Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Review Article
- Open access
- Published: 12 February 2024

Education reform and change driven by digital technology: a bibliometric study from a global perspective
- Chengliang Wang 1 ,
- Xiaojiao Chen 1 ,
- Teng Yu ORCID: orcid.org/0000-0001-5198-7261 2 , 3 ,
- Yidan Liu 1 , 4 &
- Yuhui Jing 1
Humanities and Social Sciences Communications volume 11 , Article number: 256 ( 2024 ) Cite this article
5690 Accesses
1 Citations
1 Altmetric
Metrics details
- Development studies
- Science, technology and society
Amidst the global digital transformation of educational institutions, digital technology has emerged as a significant area of interest among scholars. Such technologies have played an instrumental role in enhancing learner performance and improving the effectiveness of teaching and learning. These digital technologies also ensure the sustainability and stability of education during the epidemic. Despite this, a dearth of systematic reviews exists regarding the current state of digital technology application in education. To address this gap, this study utilized the Web of Science Core Collection as a data source (specifically selecting the high-quality SSCI and SCIE) and implemented a topic search by setting keywords, yielding 1849 initial publications. Furthermore, following the PRISMA guidelines, we refined the selection to 588 high-quality articles. Using software tools such as CiteSpace, VOSviewer, and Charticulator, we reviewed these 588 publications to identify core authors (such as Selwyn, Henderson, Edwards), highly productive countries/regions (England, Australia, USA), key institutions (Monash University, Australian Catholic University), and crucial journals in the field ( Education and Information Technologies , Computers & Education , British Journal of Educational Technology ). Evolutionary analysis reveals four developmental periods in the research field of digital technology education application: the embryonic period, the preliminary development period, the key exploration, and the acceleration period of change. The study highlights the dual influence of technological factors and historical context on the research topic. Technology is a key factor in enabling education to transform and upgrade, and the context of the times is an important driving force in promoting the adoption of new technologies in the education system and the transformation and upgrading of education. Additionally, the study identifies three frontier hotspots in the field: physical education, digital transformation, and professional development under the promotion of digital technology. This study presents a clear framework for digital technology application in education, which can serve as a valuable reference for researchers and educational practitioners concerned with digital technology education application in theory and practice.
Similar content being viewed by others
A bibliometric analysis of knowledge mapping in Chinese education digitalization research from 2012 to 2022
Digital transformation and digital literacy in the context of complexity within higher education institutions: a systematic literature review

Education big data and learning analytics: a bibliometric analysis
Introduction.
Digital technology has become an essential component of modern education, facilitating the extension of temporal and spatial boundaries and enriching the pedagogical contexts (Selwyn and Facer, 2014 ). The advent of mobile communication technology has enabled learning through social media platforms (Szeto et al. 2015 ; Pires et al. 2022 ), while the advancement of augmented reality technology has disrupted traditional conceptions of learning environments and spaces (Perez-Sanagustin et al., 2014 ; Kyza and Georgiou, 2018 ). A wide range of digital technologies has enabled learning to become a norm in various settings, including the workplace (Sjöberg and Holmgren, 2021 ), home (Nazare et al. 2022 ), and online communities (Tang and Lam, 2014 ). Education is no longer limited to fixed locations and schedules, but has permeated all aspects of life, allowing learning to continue at any time and any place (Camilleri and Camilleri, 2016 ; Selwyn and Facer, 2014 ).
The advent of digital technology has led to the creation of several informal learning environments (Greenhow and Lewin, 2015 ) that exhibit divergent form, function, features, and patterns in comparison to conventional learning environments (Nygren et al. 2019 ). Consequently, the associated teaching and learning processes, as well as the strategies for the creation, dissemination, and acquisition of learning resources, have undergone a complete overhaul. The ensuing transformations have posed a myriad of novel issues, such as the optimal structuring of teaching methods by instructors and the adoption of appropriate learning strategies by students in the new digital technology environment. Consequently, an examination of the principles that underpin effective teaching and learning in this environment is a topic of significant interest to numerous scholars engaged in digital technology education research.
Over the course of the last two decades, digital technology has made significant strides in the field of education, notably in extending education time and space and creating novel educational contexts with sustainability. Despite research attempts to consolidate the application of digital technology in education, previous studies have only focused on specific aspects of digital technology, such as Pinto and Leite’s ( 2020 ) investigation into digital technology in higher education and Mustapha et al.’s ( 2021 ) examination of the role and value of digital technology in education during the pandemic. While these studies have provided valuable insights into the practical applications of digital technology in particular educational domains, they have not comprehensively explored the macro-mechanisms and internal logic of digital technology implementation in education. Additionally, these studies were conducted over a relatively brief period, making it challenging to gain a comprehensive understanding of the macro-dynamics and evolutionary process of digital technology in education. Some studies have provided an overview of digital education from an educational perspective but lack a precise understanding of technological advancement and change (Yang et al. 2022 ). Therefore, this study seeks to employ a systematic scientific approach to collate relevant research from 2000 to 2022, comprehend the internal logic and development trends of digital technology in education, and grasp the outstanding contribution of digital technology in promoting the sustainability of education in time and space. In summary, this study aims to address the following questions:
RQ1: Since the turn of the century, what is the productivity distribution of the field of digital technology education application research in terms of authorship, country/region, institutional and journal level?
RQ2: What is the development trend of research on the application of digital technology in education in the past two decades?
RQ3: What are the current frontiers of research on the application of digital technology in education?
Literature review
Although the term “digital technology” has become ubiquitous, a unified definition has yet to be agreed upon by scholars. Because the meaning of the word digital technology is closely related to the specific context. Within the educational research domain, Selwyn’s ( 2016 ) definition is widely favored by scholars (Pinto and Leite, 2020 ). Selwyn ( 2016 ) provides a comprehensive view of various concrete digital technologies and their applications in education through ten specific cases, such as immediate feedback in classes, orchestrating teaching, and community learning. Through these specific application scenarios, Selwyn ( 2016 ) argues that digital technology encompasses technologies associated with digital devices, including but not limited to tablets, smartphones, computers, and social media platforms (such as Facebook and YouTube). Furthermore, Further, the behavior of accessing the internet at any location through portable devices can be taken as an extension of the behavior of applying digital technology.
The evolving nature of digital technology has significant implications in the field of education. In the 1890s, the focus of digital technology in education was on comprehending the nuances of digital space, digital culture, and educational methodologies, with its connotations aligned more towards the idea of e-learning. The advent and subsequent widespread usage of mobile devices since the dawn of the new millennium have been instrumental in the rapid expansion of the concept of digital technology. Notably, mobile learning devices such as smartphones and tablets, along with social media platforms, have become integral components of digital technology (Conole and Alevizou, 2010 ; Batista et al. 2016 ). In recent times, the burgeoning application of AI technology in the education sector has played a vital role in enriching the digital technology lexicon (Banerjee et al. 2021 ). ChatGPT, for instance, is identified as a novel educational technology that has immense potential to revolutionize future education (Rospigliosi, 2023 ; Arif, Munaf and Ul-Haque, 2023 ).
Pinto and Leite ( 2020 ) conducted a comprehensive macroscopic survey of the use of digital technologies in the education sector and identified three distinct categories, namely technologies for assessment and feedback, mobile technologies, and Information Communication Technologies (ICT). This classification criterion is both macroscopic and highly condensed. In light of the established concept definitions of digital technology in the educational research literature, this study has adopted the characterizations of digital technology proposed by Selwyn ( 2016 ) and Pinto and Leite ( 2020 ) as crucial criteria for analysis and research inclusion. Specifically, this criterion encompasses several distinct types of digital technologies, including Information and Communication Technologies (ICT), Mobile tools, eXtended Reality (XR) Technologies, Assessment and Feedback systems, Learning Management Systems (LMS), Publish and Share tools, Collaborative systems, Social media, Interpersonal Communication tools, and Content Aggregation tools.
Methodology and materials
Research method: bibliometric.
The research on econometric properties has been present in various aspects of human production and life, yet systematic scientific theoretical guidance has been lacking, resulting in disorganization. In 1969, British scholar Pritchard ( 1969 ) proposed “bibliometrics,” which subsequently emerged as an independent discipline in scientific quantification research. Initially, Pritchard defined bibliometrics as “the application of mathematical and statistical methods to books and other media of communication,” however, the definition was not entirely rigorous. To remedy this, Hawkins ( 2001 ) expanded Pritchard’s definition to “the quantitative analysis of the bibliographic features of a body of literature.” De Bellis further clarified the objectives of bibliometrics, stating that it aims to analyze and identify patterns in literature, such as the most productive authors, institutions, countries, and journals in scientific disciplines, trends in literary production over time, and collaboration networks (De Bellis, 2009 ). According to Garfield ( 2006 ), bibliometric research enables the examination of the history and structure of a field, the flow of information within the field, the impact of journals, and the citation status of publications over a longer time scale. All of these definitions illustrate the unique role of bibliometrics as a research method for evaluating specific research fields.
This study uses CiteSpace, VOSviewer, and Charticulator to analyze data and create visualizations. Each of these three tools has its own strengths and can complement each other. CiteSpace and VOSviewer use set theory and probability theory to provide various visualization views in fields such as keywords, co-occurrence, and co-authors. They are easy to use and produce visually appealing graphics (Chen, 2006 ; van Eck and Waltman, 2009 ) and are currently the two most widely used bibliometric tools in the field of visualization (Pan et al. 2018 ). In this study, VOSviewer provided the data necessary for the Performance Analysis; Charticulator was then used to redraw using the tabular data exported from VOSviewer (for creating the chord diagram of country collaboration); this was to complement the mapping process, while CiteSpace was primarily utilized to generate keyword maps and conduct burst word analysis.
Data retrieval
This study selected documents from the Science Citation Index Expanded (SCIE) and Social Science Citation Index (SSCI) in the Web of Science Core Collection as the data source, for the following reasons:
(1) The Web of Science Core Collection, as a high-quality digital literature resource database, has been widely accepted by many researchers and is currently considered the most suitable database for bibliometric analysis (Jing et al. 2023a ). Compared to other databases, Web of Science provides more comprehensive data information (Chen et al. 2022a ), and also provides data formats suitable for analysis using VOSviewer and CiteSpace (Gaviria-Marin et al. 2019 ).
(2) The application of digital technology in the field of education is an interdisciplinary research topic, involving technical knowledge literature belonging to the natural sciences and education-related literature belonging to the social sciences. Therefore, it is necessary to select Science Citation Index Expanded (SCIE) and Social Science Citation Index (SSCI) as the sources of research data, ensuring the comprehensiveness of data while ensuring the reliability and persuasiveness of bibliometric research (Hwang and Tsai, 2011 ; Wang et al. 2022 ).
After establishing the source of research data, it is necessary to determine a retrieval strategy (Jing et al. 2023b ). The choice of a retrieval strategy should consider a balance between the breadth and precision of the search formula. That is to say, it should encompass all the literature pertaining to the research topic while excluding irrelevant documents as much as possible. In light of this, this study has set a retrieval strategy informed by multiple related papers (Mustapha et al. 2021 ; Luo et al. 2021 ). The research by Mustapha et al. ( 2021 ) guided us in selecting keywords (“digital” AND “technolog*”) to target digital technology, while Luo et al. ( 2021 ) informed the selection of terms (such as “instruct*,” “teach*,” and “education”) to establish links with the field of education. Then, based on the current application of digital technology in the educational domain and the scope of selection criteria, we constructed the final retrieval strategy. Following the general patterns of past research (Jing et al. 2023a , 2023b ), we conducted a specific screening using the topic search (Topics, TS) function in Web of Science. For the specific criteria used in the screening for this study, please refer to Table 1 .
Literature screening
Literature acquired through keyword searches may contain ostensibly related yet actually unrelated works. Therefore, to ensure the close relevance of literature included in the analysis to the research topic, it is often necessary to perform a manual screening process to identify the final literature to be analyzed, subsequent to completing the initial literature search.
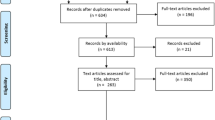
The manual screening process consists of two steps. Initially, irrelevant literature is weeded out based on the title and abstract, with two members of the research team involved in this phase. This stage lasted about one week, resulting in 1106 articles being retained. Subsequently, a comprehensive review of the full text is conducted to accurately identify the literature required for the study. To carry out the second phase of manual screening effectively and scientifically, and to minimize the potential for researcher bias, the research team established the inclusion criteria presented in Table 2 . Three members were engaged in this phase, which took approximately 2 weeks, culminating in the retention of 588 articles after meticulous screening. The entire screening process is depicted in Fig. 1 , adhering to the PRISMA guidelines (Page et al. 2021 ).
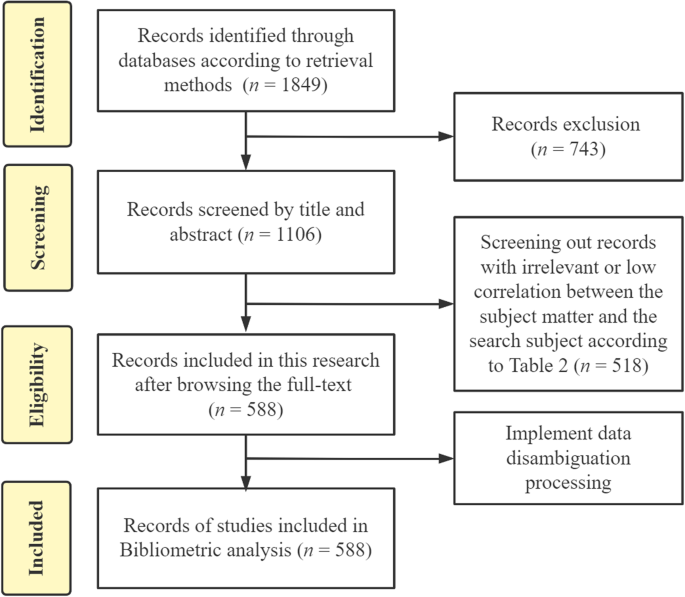
The process of obtaining and filtering the necessary literature data for research.
Data standardization
Nguyen and Hallinger ( 2020 ) pointed out that raw data extracted from scientific databases often contains multiple expressions of the same term, and not addressing these synonymous expressions could affect research results in bibliometric analysis. For instance, in the original data, the author list may include “Tsai, C. C.” and “Tsai, C.-C.”, while the keyword list may include “professional-development” and “professional development,” which often require merging. Therefore, before analyzing the selected literature, a data disambiguation process is necessary to standardize the data (Strotmann and Zhao, 2012 ; Van Eck and Waltman, 2019 ). This study adopted the data standardization process proposed by Taskin and Al ( 2019 ), mainly including the following standardization operations:
Firstly, the author and source fields in the data are corrected and standardized to differentiate authors with similar names.
Secondly, the study checks whether the journals to which the literature belongs have been renamed in the past over 20 years, so as to avoid the influence of periodical name change on the analysis results.
Finally, the keyword field is standardized by unifying parts of speech and singular/plural forms of keywords, which can help eliminate redundant entries in the knowledge graph.
Performance analysis (RQ1)
This section offers a thorough and detailed analysis of the state of research in the field of digital technology education. By utilizing descriptive statistics and visual maps, it provides a comprehensive overview of the development trends, authors, countries, institutions, and journal distribution within the field. The insights presented in this section are of great significance in advancing our understanding of the current state of research in this field and identifying areas for further investigation. The use of visual aids to display inter-country cooperation and the evolution of the field adds to the clarity and coherence of the analysis.
Time trend of the publications
To understand a research field, it is first necessary to understand the most basic quantitative information, among which the change in the number of publications per year best reflects the development trend of a research field. Figure 2 shows the distribution of publication dates.
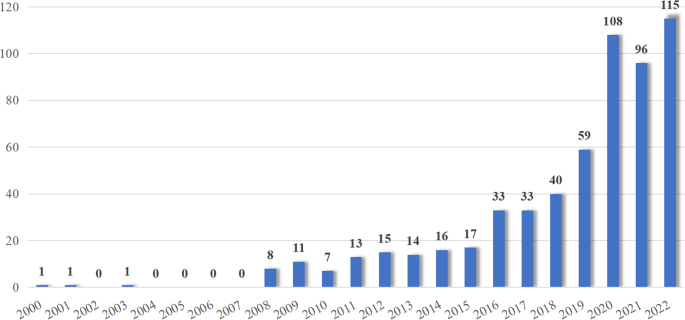
Time trend of the publications on application of digital technology in education.
From the Fig. 2 , it can be seen that the development of this field over the past over 20 years can be roughly divided into three stages. The first stage was from 2000 to 2007, during which the number of publications was relatively low. Due to various factors such as technological maturity, the academic community did not pay widespread attention to the role of digital technology in expanding the scope of teaching and learning. The second stage was from 2008 to 2019, during which the overall number of publications showed an upward trend, and the development of the field entered an accelerated period, attracting more and more scholars’ attention. The third stage was from 2020 to 2022, during which the number of publications stabilized at around 100. During this period, the impact of the pandemic led to a large number of scholars focusing on the role of digital technology in education during the pandemic, and research on the application of digital technology in education became a core topic in social science research.
Analysis of authors
An analysis of the author’s publication volume provides information about the representative scholars and core research strengths of a research area. Table 3 presents information on the core authors in adaptive learning research, including name, publication number, and average number of citations per article (based on the analysis and statistics from VOSviewer).
Variations in research foci among scholars abound. Within the field of digital technology education application research over the past two decades, Neil Selwyn stands as the most productive author, having published 15 papers garnering a total of 1027 citations, resulting in an average of 68.47 citations per paper. As a Professor at the Faculty of Education at Monash University, Selwyn concentrates on exploring the application of digital technology in higher education contexts (Selwyn et al. 2021 ), as well as related products in higher education such as Coursera, edX, and Udacity MOOC platforms (Bulfin et al. 2014 ). Selwyn’s contributions to the educational sociology perspective include extensive research on the impact of digital technology on education, highlighting the spatiotemporal extension of educational processes and practices through technological means as the greatest value of educational technology (Selwyn, 2012 ; Selwyn and Facer, 2014 ). In addition, he provides a blueprint for the development of future schools in 2030 based on the present impact of digital technology on education (Selwyn et al. 2019 ). The second most productive author in this field, Henderson, also offers significant contributions to the understanding of the important value of digital technology in education, specifically in the higher education setting, with a focus on the impact of the pandemic (Henderson et al. 2015 ; Cohen et al. 2022 ). In contrast, Edwards’ research interests focus on early childhood education, particularly the application of digital technology in this context (Edwards, 2013 ; Bird and Edwards, 2015 ). Additionally, on the technical level, Edwards also mainly prefers digital game technology, because it is a digital technology that children are relatively easy to accept (Edwards, 2015 ).
Analysis of countries/regions and organization
The present study aimed to ascertain the leading countries in digital technology education application research by analyzing 75 countries related to 558 works of literature. Table 4 depicts the top ten countries that have contributed significantly to this field in terms of publication count (based on the analysis and statistics from VOSviewer). Our analysis of Table 4 data shows that England emerged as the most influential country/region, with 92 published papers and 2401 citations. Australia and the United States secured the second and third ranks, respectively, with 90 papers (2187 citations) and 70 papers (1331 citations) published. Geographically, most of the countries featured in the top ten publication volumes are situated in Australia, North America, and Europe, with China being the only exception. Notably, all these countries, except China, belong to the group of developed nations, suggesting that economic strength is a prerequisite for fostering research in the digital technology education application field.
This study presents a visual representation of the publication output and cooperation relationships among different countries in the field of digital technology education application research. Specifically, a chord diagram is employed to display the top 30 countries in terms of publication output, as depicted in Fig. 3 . The chord diagram is composed of nodes and chords, where the nodes are positioned as scattered points along the circumference, and the length of each node corresponds to the publication output, with longer lengths indicating higher publication output. The chords, on the other hand, represent the cooperation relationships between any two countries, and are weighted based on the degree of closeness of the cooperation, with wider chords indicating closer cooperation. Through the analysis of the cooperation relationships, the findings suggest that the main publishing countries in this field are engaged in cooperative relationships with each other, indicating a relatively high level of international academic exchange and research internationalization.
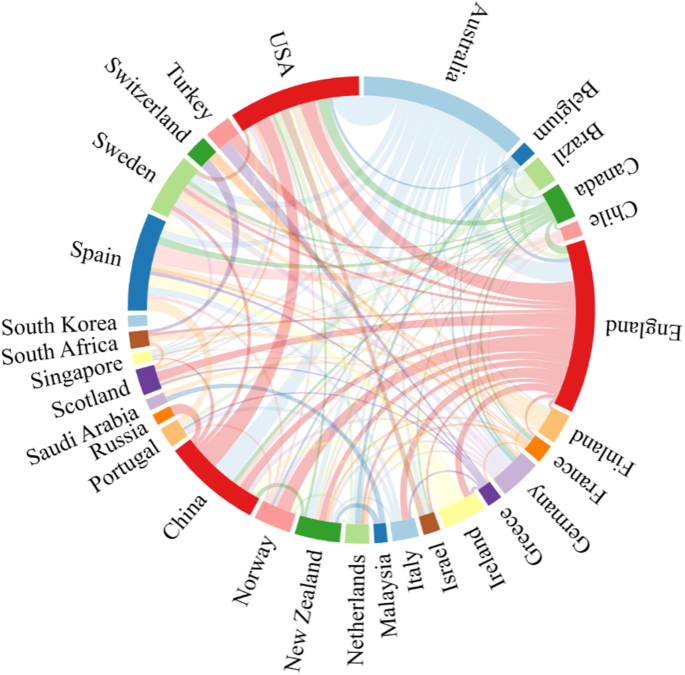
In the diagram, nodes are scattered along the circumference of a circle, with the length of each node representing the volume of publications. The weighted arcs connecting any two points on the circle are known as chords, representing the collaborative relationship between the two, with the width of the arc indicating the closeness of the collaboration.
