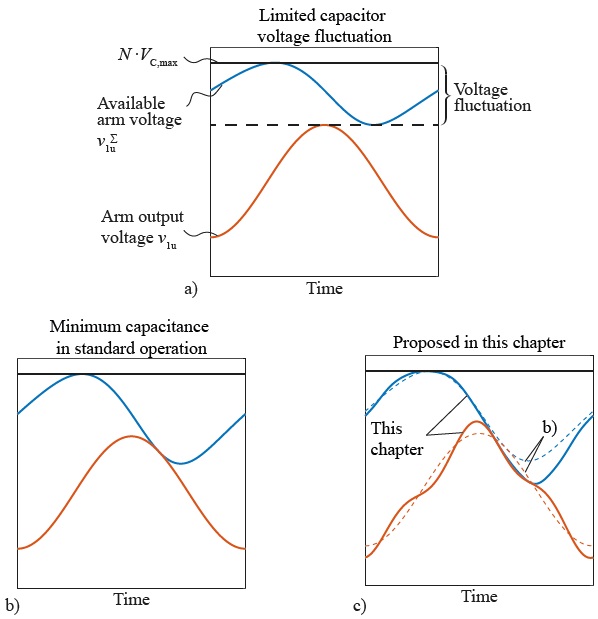
Reducing Losses and Energy Storage Requirements of Modular Multilevel Converters With Optimal Harmonic Injection
Authors: Simon Fuchs, Jurgen Biela
Published in IEEE Xplore 27 February 2023 View in IEEE Xplore
Guide for Authors
Explore the following resources that will guide you from article submission to online publication.
- Preparing Your Article
- Submission Guidelines
- Stages of Peer Review
- Post Acceptance Guide
Announcements

Enter the Best Video Award for the Opportunity to Win $500
Ieee access 10 year anniversary twitter giveaway, ieee author portal saves ieee access authors time and effort, reviewer best practices, benefits of publishing.
Learn more about the many benefits of publishing your important research in IEEE Access :
© 2024 IEEE - All rights reserved. Use of this website signifies your agreement to the IEEE TERMS AND CONDITIONS.
A not-for-profit organization, IEEE is the world’s largest technical professional organization dedicated to advancing technology for the benefit of humanity.
AWARD RULES:
NO PURCHASE NECESSARY TO ENTER OR WIN. A PURCHASE WILL NOT INCREASE YOUR CHANCES OF WINNING.
These rules apply to the “2024 IEEE Access Best Video Award Part 1″ (the “Award”).
- Sponsor: The Sponsor of the Award is The Institute of Electrical and Electronics Engineers, Incorporated (“IEEE”) on behalf of IEEE Access , 445 Hoes Lane, Piscataway, NJ 08854-4141 USA (“Sponsor”).
- Eligibility: Award is open to residents of the United States of America and other countries, where permitted by local law, who are the age of eighteen (18) and older. Employees of Sponsor, its agents, affiliates and their immediate families are not eligible to enter Award. The Award is subject to all applicable state, local, federal and national laws and regulations. Entrants may be subject to rules imposed by their institution or employer relative to their participation in Awards and should check with their institution or employer for any relevant policies. Void in locations and countries where prohibited by law.
- Agreement to Official Rules : By participating in this Award, entrants agree to abide by the terms and conditions thereof as established by Sponsor. Sponsor reserves the right to alter any of these Official Rules at any time and for any reason. All decisions made by Sponsor concerning the Award including, but not limited to the cancellation of the Award, shall be final and at its sole discretion.
- How to Enter: This Award opens on January 1, 2024 at 12:00 AM ET and all entries must be received by 11:59 PM ET on June 30, 2024 (“Promotional Period”).
Entrant must submit a video with an article submission to IEEE Access . The video submission must clearly be relevant to the submitted manuscript. Only videos that accompany an article that is accepted for publication in IEEE Access will qualify. The video may be simulations, demonstrations, or interviews with other experts, for example. Your video file should not exceed 100 MB.
Entrants can enter the Award during Promotional Period through the following method:
- The IEEE Author Portal : Entrants can upload their video entries while submitting their article through the IEEE Author Portal submission site .
- Review and Complete the Terms and Conditions: After submitting your manuscript and video through the IEEE Author Portal, entrants should then review and sign the Terms and Conditions .
Entrants who have already submitted a manuscript to IEEE Access without a video can still submit a video for inclusion in this Award so long as the video is submitted within 7 days of the article submission date. The video can be submitted via email to the article administrator. All videos must undergo peer review and be accepted along with the article submission. Videos may not be submitted after an article has already been accepted for publication.
The criteria for an article to be accepted for publication in IEEE Access are:
- The article must be original writing that enhances the existing body of knowledge in the given subject area. Original review articles and surveys are acceptable even if new data/concepts are not presented.
- Results reported must not have been submitted or published elsewhere (although expanded versions of conference publications are eligible for submission).
- Experiments, statistics, and other analyses must be performed to a high technical standard and are described in sufficient detail.
- Conclusions must be presented in an appropriate fashion and are supported by the data.
- The article must be written in standard English with correct grammar.
- Appropriate references to related prior published works must be included.
- The article must fall within the scope of IEEE Access
- Must be in compliance with the IEEE PSPB Operations Manual.
- Completion of the required IEEE intellectual property documents for publication.
- At the discretion of the IEEE Access Editor-in-Chief.
- Disqualification: The following items will disqualify a video from being considered a valid submission:
- The video is not original work.
- A video that is not accompanied with an article submission.
- The article and/or video is rejected during the peer review process.
- The article and/or video topic does not fit into the scope of IEEE Access .
- The article and/or do not follow the criteria for publication in IEEE Access .
- Videos posted in a comment on IEEE Xplore .
- Content is off-topic, offensive, obscene, indecent, abusive or threatening to others.
- Infringes the copyright, trademark or other right of any third party.
- Uploads viruses or other contaminating or destructive features.
- Is in violation of any applicable laws or regulations.
- Is not in English.
- Is not provided within the designated submission time.
- Entrant does not agree and sign the Terms and Conditions document.
Entries must be original. Entries that copy other entries, or the intellectual property of anyone other than the Entrant, may be removed by Sponsor and the Entrant may be disqualified. Sponsor reserves the right to remove any entry and disqualify any Entrant if the entry is deemed, in Sponsor’s sole discretion, to be inappropriate.
- Entrant’s Warranty and Authorization to Sponsor: By entering the Award, entrants warrant and represent that the Award Entry has been created and submitted by the Entrant. Entrant certifies that they have the ability to use any image, text, video, or other intellectual property they may upload and that Entrant has obtained all necessary permissions. IEEE shall not indemnify Entrant for any infringement, violation of publicity rights, or other civil or criminal violations. Entrant agrees to hold IEEE harmless for all actions related to the submission of an Entry. Entrants further represent and warrant, if they reside outside of the United States of America, that their participation in this Award and acceptance of a prize will not violate their local laws.
- Intellectual Property Rights: Entrant grants Sponsor an irrevocable, worldwide, royalty free license to use, reproduce, distribute, and display the Entry for any lawful purpose in all media whether now known or hereinafter created. This may include, but is not limited to, the IEEE A ccess website, the IEEE Access YouTube channel, the IEEE Access IEEE TV channel, IEEE Access social media sites (LinkedIn, Facebook, Twitter, IEEE Access Collabratec Community), and the IEEE Access Xplore page. Facebook/Twitter/Microsite usernames will not be used in any promotional and advertising materials without the Entrants’ expressed approval.
- Number of Prizes Available, Prizes, Approximate Retail Value and Odds of winning Prizes: Two (2) promotional prizes of $350 USD Amazon gift cards. One (1) grand prize of a $500 USD Amazon gift card. Prizes will be distributed to the winners after the selection of winners is announced. Odds of winning a prize depend on the number of eligible entries received during the Promotional Period. Only the corresponding author of the submitted manuscript will receive the prize.
The grand prize winner may, at Sponsor’ discretion, have his/her article and video highlighted in media such as the IEEE Access Xplore page and the IEEE Access social media sites.