Further analyzing Fig. 3 , we can extract more valuable information, enabling a deeper understanding of the connections between countries in the research field of digital technology in educational applications. It is evident that certain countries, such as the United States, China, and England, display thicker connections, indicating robust collaborative relationships in terms of productivity. These thicker lines signify substantial mutual contributions and shared objectives in certain sectors or fields, highlighting the interconnectedness and global integration in these areas. By delving deeper, we can also explore potential future collaboration opportunities through the chord diagram, identifying possible partners to propel research and development in this field. In essence, the chord diagram successfully encapsulates and conveys the multi-dimensionality of global productivity and cooperation, allowing for a comprehensive understanding of the intricate inter-country relationships and networks in a global context, providing valuable guidance and insights for future research and collaborations.
An in-depth examination of the publishing institutions is provided in Table 5 , showcasing the foremost 10 institutions ranked by their publication volume. Notably, Monash University and Australian Catholic University, situated in Australia, have recorded the most prolific publications within the digital technology education application realm, with 22 and 10 publications respectively. Moreover, the University of Oslo from Norway is featured among the top 10 publishing institutions, with an impressive average citation count of 64 per publication. It is worth highlighting that six institutions based in the United Kingdom were also ranked within the top 10 publishing institutions, signifying their leading position in this area of research.
Analysis of journals
Journals are the main carriers for publishing high-quality papers. Some scholars point out that the two key factors to measure the influence of journals in the specified field are the number of articles published and the number of citations. The more papers published in a magazine and the more citations, the greater its influence (Dzikowski, 2018 ). Therefore, this study utilized VOSviewer to statistically analyze the top 10 journals with the most publications in the field of digital technology in education and calculated the average citations per article (see Table 6 ).
Based on Table 6 , it is apparent that the highest number of articles in the domain of digital technology in education research were published in Education and Information Technologies (47 articles), Computers & Education (34 articles), and British Journal of Educational Technology (32 articles), indicating a higher article output compared to other journals. This underscores the fact that these three journals concentrate more on the application of digital technology in education. Furthermore, several other journals, such as Technology Pedagogy and Education and Sustainability, have published more than 15 articles in this domain. Sustainability represents the open access movement, which has notably facilitated research progress in this field, indicating that the development of open access journals in recent years has had a significant impact. Although there is still considerable disagreement among scholars on the optimal approach to achieve open access, the notion that research outcomes should be accessible to all is widely recognized (Huang et al. 2020 ). On further analysis of the research fields to which these journals belong, except for Sustainability, it is evident that they all pertain to educational technology, thus providing a qualitative definition of the research area of digital technology education from the perspective of journals.
Temporal keyword analysis: thematic evolution (RQ2)
The evolution of research themes is a dynamic process, and previous studies have attempted to present the developmental trajectory of fields by drawing keyword networks in phases (Kumar et al. 2021 ; Chen et al. 2022b ). To understand the shifts in research topics across different periods, this study follows past research and, based on the significant changes in the research field and corresponding technological advancements during the outlined periods, divides the timeline into four stages (the first stage from January 2000 to December 2005, the second stage from January 2006 to December 2011, the third stage from January 2012 to December 2017; and the fourth stage from January 2018 to December 2022). The division into these four stages was determined through a combination of bibliometric analysis and literature review, which presented a clear trajectory of the field’s development. The research analyzes the keyword networks for each time period (as there are only three articles in the first stage, it was not possible to generate an appropriate keyword co-occurrence map, hence only the keyword co-occurrence maps from the second to the fourth stages are provided), to understand the evolutionary track of the digital technology education application research field over time.
2000.1–2005.12: germination period
From January 2000 to December 2005, digital technology education application research was in its infancy. Only three studies focused on digital technology, all of which were related to computers. Due to the popularity of computers, the home became a new learning environment, highlighting the important role of digital technology in expanding the scope of learning spaces (Sutherland et al. 2000 ). In specific disciplines and contexts, digital technology was first favored in medical clinical practice, becoming an important tool for supporting the learning of clinical knowledge and practice (Tegtmeyer et al. 2001 ; Durfee et al. 2003 ).
2006.1–2011.12: initial development period
Between January 2006 and December 2011, it was the initial development period of digital technology education research. Significant growth was observed in research related to digital technology, and discussions and theoretical analyses about “digital natives” emerged. During this phase, scholars focused on the debate about “how to use digital technology reasonably” and “whether current educational models and school curriculum design need to be adjusted on a large scale” (Bennett and Maton, 2010 ; Selwyn, 2009 ; Margaryan et al. 2011 ). These theoretical and speculative arguments provided a unique perspective on the impact of cognitive digital technology on education and teaching. As can be seen from the vocabulary such as “rethinking”, “disruptive pedagogy”, and “attitude” in Fig. 4 , many scholars joined the calm reflection and analysis under the trend of digital technology (Laurillard, 2008 ; Vratulis et al. 2011 ). During this phase, technology was still undergoing dramatic changes. The development of mobile technology had already caught the attention of many scholars (Wong et al. 2011 ), but digital technology represented by computers was still very active (Selwyn et al. 2011 ). The change in technological form would inevitably lead to educational transformation. Collins and Halverson ( 2010 ) summarized the prospects and challenges of using digital technology for learning and educational practices, believing that digital technology would bring a disruptive revolution to the education field and bring about a new educational system. In addition, the term “teacher education” in Fig. 4 reflects the impact of digital technology development on teachers. The rapid development of technology has widened the generation gap between teachers and students. To ensure smooth communication between teachers and students, teachers must keep up with the trend of technological development and establish a lifelong learning concept (Donnison, 2009 ).
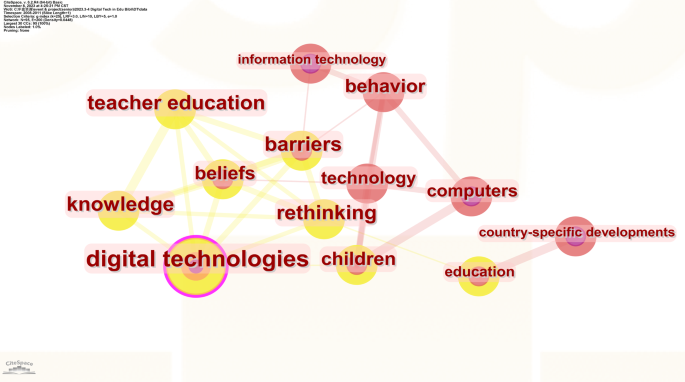
In the diagram, each node represents a keyword, with the size of the node indicating the frequency of occurrence of the keyword. The connections represent the co-occurrence relationships between keywords, with a higher frequency of co-occurrence resulting in tighter connections.
2012.1–2017.12: critical exploration period
During the period spanning January 2012 to December 2017, the application of digital technology in education research underwent a significant exploration phase. As can be seen from Fig. 5 , different from the previous stage, the specific elements of specific digital technology have started to increase significantly, including the enrichment of technological contexts, the greater variety of research methods, and the diversification of learning modes. Moreover, the temporal and spatial dimensions of the learning environment were further de-emphasized, as noted in previous literature (Za et al. 2014 ). Given the rapidly accelerating pace of technological development, the education system in the digital era is in urgent need of collaborative evolution and reconstruction, as argued by Davis, Eickelmann, and Zaka ( 2013 ).

In the domain of digital technology, social media has garnered substantial scholarly attention as a promising avenue for learning, as noted by Pasquini and Evangelopoulos ( 2016 ). The implementation of social media in education presents several benefits, including the liberation of education from the restrictions of physical distance and time, as well as the erasure of conventional educational boundaries. The user-generated content (UGC) model in social media has emerged as a crucial source for knowledge creation and distribution, with the widespread adoption of mobile devices. Moreover, social networks have become an integral component of ubiquitous learning environments (Hwang et al. 2013 ). The utilization of social media allows individuals to function as both knowledge producers and recipients, which leads to a blurring of the conventional roles of learners and teachers. On mobile platforms, the roles of learners and teachers are not fixed, but instead interchangeable.
In terms of research methodology, the prevalence of empirical studies with survey designs in the field of educational technology during this period is evident from the vocabulary used, such as “achievement,” “acceptance,” “attitude,” and “ict.” in Fig. 5 . These studies aim to understand learners’ willingness to adopt and attitudes towards new technologies, and some seek to investigate the impact of digital technologies on learning outcomes through quasi-experimental designs (Domínguez et al. 2013 ). Among these empirical studies, mobile learning emerged as a hot topic, and this is not surprising. First, the advantages of mobile learning environments over traditional ones have been empirically demonstrated (Hwang et al. 2013 ). Second, learners born around the turn of the century have been heavily influenced by digital technologies and have developed their own learning styles that are more open to mobile devices as a means of learning. Consequently, analyzing mobile learning as a relatively novel mode of learning has become an important issue for scholars in the field of educational technology.
The intervention of technology has led to the emergence of several novel learning modes, with the blended learning model being the most representative one in the current phase. Blended learning, a novel concept introduced in the information age, emphasizes the integration of the benefits of traditional learning methods and online learning. This learning mode not only highlights the prominent role of teachers in guiding, inspiring, and monitoring the learning process but also underlines the importance of learners’ initiative, enthusiasm, and creativity in the learning process. Despite being an early conceptualization, blended learning’s meaning has been expanded by the widespread use of mobile technology and social media in education. The implementation of new technologies, particularly mobile devices, has resulted in the transformation of curriculum design and increased flexibility and autonomy in students’ learning processes (Trujillo Maza et al. 2016 ), rekindling scholarly attention to this learning mode. However, some scholars have raised concerns about the potential drawbacks of the blended learning model, such as its significant impact on the traditional teaching system, the lack of systematic coping strategies and relevant policies in several schools and regions (Moskal et al. 2013 ).
2018.1–2022.12: accelerated transformation period
The period spanning from January 2018 to December 2022 witnessed a rapid transformation in the application of digital technology in education research. The field of digital technology education research reached a peak period of publication, largely influenced by factors such as the COVID-19 pandemic (Yu et al. 2023 ). Research during this period was built upon the achievements, attitudes, and social media of the previous phase, and included more elements that reflect the characteristics of this research field, such as digital literacy, digital competence, and professional development, as depicted in Fig. 6 . Alongside this, scholars’ expectations for the value of digital technology have expanded, and the pursuit of improving learning efficiency and performance is no longer the sole focus. Some research now aims to cultivate learners’ motivation and enhance their self-efficacy by applying digital technology in a reasonable manner, as demonstrated by recent studies (Beardsley et al. 2021 ; Creely et al. 2021 ).

The COVID-19 pandemic has emerged as a crucial backdrop for the digital technology’s role in sustaining global education, as highlighted by recent scholarly research (Zhou et al. 2022 ; Pan and Zhang, 2020 ; Mo et al. 2022 ). The online learning environment, which is supported by digital technology, has become the primary battleground for global education (Yu, 2022 ). This social context has led to various studies being conducted, with some scholars positing that the pandemic has impacted the traditional teaching order while also expanding learning possibilities in terms of patterns and forms (Alabdulaziz, 2021 ). Furthermore, the pandemic has acted as a catalyst for teacher teaching and technological innovation, and this viewpoint has been empirically substantiated (Moorhouse and Wong, 2021 ). Additionally, some scholars believe that the pandemic’s push is a crucial driving force for the digital transformation of the education system, serving as an essential mechanism for overcoming the system’s inertia (Romero et al. 2021 ).
The rapid outbreak of the pandemic posed a challenge to the large-scale implementation of digital technologies, which was influenced by a complex interplay of subjective and objective factors. Objective constraints included the lack of infrastructure in some regions to support digital technologies, while subjective obstacles included psychological resistance among certain students and teachers (Moorhouse, 2021 ). These factors greatly impacted the progress of online learning during the pandemic. Additionally, Timotheou et al. ( 2023 ) conducted a comprehensive systematic review of existing research on digital technology use during the pandemic, highlighting the critical role played by various factors such as learners’ and teachers’ digital skills, teachers’ personal attributes and professional development, school leadership and management, and administration in facilitating the digitalization and transformation of schools.
The current stage of research is characterized by the pivotal term “digital literacy,” denoting a growing interest in learners’ attitudes and adoption of emerging technologies. Initially, the term “literacy” was restricted to fundamental abilities and knowledge associated with books and print materials (McMillan, 1996 ). However, with the swift advancement of computers and digital technology, there have been various attempts to broaden the scope of literacy beyond its traditional meaning, including game literacy (Buckingham and Burn, 2007 ), information literacy (Eisenberg, 2008 ), and media literacy (Turin and Friesem, 2020 ). Similarly, digital literacy has emerged as a crucial concept, and Gilster and Glister ( 1997 ) were the first to introduce this concept, referring to the proficiency in utilizing technology and processing digital information in academic, professional, and daily life settings. In practical educational settings, learners who possess higher digital literacy often exhibit an aptitude for quickly mastering digital devices and applying them intelligently to education and teaching (Yu, 2022 ).
The utilization of digital technology in education has undergone significant changes over the past two decades, and has been a crucial driver of educational reform with each new technological revolution. The impact of these changes on the underlying logic of digital technology education applications has been noticeable. From computer technology to more recent developments such as virtual reality (VR), augmented reality (AR), and artificial intelligence (AI), the acceleration in digital technology development has been ongoing. Educational reforms spurred by digital technology development continue to be dynamic, as each new digital innovation presents new possibilities and models for teaching practice. This is especially relevant in the post-pandemic era, where the importance of technological progress in supporting teaching cannot be overstated (Mughal et al. 2022 ). Existing digital technologies have already greatly expanded the dimensions of education in both time and space, while future digital technologies aim to expand learners’ perceptions. Researchers have highlighted the potential of integrated technology and immersive technology in the development of the educational metaverse, which is highly anticipated to create a new dimension for the teaching and learning environment, foster a new value system for the discipline of educational technology, and more effectively and efficiently achieve the grand educational blueprint of the United Nations’ Sustainable Development Goals (Zhang et al. 2022 ; Li and Yu, 2023 ).
Hotspot evolution analysis (RQ3)
The examination of keyword evolution reveals a consistent trend in the advancement of digital technology education application research. The emergence and transformation of keywords serve as indicators of the varying research interests in this field. Thus, the utilization of the burst detection function available in CiteSpace allowed for the identification of the top 10 burst words that exhibited a high level of burst strength. This outcome is illustrated in Table 7 .
According to the results presented in Table 7 , the explosive terminology within the realm of digital technology education research has exhibited a concentration mainly between the years 2018 and 2022. Prior to this time frame, the emerging keywords were limited to “information technology” and “computer”. Notably, among them, computer, as an emergent keyword, has always had a high explosive intensity from 2008 to 2018, which reflects the important position of computer in digital technology and is the main carrier of many digital technologies such as Learning Management Systems (LMS) and Assessment and Feedback systems (Barlovits et al. 2022 ).
Since 2018, an increasing number of research studies have focused on evaluating the capabilities of learners to accept, apply, and comprehend digital technologies. As indicated by the use of terms such as “digital literacy” and “digital skill,” the assessment of learners’ digital literacy has become a critical task. Scholarly efforts have been directed towards the development of literacy assessment tools and the implementation of empirical assessments. Furthermore, enhancing the digital literacy of both learners and educators has garnered significant attention. (Nagle, 2018 ; Yu, 2022 ). Simultaneously, given the widespread use of various digital technologies in different formal and informal learning settings, promoting learners’ digital skills has become a crucial objective for contemporary schools (Nygren et al. 2019 ; Forde and OBrien, 2022 ).
Since 2020, the field of applied research on digital technology education has witnessed the emergence of three new hotspots, all of which have been affected to some extent by the pandemic. Firstly, digital technology has been widely applied in physical education, which is one of the subjects that has been severely affected by the pandemic (Parris et al. 2022 ; Jiang and Ning, 2022 ). Secondly, digital transformation has become an important measure for most schools, especially higher education institutions, to cope with the impact of the pandemic globally (García-Morales et al. 2021 ). Although the concept of digital transformation was proposed earlier, the COVID-19 pandemic has greatly accelerated this transformation process. Educational institutions must carefully redesign their educational products to face this new situation, providing timely digital learning methods, environments, tools, and support systems that have far-reaching impacts on modern society (Krishnamurthy, 2020 ; Salas-Pilco et al. 2022 ). Moreover, the professional development of teachers has become a key mission of educational institutions in the post-pandemic era. Teachers need to have a certain level of digital literacy and be familiar with the tools and online teaching resources used in online teaching, which has become a research hotspot today. Organizing digital skills training for teachers to cope with the application of emerging technologies in education is an important issue for teacher professional development and lifelong learning (Garzón-Artacho et al. 2021 ). As the main organizers and practitioners of emergency remote teaching (ERT) during the pandemic, teachers must put cognitive effort into their professional development to ensure effective implementation of ERT (Romero-Hall and Jaramillo Cherrez, 2022 ).
The burst word “digital transformation” reveals that we are in the midst of an ongoing digital technology revolution. With the emergence of innovative digital technologies such as ChatGPT and Microsoft 365 Copilot, technology trends will continue to evolve, albeit unpredictably. While the impact of these advancements on school education remains uncertain, it is anticipated that the widespread integration of technology will significantly affect the current education system. Rejecting emerging technologies without careful consideration is unwise. Like any revolution, the technological revolution in the education field has both positive and negative aspects. Detractors argue that digital technology disrupts learning and memory (Baron, 2021 ) or causes learners to become addicted and distracted from learning (Selwyn and Aagaard, 2020 ). On the other hand, the prudent use of digital technology in education offers a glimpse of a golden age of open learning. Educational leaders and practitioners have the opportunity to leverage cutting-edge digital technologies to address current educational challenges and develop a rational path for the sustainable and healthy growth of education.
Discussion on performance analysis (RQ1)
The field of digital technology education application research has experienced substantial growth since the turn of the century, a phenomenon that is quantifiably apparent through an analysis of authorship, country/region contributions, and institutional engagement. This expansion reflects the increased integration of digital technologies in educational settings and the heightened scholarly interest in understanding and optimizing their use.
Discussion on authorship productivity in digital technology education research
The authorship distribution within digital technology education research is indicative of the field’s intellectual structure and depth. A primary figure in this domain is Neil Selwyn, whose substantial citation rate underscores the profound impact of his work. His focus on the implications of digital technology in higher education and educational sociology has proven to be seminal. Selwyn’s research trajectory, especially the exploration of spatiotemporal extensions of education through technology, provides valuable insights into the multifaceted role of digital tools in learning processes (Selwyn et al. 2019 ).
Other notable contributors, like Henderson and Edwards, present diversified research interests, such as the impact of digital technologies during the pandemic and their application in early childhood education, respectively. Their varied focuses highlight the breadth of digital technology education research, encompassing pedagogical innovation, technological adaptation, and policy development.
Discussion on country/region-level productivity and collaboration
At the country/region level, the United Kingdom, specifically England, emerges as a leading contributor with 92 published papers and a significant citation count. This is closely followed by Australia and the United States, indicating a strong English-speaking research axis. Such geographical concentration of scholarly output often correlates with investment in research and development, technological infrastructure, and the prevalence of higher education institutions engaging in cutting-edge research.
China’s notable inclusion as the only non-Western country among the top contributors to the field suggests a growing research capacity and interest in digital technology in education. However, the lower average citation per paper for China could reflect emerging engagement or different research focuses that may not yet have achieved the same international recognition as Western counterparts.
The chord diagram analysis furthers this understanding, revealing dense interconnections between countries like the United States, China, and England, which indicates robust collaborations. Such collaborations are fundamental in addressing global educational challenges and shaping international research agendas.
Discussion on institutional-level contributions to digital technology education
Institutional productivity in digital technology education research reveals a constellation of universities driving the field forward. Monash University and the Australian Catholic University have the highest publication output, signaling Australia’s significant role in advancing digital education research. The University of Oslo’s remarkable average citation count per publication indicates influential research contributions, potentially reflecting high-quality studies that resonate with the broader academic community.
The strong showing of UK institutions, including the University of London, The Open University, and the University of Cambridge, reinforces the UK’s prominence in this research field. Such institutions are often at the forefront of pedagogical innovation, benefiting from established research cultures and funding mechanisms that support sustained inquiry into digital education.
Discussion on journal publication analysis
An examination of journal outputs offers a lens into the communicative channels of the field’s knowledge base. Journals such as Education and Information Technologies , Computers & Education , and the British Journal of Educational Technology not only serve as the primary disseminators of research findings but also as indicators of research quality and relevance. The impact factor (IF) serves as a proxy for the quality and influence of these journals within the academic community.
The high citation counts for articles published in Computers & Education suggest that research disseminated through this medium has a wide-reaching impact and is of particular interest to the field. This is further evidenced by its significant IF of 11.182, indicating that the journal is a pivotal platform for seminal work in the application of digital technology in education.
The authorship, regional, and institutional productivity in the field of digital technology education application research collectively narrate the evolution of this domain since the turn of the century. The prominence of certain authors and countries underscores the importance of socioeconomic factors and existing academic infrastructure in fostering research productivity. Meanwhile, the centrality of specific journals as outlets for high-impact research emphasizes the role of academic publishing in shaping the research landscape.
As the field continues to grow, future research may benefit from leveraging the collaborative networks that have been elucidated through this analysis, perhaps focusing on underrepresented regions to broaden the scope and diversity of research. Furthermore, the stabilization of publication numbers in recent years invites a deeper exploration into potential plateaus in research trends or saturation in certain sub-fields, signaling an opportunity for novel inquiries and methodological innovations.
Discussion on the evolutionary trends (RQ2)
The evolution of the research field concerning the application of digital technology in education over the past two decades is a story of convergence, diversification, and transformation, shaped by rapid technological advancements and shifting educational paradigms.
At the turn of the century, the inception of digital technology in education was largely exploratory, with a focus on how emerging computer technologies could be harnessed to enhance traditional learning environments. Research from this early period was primarily descriptive, reflecting on the potential and challenges of incorporating digital tools into the educational setting. This phase was critical in establishing the fundamental discourse that would guide subsequent research, as it set the stage for understanding the scope and impact of digital technology in learning spaces (Wang et al. 2023 ).
As the first decade progressed, the narrative expanded to encompass the pedagogical implications of digital technologies. This was a period of conceptual debates, where terms like “digital natives” and “disruptive pedagogy” entered the academic lexicon, underscoring the growing acknowledgment of digital technology as a transformative force within education (Bennett and Maton, 2010 ). During this time, the research began to reflect a more nuanced understanding of the integration of technology, considering not only its potential to change where and how learning occurred but also its implications for educational equity and access.
In the second decade, with the maturation of internet connectivity and mobile technology, the focus of research shifted from theoretical speculations to empirical investigations. The proliferation of digital devices and the ubiquity of social media influenced how learners interacted with information and each other, prompting a surge in studies that sought to measure the impact of these tools on learning outcomes. The digital divide and issues related to digital literacy became central concerns, as scholars explored the varying capacities of students and educators to engage with technology effectively.
Throughout this period, there was an increasing emphasis on the individualization of learning experiences, facilitated by adaptive technologies that could cater to the unique needs and pacing of learners (Jing et al. 2023a ). This individualization was coupled with a growing recognition of the importance of collaborative learning, both online and offline, and the role of digital tools in supporting these processes. Blended learning models, which combined face-to-face instruction with online resources, emerged as a significant trend, advocating for a balance between traditional pedagogies and innovative digital strategies.
The later years, particularly marked by the COVID-19 pandemic, accelerated the necessity for digital technology in education, transforming it from a supplementary tool to an essential platform for delivering education globally (Mo et al. 2022 ; Mustapha et al. 2021 ). This era brought about an unprecedented focus on online learning environments, distance education, and virtual classrooms. Research became more granular, examining not just the pedagogical effectiveness of digital tools, but also their role in maintaining continuity of education during crises, their impact on teacher and student well-being, and their implications for the future of educational policy and infrastructure.
Across these two decades, the research field has seen a shift from examining digital technology as an external addition to the educational process, to viewing it as an integral component of curriculum design, instructional strategies, and even assessment methods. The emergent themes have broadened from a narrow focus on specific tools or platforms to include wider considerations such as data privacy, ethical use of technology, and the environmental impact of digital tools.
Moreover, the field has moved from considering the application of digital technology in education as a primarily cognitive endeavor to recognizing its role in facilitating socio-emotional learning, digital citizenship, and global competencies. Researchers have increasingly turned their attention to the ways in which technology can support collaborative skills, cultural understanding, and ethical reasoning within diverse student populations.
In summary, the past over twenty years in the research field of digital technology applications in education have been characterized by a progression from foundational inquiries to complex analyses of digital integration. This evolution has mirrored the trajectory of technology itself, from a facilitative tool to a pervasive ecosystem defining contemporary educational experiences. As we look to the future, the field is poised to delve into the implications of emerging technologies like AI, AR, and VR, and their potential to redefine the educational landscape even further. This ongoing metamorphosis suggests that the application of digital technology in education will continue to be a rich area of inquiry, demanding continual adaptation and forward-thinking from educators and researchers alike.
Discussion on the study of research hotspots (RQ3)
The analysis of keyword evolution in digital technology education application research elucidates the current frontiers in the field, reflecting a trajectory that is in tandem with the rapidly advancing digital age. This landscape is sculpted by emergent technological innovations and shaped by the demands of an increasingly digital society.
Interdisciplinary integration and pedagogical transformation
One of the frontiers identified from recent keyword bursts includes the integration of digital technology into diverse educational contexts, particularly noted with the keyword “physical education.” The digitalization of disciplines traditionally characterized by physical presence illustrates the pervasive reach of technology and signifies a push towards interdisciplinary integration where technology is not only a facilitator but also a transformative agent. This integration challenges educators to reconceptualize curriculum delivery to accommodate digital tools that can enhance or simulate the physical aspects of learning.
Digital literacy and skills acquisition
Another pivotal frontier is the focus on “digital literacy” and “digital skill”, which has intensified in recent years. This suggests a shift from mere access to technology towards a comprehensive understanding and utilization of digital tools. In this realm, the emphasis is not only on the ability to use technology but also on critical thinking, problem-solving, and the ethical use of digital resources (Yu, 2022 ). The acquisition of digital literacy is no longer an additive skill but a fundamental aspect of modern education, essential for navigating and contributing to the digital world.
Educational digital transformation
The keyword “digital transformation” marks a significant research frontier, emphasizing the systemic changes that education institutions must undergo to align with the digital era (Romero et al. 2021 ). This transformation includes the redesigning of learning environments, pedagogical strategies, and assessment methods to harness digital technology’s full potential. Research in this area explores the complexity of institutional change, addressing the infrastructural, cultural, and policy adjustments needed for a seamless digital transition.
Engagement and participation
Further exploration into “engagement” and “participation” underscores the importance of student-centered learning environments that are mediated by technology. The current frontiers examine how digital platforms can foster collaboration, inclusivity, and active learning, potentially leading to more meaningful and personalized educational experiences. Here, the use of technology seeks to support the emotional and cognitive aspects of learning, moving beyond the transactional view of education to one that is relational and interactive.
Professional development and teacher readiness
As the field evolves, “professional development” emerges as a crucial area, particularly in light of the pandemic which necessitated emergency remote teaching. The need for teacher readiness in a digital age is a pressing frontier, with research focusing on the competencies required for educators to effectively integrate technology into their teaching practices. This includes familiarity with digital tools, pedagogical innovation, and an ongoing commitment to personal and professional growth in the digital domain.
Pandemic as a catalyst
The recent pandemic has acted as a catalyst for accelerated research and application in this field, particularly in the domains of “digital transformation,” “professional development,” and “physical education.” This period has been a litmus test for the resilience and adaptability of educational systems to continue their operations in an emergency. Research has thus been directed at understanding how digital technologies can support not only continuity but also enhance the quality and reach of education in such contexts.
Ethical and societal considerations
The frontier of digital technology in education is also expanding to consider broader ethical and societal implications. This includes issues of digital equity, data privacy, and the sociocultural impact of technology on learning communities. The research explores how educational technology can be leveraged to address inequities and create more equitable learning opportunities for all students, regardless of their socioeconomic background.
Innovation and emerging technologies
Looking forward, the frontiers are set to be influenced by ongoing and future technological innovations, such as artificial intelligence (AI) (Wu and Yu, 2023 ; Chen et al. 2022a ). The exploration into how these technologies can be integrated into educational practices to create immersive and adaptive learning experiences represents a bold new chapter for the field.
In conclusion, the current frontiers of research on the application of digital technology in education are multifaceted and dynamic. They reflect an overarching movement towards deeper integration of technology in educational systems and pedagogical practices, where the goals are not only to facilitate learning but to redefine it. As these frontiers continue to expand and evolve, they will shape the educational landscape, requiring a concerted effort from researchers, educators, policymakers, and technologists to navigate the challenges and harness the opportunities presented by the digital revolution in education.
Conclusions and future research
Conclusions.
The utilization of digital technology in education is a research area that cuts across multiple technical and educational domains and continues to experience dynamic growth due to the continuous progress of technology. In this study, a systematic review of this field was conducted through bibliometric techniques to examine its development trajectory. The primary focus of the review was to investigate the leading contributors, productive national institutions, significant publications, and evolving development patterns. The study’s quantitative analysis resulted in several key conclusions that shed light on this research field’s current state and future prospects.
(1) The research field of digital technology education applications has entered a stage of rapid development, particularly in recent years due to the impact of the pandemic, resulting in a peak of publications. Within this field, several key authors (Selwyn, Henderson, Edwards, etc.) and countries/regions (England, Australia, USA, etc.) have emerged, who have made significant contributions. International exchanges in this field have become frequent, with a high degree of internationalization in academic research. Higher education institutions in the UK and Australia are the core productive forces in this field at the institutional level.
(2) Education and Information Technologies , Computers & Education , and the British Journal of Educational Technology are notable journals that publish research related to digital technology education applications. These journals are affiliated with the research field of educational technology and provide effective communication platforms for sharing digital technology education applications.
(3) Over the past two decades, research on digital technology education applications has progressed from its early stages of budding, initial development, and critical exploration to accelerated transformation, and it is currently approaching maturity. Technological progress and changes in the times have been key driving forces for educational transformation and innovation, and both have played important roles in promoting the continuous development of education.
(4) Influenced by the pandemic, three emerging frontiers have emerged in current research on digital technology education applications, which are physical education, digital transformation, and professional development under the promotion of digital technology. These frontier research hotspots reflect the core issues that the education system faces when encountering new technologies. The evolution of research hotspots shows that technology breakthroughs in education’s original boundaries of time and space create new challenges. The continuous self-renewal of education is achieved by solving one hotspot problem after another.
The present study offers significant practical implications for scholars and practitioners in the field of digital technology education applications. Firstly, it presents a well-defined framework of the existing research in this area, serving as a comprehensive guide for new entrants to the field and shedding light on the developmental trajectory of this research domain. Secondly, the study identifies several contemporary research hotspots, thus offering a valuable decision-making resource for scholars aiming to explore potential research directions. Thirdly, the study undertakes an exhaustive analysis of published literature to identify core journals in the field of digital technology education applications, with Sustainability being identified as a promising open access journal that publishes extensively on this topic. This finding can potentially facilitate scholars in selecting appropriate journals for their research outputs.
Limitation and future research
Influenced by some objective factors, this study also has some limitations. First of all, the bibliometrics analysis software has high standards for data. In order to ensure the quality and integrity of the collected data, the research only selects the periodical papers in SCIE and SSCI indexes, which are the core collection of Web of Science database, and excludes other databases, conference papers, editorials and other publications, which may ignore some scientific research and original opinions in the field of digital technology education and application research. In addition, although this study used professional software to carry out bibliometric analysis and obtained more objective quantitative data, the analysis and interpretation of data will inevitably have a certain subjective color, and the influence of subjectivity on data analysis cannot be completely avoided. As such, future research endeavors will broaden the scope of literature screening and proactively engage scholars in the field to gain objective and state-of-the-art insights, while minimizing the adverse impact of personal subjectivity on research analysis.
Data availability
The datasets analyzed during the current study are available in the Dataverse repository: https://doi.org/10.7910/DVN/F9QMHY
Alabdulaziz MS (2021) COVID-19 and the use of digital technology in mathematics education. Educ Inf Technol 26(6):7609–7633. https://doi.org/10.1007/s10639-021-10602-3
Arif TB, Munaf U, Ul-Haque I (2023) The future of medical education and research: is ChatGPT a blessing or blight in disguise? Med Educ Online 28. https://doi.org/10.1080/10872981.2023.2181052
Banerjee M, Chiew D, Patel KT, Johns I, Chappell D, Linton N, Cole GD, Francis DP, Szram J, Ross J, Zaman S (2021) The impact of artificial intelligence on clinical education: perceptions of postgraduate trainee doctors in London (UK) and recommendations for trainers. BMC Med Educ 21. https://doi.org/10.1186/s12909-021-02870-x
Barlovits S, Caldeira A, Fesakis G, Jablonski S, Koutsomanoli Filippaki D, Lázaro C, Ludwig M, Mammana MF, Moura A, Oehler DXK, Recio T, Taranto E, Volika S(2022) Adaptive, synchronous, and mobile online education: developing the ASYMPTOTE learning environment. Mathematics 10:1628. https://doi.org/10.3390/math10101628
Article Google Scholar
Baron NS(2021) Know what? How digital technologies undermine learning and remembering J Pragmat 175:27–37. https://doi.org/10.1016/j.pragma.2021.01.011
Batista J, Morais NS, Ramos F (2016) Researching the use of communication technologies in higher education institutions in Portugal. https://doi.org/10.4018/978-1-5225-0571-6.ch057
Beardsley M, Albó L, Aragón P, Hernández-Leo D (2021) Emergency education effects on teacher abilities and motivation to use digital technologies. Br J Educ Technol 52. https://doi.org/10.1111/bjet.13101
Bennett S, Maton K(2010) Beyond the “digital natives” debate: towards a more nuanced understanding of students’ technology experiences J Comput Assist Learn 26:321–331. https://doi.org/10.1111/j.1365-2729.2010.00360.x
Buckingham D, Burn A (2007) Game literacy in theory and practice 16:323–349
Google Scholar
Bulfin S, Pangrazio L, Selwyn N (2014) Making “MOOCs”: the construction of a new digital higher education within news media discourse. In: The International Review of Research in Open and Distributed Learning 15. https://doi.org/10.19173/irrodl.v15i5.1856
Camilleri MA, Camilleri AC(2016) Digital learning resources and ubiquitous technologies in education Technol Knowl Learn 22:65–82. https://doi.org/10.1007/s10758-016-9287-7
Chen C(2006) CiteSpace II: detecting and visualizing emerging trends and transient patterns in scientific literature J Am Soc Inf Sci Technol 57:359–377. https://doi.org/10.1002/asi.20317
Chen J, Dai J, Zhu K, Xu L(2022) Effects of extended reality on language learning: a meta-analysis Front Psychol 13:1016519. https://doi.org/10.3389/fpsyg.2022.1016519
Article PubMed PubMed Central Google Scholar
Chen J, Wang CL, Tang Y (2022b) Knowledge mapping of volunteer motivation: a bibliometric analysis and cross-cultural comparative study. Front Psychol 13. https://doi.org/10.3389/fpsyg.2022.883150
Cohen A, Soffer T, Henderson M(2022) Students’ use of technology and their perceptions of its usefulness in higher education: International comparison J Comput Assist Learn 38(5):1321–1331. https://doi.org/10.1111/jcal.12678
Collins A, Halverson R(2010) The second educational revolution: rethinking education in the age of technology J Comput Assist Learn 26:18–27. https://doi.org/10.1111/j.1365-2729.2009.00339.x
Conole G, Alevizou P (2010) A literature review of the use of Web 2.0 tools in higher education. Walton Hall, Milton Keynes, UK: the Open University, retrieved 17 February
Creely E, Henriksen D, Crawford R, Henderson M(2021) Exploring creative risk-taking and productive failure in classroom practice. A case study of the perceived self-efficacy and agency of teachers at one school Think Ski Creat 42:100951. https://doi.org/10.1016/j.tsc.2021.100951
Davis N, Eickelmann B, Zaka P(2013) Restructuring of educational systems in the digital age from a co-evolutionary perspective J Comput Assist Learn 29:438–450. https://doi.org/10.1111/jcal.12032
De Belli N (2009) Bibliometrics and citation analysis: from the science citation index to cybermetrics, Scarecrow Press. https://doi.org/10.1111/jcal.12032
Domínguez A, Saenz-de-Navarrete J, de-Marcos L, Fernández-Sanz L, Pagés C, Martínez-Herráiz JJ(2013) Gamifying learning experiences: practical implications and outcomes Comput Educ 63:380–392. https://doi.org/10.1016/j.compedu.2012.12.020
Donnison S (2009) Discourses in conflict: the relationship between Gen Y pre-service teachers, digital technologies and lifelong learning. Australasian J Educ Technol 25. https://doi.org/10.14742/ajet.1138
Durfee SM, Jain S, Shaffer K (2003) Incorporating electronic media into medical student education. Acad Radiol 10:205–210. https://doi.org/10.1016/s1076-6332(03)80046-6
Dzikowski P(2018) A bibliometric analysis of born global firms J Bus Res 85:281–294. https://doi.org/10.1016/j.jbusres.2017.12.054
van Eck NJ, Waltman L(2009) Software survey: VOSviewer, a computer program for bibliometric mapping Scientometrics 84:523–538 https://doi.org/10.1007/s11192-009-0146-3
Edwards S(2013) Digital play in the early years: a contextual response to the problem of integrating technologies and play-based pedagogies in the early childhood curriculum Eur Early Child Educ Res J 21:199–212. https://doi.org/10.1080/1350293x.2013.789190
Edwards S(2015) New concepts of play and the problem of technology, digital media and popular-culture integration with play-based learning in early childhood education Technol Pedagogy Educ 25:513–532 https://doi.org/10.1080/1475939x.2015.1108929
Article MathSciNet Google Scholar
Eisenberg MB(2008) Information literacy: essential skills for the information age DESIDOC J Libr Inf Technol 28:39–47. https://doi.org/10.14429/djlit.28.2.166
Forde C, OBrien A (2022) A literature review of barriers and opportunities presented by digitally enhanced practical skill teaching and learning in health science education. Med Educ Online 27. https://doi.org/10.1080/10872981.2022.2068210
García-Morales VJ, Garrido-Moreno A, Martín-Rojas R (2021) The transformation of higher education after the COVID disruption: emerging challenges in an online learning scenario. Front Psychol 12. https://doi.org/10.3389/fpsyg.2021.616059
Garfield E(2006) The history and meaning of the journal impact factor JAMA 295:90. https://doi.org/10.1001/jama.295.1.90
Article PubMed Google Scholar
Garzón-Artacho E, Sola-Martínez T, Romero-Rodríguez JM, Gómez-García G(2021) Teachers’ perceptions of digital competence at the lifelong learning stage Heliyon 7:e07513. https://doi.org/10.1016/j.heliyon.2021.e07513
Gaviria-Marin M, Merigó JM, Baier-Fuentes H(2019) Knowledge management: a global examination based on bibliometric analysis Technol Forecast Soc Change 140:194–220. https://doi.org/10.1016/j.techfore.2018.07.006
Gilster P, Glister P (1997) Digital literacy. Wiley Computer Pub, New York
Greenhow C, Lewin C(2015) Social media and education: reconceptualizing the boundaries of formal and informal learning Learn Media Technol 41:6–30. https://doi.org/10.1080/17439884.2015.1064954
Hawkins DT(2001) Bibliometrics of electronic journals in information science Infor Res 7(1):7–1. http://informationr.net/ir/7-1/paper120.html
Henderson M, Selwyn N, Finger G, Aston R(2015) Students’ everyday engagement with digital technology in university: exploring patterns of use and “usefulness J High Educ Policy Manag 37:308–319 https://doi.org/10.1080/1360080x.2015.1034424
Huang CK, Neylon C, Hosking R, Montgomery L, Wilson KS, Ozaygen A, Brookes-Kenworthy C (2020) Evaluating the impact of open access policies on research institutions. eLife 9. https://doi.org/10.7554/elife.57067
Hwang GJ, Tsai CC(2011) Research trends in mobile and ubiquitous learning: a review of publications in selected journals from 2001 to 2010 Br J Educ Technol 42:E65–E70. https://doi.org/10.1111/j.1467-8535.2011.01183.x
Hwang GJ, Wu PH, Zhuang YY, Huang YM(2013) Effects of the inquiry-based mobile learning model on the cognitive load and learning achievement of students Interact Learn Environ 21:338–354. https://doi.org/10.1080/10494820.2011.575789
Jiang S, Ning CF (2022) Interactive communication in the process of physical education: are social media contributing to the improvement of physical training performance. Universal Access Inf Soc, 1–10. https://doi.org/10.1007/s10209-022-00911-w
Jing Y, Zhao L, Zhu KK, Wang H, Wang CL, Xia Q(2023) Research landscape of adaptive learning in education: a bibliometric study on research publications from 2000 to 2022 Sustainability 15:3115–3115. https://doi.org/10.3390/su15043115
Jing Y, Wang CL, Chen Y, Wang H, Yu T, Shadiev R (2023b) Bibliometric mapping techniques in educational technology research: a systematic literature review. Educ Inf Technol 1–29. https://doi.org/10.1007/s10639-023-12178-6
Krishnamurthy S (2020) The future of business education: a commentary in the shadow of the Covid-19 pandemic. J Bus Res. https://doi.org/10.1016/j.jbusres.2020.05.034
Kumar S, Lim WM, Pandey N, Christopher Westland J (2021) 20 years of electronic commerce research. Electron Commer Res 21:1–40
Kyza EA, Georgiou Y(2018) Scaffolding augmented reality inquiry learning: the design and investigation of the TraceReaders location-based, augmented reality platform Interact Learn Environ 27:211–225. https://doi.org/10.1080/10494820.2018.1458039
Laurillard D(2008) Technology enhanced learning as a tool for pedagogical innovation J Philos Educ 42:521–533. https://doi.org/10.1111/j.1467-9752.2008.00658.x
Li M, Yu Z (2023) A systematic review on the metaverse-based blended English learning. Front Psychol 13. https://doi.org/10.3389/fpsyg.2022.1087508
Luo H, Li G, Feng Q, Yang Y, Zuo M (2021) Virtual reality in K-12 and higher education: a systematic review of the literature from 2000 to 2019. J Comput Assist Learn. https://doi.org/10.1111/jcal.12538
Margaryan A, Littlejohn A, Vojt G(2011) Are digital natives a myth or reality? University students’ use of digital technologies Comput Educ 56:429–440. https://doi.org/10.1016/j.compedu.2010.09.004
McMillan S(1996) Literacy and computer literacy: definitions and comparisons Comput Educ 27:161–170. https://doi.org/10.1016/s0360-1315(96)00026-7
Mo CY, Wang CL, Dai J, Jin P (2022) Video playback speed influence on learning effect from the perspective of personalized adaptive learning: a study based on cognitive load theory. Front Psychology 13. https://doi.org/10.3389/fpsyg.2022.839982