The prize(s) for the Award are being sponsored by IEEE. No cash in lieu of prize or substitution of prize permitted, except that Sponsor reserves the right to substitute a prize or prize component of equal or greater value in its sole discretion for any reason at time of award. Sponsor shall not be responsible for service obligations or warranty (if any) in relation to the prize(s). Prize may not be transferred prior to award. All other expenses associated with use of the prize, including, but not limited to local, state, or federal taxes on the Prize, are the sole responsibility of the winner. Winner(s) understand that delivery of a prize may be void where prohibited by law and agrees that Sponsor shall have no obligation to substitute an alternate prize when so prohibited. Amazon is not a sponsor or affiliated with this Award.
- Selection of Winners: Promotional prize winners will be selected based on entries received during the Promotional Period. The sponsor will utilize an Editorial Panel to vote on the best video submissions. Editorial Panel members are not eligible to participate in the Award. Entries will be ranked based on three (3) criteria:
- Presentation of Technical Content
- Quality of Video
Upon selecting a winner, the Sponsor will notify the winner via email. All potential winners will be notified via their email provided to the sponsor. Potential winners will have five (5) business days to respond after receiving initial prize notification or the prize may be forfeited and awarded to an alternate winner. Potential winners may be required to sign an affidavit of eligibility, a liability release, and a publicity release. If requested, these documents must be completed, signed, and returned within ten (10) business days from the date of issuance or the prize will be forfeited and may be awarded to an alternate winner. If prize or prize notification is returned as undeliverable or in the event of noncompliance with these Official Rules, prize will be forfeited and may be awarded to an alternate winner.
- General Prize Restrictions: No prize substitutions or transfer of prize permitted, except by the Sponsor. Import/Export taxes, VAT and country taxes on prizes are the sole responsibility of winners. Acceptance of a prize constitutes permission for the Sponsor and its designees to use winner’s name and likeness for advertising, promotional and other purposes in any and all media now and hereafter known without additional compensation unless prohibited by law. Winner acknowledges that neither Sponsor, Award Entities nor their directors, employees, or agents, have made nor are in any manner responsible or liable for any warranty, representation, or guarantee, express or implied, in fact or in law, relative to any prize, including but not limited to its quality, mechanical condition or fitness for a particular purpose. Any and all warranties and/or guarantees on a prize (if any) are subject to the respective manufacturers’ terms therefor, and winners agree to look solely to such manufacturers for any such warranty and/or guarantee.
11.Release, Publicity, and Privacy : By receipt of the Prize and/or, if requested, by signing an affidavit of eligibility and liability/publicity release, the Prize Winner consents to the use of his or her name, likeness, business name and address by Sponsor for advertising and promotional purposes, including but not limited to on Sponsor’s social media pages, without any additional compensation, except where prohibited. No entries will be returned. All entries become the property of Sponsor. The Prize Winner agrees to release and hold harmless Sponsor and its officers, directors, employees, affiliated companies, agents, successors and assigns from and against any claim or cause of action arising out of participation in the Award.
Sponsor assumes no responsibility for computer system, hardware, software or program malfunctions or other errors, failures, delayed computer transactions or network connections that are human or technical in nature, or for damaged, lost, late, illegible or misdirected entries; technical, hardware, software, electronic or telephone failures of any kind; lost or unavailable network connections; fraudulent, incomplete, garbled or delayed computer transmissions whether caused by Sponsor, the users, or by any of the equipment or programming associated with or utilized in this Award; or by any technical or human error that may occur in the processing of submissions or downloading, that may limit, delay or prevent an entrant’s ability to participate in the Award.
Sponsor reserves the right, in its sole discretion, to cancel or suspend this Award and award a prize from entries received up to the time of termination or suspension should virus, bugs or other causes beyond Sponsor’s control, unauthorized human intervention, malfunction, computer problems, phone line or network hardware or software malfunction, which, in the sole opinion of Sponsor, corrupt, compromise or materially affect the administration, fairness, security or proper play of the Award or proper submission of entries. Sponsor is not liable for any loss, injury or damage caused, whether directly or indirectly, in whole or in part, from downloading data or otherwise participating in this Award.