Moorhouse BL (2021) Beginning teaching during COVID-19: newly qualified Hong Kong teachers’ preparedness for online teaching. Educ Stud 1–17. https://doi.org/10.1080/03055698.2021.1964939
Moorhouse BL, Wong KM (2021) The COVID-19 Pandemic as a catalyst for teacher pedagogical and technological innovation and development: teachers’ perspectives. Asia Pac J Educ 1–16. https://doi.org/10.1080/02188791.2021.1988511
Moskal P, Dziuban C, Hartman J (2013) Blended learning: a dangerous idea? Internet High Educ 18:15–23
Mughal MY, Andleeb N, Khurram AFA, Ali MY, Aslam MS, Saleem MN (2022) Perceptions of teaching-learning force about Metaverse for education: a qualitative study. J. Positive School Psychol 6:1738–1745
Mustapha I, Thuy Van N, Shahverdi M, Qureshi MI, Khan N (2021) Effectiveness of digital technology in education during COVID-19 pandemic. a bibliometric analysis. Int J Interact Mob Technol 15:136
Nagle J (2018) Twitter, cyber-violence, and the need for a critical social media literacy in teacher education: a review of the literature. Teach Teach Education 76:86–94
Nazare J, Woolf A, Sysoev I, Ballinger S, Saveski M, Walker M, Roy D (2022) Technology-assisted coaching can increase engagement with learning technology at home and caregivers’ awareness of it. Comput Educ 188:104565
Nguyen UP, Hallinger P (2020) Assessing the distinctive contributions of simulation & gaming to the literature, 1970-2019: a bibliometric review. Simul Gaming 104687812094156. https://doi.org/10.1177/1046878120941569
Nygren H, Nissinen K, Hämäläinen R, Wever B(2019) Lifelong learning: formal, non-formal and informal learning in the context of the use of problem-solving skills in technology-rich environments Br J Educ Technol 50:1759–1770. https://doi.org/10.1111/bjet.12807
Page MJ, McKenzie JE, Bossuyt PM, Boutron I, Hoffmann TC, Mulrow CD, Moher D (2021) The PRISMA 2020 statement: an updated guideline for reporting systematic reviews. Int J Surg 88:105906
Pan SL, Zhang S(2020) From fighting COVID-19 pandemic to tackling sustainable development goals: an opportunity for responsible information systems research Int J Inf Manage 55:102196. https://doi.org/10.1016/j.ijinfomgt.2020.102196
Pan X, Yan E, Cui M, Hua W(2018) Examining the usage, citation, and diffusion patterns of bibliometric mapping software: a comparative study of three tools J Informetr 12:481–493. https://doi.org/10.1016/j.joi.2018.03.005
Parris Z, Cale L, Harris J, Casey A (2022) Physical activity for health, covid-19 and social media: what, where and why?. Movimento, 28. https://doi.org/10.22456/1982-8918.122533
Pasquini LA, Evangelopoulos N (2016) Sociotechnical stewardship in higher education: a field study of social media policy documents. J Comput High Educ 29:218–239
Pérez-Sanagustín M, Hernández-Leo D, Santos P, Delgado Kloos C, Blat J(2014) Augmenting reality and formality of informal and non-formal settings to enhance blended learning IEEE Trans Learn Technol 7:118–131. https://doi.org/10.1109/TLT.2014.2312719
Pinto M, Leite C (2020) Digital technologies in support of students learning in Higher Education: literature review. Digital Education Review 343–360. https://doi.org/10.1344/der.2020.37.343-360
Pires F, Masanet MJ, Tomasena JM, Scolari CA(2022) Learning with YouTube: beyond formal and informal through new actors, strategies and affordances Convergence 28(3):838–853. https://doi.org/10.1177/1354856521102054
Pritchard A (1969) Statistical bibliography or bibliometrics 25:348
Romero M, Romeu T, Guitert M, Baztán P (2021) Digital transformation in higher education: the UOC case. In ICERI2021 Proceedings (pp. 6695–6703). IATED https://doi.org/10.21125/iceri.2021.1512
Romero-Hall E, Jaramillo Cherrez N (2022) Teaching in times of disruption: faculty digital literacy in higher education during the COVID-19 pandemic. Innovations in Education and Teaching International 1–11. https://doi.org/10.1080/14703297.2022.2030782
Rospigliosi PA(2023) Artificial intelligence in teaching and learning: what questions should we ask of ChatGPT? Interactive Learning Environments 31:1–3. https://doi.org/10.1080/10494820.2023.2180191
Salas-Pilco SZ, Yang Y, Zhang Z(2022) Student engagement in online learning in Latin American higher education during the COVID-19 pandemic: a systematic review. Br J Educ Technol 53(3):593–619. https://doi.org/10.1111/bjet.13190
Selwyn N(2009) The digital native-myth and reality In Aslib proceedings 61(4):364–379. https://doi.org/10.1108/00012530910973776
Selwyn N(2012) Making sense of young people, education and digital technology: the role of sociological theory Oxford Review of Education 38:81–96. https://doi.org/10.1080/03054985.2011.577949
Selwyn N, Facer K(2014) The sociology of education and digital technology: past, present and future Oxford Rev Educ 40:482–496. https://doi.org/10.1080/03054985.2014.933005
Selwyn N, Banaji S, Hadjithoma-Garstka C, Clark W(2011) Providing a platform for parents? Exploring the nature of parental engagement with school Learning Platforms J Comput Assist Learn 27:314–323. https://doi.org/10.1111/j.1365-2729.2011.00428.x
Selwyn N, Aagaard J (2020) Banning mobile phones from classrooms-an opportunity to advance understandings of technology addiction, distraction and cyberbullying. Br J Educ Technol 52. https://doi.org/10.1111/bjet.12943
Selwyn N, O’Neill C, Smith G, Andrejevic M, Gu X (2021) A necessary evil? The rise of online exam proctoring in Australian universities. Media Int Austr 1329878X2110058. https://doi.org/10.1177/1329878x211005862
Selwyn N, Pangrazio L, Nemorin S, Perrotta C (2019) What might the school of 2030 be like? An exercise in social science fiction. Learn, Media Technol 1–17. https://doi.org/10.1080/17439884.2020.1694944
Selwyn, N (2016) What works and why?* Understanding successful technology enabled learning within institutional contexts 2016 Final report Appendices (Part B). Monash University Griffith University
Sjöberg D, Holmgren R (2021) Informal workplace learning in swedish police education-a teacher perspective. Vocations and Learning. https://doi.org/10.1007/s12186-021-09267-3
Strotmann A, Zhao D (2012) Author name disambiguation: what difference does it make in author-based citation analysis? J Am Soc Inf Sci Technol 63:1820–1833
Article CAS Google Scholar
Sutherland R, Facer K, Furlong R, Furlong J(2000) A new environment for education? The computer in the home. Comput Educ 34:195–212. https://doi.org/10.1016/s0360-1315(99)00045-7
Szeto E, Cheng AY-N, Hong J-C(2015) Learning with social media: how do preservice teachers integrate YouTube and Social Media in teaching? Asia-Pac Educ Res 25:35–44. https://doi.org/10.1007/s40299-015-0230-9
Tang E, Lam C(2014) Building an effective online learning community (OLC) in blog-based teaching portfolios Int High Educ 20:79–85. https://doi.org/10.1016/j.iheduc.2012.12.002
Taskin Z, Al U(2019) Natural language processing applications in library and information science Online Inf Rev 43:676–690. https://doi.org/10.1108/oir-07-2018-0217
Tegtmeyer K, Ibsen L, Goldstein B(2001) Computer-assisted learning in critical care: from ENIAC to HAL Crit Care Med 29:N177–N182. https://doi.org/10.1097/00003246-200108001-00006
Article CAS PubMed Google Scholar
Timotheou S, Miliou O, Dimitriadis Y, Sobrino SV, Giannoutsou N, Cachia R, Moné AM, Ioannou A(2023) Impacts of digital technologies on education and factors influencing schools' digital capacity and transformation: a literature review. Educ Inf Technol 28(6):6695–6726. https://doi.org/10.1007/s10639-022-11431-8
Trujillo Maza EM, Gómez Lozano MT, Cardozo Alarcón AC, Moreno Zuluaga L, Gamba Fadul M (2016) Blended learning supported by digital technology and competency-based medical education: a case study of the social medicine course at the Universidad de los Andes, Colombia. Int J Educ Technol High Educ 13. https://doi.org/10.1186/s41239-016-0027-9
Turin O, Friesem Y(2020) Is that media literacy?: Israeli and US media scholars’ perceptions of the field J Media Lit Educ 12:132–144. https://doi.org/10.1007/s11192-009-0146-3
Van Eck NJ, Waltman L (2019) VOSviewer manual. Universiteit Leiden
Vratulis V, Clarke T, Hoban G, Erickson G(2011) Additive and disruptive pedagogies: the use of slowmation as an example of digital technology implementation Teach Teach Educ 27:1179–1188. https://doi.org/10.1016/j.tate.2011.06.004
Wang CL, Dai J, Xu LJ (2022) Big data and data mining in education: a bibliometrics study from 2010 to 2022. In 2022 7th International Conference on Cloud Computing and Big Data Analytics ( ICCCBDA ) (pp. 507-512). IEEE. https://doi.org/10.1109/icccbda55098.2022.9778874
Wang CL, Dai J, Zhu KK, Yu T, Gu XQ (2023) Understanding the continuance intention of college students toward new E-learning spaces based on an integrated model of the TAM and TTF. Int J Hum-Comput Int 1–14. https://doi.org/10.1080/10447318.2023.2291609
Wong L-H, Boticki I, Sun J, Looi C-K(2011) Improving the scaffolds of a mobile-assisted Chinese character forming game via a design-based research cycle Comput Hum Behav 27:1783–1793. https://doi.org/10.1016/j.chb.2011.03.005
Wu R, Yu Z (2023) Do AI chatbots improve students learning outcomes? Evidence from a meta-analysis. Br J Educ Technol. https://doi.org/10.1111/bjet.13334
Yang D, Zhou J, Shi D, Pan Q, Wang D, Chen X, Liu J (2022) Research status, hotspots, and evolutionary trends of global digital education via knowledge graph analysis. Sustainability 14:15157–15157. https://doi.org/10.3390/su142215157
Yu T, Dai J, Wang CL (2023) Adoption of blended learning: Chinese university students’ perspectives. Humanit Soc Sci Commun 10:390. https://doi.org/10.3390/su142215157
Yu Z (2022) Sustaining student roles, digital literacy, learning achievements, and motivation in online learning environments during the COVID-19 pandemic. Sustainability 14:4388. https://doi.org/10.3390/su14084388
Za S, Spagnoletti P, North-Samardzic A(2014) Organisational learning as an emerging process: the generative role of digital tools in informal learning practices Br J Educ Technol 45:1023–1035. https://doi.org/10.1111/bjet.12211
Zhang X, Chen Y, Hu L, Wang Y (2022) The metaverse in education: definition, framework, features, potential applications, challenges, and future research topics. Front Psychol 13:1016300. https://doi.org/10.3389/fpsyg.2022.1016300
Zhou M, Dzingirai C, Hove K, Chitata T, Mugandani R (2022) Adoption, use and enhancement of virtual learning during COVID-19. Education and Information Technologies. https://doi.org/10.1007/s10639-022-10985-x
Download references
Acknowledgements
This research was supported by the Zhejiang Provincial Social Science Planning Project, “Mechanisms and Pathways for Empowering Classroom Teaching through Learning Spaces under the Strategy of High-Quality Education Development”, the 2022 National Social Science Foundation Education Youth Project “Research on the Strategy of Creating Learning Space Value and Empowering Classroom Teaching under the background of ‘Double Reduction’” (Grant No. CCA220319) and the National College Student Innovation and Entrepreneurship Training Program of China (Grant No. 202310337023).
Author information
Authors and affiliations.
College of Educational Science and Technology, Zhejiang University of Technology, Zhejiang, China
Chengliang Wang, Xiaojiao Chen, Yidan Liu & Yuhui Jing
Graduate School of Business, Universiti Sains Malaysia, Minden, Malaysia
Department of Management, The Chinese University of Hong Kong, Hong Kong, China
College of Humanities and Social Sciences, Beihang University, Beijing, China
You can also search for this author in PubMed Google Scholar
Contributions
Conceptualization: Y.J., C.W.; methodology, C.W.; software, C.W., Y.L.; writing-original draft preparation, C.W., Y.L.; writing-review and editing, T.Y., Y.L., C.W.; supervision, X.C., T.Y.; project administration, Y.J.; funding acquisition, X.C., Y.L. All authors read and approved the final manuscript. All authors have read and approved the re-submission of the manuscript.
Corresponding author
Correspondence to Yuhui Jing .
Ethics declarations
Ethical approval.
Ethical approval was not required as the study did not involve human participants.
Informed consent
Informed consent was not required as the study did not involve human participants.
Competing interests
The authors declare no competing interests.

Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
Rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Wang, C., Chen, X., Yu, T. et al. Education reform and change driven by digital technology: a bibliometric study from a global perspective. Humanit Soc Sci Commun 11 , 256 (2024). https://doi.org/10.1057/s41599-024-02717-y
Download citation
Received : 11 July 2023
Accepted : 17 January 2024
Published : 12 February 2024
DOI : https://doi.org/10.1057/s41599-024-02717-y
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
This article is cited by
A meta-analysis of learners’ continuance intention toward online education platforms.
- Chengliang Wang
Education and Information Technologies (2024)
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

Teaching" Values in Technology Education: A Critical Approach for the Theoretical Framework

2002, Learning in Technology Education: Challenges for the
Centre for Technology Education Research Griffith University his paper discusses the issues of values in technology education in the context of a critical review of the literature. It presents the findings of this analysis and argues that the typology of values developed in ...
Related Papers
International Journal of Technology and Design Education
Margarita Pavlova
International Journal of Environmental Studies
Carolyn Hanks
Sorrel Edwards
Romina M Jamieson-Proctor
Dr. Plamen Kushkiev
This paper aims to critique the conceptual framework and paradigmatic nature of two studies that report on empirical data to draw conclusions and claim transferability. The focus is placed on the influence of the raft of beliefs and values the researcher brings to the process of research. My main argument is that research can never be value-free, because research frameworks and designs are underpinned by a set of assumptions about the nature of social reality, what good knowledge is, and how to attain it. Researchers are expected to be self-reflexive and state how their values affect the choice of topic and overall design of their inquiry. In this paper, I deconstruct the theoretical underpinnings and methodological decisions the researchers make to shed light on the influential role of values on the process of educational inquiry. To put my discussion in context, I opt to critique Hariri’s (2014) study, which investigates TEFL university instructors’ emotional attitudes to their st...
e-Pedagogium
Adéla Antlová
Modern education today, some argue, easily integrates and adjusts to new technological developments through fl exible curricula in the areas where these developments are taking place such as in the field of information technology or in the widespread use of the Internet. However, modern education can be criticized for ignoring or failing to lead societies toward a more humane future in the face of massive social and ecological changes. When it decides to encounter those social problems, the solutions that modern education procures are usually based on a fragmented or reductionist mindset that insulates them from many of the factors generating these problems and their interconnections. Th is article aims to examine the basic philosophical assumptions that have shaped the modern learning and educational systems and how the split between facts and values occurred. How well is modern education dealing with modern problems – the crisis of family and community, the worsening situation of civic culture and understanding, malpractice in many financial arenas of the world, global warming and dramatic ecological change across the planet, and etc.? Because the animating ideas behind the models of modern education are so strongly shaped by the infl uence of positivist knowledge and science, they are often inadequate where these issues are concerned because their basic assumptions regarding fundamental and ontological questions which foster students’ inner worlds leave no space for the realm of values. I also more broadly discuss the
Eric Feinblatt
RELATED PAPERS
Post Augustum
Vassiliki Kokkori , Κόκκορη Βασιλική
Weber, T., McPhee, M.J. and Anderssen, R.S. (eds) MODSIM2015, 21st International Congress on Modelling and Simulation
Indian Journal of Agricultural Research
Arcc Journals
SDU International Journal of Educational Studies
Mehmet Akif Ocak
Adam Blackshaw
Gonzalo Muñoz Salvador
Revista Cubana De Medicina Intensiva Y Emergencias
Alberto Garcia Gomez
Revista de la construcción
Ricardo Andrés Castillo Diaz
วารสารพยาบาลสงขลานครินทร์ Songklanagarind Journal of Nursing
Ingkata Kotnara
Foro Educacional
Jorge Carcamo
PODPORA INKLUZÍVNEHO VZDELÁVANIA NA SLOVENSKU A V ZAHRANIČÍ
Rastislav Rosinsky
Gary Libben
Jayne Green
Journal of Traumatic Stress
Journal of digital social research
Nora Madison
European Journal of Neurology
Sven Pålhagen
Nauka ì tehnìka sʹogodnì
Taras Hryhorchuk
Classiques des sciences sociales.
Gilles Gagnė
The New Educational Review
Zdena Kráľová
Pakistan Armed Forces Medical Journal
JPMI (Jurnal Pendidikan Matematika Indonesia)
eka mahendra
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
Education in Human Values
Planting the Seed of Sustainability in Young Minds
- Reference work entry
- First Online: 20 June 2018
- Cite this reference work entry

- Rohana Ulluwishewa 3
2650 Accesses
1 Citations
Most conventional strategies adopted for achieving sustainability are designed to bring about external changes in the form of technological, institutional, and infrastructural changes. However, past experiences in development show without inner changes – changes in our values, which influence our attitudes and behavior – external changes are unable to achieve sustainability. Materialistic values such as money, material possessions, power, social status, recognition, fame, and reputation etc., dominant in our modern society cause our relationships with fellow human beings and with nature to be self-centered and exploitative, and our behavior unsustainable. To achieve sustainability, these external changes need to be supplemented with inner changes to bring a shift from materialistic values to human values: love, truth, right conduct, peace, and nonviolence, leading to relationships that are selfless, loving, and nonexploitative. Thus, human values can play a significant role in achieving sustainability. Recent discoveries in quantum physics and neuroscience have revealed that these human values are intrinsic to human beings and are hardwired in our brains. Education in human values is a program designed to bring out these values and guide our behavior and attitudes. Drawing on empirical evidence from the value-based water education implemented by the United Nations Human Settlements Programme in six African countries, this chapter highlights the potential capacity of education in human values to plant the seed of sustainability in young minds.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Durable hardcover edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
(Sathya Sai Baba was a highly revered spiritual leader and world teacher, whose life and message are inspiring millions of people throughout the world to turn God-ward and to lead more purposeful and moral lives. His timeless and universal teachings, along with the manner in which he leads his own life, are attracting seekers of Truth from all the religions of the world. Yet, he is not seeking to start a new religion. Nor does he wish to direct followers to any particular religion. Rather, he urges us to continue to follow the religion of our choice and/or upbringing. For further information, please visit https://www.sathyasai.org/intro/message.htm )
Andre, D. (2002). Value-based water education: Project overview. In Human values in water education: Creating a new water-use ethics in African cities (pp. 1–10). Nairobi: UN-Habitat
Google Scholar
Arden, J. B. (2010). Rewire your brain: Think your way to a better life . Hoboken: Wiley.
Barraque, B. (2011). Urban water conflicts . Boca Raton: UNESCO Publishing/CRC Press.
Begley, S. (2007). Train your mind change your brain: How new science reveals our extraordinary potential to transform ourselves . New York: Ballantine Books.
Bohn, D. (1980). Wholeness and the implicate order . London: Routledge & Kegan Paul.
Bohn, D., & Hiley, B. J. (1993). The undivided universe . New York: Routledge.
Brown, K. W., & Kasser, T. (2005). Are psychological and ecological well-being compatible? The role of values, mindfulness and lifestyle. Social Indicators Research, 74 , 349–368.
Article Google Scholar
Brudtland Report. (1987). Our common future: Report of the world commission on environment and development . www.un-documents.net/our-common-future.pdf . Accessed 20 July 2017.
Clark, N. (2004). Water education in African cities (Sida Evaluation 4/21) : United Nations Human Settlement Programme. http://www.sida.se/contentassets/94c8423f1b3245208dd27a6aa6dad10c/water-education-in-african-cities---united-nations-human-settlements-program_2129.pdf . Accessed 22 Aug 2017.
Cohen, P., & Cohen, J. (1996). Life values and adolescents mental health . Mahwah: Lawrence Erlbaum Associates, Publishers.
Cozolino, L. (2006). The neuroscience of human relationships: Attachment and the developing social brain . New York: W.W. Norton & Company.
Dahl, A. (2001). Values as the foundation for sustainable behaviour . Paper presented at the 5th annual conference of the International Environment Forum, Hluboka nad Vltavou, Czech Republic, 19–21 Oct 2001.
Dean, L. R., Carroll, J. S., & Chongming, Y. (2007). Materialism, perceived financial problems, and marital satisfaction. Family & Consumer Sciences, 35 (3), 260–281.
Elgin, D. (2009). Living universe . San Francisco: Berrett-Koehler.
Fox, S. (2010). What causes corporate greed? Live Science . https://www.livescience.com/6394-corporate-greed.html . Accessed 20 Aug 2017.
Gatersleben, B., Meadows, J., Abrahamse, W., & Jackson, T. (2008). Materialistic and environmental values of young people . Unpublished manuscript. University of Surrey.
Graaf, J., Wann, D., & Naylor, T. H. (2001). Affluenza: All consuming epidemic . San Francisco: Berrett-Koehler Publishers.
Hailu, D. (2002). Country perspective Ethiopia. In Human values in water education: Creating a new water-use ethics in African cities (pp. 20–23). Nairobi, Kenya: UN-Habitat
Haisch, B. (2009). The god theory: Universes: Zero-point fields, and what’s behind it all . San Francisco: Red Wheel/Weiser.
Hamilton, C., & Denniss, R. (2005). Affluenza: When too much is never enough . Crows Nest: Allen & Unwin.
Ikerd, J. (2015). Sustainability and human values . http://web.missouri.edu/ikerdj/papers/TSU%20--%20Human%20values%20-%20Sustainability.htm . Accessed 20 July 2017.
IRIN. (2013). In Africa, corruption dirties water. http://www.irinnews.org/analysis/2013/03/14 . Accessed 22 Aug 2017.
Johannessen, A. (2002). Human values in water education: Application in water classrooms . In Human values in water education: Creating a new water-use ethics in African cities (pp. 34–37). Nairobi: UN-Habitat
Kanu, V. (2002). Contribution of value-based water education to national educational goals and objectives in Africa: A regional perspective. In Human values in water education: Creating a new water-use ethic in African cities (pp. 15–19). Nairobi, Kenya: UN-Habitat.
Kasser, T. (2002). The high price of materialism . Cambridge, MA: MIT Press.
Kasser, T. (2005). Frugality, generosity, and materialism in children and adolescents. In K. A. Moore & L. H. Lippman (Eds.), What do children need to flourish?: Conceptualizing and measuring indicators of positive development (pp. 357–373). New York: Springer Science.
Chapter Google Scholar
Kasser, T. (2009). Values and ecological sustainability. In S. R. Kellert & J. G. Speth (Eds.), The coming transformation: Values to sustain human and natural communities (pp. 180–204). New Haven: Yale School of Forestry and Environment.
Kasser, T. (2011). Cultural values and the well-being of future generations: A cross-national study. Journal of Cross-Cultural Psychology, 42 (2), 206–215.
Kasser, T., and Ryan, R. M. (1993). A dark side of the American dream: Correlates of financial success as a central life aspiration. Journal of Personal and Social psychology, 65 , 410–422.
Kasser, T., Ryan, R. M., Couchman, C. E., & Sheldon, K. M. (2003). Materialistic values: Their causes and consequences. In T. Kasser & A. D. Kanner (Eds.), Psychology and consumer culture: The struggle for a good life in a materialistic world (pp. 11–29). Washington, DC: American Psychological Association.
Kluckhohn, C. K. (1951). Values and value orientations in the theory of action. In T. Parsons & E. A. Shils (Eds.), Toward a general theory of action . Cambridge, MA: Harvard University Press.
Lanza, R. (2009). Biocentrism: How life and consciousness are the keys to understanding the true nature of the universe . Dallas: Ben Bella Books.
Lanza, R. (2017). Are we part of a single living organism? http://www.robertlanzabiocentrism.com/are-we-part-of-a-single-living-organism/#eSetzJgBzFeT8fiX.99 . Accessed 25 Aug 2017.
Leiserowitz, A., Kates, R., & Parris, T. (2006). Sustainability values, attitudes and behaviours: A review of multi-national and global trends. Annual Review of Environment and Resources, 31 , 413–444.
Lieberman, M. D. (2013). Social: Why our brains are wired to connect . New York: Crown.
McHoskey, J. W. (1999). Machiavellianism, intrinsic versus extrinsic goals, and social interests: A self-determination theory analysis. Motivation and Emotion, 23 , 267–283.
Merzenich, M. (2013). Soft-wired: How the new neuroscience of brain plasticity can change your life . San Francisco: Parnassus Publishing.
Newberg, A., & Waldman, M. R. (2015). How enlightenment change your brain: The new science of transformation . New York: Hay House.
Oto, E. C., & Alaye, F. K. (2002). Country perspective: Ghana. In Human values in water education: Creating a new water-use ethics in African cities (pp. 24–25). Nairobi, Kenya: UN-Habitat.
Pfaff, D. (2007). The neuroscience of fair play: Why we (usually) follow the golden rule . New York: Dana Press.
Pfaff, D. (2015). The altruistic brain: How we are naturally good . Oxford: Oxford University Press.
Plummer, J., & Cross, P. (2006). Tackling corruption in the water sector and sanitation sector in Africa. In J. E. Campos & S. Pradhan (Eds.), The many faces of corruption: Tackling vulnerabilities in sector level . Washington, DC: The World Bank.
Post, S. (2003). Unlimited love: Altruism, compassion and service . Philadelphia: Templeton Press.
Richins, M. L., & Dawson, S. (1992). A consumer values orientation for materialism and its measurement: Scale development and validation. Journal of Consumer Research, 19 , 303–316.
Rizzolatt, G., & Crighero, L. (2004). The mirror-neuron system. Annual Review of Neuroscience, 27 , 169–192.
Rokeach, M. (1973). The nature of human values . New York: Free Press.
Rousseau, B. (2013). Your conscious classroom: The power of reflection . Bloomington: Balboa Press.
Satyasaiuk. (2017). Sathya Sai Schools Zambia. http://www.sathyasaiehv.org.uk/Zambia.htm . Accessed 20 Aug 2017.
Schwartz, S. H. (1992). Universals in the content and structure of values: Theory and empirical tests in 20 countries. In M. Zanna (Ed.), Advances in experimental social psychology (Vol. 25, pp. 1–65). New York: Academic Press.
Schwartz, S. H. (1996). Value priorities and behaviour: Applying of theory of integrated value systems. In C. Seligman, J. M. Olson, & M. P. Zanna (Eds.), The psychology of values: The Ontario symposium (Vol. 8, pp. 1–24). Hillsdale: Erlbaum.
Schwartz, S. H. (2006). Basic human values: Theory, measurement, and applications. Revue Française de Sociologie, 47 (4), 929.
Sheldon, K. M., & McGregor, H. M. (2000). Extrinsic value orientation and the tragedy of the commons. Journal of Personality, 68 , 383–411.
Tomasello, M. (2008). For kids altruism comes naturally, psychologist says. Stanford News . http://news.stanford.edu/news/2008/november5/tanner-110508.html . Accessed 20 June 2017.
Trainer, T. (2007). Renewable energy cannot sustain a consumer society . Dordrecht: Springer.
Ulluwishewa, R. (2014). Spirituality and sustainable development . Hampshire: Palgrave Macmillan.
Book Google Scholar
Ulluwishewa, R. (2016). Spirituality, sustainability and happiness: A quantum-neuroscientific perspective. In S. Dhiman & J. Marques (Eds.), Spirituality and sustainability: New horizons and exemplary approaches . Switzerland: Springer International.
UNESCO. (2012). Managing water under uncertainty and risk , United Nations world water development report, 4 . Paris: UNESCO.
UN-Habitat. (2002). Human values in water education: Creating a new water-use ethic in African cities. Nairobi, Kenya: UN-Habitat.
Warneken, F., & Tomasello, M. (2013). Altruistic helping in human infants and young chimpanzees. Science, 311 , 1302–1303. http://www.eva.mpg.de/psycho/staff/tomas/pdf/Warn_Science.pdf . Accessed 20 June 2017.
Williams, G. C., Cox, E. M., Hedberg, V. A., & Deci, E. L. (2000). Extrinsic life goals and health risk behaviours in adolescents. Journal of Applied Social Psychology, 30 , 1756–1771.
Download references
Acknowledgments
The author wishes to thank Richard Wallis and Kim Penny for providing editorial assistance.
Author information
Authors and affiliations.
(Former) Massey University, Palmerston North, New Zealand
Rohana Ulluwishewa
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Rohana Ulluwishewa .
Editor information
Editors and affiliations.
School of Business, Woodbury University, Burbank, California, USA
Joan Marques
Rights and permissions
Reprints and permissions
Copyright information
© 2018 Springer International Publishing AG, part of Springer Nature
About this entry
Cite this entry.
Ulluwishewa, R. (2018). Education in Human Values. In: Marques, J. (eds) Handbook of Engaged Sustainability. Springer, Cham. https://doi.org/10.1007/978-3-319-71312-0_23
Download citation
DOI : https://doi.org/10.1007/978-3-319-71312-0_23
Published : 20 June 2018
Publisher Name : Springer, Cham
Print ISBN : 978-3-319-71311-3
Online ISBN : 978-3-319-71312-0
eBook Packages : Business and Management Reference Module Humanities and Social Sciences Reference Module Business, Economics and Social Sciences
Share this entry
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
- Modern technological education and human values.
- Topics >>
- Civil Services >>
- Education Essays for Competitive Exams -07/18/14
- « Previous
- Next »
- RE: Modern technological education and human values. -navpreet (01/16/15)
- we are going to present a paper on this topic at national seminar.it helps us a lot .
Related Content
- Credit Based Higher Education System-Status, Opportunities a...
- Children should be encouraged to think independently
- India’s contribution to world wisdom
- University education just helps the graduates get a good pla...
- Education should be made free for everyone as is a human rig...
- Students should always learn in their native language
- Children should only take up educational activities in free ...
- Is cramming books the real education?
- Credit - based higher education system - status, opportuniti...
- Parents are the best teachers.
- What is the main reason for people to go to University?
- Children should never be educated at home by their parents.
- Technological advancement rules out the need to learn foreig...
- Should sex education be a part of school curriculum for chil...
- CareerRide on YOUTUBE
- CareerRide on INSTAGRAM
Related Topics
- Security - IAS Mains General Studies Paper - III
- Disaster Management - IAS Mains General Studies Paper - III
- Social Justice - IAS Mains General Studies Paper - II
- Indian culture - IAS Mains General Studies Paper - I
- Science Essays for Competitive Exams
- Questions on Indian polity and Governance
- Technical Support
- Find My Rep
You are here
Science, Technology, & Human Values
Preview this book.
- Description
- Aims and Scope
- Editorial Board
- Abstracting / Indexing
- Submission Guidelines
Since 1972, Science, Technology, & Human Values has provided a forum for cutting-edge research and debate in the field of Science and Technology Studies (STS). This is a collectively edited, peer-reviewed, transnational, interdisciplinary journal containing research, analyses and commentary on the development and dynamics of science and technology, with a focus on their relationship to politics, economy, society and culture.
ST&HV publishes and seeks to foster work that is politically and ethically engaged from scholars from across the social sciences and humanities. It is committed to publishing both field-defining and field-extending work, expanding the purview of the field into new areas, and intervening in a common set of conceptual and topical conversations. The journal publishes work that contributes to STS and makes a contribution with STS, emphasising that theory, method and practice unfold in situated assemblages.
We strongly encourage submissions from scholars from a range of career stages and disciplinary backgrounds, including those located outside Global North institutions and locations.
The journal publishes a variety of formats including:
- Articles that report original empirical research or conceptual analyses that advance thinking in the field of STS and provide provocative new insights and ideas.
- Commentaries that present fresh perspectives on major public issues involving science and technology, or that respond to articles published in the journal, and are usually followed by a reply from the author.
- Review Essays that synthesise, analyze and provide context for multiple new publications on science, technology and their relations with society and culture.
This journal is a member of the Committee on Publication Ethics (COPE) and an official journal of the Society for the Social Studies of Science (4S).
As scientific advances improve our lives, they also complicate how we live and react to the new technologies. More and more, human values come into conflict with scientific advancement as we deal with important issues such as nuclear power, environmental degradation and information technology. Science, Technology, & Human Values is a peer-reviewed, international, interdisciplinary journal containing research, analyses and commentary on the development and dynamics of science and technology, including their relationship to politics, society and culture. The journal provides you with work from scholars in a diverse range of disciplines across the social sciences. Among the disciplines you will find in Science, Technology, & Human Values are: political science, sociology, environmental studies, anthropology, literature, history, economics, and philosophy.
- Abstract Journal of the Educational Resources Information Center (ERIC)
- America: History and Life
- Clarivate Analytics: Current Contents - Physical, Chemical & Earth Sciences
- Corporate ResourceNET - Ebsco
- Current Citations Express
- EBSCO: Human Resources Abstracts
- EBSCO: Vocational & Career Collection
- ERIC Current Index to Journals in Education (CIJE)
- Gale: Diversity Studies Collection
- Historical Abstracts
- International Political Science Abstracts
- MAS FullTEXT
- MasterFILE - Ebsco
- ProQuest: CSA Sociological Abstracts
- ProQuest: International Bibliography of the Social Sciences (IBSS)
- Social SciSearch
- Social Sciences Citation Index (Web of Science)
- Standard Periodical Directory (SPD)
- TOPICsearch - Ebsco
- The Philosopher's Index
ST&HV is committed to science and technology studies scholarship of every sort: conceptual and empirical, analytic and normative, qualitative and quantitative, fundamental and use-driven, provided that it is original, rigorous, logical, and lucid. We welcome work that couples analysis with ideas for action, that promotes dialogue and synthesis among diverse specialties and sectors, and that extends the purview of STS into new areas. ST&HV welcomes scholarship that crosses cultural borders, addresses global challenges, or explores emerging fields of science or technology. The scholarship in our field has attracted broad interdisciplinary interest, and in response ST&HV is committed to remaining an accessible, ecumenical, and readable journal. The motivation and implications of a paper must be clear, its conceptual language must use terms that are widely understood or clearly defined, and its empirical material and methods must be sound and described in sufficient detail.
Manuscript Preparation Guideline
Authors are invited to submit manuscripts of no more than 8,000 words, excluding abstract, endnotes and references. Please submit manuscripts electronically at https://mc.manuscriptcentral.com/sthv as an MS Word file. ST&HV uses the Chicago style for referencing, and we prefer in-text referencing (the author-date approach) and endnotes for extended elaborations/qualifications etc. to the main text. Please be prepared to provide an Abstract as well as five keywords with your manuscript. Author names and addresses should only appear on a removable cover page to facilitate double-blind review. Send all other correspondence to sthv no space journal no space at gmail
1.1. Title, Keywords and Abstracts : Please include an abstract of no more than 200 words. Endnotes and references should follow the text, with tables and figures following on separate pages. To facilitate anonymous review, the name, affiliation, mailing address, phone and fax numbers, and e-mail address of each author should appear in a separate title page that is not included in the main document of a submitted paper. Please also list four to six keywords and any acknowledgments on the title page
1.2. Maximizing online discoverability: The title, keywords and abstract are key to ensuring readers find your article online through online search engines such as Google. Please refer to the information and guidance on how best to title your article, write your abstract and select your keywords by visiting Sage’s Journal Author Gateway Guidelines on how to Help Readers Find Your Article online.
1.3. Author names, affiliations and corresponding author: Where the family name or surname may be ambiguous (e.g., a multiword name), please indicate this clearly. Author affiliations should only reflect the institution(s) where the research was done and will not be changed post publication. Clearly indicate who will handle correspondence at all stages, and the corresponding author should list a permanent email address (which is not related to his/her institution) so that readers can reach the corresponding author after any future job/institution shifts.
1.4. Prepare manuscripts according to the Chicago Manual of Style, 16th Ed. Double-space all material, including the abstract, endnotes, references, quotations, appendixes, and tables. Each table and figure should appear at the end of the document file.
Please make sure to take care of the following areas while preparing the content:
· Page numbers should be mentioned for quoted material in the text. · Abbreviations must be spelled out in first occurrence per CMS style · References should be complete—volume, issue, page numbers (for journal-type references) and publisher name and location (Book-type references)· Accessed dates should be provided for online references
When formatting text and references, please ensure you check the Chicago style (16th ed) for ST&HV. Here is the quick link to the Chicago style:
Chicago Manual of Style
Sage Language Services: Leave the editing to the experts
Sage Language Services can help authors with editing, translation, and formatting of the manuscript prior to journal submission. An author's use of these services in no way guarantees that his or her submission will ultimately be accepted, and any costs incurred are the sole responsibility of the author. For further information, we encourage the authors to visit the Sage Languageservices link.
Manuscript Review Process
Upon receiving a new submission the Editors read papers carefully to determine their appropriateness for the journal – a process that takes about one month. Those submissions deemed appropriate are moved into a double-blind review process – a process that may take up to 6 months. Accepted papers are published ahead of print in OnLine First, and slated for print publication as soon as possible thereafter.
Book Review Essays
Instead of “Book Reviews” ST&HV publishes “Review Essays” (no more than 5,000 words) that cover emerging themes within STS as catalyzed by recently published books in the field. Unlike traditional book reviews, these lengthier essays lend perspective by setting the books’ themes in the wider context of intellectual and methodological achievements, position those books within current debates and research trajectories, and indicate what conceptual and empirical work remains to be done. Review essays will be peer reviewed and otherwise treated as regular article publications, rather than as book reviews. Please let us know if you are interested in undertaking a review essay for ST&HV. Queries should be sent to: [email protected] .
Special Issues
ST&HV regularly publishes Special Issues edited by guest editors. The journal is now implementing a new process involving an annual Call for Proposals for Special Issues. Each year, the Call for Proposals will be issued publicly in March-April and will close in June-July. Please look out for the Call for Proposals in due course as it will be publicised in a number of places including the 4S newsletter “Technoscience”. In the meantime, queries should be sent to: [email protected] .
As part of our commitment to ensuring an ethical, transparent and fair peer review process Sage is a supporting member of ORCID, the Open Researcher and Contributor ID .
ORCID provides a unique and persistent digital identifier that distinguishes researchers from every other researcher, even those who share the same name, and, through integration in key research workflows such as manuscript and grant submission, supports automated linkages between researchers and their professional activities, ensuring that their work is recognized.
We encourage all authors and co-authors to link their ORCIDs to their accounts in our online peer review platforms. It takes seconds to do: click the link when prompted, sign into your ORCID account and our systems are automatically updated. We collect ORCID iDs during the manuscript submission process and your ORCID iD then becomes part of your accepted publication’s metadata, making your work attributable to you and only you. Your ORCID iD is published with your article so that fellow researchers reading your work can link to your ORCID profile and from there link to your other publications.
If you do not already have an ORCID iD please follow this link to create one or visit our ORCID homepage to learn more.
ST&HV may accept submissions of papers that have been posted on pre-print servers; please alert the Editorial Office when submitting and include the DOI for the preprint in the designated field in the manuscript submission system. Authors should not post an updated version of their paper on the preprint server while it is being peer reviewed for possible publication in the journal. If the article is accepted for publication, the author may re-use their work according to the journal's author archiving policy.
If your paper is accepted, you must include a link on your preprint to the final version of your paper.
Visit the Sage Journals and Preprints page for more details about preprints.
- Read Online
- Sample Issues
- Current Issue
- Email Alert
- Permissions
- Foreign rights
- Reprints and sponsorship
- Advertising
Individual Subscription, Print Only
Institutional Subscription, E-access
Institutional Subscription & Backfile Lease, E-access Plus Backfile (All Online Content)
Institutional Subscription, Print Only
Institutional Subscription, Combined (Print & E-access)
Institutional Subscription & Backfile Lease, Combined Plus Backfile (Current Volume Print & All Online Content)
Institutional Backfile Purchase, E-access (Content through 1998)
Individual, Single Print Issue
Institutional, Single Print Issue
To order single issues of this journal, please contact SAGE Customer Services at 1-800-818-7243 / 1-805-583-9774 with details of the volume and issue you would like to purchase.

- Table of Contents
- Random Entry
- Chronological
- Editorial Information
- About the SEP
- Editorial Board
- How to Cite the SEP
- Special Characters
- Advanced Tools
- Support the SEP
- PDFs for SEP Friends
- Make a Donation
- SEPIA for Libraries
- Entry Contents
Bibliography
Academic tools.
- Friends PDF Preview
- Author and Citation Info
- Back to Top
Information Technology and Moral Values
Every action we take leaves a trail of information that could, in principle, be recorded and stored for future use. For instance, one might use the older forms of information technologies of pen and paper and keep a detailed diary listing all the things one did and thought during the day. It might be a daunting task to record all this information this way but there are a growing list of technologies and software applications that can help us collect all manner of data, which in principle, and in practice, can be aggregated together for use in building a data profile about you, a digital diary with millions of entries. Some examples of which might be: a detailed listing of all of your economic transactions; a GPS generated plot of where you traveled; a list of all the web addresses you visited and the details of each search you initiated online; a listing of all your vital signs such as blood pressure and heart rate; all of your dietary intakes for the day; and any other kind of data that can be measured. As you go through this thought experiment you begin to see the complex trail of data that you generate each and every day and how that same data might be efficiently collected and stored though the use of information technologies. It is here we can begin to see how information technology can impact moral values. As this data gathering becomes more automated and ever-present, we must ask who is in control of collecting this data and what is done with it once it has been collected and stored? Which bits of information should be made public, which held private, and which should be allowed to become the property of third parties like corporations? Questions of the production, access, and control of information will be at the heart of moral challenges surrounding the use of information technology.
One might argue that the situation just described is no different from the moral issues revolving around the production, access, and control of any basic necessity of life. If one party has the privilege of the exclusive production, access, and/or control of some natural resource, then that by necessity prohibits others from using this resource without the consent of the exclusive owner. This is not necessarily so with digital information. Digital information is nonexclusory, meaning we can all, at least theoretically, possess the same digital information without excluding its use from others. This is because copying digital information from one source to another does not require eliminating the previous copy. Unlike a physical object, theoretically, we can all possess the same digital object as it can be copied indefinitely with no loss of fidelity. Since making these copies is often so cheap that it is almost without cost, there is no technical obstacle to the spread of all information as long as there are people willing to copy it and distribute it. Only appeals to morality, or economic justice might prevent the distribution of certain forms of information. For example, digital entertainment media, such as songs or video, has been a recurring battleground as users and producers of the digital media fight to either curtail or extend the free distribution of this material. Therefore, understanding the role of moral values in information technology is indispensable to the design and use of these technologies (Johnson, 1985, Moore, 1985, Nissenbaum, 1998, Spinello, 2001). It should be noted that this entry will not directly address the phenomenological approach to the ethics of information technology since there is a detailed entry on this subject available (see the entry on phenomenological approaches to ethics and information technology ).
1. Introduction
2.1.1 moral values in information recording, 2.1.2 moral values in communicating and accessing information, 2.1.3 moral values in organizing and synthesizing information, 2.2 the moral paradox of information technologies, 3.1.1 online games and worlds.
- 3.1.2 The Lure of the Virtual Game Worlds
3.1.3 The Technological Transparency Paradox
3.3 malware, spyware and informational warfare, 3.4.1 acceleration of change, 3.4.2 artificial intelligence and artificial life, 3.4.3 robotics and moral values, 4.1 information technology as a model for moral discovery, 4.2 information technology as a moral system, 4.3 informational organisms as moral agents, other internet resources, related entries.
Information technology is ubiquitous in the lives of people across the globe. These technologies take many forms such as personal computers, smart phones, internet technologies, as well as AI and robotics. In fact, the list is growing constantly and new forms of these technologies are working their way into every aspect of daily life. They all have some form of computation at their core and human users interface with them mostly through applications and other software operating systems. In some cases, such as massive multiplayer online games (see section 3.1.1 below), these technologies are even opening up new ways for humans to interacting with each other. Information technologies are used to record, communicate, synthesize or organize information through the use of computer technologies. Information itself can be understood as any useful data, instructions, or meaningful message content. The word literally means to “give form to” or to shape one’s thoughts. A basic type of information technology might be the proverbial string tied around one’s finger that is used to remind, or inform, someone that they have some specific task to accomplish that day. Here the string stands in for a more complex proposition such as “buy groceries before you come home.” The string itself is not the information, it merely symbolizes the information and therefore this symbol must be correctly interpreted for it to be useful. Which raises the question, what is information itself?
Unfortunately there is not a completely satisfying and philosophically rigorous definition available, though there are at least two very good starting points. For those troubled by the ontological questions regarding information, we might want to simply focus on the symbols and define information as any meaningfully ordered set of symbols. Mathematicians and engineers prefer to focus on this aspect of information, which is called “syntax” and leave the meaningfulness of information or its “semantics” for others to figure out. Claude E. Shannon working at Bell Labs in the forties produced a landmark mathematical theory of communication (1948). In this work he utilized his experiences in cryptography and telephone technologies to work out a mathematical formulation describing how syntactical information can be turned into a signal that is transmitted in such a way as to mitigate noise or other extraneous signals which can then be decoded by the desired receiver of the message (Shannon 1948; Shannon and Weaver 1949). The concepts described by Shannon, (along with additional important innovations made by others who are too many to list), explain the way that information technology works, but we still have the deeper questions to resolve if we want to thoroughly trace the impact of information technologies on moral values. Some philosophers noted the fact that information technologies had highlighted the distinction between syntax and semantics, and have been vocal critics about the inability of technologies to bridge the gap between the two concepts. Meaning that while information technologies might be adept at manipulating syntax, they would be incapable of ever understanding the semantics, or meanings, of the information upon which they worked.