Representations and Warranties Regarding Entries: By submitting an Entry, you represent and warrant that your Entry does not and shall not comprise, contain, or describe, as determined in Sponsor’s sole discretion: (A) false statements or any misrepresentations of your affiliation with a person or entity; (B) personally identifying information about you or any other person; (C) statements or other content that is false, deceptive, misleading, scandalous, indecent, obscene, unlawful, defamatory, libelous, fraudulent, tortious, threatening, harassing, hateful, degrading, intimidating, or racially or ethnically offensive; (D) conduct that could be considered a criminal offense, could give rise to criminal or civil liability, or could violate any law; (E) any advertising, promotion or other solicitation, or any third party brand name or trademark; or (F) any virus, worm, Trojan horse, or other harmful code or component. By submitting an Entry, you represent and warrant that you own the full rights to the Entry and have obtained any and all necessary consents, permissions, approvals and licenses to submit the Entry and comply with all of these Official Rules, and that the submitted Entry is your sole original work, has not been previously published, released or distributed, and does not infringe any third-party rights or violate any laws or regulations.
12.Disputes: EACH ENTRANT AGREES THAT: (1) ANY AND ALL DISPUTES, CLAIMS, AND CAUSES OF ACTION ARISING OUT OF OR IN CONNECTION WITH THIS AWARD, OR ANY PRIZES AWARDED, SHALL BE RESOLVED INDIVIDUALLY, WITHOUT RESORTING TO ANY FORM OF CLASS ACTION, PURSUANT TO ARBITRATION CONDUCTED UNDER THE COMMERCIAL ARBITRATION RULES OF THE AMERICAN ARBITRATION ASSOCIATION THEN IN EFFECT, (2) ANY AND ALL CLAIMS, JUDGMENTS AND AWARDS SHALL BE LIMITED TO ACTUAL OUT-OF-POCKET COSTS INCURRED, INCLUDING COSTS ASSOCIATED WITH ENTERING THIS AWARD, BUT IN NO EVENT ATTORNEYS’ FEES; AND (3) UNDER NO CIRCUMSTANCES WILL ANY ENTRANT BE PERMITTED TO OBTAIN AWARDS FOR, AND ENTRANT HEREBY WAIVES ALL RIGHTS TO CLAIM, PUNITIVE, INCIDENTAL, AND CONSEQUENTIAL DAMAGES, AND ANY OTHER DAMAGES, OTHER THAN FOR ACTUAL OUT-OF-POCKET EXPENSES, AND ANY AND ALL RIGHTS TO HAVE DAMAGES MULTIPLIED OR OTHERWISE INCREASED. ALL ISSUES AND QUESTIONS CONCERNING THE CONSTRUCTION, VALIDITY, INTERPRETATION AND ENFORCEABILITY OF THESE OFFICIAL RULES, OR THE RIGHTS AND OBLIGATIONS OF ENTRANT AND SPONSOR IN CONNECTION WITH THE AWARD, SHALL BE GOVERNED BY, AND CONSTRUED IN ACCORDANCE WITH, THE LAWS OF THE STATE OF NEW JERSEY, WITHOUT GIVING EFFECT TO ANY CHOICE OF LAW OR CONFLICT OF LAW, RULES OR PROVISIONS (WHETHER OF THE STATE OF NEW JERSEY OR ANY OTHER JURISDICTION) THAT WOULD CAUSE THE APPLICATION OF THE LAWS OF ANY JURISDICTION OTHER THAN THE STATE OF NEW JERSEY. SPONSOR IS NOT RESPONSIBLE FOR ANY TYPOGRAPHICAL OR OTHER ERROR IN THE PRINTING OF THE OFFER OR ADMINISTRATION OF THE AWARD OR IN THE ANNOUNCEMENT OF THE PRIZES.