One famous example can be found in the “Chinese Room Argument” (Searle 1980) in which the philosopher John Searle argued that even if one were to build a machine that could take stories written in Chinese as input and then output coherent answers to questions about those stories, it would not prove that the machine itself actually understood what it was doing. The argument rests on the claim that if you replaced the workings of the machine with a person who was not a native Chinese speaker who would then painstakingly follow a set of rules to transform the set of Chinese logograms input into other output symbols. The claim is that that person would not understand the input and also would not know what the system is saying as its output, it is all meaningless symbol manipulation to them. The conclusion is that this admittedly strange system could skillfully use the syntax of the language and story while the person inside would have no ability to understand the semantics, or meaning, of the stories (Searle 1980). Replace the person with electronics and it follows that the electronics also have no understanding of the symbols they are processing. This argument, while provocative is not universally accepted and has lead to decades worth of argument and rebuttal (see the entry on the Chinese room argument ).
Information technology has also had a lasting impression on the philosophical study of logic and information. In this field logic is used as a way to understand information as well as using information science as a way to build the foundations of logic itself (see the entry on logic and information ).
The issues just discussed are fascinating but they are separate arguments that do not necessarily have to be resolved before we can enter a discussion on information technology and moral values. Even purely syntactical machines can still impact many important ethical concerns even if they are completely oblivious to the semantic meaning of the information that they compute.
The second starting point is to explore the more metaphysical role that information might play in philosophy. If we were to begin with the claim that information either constitutes or is closely correlated with what constitutes our existence and the existence of everything around us, then this claim means that information plays an important ontological role in the manner in which the universe operates. Adopting this standpoint places information as a core concern for philosophy and gives rise to the fields philosophy of information and information ethics. In this entry, we will not limit our exploration to just the theory of information but instead look more closely at the actual moral and ethical impacts that information technologies are already having on our societies. Philosophy of Information will not be addressed in detail here but the interested reader can begin with Floridi (2010b, 2011b) for an introduction. Some of the most important aspects of Information Ethics will be outlined in more detail below.
2. The Moral Challenges of Information Technology
The move from one set of dominant information technologies to another is always morally contentious. Socrates lived during the long transition from a largely oral tradition to a newer information technology consisting of writing down words and information and collecting those writings into scrolls and books. Famously Socrates was somewhat antagonistic to writing and scholars claim that he never wrote anything down himself. Ironically, we only know about Socrates’ argument against writing because his student Plato ignored his teacher and wrote them down in a dialogue called “Phaedrus” (Plato). Towards the end of this dialogue Socrates discusses with his friend Phaedrus the “…conditions which make it (writing) proper or improper” (section 274b–479c). Socrates tells a fable of an Egyptian God he names Theuth who gives the gift of writing to a king named Thamus. Thamus is not pleased with the gift and replies,
If men learn this, it will implant forgetfulness in their souls; they will cease to exercise memory because they rely on that which is written, calling things to remembrance no longer from within themselves, but by means of external marks. (Phaedrus, section 275a)
Socrates, who was adept at quoting lines from poems and epics and placing them into his conversations, fears that those who rely on writing will never be able to truly understand and live by these words. For Socrates there is something immoral or false about writing. Books can provide information but they cannot, by themselves, give you the wisdom you need to use or deeply understand that information. Conversely, in an oral tradition you do not simply consult a library, you are the library, a living manifestation of the information you know by heart. For Socrates, reading a book is nowhere near as insightful as talking with its author. Written words,
…seem to talk to you as though they were intelligent, but if you ask them anything about what they say, from a desire to be instructed, they go on telling you the same thing forever. (Phaedrus, section 275d).
His criticism of writing at first glance may seem humorous but the temptation to use recall and call it memory is getting more and more prevalent in modern information technologies. Why learn anything when information is just an Internet search away? In order to avoid Socrates’ worry, information technologies should do more than just provide access to information; they should also help foster wisdom and understanding as well.
2.1 The Fundamental Character of Information Technologies
Early in the information technology revolution Richard Mason suggested that the coming changes in information technologies, such as their roles in education and economic impacts, would necessitate rethinking the social contract (Mason 1986). He worried that they would challenge privacy, accuracy, property and accessibility (PAPA) and to protect our society we “… must formulate a new social contract, one that insures everyone the right to fulfill his or her own human potential” (Mason 1986 P. 11) What he could not have known then was how often we would have to update the social contract as these technologies rapidly change. Information technologies change quickly and move in and out of fashion at a bewildering pace. This makes it difficult to try to list them all and catalog the moral impacts of each. The very fact that this change is so rapid and momentous has caused some to argue that we need to deeply question the ethics of the process of developing emerging technologies (Moor 2008). It has also been argued that the ever morphing nature of information technology is changing our ability to even fully understand moral values as they change. Lorenzo Magnani claims that acquiring knowledge of how that change confounds our ability to reason morally “…has become a duty in our technological world” (Magnani 2007, 93). The legal theorist Larry Lessig warns that the pace of change in information technology is so rapid that it leaves the slow and deliberative process of law and political policy behind and in effect these technologies become lawless, or extralegal. This is due to the fact that by the time a law is written to curtail, for instance, some form of copyright infringement facilitated by a particular file sharing technology, that technology has become out of date and users are on to something else that facilitates even more copyright infringement (Lessig 1999). But even given this rapid pace of change, it remains the case that information technologies or applications can all be categorized into at least three different types – each of which we will look at below.
All information technologies record (store), transmit (communicate), organize and/or synthesize information. For example, a book is a record of information, a telephone is used to communicate information, and the Dewey decimal system organizes information. Many information technologies can accomplish more than one of the above functions and, most notably, the computer can accomplish all of them since it can be described as a universal machine (see the entry on computability and complexity ), so it can be programmed to emulate any form of information technology. In section 2 we will look at some specific example technologies and applications from each of the three types of information technology listed above and track the moral challenges that arise out of the use and design of these particular technologies. In addition to the above we will need to address the growing use of information environments such as massive multiplayer games, which are environments completely composed of information where people can develop alternate lives filled with various forms of social activities (see section 3.3 ). Finally we will look at not only how information technology impacts our moral intuitions but also how it might be changing the very nature of moral reasoning. In section 4 , we will look at information as a technology of morality and how we might program applications and robots to interact with us in a more morally acceptable manner.
The control of information is power, and in an information economy such as we find ourselves today, it may be the ultimate form of political power. We live in a world rich in data and the technology to produce, record, and store vast amounts of this data has developed rapidly. The primary moral concern here is that when we collect, store, and/or access information, it is vital that this be done in a just manner that can reasonably be seen as fair and in the best interests of all parties involved. As was mentioned above, each of us produces a vast amount of information every day that could be recorded and stored as useful data to be accessed later when needed. But moral conundrums arise when that collection, storage and use of our information is done by third parties without our knowledge or done with only our tacit consent. The social institutions that have traditionally exercised this power are things like, religious organizations, universities, libraries, healthcare officials, government agencies, banks and corporations. These entities have access to stored information that gives them a certain amount of power over their customers and constituencies. Today each citizen has access to more and more of that stored information without the necessity of utilizing the traditional mediators of that information and therefore a greater individual share of social power (see Lessig 1999).
One of the great values of modern information technology is that it makes the recording of information easy and almost automatic. Today, a growing number of people enter biometric data such as blood pressure, calorie intake, exercise patterns, etc. into applications designed to help them achieve a healthier lifestyle. This type of data collection could become almost fully automated in the near future. Through the use of smart watches or technologies such as the “Fitbit,” or gathered through a users smartphone, such as applications that use the GPS tracking to track the length and duration of a user’s walk or run. How long until a smartphone collects a running data stream of your blood pressure throughout the day perhaps tagged with geolocation markers of particularly high or low readings? In one sense this could be immensely powerful data that could lead to much healthier lifestyle choices. But it could also be a serious breach in privacy if the information got into the wrong hands, which could be easily accomplished, since third parties have access to information collected on smartphones and online applications. In the next section ( 2.1.2 ) we will look at some theories on how best to ethically communicate this recorded information to preserve privacy. But here we must address a more subtle privacy breach – the collection and recording of data about a users without their knowledge or consent. When searching on the Internet, browser software records all manner of data about our visits to various websites which can, for example, make webpages load faster next time you visit them. Even the websites themselves use various means to record information when your computer has accessed them and they may leave bits of information on your computer which the site can use the next time you visit. Some websites are able to detect which other sites you have visited or which pages on the website you spend the most time on. If someone were following you around a library noting down this kind of information, you might find it uncomfortable or hostile, but online this kind of behavior takes place behind the scenes and is barely noticed by the casual user.
According to some professionals, information technology has all but eliminated the private sphere and that it has been this way for decades. Scott McNealy of Sun Microsystems famously announced in 1999: “You have zero privacy anyway. Get over it” (Sprenger, 1999). Helen Nissenbaum observes that,
[w]here previously, physical barriers and inconvenience might have discouraged all but the most tenacious from ferreting out information, technology makes this available at the click of a button or for a few dollars (Nissenbaum 1997)
and since the time when she wrote this the gathering of personal data has become more automated and cheaper. Clearly, earlier theories of privacy that assumed the inviolability of physical walls no longer apply but as Nissenbaum argues, personal autonomy and intimacy require us to protect privacy nonetheless (Nissenbaum 1997).
A final concern in this section is that information technologies are now storing user data in “the cloud” meaning that the data is stored on a device remotely located from the user and not owned or operated by that user, but the data is then available from anywhere the user happens to be, on any device they happen to be using. This ease of access has the result of also making the relationship one has to one’s own data more tenuous because of the uncertainty about the physical location of that data. Since personal data is crucially important to protect, the third parties that offer “cloud” services need to understand the responsibility of the trust the user is placing in them. If you load all the photographs of your life to a service like Flickr and they were to somehow lose or delete them, this would be a tragic mistake that might be impossible to repair.
Information technology has forced us to rethink earlier notions of privacy that were based on print technologies, such as letters, notes, books, pamphlets, newspapers, etc. The moral values that coalesced around these earlier technologies have been sorely stretched by the easy way that information can be shared and altered using digital information technologies and this has required the rapid development of new moral theories that recognize both the benefits and risks of communicating all manner of information using modern information technologies. The primary moral values that seem to be under pressure from these changes are privacy, confidentiality, ownership, trust, and the veracity of the information being communicated in these new ways.
Who has the final say whether or not some information about a user is communicated or not? Who is allowed to sell your medical records, your financial records, your email, your browser history, etc.? If you do not have control over this process, then how can you enforce your own moral right to privacy? For instance Alan Westin argued in the very early decades of the advance of digital information technologies that control of access to one’s personal information was the key to maintaining privacy (Westin, 1967). It follows that if we care about privacy, then we should give all the control of access to personal information to the individual. Most corporate entities resist this notion for the simple reason that information about users has become a primary commodity in the digital world boosting the vast fortunes of corporations like Google or Facebook. Indeed, there is a great deal of utility each of us gains from the services provided by internet search companies like Google and social networks such as Facebook. It might be argued that it is actually a fair exchange we receive since they provide search results and other applications for free and they offset the cost of creating those valuable serviced by collecting data from individual user behavior that can be monetized in various lucrative ways. A major component of the profit model for these companies is based on directed advertising where the information collected on the user is used to help identify advertising that will be most effective on a particular user based on his or her search history and other online behaviors. Simply by using the free applications offered, each user tacitly agrees to give up some amount of privacy that varies with the applications they are using. Even if we were to agree that there is some utility to the services users receive in this exchange, there are still many potential moral problems with this arrangement. If we follow the argument raised by Westin earlier that privacy is equivalent to information control (ibid.), then we do seem to be ceding our privacy away little by little given that we have almost no control or even much understanding of the vast amounts of digital information that is collected about us.
There is a counterargument to this. Herman Tavani and James Moor (2004) argue that in some cases giving the user more control of their information may actually result in greater loss of privacy. Their primary argument is that no one can actually control all of the information about oneself that is produced every day by our activities. If we focus only on the fraction of it that we can control, we lose sight of the vast mountains of data we cannot (Tavani and Moor, 2004). Tavani and Moor argue that privacy must be recognized by the third parties that do control your information and only if those parties have a commitment to protecting user privacy, will we actually acquire any privacy worth having. Towards this end, they suggest that we think in terms of restricted access to information rather than strict personal control of information (ibid).
Information security is another important moral value that impacts the communication and access of user information. If we grant the control of our information to third parties in exchange for the services they provide, then these entities must also be responsible for restricting the access to that information by others who might use it to harm us (See Epstein 2007; Magnani 2007; Tavani 2007). With enough information, a person’s entire identity can be stolen and used to facilitate fraud and larceny. This type of crime has grown rapidly since the advent of digital information technologies. The victims of these crimes can have their lives ruined as they try to rebuild such things as their credit rating and bank accounts. This has led to the design of computer systems that are more difficult to access and the growth of a new industry dedicated to securing computer systems. Even with these efforts the economic and social impact of cybercrime is growing at a staggering rate. In February of 2018 the cyber-security company McAfee released a report that estimated the world cost in cybercrime was up from $445 billion in 2014 to $608 billion dollars or 0.8 of the global GDP in 2018, and that is not counting the hidden costs of increased friction and productivity loss in time spent trying to fight cybercrime (McAfee 2018).
The difficulty in obtaining complete digital security rests on the fact that the moral value of security can be in conflict with the moral values of sharing and openness, and it is these later values that guided many of the early builders of information technology. Steven Levy (1984) describes in his book, “Hackers: Heroes of the Computer Revolution,” a kind of “Hacker ethic,” that includes the idea that computers should be freely accessible and decentralized in order to facilitate “world improvement” and further social justice (Levy 1984; see also Markoff 2005). So it seems that information technology has a strong dissonance created in the competing values of security and openness that is worked right into the design of these technologies and this is all based on the competing moral values held by the various people who designed the technologies themselves.
This conflict in values has been debated by philosophers. While many of the hackers interviewed by Levy argue that hacking is not as dangerous as it seems and that it is mostly about gaining access to hidden knowledge of how information technology systems work, Eugene Spafford counters that no computer break-in is entirely harmless and that the harm precludes the possibility of ethical hacking except in the most extreme cases (Spafford 2007). Kenneth Himma largely agrees that the activity of computer hacking is unethical but that politically motivated hacking or “Hacktivism” may have some moral justification, though he is hesitant to give his complete endorsement of the practice due to the largely anonymous nature of the speech entailed by the hacktivist protests (Himma 2007b). Mark Manion and Abby Goodrum agree that hacktivism could be a special case of ethical hacking but warn that it should proceed in accordance to the moral norms set by the acts of civil disobedience that marked the twentieth century or risk being classified as online terrorism (Manion and Goodrum 2007).
A very similar value split plays out in other areas as well, particularly in the field of intellectual property rights (see entry on intellectual property/ ) and pornography and censorship (see entry on pornography and censorship ). What information technology adds to these long standing moral debates is the nearly effortless access to information that others might want to control such as intellectual property, dangerous information and pornography (Floridi 1999), as well as providing technological anonymity for both the user and those providing access to the information in question (Nissenbaum 1999; Sullins 2010). For example, even though cases of bullying and stalking occur regularly, the anonymous and remote actions of cyber-bullying and cyberstalking make these behaviors much easier and the perpetrator less likely to be caught. Given that information technologies can make these unethical behaviors more likely, then it can be argued that the design of cyberspace itself tacitly promotes unethical behavior (Adams 2002; Grodzinsky and Tavani 2002). Since the very design capabilities of information technology influence the lives of their users, the moral commitments of the designers of these technologies may dictate the course society will take and our commitments to certain moral values will then be determined by technologists (Brey 2010; Bynum 2000; Ess 2009; Johnson 1985; Magnani 2007; Moor 1985; Spinello 2001; Sullins 2010).
Assuming we are justified in granting access to some store of information that we may be in control of, there is a duty to ensure that that information is truthful, accurate, and useful. A simple experiment will show that information technologies might have some deep problems in this regard. Load a number of different search engines and then type the same search terms in each of them, each will present different results and some of these searches will vary widely from one another. This shows that each of these services uses a different proprietary algorithm for presenting the user with results from their search. It follows then that not all searches are equal and the truthfulness, accuracy, and usefulness of the results will depend greatly on which search provider you are using and how much user information is shared with this provider. All searches are filtered by various algorithms in order to ensure that the information the search provider believes is most important to the user is listed first. Since these algorithms are not made public and are closely held trade secrets, users are placing a great deal of trust in this filtering process. The hope is that these filtering decisions are morally justifiable but it is difficult to know. A simple example is found in “clickjacking.” If we are told a link will take us to one location on the web yet when we click it we are taken to some other place, the user may feel that this is a breach of trust. This is often called “clickjacking” and malicious software can clickjack a browser by taking the user to some other site than what is expected; it will usually be rife with other links that pay the clickjacker for bringing traffic to them (Hansen and Grossman, 2008). Again the anonymity and ease of use that information technology provides can facilitate deceitful practices such as clickjacking. Pettit (2009) suggests that this should cause us to reevaluate the role that moral values such as trust and reliance play in a world of information technology. Anonymity and the ability to hide the authors of news reports online has contributed to the raise of “fake news” or propaganda of various sorts posing as legitimate news. This is a significant problem and will be discussed in section (2.2.3) below
Lastly in this section we must address the impact that the access to information has on social justice. Information technology was largely developed in the Western industrial societies during the twentieth century. But even today the benefits of this technology have not spread evenly around the world and to all socioeconomic demographics. Certain societies and social classes have little to no access to the information easily available to those in more well off and in developed nations, and some of those who have some access have that access heavily censored by their own governments. This situation has come to be called the “digital divide,” and despite efforts to address this gap it may be growing wider. It is worth noting that as the cost of smart phones decreases these technologies are giving some access to the global internet to communities that have been shut out before (Poushter 2016). While much of this gap is driven by economics (see Warschauer 2003), Charles Ess notes that there is also a problem with the forces of a new kind of cyber enabled colonialism and ethnocentrism that can limit the desire of those outside the industrial West to participate in this new “Global Metropolis” (Ess 2009). John Weckert also notes that cultural differences in giving and taking offence play a role in the design of more egalitarian information technologies (Weckert 2007). Others argue that basic moral concerns like privacy are weighed differently in Asian cultures (Hongladarom 2008; Lü 2005).
In addition to storing and communicating information, many information technologies automate the organizing of information as well as synthesizing or mechanically authoring or acting on new information. Norbert Wiener first developed a theory of automated information synthesis which he called Cybernetics (Wiener 1961 [1948]). Wiener realized that a machine could be designed to gather information about the world, derive logical conclusions about that information which would imply certain actions, which the machine could then implement, all without any direct input form a human agent. Wiener quickly saw that if his vision of cybernetics was realized, there would be tremendous moral concerns raised by such machines and he outlined some of them in his book the Human Use of Human Beings (Wiener 1950). Wiener argued that, while this sort of technology could have drastic moral impacts, it was still possible to be proactive and guide the technology in ways that would increase the moral reasoning capabilities of both humans and machines (Bynum 2008).
Machines make decisions that have moral impacts. Wendell Wallach and Colin Allen tell an anecdote in their book “Moral Machines” (2008). One of the authors left on a vacation and when he arrived overseas his credit card stopped working, perplexed, he called the bank and learned that an automatic anti-theft program had decided that there was a high probability that the charges he was trying to make were from someone stealing his card and that in order to protect him the machine had denied his credit card transactions. Here we have a situation where a piece of information technology was making decisions about the probability of nefarious activity happening that resulted in a small amount of harm to the person that it was trying to help. Increasingly, machines make important life changing financial decisions about people without much oversight from human agents. Whether or not you will be given a credit card, mortgage loan, the price you will have to pay for insurance, etc., is very often determined by a machine. For instance if you apply for a credit card, the machine will look for certain data points, like your salary, your credit record, the economic condition of the area you reside in, etc., and then calculate the probability that you will default on your credit card. That probability will either pass a threshold of acceptance or not and determine whether or not you are given the card. The machine can typically learn to make better judgments given the results of earlier decisions it has made. This kind of machine learning and prediction is based on complex logic and mathematics (see for example, Russell and Norvig 2010), this complexity may result in slightly humorous examples of mistaken predictions as told in the anecdote above, or it might be more eventful. For example, the program may interpret the data regarding the identity of one’s friends and acquaintances, his or her recent purchases, and other readily available social data, which might result in the mistaken classification of that person as a potential terrorist, thus altering that person’s life in a powerfully negative way (Sullins 2010). It all depends on the design of the learning and prediction algorithm, something that is typically kept secret, so that it is hard to justify the veracity of the prediction.
Several of the issues raised above result from the moral paradox of Information technologies. Many users want information to be quickly accessible and easy to use and desire that it should come at as low a cost as possible, preferably free. But users also want important and sensitive information to be secure, stable and reliable. Maximizing our value of quick and low cost minimizes our ability to provide secure and high quality information and the reverse is true also. Thus the designers of information technologies are constantly faced with making uncomfortable compromises. The early web pioneer Stewart Brand sums this up well in his famous quote:
In fall 1984, at the first Hackers’ Conference, I said in one discussion session: “On the one hand information wants to be expensive, because it’s so valuable. The right information in the right place just changes your life. On the other hand, information wants to be free, because the cost of getting it out is getting lower and lower all the time. So you have these two fighting against each other” (Clarke 2000—see Other Internet Resources) [ 1 ]
Since these competing moral values are essentially impossible to reconcile, they are likely to continue to be at the heart of moral debates in the use and design of information technologies for the foreseeable future.