- Limitation of Liability: The Sponsor, Award Entities and their respective parents, affiliates, divisions, licensees, subsidiaries, and advertising and promotion agencies, and each of the foregoing entities’ respective employees, officers, directors, shareholders and agents (the “Released Parties”) are not responsible for incorrect or inaccurate transfer of entry information, human error, technical malfunction, lost/delayed data transmissions, omission, interruption, deletion, defect, line failures of any telephone network, computer equipment, software or any combination thereof, inability to access web sites, damage to a user’s computer system (hardware and/or software) due to participation in this Award or any other problem or error that may occur. By entering, participants agree to release and hold harmless the Released Parties from and against any and all claims, actions and/or liability for injuries, loss or damage of any kind arising from or in connection with participation in and/or liability for injuries, loss or damage of any kind, to person or property, arising from or in connection with participation in and/or entry into this Award, participation is any Award-related activity or use of any prize won. Entry materials that have been tampered with or altered are void. If for any reason this Award is not capable of running as planned, or if this Award or any website associated therewith (or any portion thereof) becomes corrupted or does not allow the proper playing of this Award and processing of entries per these rules, or if infection by computer virus, bugs, tampering, unauthorized intervention, affect the administration, security, fairness, integrity, or proper conduct of this Award, Sponsor reserves the right, at its sole discretion, to disqualify any individual implicated in such action, and/or to cancel, terminate, modify or suspend this Award or any portion thereof, or to amend these rules without notice. In the event of a dispute as to who submitted an online entry, the entry will be deemed submitted by the authorized account holder the email address submitted at the time of entry. “Authorized Account Holder” is defined as the person assigned to an email address by an Internet access provider, online service provider or other organization responsible for assigning email addresses for the domain associated with the email address in question. Any attempt by an entrant or any other individual to deliberately damage any web site or undermine the legitimate operation of the Award is a violation of criminal and civil laws and should such an attempt be made, the Sponsor reserves the right to seek damages and other remedies from any such person to the fullest extent permitted by law. This Award is governed by the laws of the State of New Jersey and all entrants hereby submit to the exclusive jurisdiction of federal or state courts located in the State of New Jersey for the resolution of all claims and disputes. Facebook, LinkedIn, Twitter, G+, YouTube, IEEE Xplore , and IEEE TV are not sponsors nor affiliated with this Award.
- Award Results and Official Rules: To obtain the identity of the prize winner and/or a copy of these Official Rules, send a self-addressed stamped envelope to Kimberly Rybczynski, IEEE, 445 Hoes Lane, Piscataway, NJ 08854-4141 USA.

COMMENTS
Cloud computing has become a widely exploited research area in academia and industry. Cloud computing benefits both cloud services providers (CSPs) and consumers. The security challenges associated with cloud computing have been widely studied in the literature. This systematic literature review (SLR) is aimed to review the existing research studies on cloud computing security, threats, and ...
Date Added to IEEE Xplore: 30 July 2021 ISBN Information: Electronic ISBN: 978-1-7281-9061-7 ... Papers. 1439. Full. Text Views. Alerts. Alerts. Manage Content Alerts . Add to Citation Alerts ... Hence BMS form a important part of any electric vehicle and so, more and more research are still being conducted in the field to develop more ...
The paper first explains what cyber space and cyber security is. Then the costs and impact of cyber security are discussed. ... Date of Conference: 18-20 November 2021 Date Added to IEEE Xplore: 11 January 2022 ISBN Information: Electronic ISBN: 978-1-6654-1758-7 Print on Demand(PoD) ISBN: 978-1-6654-1759-4 INSPEC Accession Number: ...
Computational Media Intelligence: Human-Centered Machine Analysis of Media. By K. Somandepalli, T. Guha, V. R. Martinez, N. Kumar, H. Adam, and S. Narayanan. The topic treated in this article is the application of deep learning algorithms, combined with audio-visual signal processing, to analyze entertainment media such as film/TV.
6G Wireless Systems: Vision, Requirements, Challenges, Insights, and Opportunities. By H. Tataria, M. Shafi, A. F. Molisch, M. Dohler, H. Sjöland, and F. Tufvesson. This article aims to provide a holistic top-down view of sixth-generation wireless system design and proposes fundamental changes that are required in the core networks of the future.
IEEE and its members inspire a global community to innovate for a better tomorrow through highly cited publications, conferences, technology standards, and professional and educational activities. IEEE is the trusted "voice" for engineering, computing, and technology information around the globe.