3. Specific Moral Challenges at the Cultural Level
In the section above, the focus was on the moral impacts of information technologies on the individual user. In this section, the focus will be on how these technologies shape the moral landscape at the societal level. At the turn of the twentieth century the term “web 2.0” began to surface and it referred to the new way that the world wide web was being used as a medium for information sharing and collaboration as well as a change in the mindset of web designers to include more interoperability and user-centered experiences on their websites. This term has also become associated with “social media” and “social networking.” While the original design of the World Wide Web in 1989 by its creator Tim Berners-Lee was always one that included notions of meeting others and collaborating with them online, users were finally ready to fully exploit those capabilities by 2004 when the first Web 2.0 conference was held by O’Reilly Media (O’Reilly 2007 [2005]). This change has meant that a growing number of people have begun to spend significant portions of their lives online with other users experiencing a new unprecedented lifestyle. Social networking is an important part of many people’s lives worldwide. Vast numbers of people congregate on sites like Facebook and interact with friends old and new, real and virtual. The Internet offers the immersive experience of interacting with others in virtual worlds where environments are constructed entirely out of information. Just now, emerging onto the scene are technologies that will allow us to merge the real and the virtual. This new form of “augmented reality” is facilitated by the fact that many people now carry GPS enabled smart phones and other portable computers with them upon which they can run applications that let them interact with their surroundings and their computers at the same time, perhaps looking at an item though the camera in their device and the “app” calling up information about that entity and displaying it in a bubble above the item. Each of these technologies comes with their own suite of new moral challenges some of which will be discussed below.
3.1 Social Media and Networking
Social networking is a term given to sites and applications which facilitate online social interactions that typically focus on sharing information with other users referred to as “friends.” The most famous of these sites today is Facebook but there are many others, such as Instagram, Twitter, Snapchat, to name just a few. There are a number of moral values that these sites call into question. Shannon Vallor (2011, 2016) has reflected on how sites like Facebook change or even challenge our notion of friendship. Her analysis is based on the Aristotelian theory of friendship (see entry on Aristotle’s ethics ). Aristotle argued that humans realize a good and true life though virtuous friendships. Vallor notes that four key dimensions of Aristotle’s ‘virtuous friendship,’ namely: reciprocity, empathy, self-knowledge and the shared life, and that the first three are found in online social media in ways that can sometimes strengthen friendship (Vallor 2011, 2016). Yet she argues that social media is not yet up to the task of facilitating what Aristotle calls ‘the shared life.’ Meaning that social media can give us shared activities but not the close intimate friendship that shared daily lives can give. (Here is a more complete discussion of Aristotelian friendship ). Thus these media cannot fully support the Aristotelian notion of complete and virtuous friendship by themselves (Vallor 2011). Vallor also has a similar analysis of other Aristotelian virtues such as patience, honesty, and empathy and their problematic application in social media (Vallor 2010). Vallor has gone on to argue that both the users and designers of information technologies need to develop a new virtue that she terms “technomoral wisdom” which can help us foster better online communities and friendships (Vallor, 2016).
Johnny Hartz Søraker (2012) argues for a nuanced understanding of online friendship rather than a rush to normative judgement on the virtues of virtual friends.
Privacy issues abound in the use of social media. James Parrish following Mason (1986) recommends four policies that a user of social media should follow to ensure proper ethical concern for other’s privacy:
- When sharing information on SNS (social network sites), it is not only necessary to consider the privacy of one’s personal information, but the privacy of the information of others who may be tied to the information being shared.
- When sharing information on SNS, it is the responsibility of the one desiring to share information to verify the accuracy of the information before sharing it.
- A user of SNS should not post information about themselves that they feel they may want to retract at some future date. Furthermore, users of SNS should not post information that is the product of the mind of another individual unless they are given consent by that individual. In both cases, once the information is shared, it may be impossible to retract.
- It is the responsibility of the SNS user to determine the authenticity of a person or program before allowing the person or program access to the shared information. (Parrish 2010)
These systems are not normally designed to explicitly infringe on individual privacy, but since these services are typically free there is a strong economic drive for the service providers to harvest at least some information about their user’s activities on the site in order to sell that information to advertisers for directed marketing. This marketing can be done with the provider just selling access to users’ data that has been made anonymous, so that the advertiser knows that the user may be likely to buy a pair of jeans but they do not be given the exact identity of that person. In this way a social network provider can try to maintain the moral value of privacy for its users while still profiting off of linking them with advertisers.
The first moral impact one encounters when contemplating online games is the tendency for these games to portray violence, sexism, and sexual violence. There are many news stories that claim a cause and effect relationship between violence in computer games and real violence. The claim that violence in video games has a causal connection to actual violence has been strongly critiqued by the social scientist Christopher J. Ferguson (Ferguson 2007). However, Mark Coeckelbergh argues that since this relationship is tenuous at best and that the real issue at hand is the effect these games have on one’s moral character (Coeckelbergh 2007). But Coeckelbergh goes on to claim that computer games could be designed to facilitate virtues like empathy and cosmopolitan moral development, thus he is not arguing against all games just those where the violence inhibits moral growth (Coeckelbergh 2007). A good example of this might be the virtual reality experience that was designed by Planned Parenthood in 2017, “…which focuses on the experience of accessing abortion in America, positively influences the way viewers feel about the harassment that many patients, providers, and health center staff experience from opponents of safe, legal abortion” (Planned Parenthood, 2017).
Marcus Schulzke (2010) defends the depiction of violence in video games. Schulzke’s main claim is that actions in a virtual world are very different from actions in the real world. Although a player may “kill” another player in a virtual world, the offended player is instantly back in the game and the two will almost certainly remain friends in the real world. Thus virtual violence is very different from real violence, a distinction that gamers are comfortable with (Schulzke 2010). While virtual violence may seem palatable to some, Morgan Luck (2009) seeks a moral theory that might be able to allow the acceptance of virtual murder but that will not extend to other immoral acts such as pedophilia. Christopher Bartel (2011) is less worried about the distinction Luck attempts to draw; Bartel argues that virtual pedophilia is real child pornography, which is already morally reprehensible and illegal across the globe.
While violence is easy to see in online games, there is a much more substantial moral value at play and that is the politics of virtual worlds. Peter Ludlow and Mark Wallace describe the initial moves to online political culture in their book, The Second Life Herald: The Virtual Tabloid that Witnessed the Dawn of the Metaverse (2007). Ludlow and Wallace chronicle how the players in massive online worlds have begun to form groups and guilds that often confound the designers of the game and are at times in conflict with those that make the game. Their contention is that designers rarely realize that they are creating a space where people intended to live large portions of their lives and engage in real economic and social activity and thus the designers have the moral duties somewhat equivalent to those who may write a political constitution (Ludlow and Wallace 2007). According to Purcell (2008), there is little commitment to democracy or egalitarianism by those who create and own online games and this needs to be discussed, if more and more of us are going to spend time living in these virtual societies.
3.1.2 The Lure of the Virtual in Game Worlds
A persistent concern about the use of computers and especially computer games is that this could result in anti-social behavior and isolation. Yet studies might not support these hypotheses (Gibba, et al. 1983). With the advent of massively multiplayer games as well as video games designed for families the social isolation hypothesis is even harder to believe. These games do, however, raise gender equality issues. James Ivory used online reviews of games to complete a study that shows that male characters outnumber female characters in games and those female images that are in games tend to be overly sexualized (Ivory 2006). Soukup (2007) suggests that gameplay in these virtual worlds is most often based on gameplay that is oriented to masculine styles of play thus potentially alienating women players. And those women that do participate in game play at the highest level play roles in gaming culture that are very different from those the largely heterosexual white male gamers, often leveraging their sexuality to gain acceptance (Taylor et al. 2009). Additionally, Joan M. McMahon and Ronnie Cohen have studied how gender plays a role in the making of ethical decisions in the virtual online world, with women more likely to judge a questionable act as unethical then men (2009). Marcus Johansson suggests that we may be able to mitigate virtual immorality by punishing virtual crimes with virtual penalties in order to foster more ethical virtual communities (Johansson 2009).
The media has raised moral concerns about the way that childhood has been altered by the use of information technology (see for example Jones 2011). Many applications are now designed specifically for babies and toddlers with educational applications or just entertainment to help keep the children occupied while their parents are busy. This encourages children to interact with computers from as early an age as possible. Since children may be susceptible to media manipulation such as advertising we have to ask if this practice is morally acceptable or not. Depending on the particular application being used, it may encourage solitary play that may lead to isolation but others are more engaging with both the parents and the children playing (Siraj-Blatchford 2010). It should also be noted that pediatricians have advised that there are no known benefits to early media use amongst young children but there potential risks (Christakis 2009). Studies have shown that from 1998 to 2008, sedentary lifestyles amongst children in England have resulted in the first measured decline in strength since World War Two (Cohen et al. 2011). It is not clear if this decline is directly attributable to information technology use but it may be a contributing factor. In 2018 the American Academy of Pediatrics released some simple guidelines for parents who may be trying to set realistic limits on this activity ( Tips from the American Academy of Pediatrics ).
One may wonder why social media services tend to be free to use, but none the less, often make fabulous profits for the private companies that offer these services. It is no deep secret that the way these companies make profit is through the selling of information that the users are uploading to the system as they interact with it. The more users, and the more information that they provide, the greater the value that aggregating that information becomes. Mark Zuckerberg stated his philosophical commitment to the social value of this in his letter to shareholders from February 1, 2012:
At Facebook, we build tools to help people connect with the people they want and share what they want, and by doing this we are extending people’s capacity to build and maintain relationships. People sharing more – even if just with their close friends or families – creates a more open culture and leads to a better understanding of the lives and perspectives of others. We believe that this creates a greater number of stronger relationships between people, and that it helps people get exposed to a greater number of diverse perspectives. By helping people form these connections, we hope to rewire the way people spread and consume information. We think the world’s information infrastructure should resemble the social graph “a network built from the bottom up or peer-to-peer, rather than the monolithic, top-down structure that has existed to date. We also believe that giving people control over what they share is a fundamental principle of this rewiring” (Facebook, Inc., 2012).
The social value of perusing this is debatable, but the economic value has been undeniable. At the time this was written, Mark Zuckerberg has been constantly listed in the top ten richest billionaires by Forbes Magazine where he is typically in the top five of that rarefied group. An achievement built on providing a free service to the world. What companies like Facebook do charge for are services, such as directed advertising, which allow third party companies to access information that users have provided to the social media applications. The result is that ads bought on an application such as Facebook are more likely to be seen as useful to viewers who are much more likely to click on these ads and buy the advertised products. The more detailed and personal the information shared, the more valuable it will be to the companies that it is shared with. This radical transparency of sharing deeply personal information with companies like Facebook is encouraged. Those who do use social networking technologies do receive value as evidenced by the rapid growth of this technology. Statista reports that in 2019 there will be 2.77 billion users of social media worldwide and it will grow to 3.02 by 2021 (Statista, 2018). The question here is, what do we give up in order to receive this “free” service? In 2011, back when there were less than a billion social media users the technology critic Andrew Keen warned that, “sharing is a trap,” and that there was a kind of cult of radical transparency developing that clouded our ability to think critically about the kind of power we were giving these companies (Keen, 2011). Even before companies like Facebook were making huge profits, there were those warning of the dangers of the cult of transparency with warning such as:
…it is not surprising that public distrust has grown in the very years in which openness and transparency have been so avidly pursued. Transparency destroys secrecy: but it may not limit the deception and deliberate misinformation that undermine relations of trust. If we want to restore trust we need to reduce deception and lies, rather than secrecy. (O’Neill, 2002)
In the case of Facebook we can see that some of the warnings of the critics were prescient. In April of 2018, Mark Zuckerberg was called before congress where he apologized for the actions of his corporation in a scandal that involved divulging a treasure trove of information about his users to an independent researcher, who then sold it to Cambridge Analytica, which was a company involved in political data analysis. This data was then used to target political ads to the users of Facebook. Many of which were fake ads created by Russian intelligence to disrupt the US election in 2016 (Au-Yeung, 2018).
The philosopher Shannon Vallor critiques the cult of transparency as a version of what she calls the “Technological Transparency Paradox” (Vallor, 2016). She notes that those in favor of developing technologies to promote radically transparent societies, do so under the premise that this openness will increase accountability and democratic ideals. But the paradox is that this cult of transparency often achieves just the opposite with large unaccountable organizations that are not democratically chosen holding information that can be used to weaken democratic societies. This is due to the asymmetrical relationship between the user and the companies with whom she shares all the data of her life. The user is, indeed radically open and transparent to the company, but the algorithms used to mine the data and the 3rd parties that this data is shared with is opaque and not subject to accountability. We, the users of these technologies, are forced to be transparent but the companies profiting off our information are not required to be equally transparent.
Malware and computer virus threats continue to grow at an astonishing rate. Security industry professionals report that while certain types of malware attacks such as spam are falling out of fashion, newer types of attacks such as Ransomware and other methods focused on mobile computing devices, cryptocurrency, and the hacking of cloud computing infrastructure are on the rise outstripping any small relief seen in the slowing down of older forms of attack (Cisco Systems 2018; Kaspersky Lab 2017, McAfee 2018, Symantec 2018). What is clear is that this type of activity will be with us for the foreseeable future. In addition to the largely criminal activity of malware production, we must also consider the related but more morally ambiguous activities of hacking, hacktivism, commercial spyware, and informational warfare. Each of these topics has its own suite of subtle moral ambiguities. We will now explore some of them here.
While there may be wide agreement that the conscious spreading of malware is of questionable morality there is an interesting question as to the morality of malware protection and anti-virus software. With the rise in malicious software there has been a corresponding growth in the security industry which is now a multibillion dollar market. Even with all the money spent on security software there seems to be no slowdown in virus production, in fact quite the opposite has occurred. This raises an interesting business ethics concern; what value are customers receiving for their money from the security industry? The massive proliferation of malware has been shown to be largely beyond the ability of anti-virus software to completely mitigate. There is an important lag in the time between when a new piece of malware is detected by the security community and the eventual release of the security patch and malware removal tools.
The anti-virus modus operandi of receiving a sample, analyzing the sample, adding detection for the sample, performing quality assurance, creating an update, and finally sending the update to their users leaves a huge window of opportunity for the adversary … even assuming that anti-virus users update regularly. (Aycock and Sullins 2010)
In the past most malware creation was motivated by hobbyists and amateurs, but this has changed and now much of this activity is criminal in nature (Cisco Systems 2018; Kaspersky Lab 2017, McAfee 2018, Symantec 2018). Aycock and Sullins (2010) argue that relying on a strong defense is not enough and the situation requires a counteroffensive reply as well and they propose an ethically motivated malware research and creation program. This is not an entirely new idea and it was originally suggested by the Computer Scientist George Ledin in his editorial for the Communications of the ACM , “Not Teaching Viruses and Worms is Harmful” (2005). This idea does run counter to the majority opinion regarding the ethics of learning and deploying malware. Many computer scientists and researchers in information ethics agree that all malware is unethical (Edgar 2003; Himma 2007a; Neumann 2004; Spafford 1992; Spinello 2001). According to Aycock and Sullins, these worries can be mitigated by open research into understanding how malware is created in order to better fight this threat (2010).
When malware and spyware is created by state actors, we enter the world of informational warfare and a new set of moral concerns. Every developed country in the world experiences daily cyber-attacks, with the major target being the United States that experiences a purported 1.8 billion attacks a month in 2010 (Lovely 2010) and 80 billion malicious scans world wide in 2017 (McAfee 2018). The majority of these attacks seem to be just probing for weaknesses but they can devastate a countries internet such as the cyber-attacks on Estonia in 2007 and those in Georgia which occurred in 2008. While the Estonian and Georgian attacks were largely designed to obfuscate communication within the target countries more recently informational warfare has been used to facilitate remote sabotage. The famous Stuxnet virus used to attack Iranian nuclear centrifuges is perhaps the first example of weaponized software capable of creating remotely damaging physical facilities (Cisco Systems 2018). The coming decades will likely see many more cyber weapons deployed by state actors along well-known political fault lines such as those between Israel-America-western Europe vs Iran, and America-Western Europe vs China (Kaspersky Lab 2018). The moral challenge here is to determine when these attacks are considered a severe enough challenge to the sovereignty of a nation to justify military reactions and to react in a justified and ethical manner to them (Arquilla 2010; Denning 2008, Kaspersky Lab 2018).
The primary moral challenge of informational warfare is determining how to use weaponized information technologies in a way that honors our commitments to just and legal warfare. Since warfare is already a morally questionable endeavor it would be preferable if information technologies could be leveraged to lessen violent combat. For instance, one might argue that the Stuxnet virus used undetected from 2005 to 2010 did damage to Iranian nuclear weapons programs that in generations before might have only been accomplished by an air raid or other kinetic military action that would have incurred significant civilian casualties—and that so far there have been no reported human casualties resulting from Stuxnet. Thus malware might lessen the amount of civilian casualties in conflict. The malware known as “Flame” is an interesting case of malware that evidence suggests was designed to aid in espionage. One might argue that more accurate information given to decision makers during wartime should help them make better decisions on the battlefield. On the other hand, these new informational warfare capabilities might allow states to engage in continual low level conflict eschewing efforts for peacemaking which might require political compromise.
3.4 Future Concerns
As was mentioned in the introduction above, information technologies are in a constant state of change and innovation. The internet technologies that have brought about so much social change were scarcely imaginable just decades before they appeared. Even though we may not be able to foresee all possible future information technologies, it is important to try to imagine the changes we are likely to see in emerging technologies. James Moor argues that moral philosophers need to pay particular attention to emerging technologies and help influence the design of these technologies early on to encourage beneficial moral outcomes (Moor 2005). The following sections contain some potential technological concerns.
An information technology has an interesting growth pattern that has been observed since the founding of the industry. Intel engineer Gordon E. Moore noticed that the number of components that could be installed on an integrated circuit doubled every year for a minimal economic cost and he thought it might continue that way for another decade or so from the time he noticed it in 1965 (Moore 1965). History has shown his predictions were rather conservative. This doubling of speed and capabilities along with a halving of costs to produce it has roughly continued every eighteen months since 1965 and is likely to continue. This phenomenon is not limited to computer chips and can also be found in many different forms of information technologies. The potential power of this accelerating change has captured the imagination of the noted inventor and futurist Ray Kurzweil. He has famously predicted that if this doubling of capabilities continues and more and more technologies become information technologies, then there will come a point in time where the change from one generation of information technology to the next will become so massive that it will change everything about what it means to be human. Kurzweil has named this potential event “the Singularity” at which time he predicts that our technology will allow us to become a new post human species (2006). If this is correct, there could be no more profound change to our moral values. There has been some support for this thesis from the technology community with institutes such as the Acceleration Studies Foundation, Future of Humanity Institute, and H+. [ 2 ] Reaction to this hypothesis from philosophers has been mixed but largely critical. For example Mary Midgley (1992) argues that the belief that science and technology will bring us immortality and bodily transcendence is based on pseudoscientific beliefs and a deep fear of death. In a similar vein Sullins (2000) argues that there is often a quasi-religious aspect to the acceptance of transhumanism that is committed to certain outcomes such as uploading of human consciousness into computers as a way to achieve immortality, and that the acceptance of the transhumanist hypothesis influences the values embedded in computer technologies, which can be dismissive or hostile to the human body.
There are other cogent critiques of this argument but none as simple as the realization that:
…there is, after all, a limit to how small things can get before they simply melt. Moore’s Law no longer holds. Just because something grows exponentially for some time, does not mean that it will continue to do so forever… (Floridi, 2016).
While many ethical systems place a primary moral value on preserving and protecting nature and the natural given world, transhumanists do not see any intrinsic value in defining what is natural and what is not and consider arguments to preserve some perceived natural state of the human body as an unjustifiable obstacle to progress. Not all philosophers are critical of transhumanism, as an example Nick Bostrom (2008) of the Future of Humanity Institute at Oxford University argues that putting aside the feasibility argument, we must conclude that there are forms of posthumanism that would lead to long and worthwhile lives and that it would be overall a very good thing for humans to become posthuman if it is at all possible (Bostrom, 2008).
Artificial Intelligence (AI) refers to the many longstanding research projects directed at building information technologies that exhibit some or all aspects of human level intelligence and problem solving. Artificial Life (ALife) is a project that is not as old as AI and is focused on developing information technologies and or synthetic biological technologies that exhibit life functions typically found only in biological entities. A more complete description of logic and AI can be found in the entry on logic and artificial intelligence . ALife essentially sees biology as a kind of naturally occurring information technology that may be reverse engineered and synthesized in other kinds of technologies. Both AI and ALife are vast research projects that defy simple explanation. Instead the focus here is on the moral values that these technologies impact and the way some of these technologies are programmed to affect emotion and moral concern.
3.4.2.1 Artificial Intelligence
Alan Turing is credited with defining the research project that would come to be known as Artificial Intelligence in his seminal 1950 paper “Computing Machinery and Intelligence.” He described the “imitation game,” where a computer attempts to fool a human interlocutor that it is not a computer but another human (Turing 1948, 1950). In 1950, he made the now famous claim that
I believe that in about fifty years’ time…. one will be able to speak of machines thinking without expecting to be contradicted.
A description of the test and its implications to philosophy outside of moral values can be found here (see entry on the Turing test ). Turing’s prediction may have been overly ambitious and in fact some have argued that we are nowhere near the completion of Turing’s dream. For example, Luciano Floridi (2011a) argues that while AI has been very successful as a means of augmenting our own intelligence, but as a branch of cognitive science interested in intelligence production, AI has been a dismal disappointment. The opposite opinion has also been argued and some claim that the Turing Test has already been passed or at least that programmers are on the verge of doing so. For instance it was reported by the BBC in 2014 that the Turing Test had been passed by a program that could convince the judges that it was a 13 year old Ukrainian boy, but even so, many experts remain skeptical (BBC 2014).
For argument’s sake, assume Turing is correct even if he is off in his estimation of when AI will succeed in creating a machine that can converse with you. Yale professor David Gelernter worries that that there would be certain uncomfortable moral issues raised. “You would have no grounds for treating it as a being toward which you have moral duties rather than as a tool to be used as you like” (Gelernter 2007). Gelernter suggests that consciousness is a requirement for moral agency and that we may treat anything without it in any way that we want without moral regard. Sullins (2006) counters this argument by noting that consciousness is not required for moral agency. For instance, nonhuman animals and the other living and nonliving things in our environment must be accorded certain moral rights, and indeed, any Turing capable AI would also have moral duties as well as rights, regardless of its status as a conscious being (Sullins 2006).