This survey paper emphasizes and contributes to the various aspects of IoT with current popular applications and the recent research trends in this technology. ... Date of Conference: 07-09 October 2021 Date Added to IEEE Xplore: 18 November 2021 ISBN Information: Electronic ISBN: 978-1-6654-2554-4 Print on Demand(PoD) ISBN: 978-1 -6654-2555 ...
List of Accepted Papers in IEEE INFOCOM 2021 Main Conference. 6GAN: IPv6 Multi-Pattern Target Generation via Generative Adversarial Nets with Reinforcement Learning. Tianyu Cui (Institute of Information Engineering, University of Chinese Academy of Sciences, China); Gaopeng Gou (Institute of Information EngineeringChinese Academy of Sciences ...
The IEEE Member Digital Library, brought to you via the IEEE Xplore digital library, gives you instant access to all IEEE journal articles, magazines, and conference papers—the most essential information in technology today. With two great options designed to meet the needs—and budget—of every IEEE member, simply choose the subscription that's right for you:
Papers. More detail about papers and their associated presentations will be released with the virtual website. What follows is a list of papers groups by session. Tuesday, October 2610:00-11:30AM CDT (UTC-5)Best PapersSession Chair: Bongshin Lee, Silvia Miksch, Anders Ynnerman. Simultaneous Matrix Orderings for Graph Collections Authors: Nathan ...
This paper reviewed the sign language research in the vision-based hand gesture recognition system from 2014 to 2020. Its objective is to identify the progress and what needs more attention. We have extracted a total of 98 articles from well-known online databases using selected keywords. The review shows that the vision-based hand gesture recognition research is an active field of research ...
IEEE provides guidelines for formatting your paper. These guidelines must be followed when you're submitting a manuscript for publication in an IEEE journal. Some of the key guidelines are: Formatting the text as two columns, in Times New Roman, 10 pt. Including a byline, an abstract, and a set of keywords at the start of the research paper.
Thesis Essays: Ieee research paper sample FREE Formatting! Ieee research paper sample. These are the basis of the stages of the. Discussion of those results, hence. Ideas change. Brain-Inspired Golden Chip Free Hardware Tro Detection 3 [ IEEE TIFS 2021] Accepted Paper : Brain-Inspired Golden Chip Free has been accepted for publication in IEEE ...
IEEE VR 2021 seeks original, high-quality papers in all areas related to virtual reality (VR), including augmented reality (AR), mixed reality (MR), and 3D user interfaces (3DUIs). ... Each research paper should provide a validated contribution covering one or more of the following categories: methodological, technology, applications, and ...
IEEE Access was included in the 2022 Journal Citation Report (JCR) and received: . an impact factor of 3.9 *Impact factor = citations in 2022 to articles published in 2020 and 2021/articles published in 2020 and 2021; an Eigenfactor of 0.32872 *Measured by counting the total number of citations a journal receives over a five-year period; an article influence score of 0.685 *This is a journal ...
June 2021. Electric Vehicles. Electric Vehicles. Abstract - This paper gives a mini overview of the recent research and works in the sector of electric vehicles. The paper describes the main part of electric vehicles and their work. The major components are battery, motor, charger, steering, and braking. The paper finally shows basic concepts ...
AI research is booming: More than 120,000 peer-reviewed AI papers were published in 2019. The report also notes that between 2000 and 2019, AI papers went from being 0.8 percent of all peer ...
2021 2020 2019 2018 ... (Microsoft Research) Amir Globerson (Tel Aviv University, Google) ... and oral and poster presentations of refereed papers. Along with the conference is a professional exposition focusing on machine learning in practice, a series of tutorials, and topical workshops that provide a less formal setting for the exchange of ...
AWARD RULES: NO PURCHASE NECESSARY TO ENTER OR WIN. A PURCHASE WILL NOT INCREASE YOUR CHANCES OF WINNING. These rules apply to the "2024 IEEE Access Best Video Award Part 1″ (the "Award").. Sponsor: The Sponsor of the Award is The Institute of Electrical and Electronics Engineers, Incorporated ("IEEE") on behalf of IEEE Access, 445 Hoes Lane, Piscataway, NJ 08854-4141 USA ...