AI is certainly capable of creating machines that can converse effectively in simple ways with with human beings as evidenced by Apple Siri, Amazon Alexa, OK Goolge, etc. along with the many systems that businesses use to automate customer service, but these are still a ways away form having the natural kinds of unscripted conversations humans have with one another. But that may not matter when it comes to assessing the moral impact of these technologies. In addition, there are still many other applications that use AI technology. Nearly all of the information technologies we discussed above such as, search, computer games, data mining, malware filtering, robotics, etc., all utilize AI programming techniques. Thus AI will grow to be a primary location for the moral impacts of information technologies. Many governments and professional associations are now developing ethical guidelines and standards to help shape this important technology, on e good example is the Global Initiative on the Ethics of Intelligent and Autonomous Systems (IEEE 2018).
3.4.2.2 Artificial Life
Artificial Life (ALife) is an outgrowth of AI and refers to the use of information technology to simulate or synthesize life functions. The problem of defining life has been an interest in philosophy since its founding. See the entry on life for a look at the concept of life and its philosophical ramifications. If scientists and technologists were to succeed in discovering the necessary and sufficient conditions for life and then successfully synthesize it in a machine or through synthetic biology, then we would be treading on territory that has significant moral impact. Mark Bedau has been tracing the philosophical implications of ALife for some time now and argues that there are two distinct forms of ALife and each would thus have different moral effects if and when we succeed in realizing these separate research agendas (Bedau 2004; Bedau and Parke 2009). One form of ALife is completely computational and is in fact the earliest form of ALife studied. ALife is inspired by the work of the mathematician John von Neumann on self-replicating cellular automata, which von Neumann believed would lead to a computational understanding of biology and the life sciences (1966). The computer scientist Christopher Langton simplified von Neumann’s model greatly and produced a simple cellular automata called “Loops” in the early eighties and helped get the field off the ground by organizing the first few conferences on Artificial Life (1989). Artificial Life programs are quite different from AI programs. Where AI is intent on creating or enhancing intelligence, ALife is content with very simple minded programs that display life functions rather than intelligence. The primary moral concern here is that these programs are designed to self-reproduce and in that way resemble computer viruses and indeed successful ALife programs could become as malware vectors. The second form of ALife is much more morally charged. This form of ALife is based on manipulating actual biological and biochemical processes in such a way as to produce novel life forms not seen in nature.
Scientists at the J. Craig Venter institute were able to synthesize an artificial bacterium called JCVI-syn1.0 in May of 2010. While media paid attention to this breakthrough, they tended to focus on the potential ethical and social impacts of the creation of artificial bacteria. Craig Venter himself launched a public relations campaign trying to steer the conversation about issues relating to creating life. This first episode in the synthesis of life gives us a taste of the excitement and controversy that will be generated when more viable and robust artificial protocells are synthesized. The ethical concerns raised by Wet ALife, as this kind of research is called, are more properly the jurisdiction of bioethics (see entry on theory and bioethics ). But it does have some concern for us here in that Wet ALife is part of the process of turning theories from the life sciences into information technologies. This will tend to blur the boundaries between bioethics and information ethics. Just as software ALife might lead to dangerous malware, so too might Wet ALife lead to dangerous bacteria or other disease agents. Critics suggest that there are strong moral arguments against pursuing this technology and that we should apply the precautionary principle here which states that if there is any chance at a technology causing catastrophic harm, and there is no scientific consensus suggesting that the harm will not occur, then those who wish to develop that technology or pursue that research must prove it to be harmless first (see Epstein 1980). Mark Bedau and Mark Traint argue against a too strong adherence to the precautionary principle by suggesting that instead we should opt for moral courage in pursuing such an important step in human understanding of life (2009). They appeal to the Aristotelian notion of courage, not a headlong and foolhardy rush into the unknown, but a resolute and careful step forward into the possibilities offered by this research.
Information technologies have not been content to remain confined to virtual worlds and software implementations. These technologies are also interacting directly with us through robotics applications. Robotics is an emerging technology but it has already produced a number of applications that have important moral implications. Technologies such as military robotics, medical robotics, personal robotics and the world of sex robots are just some of the already existent uses of robotics that impact on and express our moral commitments (see, Anderson and Anderson 2011; Capurro and Nagenborg 2009; Lin et al. 2012, 2017).
There have already been a number of valuable contributions to the growing fields of machine morality and robot ethics (roboethics). For example, in Wallach and Allen’s book Moral Machines: Teaching Robots Right from Wrong (2010), the authors present ideas for the design and programming of machines that can functionally reason on moral questions as well as examples from the field of robotics where engineers are trying to create machines that can behave in a morally defensible way. The introduction of semi and fully autonomous machines, (meaning machines that make decisions with little or no human intervention), into public life will not be simple. Towards this end, Wallach (2011) has also contributed to the discussion on the role of philosophy in helping to design public policy on the use and regulation of robotics.
Military robotics has proven to be one of the most ethically charged robotics applications (Lin et al. 2008, 2013, Lin 2010; Strawser, 2013). Today these machines are largely remotely operated (telerobots) or semi-autonomous, but over time these machines are likely to become more and more autonomous due to the necessities of modern warfare (Singer 2009). In the first decades of war in the 21 st century robotic weaponry has been involved in numerous killings of both soldiers and noncombatants (Plaw 2013), and this fact alone is of deep moral concern. Gerhard Dabringer has conducted numerous interviews with ethicists and technologists regarding the implications of automated warfare (Dabringer 2010). Many ethicists are cautious in their acceptance of automated warfare with the provision that the technology is used to enhance ethical conduct in war, for instance by reducing civilian and military casualties or helping warfighters follow International Humanitarian Law and other legal and ethical codes of conduct in war (see Lin et al. 2008, 2013; Sullins 2009b), but others have been highly skeptical of the prospects of an ethical autonomous war due to issues like the risk to civilians and the ease in which wars might be declared given that robots will be taking most of the risk (Asaro 2008; Sharkey 2011).
4. Information Technologies of Morality
A key development in the realm of information technologies is that they are not only the object of moral deliberations but they are also beginning to be used as a tool in moral deliberation itself. Since artificial intelligence technologies and applications are a kind of automated problem solvers, and moral deliberations are a kind of problem, it was only a matter of time before automated moral reasoning technologies would emerge. This is still only an emerging technology but it has a number of very interesting moral implications which will be outlined below. The coming decades are likely to see a number of advances in this area and ethicists need to pay close attention to these developments as they happen. Susan and Michael Anderson have collected a number of articles regarding this topic in their book, Machine Ethics (2011), and Rocci Luppicini has a section of his anthology devoted to this topic in the Handbook of Research on Technoethics (2009).
Patrick Grim has been a longtime proponent of the idea that philosophy should utilize information technologies to automate and illustrate philosophical thought experiments (Grim et al. 1998; Grim 2004). Peter Danielson (1998) has also written extensively on this subject beginning with his book Modeling Rationality, Morality, and Evolution with much of the early research in the computational theory of morality centered on using computer models to elucidate the emergence of cooperation between simple software AI or ALife agents (Sullins 2005).
Luciano Floridi and J. W. Sanders argue that information as it is used in the theory of computation can serve as a powerful idea that can help resolve some of the famous moral conundrums in philosophy such as the nature of evil (1999, 2001). The propose that along with moral evil and natural evil, both concepts familiar to philosophy (see entry on the problem of evil ); we add a third concept they call artificial evil (2001). Floridi and Sanders contend that if we do this then we can see that the actions of artificial agents
…to be morally good or evil can be determined even in the absence of biologically sentient participants and thus allows artificial agents not only to perpetrate evil (and for that matter good) but conversely to ‘receive’ or ‘suffer from’ it. (Floridi and Sanders 2001)
Evil can then be equated with something like information dissolution, where the irretrievable loss of information is bad and the preservation of information is good (Floridi and Sanders 2001). This idea can move us closer to a way of measuring the moral impacts of any given action in an information environment.
Early in the twentieth century the American philosopher John Dewey (see entry on John Dewey ) proposed a theory of inquiry based on the instrumental uses of technology. Dewey had an expansive definition of technology which included not only common tools and machines but information systems such as logic, laws and even language as well (Hickman 1990). Dewey argued that we are in a ‘transactional’ relationship with all of these technologies within which we discover and construct our world (Hickman 1990). This is a helpful standpoint to take as it allows us to advance the idea that an information technology of morality and ethics is not impossible. As well as allowing us to take seriously the idea that the relations and transactions between human agents and those that exist between humans and their artifacts have important ontological similarities. While Dewey could only dimly perceive the coming revolutions in information technologies, his theory is useful to us still because he proposed that ethics was not only a theory but a practice and solving problems in ethics is like solving problems in algebra (Hickman 1990). If he is right, then an interesting possibility arises, namely the possibility that ethics and morality are computable problems and therefore it should be possible to create an information technology that can embody moral systems of thought.
In 1974 the philosopher Mario Bunge proposed that we take the notion of a ‘technoethics’ seriously arguing that moral philosophers should emulate the way engineers approach a problem. Engineers do not argue in terms of reasoning by categorical imperatives but instead they use:
… the forms If A produces B , and you value B , chose to do A , and If A produces B and C produces D , and you prefer B to D , choose A rather than C . In short, the rules he comes up with are based on fact and value, I submit that this is the way moral rules ought to be fashioned, namely as rules of conduct deriving from scientific statements and value judgments. In short ethics could be conceived as a branch of technology. (Bunge 1977, 103)
Taking this view seriously implies that the very act of building information technologies is also the act of creating specific moral systems within which human and artificial agents will, at least occasionally, interact through moral transactions. Information technologists may therefore be in the business of creating moral systems whether they know it or not and whether or not they want that responsibility.
The most comprehensive literature that argues in favor of the prospect of using information technology to create artificial moral agents is that of Luciano Floridi (1999, 2002, 2003, 2010b, 2011b), and Floridi with Jeff W. Sanders (1999, 2001, 2004). Floridi (1999) recognizes that issues raised by the ethical impacts of information technologies strain our traditional moral theories. To relieve this friction he argues that what is needed is a broader philosophy of information (2002). After making this move, Floridi (2003) claims that information is a legitimate environment of its own and that has its own intrinsic value that is in some ways similar to the natural environment and in other ways radically foreign but either way the result is that information is on its own a thing that is worthy of ethical concern. Floridi (2003) uses these ideas to create a theoretical model of moral action using the logic of object oriented programming.
His model has seven components; 1) the moral agent a, 2) the moral patient p (or more appropriately, reagent), 3) the interactions of these agents, 4) the agent’s frame of information, 5) the factual information available to the agent concerning the situation that agent is attempting to navigate, 6) the environment the interaction is occurring in, and 7) the situation in which the interaction occurs (Floridi 2003, 3). Note that there is no assumption of the ontology of the agents concerned in the moral relationship modeled and these agents can be any mixture or artificial or natural in origin (Sullins 2009a).
There is additional literature which critiques arguments such as Floridi’s with the hope of expanding the idea of automated moral reasoning so that one can speak of many different types of automated moral technologies form simple applications all the way to full moral agents with rights and responsibilities similar to humans (Adam 2008; Anderson and Anderson 2011; Johnson and Powers 2008; Schmidt 2007; Wallach and Allen 2010).
While scholars recognize that we are still some time from creating information technology that would be unequivocally recognized as an artificial moral agent, there are strong theoretical arguments in suggesting that automated moral reasoning is an eventual possibility and therefore it is an appropriate area of study for those interested in the moral impacts of information technologies.
- Adam, A., 2002, “Cyberstalking and Internet pornography: Gender and the gaze,” Ethics and Information Technology , 4(2): 133–142.
- –––, 2008, “Ethics for things,” Ethics and Information technology , 10(2–3): 149–154.
- American Academy of Pediatrics, 2018, “Tips from the American Academy of Pediatrics to Help Families Manage the Ever Changing Digital Landscape,” May 1, available online .
- Anderson, M. and S. L. Anderson (eds.), 2011, Machine Ethics , Cambridge: Cambridge University Press.
- Arkin, R., 2009, Governing Lethal Behavior in Autonomous Robots , New York: Chapman and Hall/CRC.
- Arquilla, J., 2010, “Conflict, Security and Computer Ethics,” in Floridi 2010a.
- Asaro, P., 2008. “How Just Could a Robot War Be?” in Philip Brey, Adam Briggle and Katinka Waelbers (eds.), Current Issues in Computing And Philosophy , Amsterdam, The Netherlands: IOS Press, pp. 50–64.
- –––, 2009. “Modeling the Moral User: Designing Ethical Interfaces for Tele-Operation,” IEEE Technology & Society , 28(1): 20–24.
- Au-Yeung A., 2018. “Why Investors Remain Bullish On Facebook in Day Two Of Zuckerberg’s Congressional Hearnings,” Forbes , April 11, available online .
- Aycock, J. and J. Sullins, 2010, “Ethical Proactive Threat Research,” Workshop on Ethics in Computer Security Research (LNCS 6054) , New York: Springer, pp. 231–239.
- Bartell, C., 2011, “Resolving the gamer’s dilemma,” Ethics and Information Technology , 14(1):11–16.
- Baase, S., 2008, A Gift of Fire: Social, Legal, and Ethical Issues for Computing and the Internet , Englewood Cliffs, NJ: Prentice Hall.
- BBC, 2014, “Computer AI passes Turing test in ‘world first’,” BBC Technology [ available online ]
- Bedau, M., 2004, “Artificial Life,” in Floridi 2004.
- Bedau, M. and E. Parke (eds.), 2009, The Ethics of Protocells: Moral and Social Implications of Creating Life in the Laboratory , Cambridge: MIT Press.
- Bedau, M. and M. Traint, 2009, “Social and Ethical Implications of Creating Artificial Cells,” in Bedau and Parke 2009.
- Bostrom, N., 2008, “Why I Want to be a Posthuman When I Grow Up,” in Medical Enhancement and Posthumanity , G. Gordijn and R. Chadwick (eds), Berlin: Springer, pp. 107–137.
- Brey, P., 2008, “Virtual Reality and Computer Simulation,” in Himma and Tavanni 2008
- –––, 2010, “Values in Technology and Disclosive Computer Ethics,” in Floridi 2010a.
- Bunge, M. 1977, “Towards a Technoethics,” The Monist , 60(1): 96–107.
- Bynum, T., 2000, “Ethics and the Information Revolution,” Ethics in the Age of Information Technology , pp. 32–55, Linköping, Sweden: Center for Applied Ethics at Linköping University.
- –––, 2008, “Norbert Wiener and the Rise of Information Ethics,” in van den Hoven and Weckert 2008.
- Capurro, R., Nagenborg, M., 2009, Ethics and Robotics , [CITY]: IOS Press
- Christakis, D. A., 2009, “The effects of infant media usage: what do we know and what should we learn?” Acta Pædiatrica , 98 (1): 8–16.
- Cisco Systems, Inc., 2018, Cisco 2018 Annual Security Report: Small and Mighty: How Small and Midmarket Businesses Can Fortify Their Defenses Against Today’s Threats , San Jose, CA: Cisco Systems Inc. [ available online ]
- Coeckelbergh, M., 2007, “Violent Computer Games, Empathy, and Cosmopolitanism,” Ethics and Information Technology , 9(3): 219–231
- Cohen, D. D., C. Voss, M. J. D. Taylor, A. Delextrat, A. A. Ogunleye, and G. R. H. Sandercock, 2011, “Ten-year secular changes in muscular fitness in English children,” Acta Paediatrica , 100(10): e175–e177.
- Danielson, P., 1998, Modeling Rationality, Morality, and Evolution , Oxford: Oxford University Press.
- Dabringer, G., (ed.) 2010, Ethica Themen: Ethical and Legal Aspects of Unmanned Systems, Interviews , Vienna, Austria: Austrian Ministry of Defence and Sports. [ available online ]
- Denning, D., 2008, “The Ethics of Cyber Conflict,” In Himma and Tavanni 2008.
- Dodig-Crnkovic, G., Hofkirchner, W., 2011, “Floridi’s ‘Open Problems in Philosophy of Information’, Ten Years Later,” Information , (2): 327–359. [ available online ]
- Edgar, S.L., 2003, Morality and Machines , Sudbury Massachusetts: Jones and Bartlett.
- Epstein, R., 2007, “The Impact of Computer Security Concerns on Software Development,” in Himma 2007a, pp. 171–202.
- Epstein, L.S. 1980. “Decision-making and the temporal resolution of uncertainty”. International Economic Review 21 (2): 269–283.
- Ess, C., 2009, Digital Media Ethics , Massachusetts: Polity Press.
- Facebook, Inc., 2012, Form S-1: Registration Statement , filed with the United States Securities and Exchange Commission, Washington, DC, available online .
- Floridi, L., 1999, “Information Ethics: On the Theoretical Foundations of Computer Ethics”, Ethics and Information Technology , 1(1): 37–56.
- –––, 2002, “What is the Philosophy of Information?” in Metaphilosophy , 33(1/2): 123–145.
- –––, 2003, “On the Intrinsic Value of Information Objects and the Infosphere,” Ethics and Information Technology , 4(4): 287–304.
- –––, 2004, The Blackwell Guide to the Philosophy of Computing and Information , Blackwell Publishing.
- ––– (ed.), 2010a, The Cambridge Handbook of Information and Computer Ethics , Cambridge: Cambridge University Press.
- –––, 2010b, Information: A Very Short Introduction , Oxford: Oxford University Press.
- –––, 2011a, “Enveloping the World for AI,” The Philosopher’s Magazine , 54: 20–21
- –––, 2011b, The Philosophy of Information , Oxford: Oxford University Press.
- –––, 2016, “Should We be Afraid of AI?”, Neigel Warburton (ed.), Aeon , 09 May 2016, available online .
- Floridi, L. and J. W. Sanders, 1999, “Entropy as Evil in Information Ethics,” Etica & Politica , special issue on Computer Ethics, I(2). [ available online ]
- –––, 2001, “Artificial evil and the foundation of computer ethics,” in Ethics and Information Technology , 3(1): 55–66. doi:10.1023/A:1011440125207
- –––, 2004, “On the Morality of Artificial Agents,” in Minds and Machines , 14(3): 349–379 [ available online ]
- Furguson, C. J., 2007, “The Good The Bad and the Ugly: A Meta-analytic Review of Positive and Negative Effects of Violent Video Games,” Psychiatric Quarterly , 78(4): 309–316.
- Gelernter, D., 2007, “Artificial Intelligence Is Lost in the Woods,” Technology Review , July/August, pp. 62–70. [ available online ]
- Gibba, G. D., J. R. Baileya, T. T. Lambirtha, and W. Wilsona, 1983, “Personality Differences Between High and Low Electronic Video Game Users,” The Journal of Psychology , 114(2): 159–165.
- Grim, P., 2004, “Computational Modeling as a Philosophical Methodology,” In Floridi 2004.
- Grim, P., G. Mar, and P. St. Denis, 1998, The Philosophical Computer: Exploratory Essays in Philosophical Computer Modeling , MIT Press.
- Grodzinsky, F. S. and H. T. Tavani, 2002, “Ethical Reflections on Cyberstalking,” Computers and Society , 32(1): 22–32.
- Hansen, R. and J. Grossman, 2008, “Clickjacking,” SecTheory: Internet Security . [ available online ]
- Hickman, L. A. 1990, John Dewey’s Pragmatic Technology , Bloomington, Indiana: Indiana University Press.
- Himma, K. E. (ed.), 2007a, Internet Security, Hacking, Counterhacking, and Society , Sudbury Massachusetts: Jones and Bartlett Publishers.
- Himma, K. E., 2007b, “Hacking as Politically Motivated Digital Civil Disobedience: Is Hacktivisim Morally Justified?” In Himma 2007a, pp. 73–98.
- Himma, K. E., and H. T. Tavanni (eds.), 2008, The Handbook of Information and Computer Ethics , Wiley-Interscience; 1 st edition
- Hongladarom, S., 2008, “Privacy, Contingency, Identity and the Group,” Handbook of Research on Technoethics. Vol. II , R. Luppicini and Rebecca Adell Eds. Hershey, PA: IGI Global, pp. 496–511.
- IEEE 2018, “Ethically Aligned Design: The IEEE Global Initiative on Ethics of Autonomous and Intelligent Systems”, IEEE [ available online ]
- Ivory, J. D., 2006, “Still a Man’s Game: Gender Representation in Online Reviews of Video Games,” Mass Communication and Society , 9(1): 103–114.
- Johansson, M., 2009, “Why unreal punishments in response to unreal crimes might actually be a really good thing,” Ethics and Information Technology , 11(1): 71–79
- Johnson, D.G., 1985, Computer Ethics , Englewood Cliffs, New Jersey: Prentice Hall. (2 nd ed., 1994; 3 rd ed., 2001; 4 th ed., 2009).
- Johnson D. G., and T. Powers, 2008, “Computers and Surrogate Agents,” In van den Hoven and Weckert 2008.
- Jones, T., 2011, “Techno-toddlers: A is for Apple,” The Guardian , Friday November 18. [ available online ]
- Kaspersky Lab, 2017, Kaspersky Security Bulletin: KASPERSKY LAB THREAT PREDICTIONS FOR 2018 ,Moscow, Russia: Kaspersky Lab ZAO. [ available online ]
- Keen, A., 2011, “Your Life Torn Open, Essay 1: Sharing is a trap,” Wired , 03 Feb 2011, available online .
- Kurzweil, R., 2006, The Singularity is Near , New York: Penguin Press.
- Langton, C. G., (ed.), 1989, Artificial Life: the Proceedings of an Interdisciplinary Workshop on the Synthesis and Simulation of Living Systems , Redwood City: Addison-Wesley.
- Ledin G., 2005, “Not Teaching Viruses and Worms is Harmful” Communications of the ACM , 48(1): 144.
- Lessig, L., 1999, Code and Other Values of Cyberspace , New York: Basic Books.
- Levy, S., 1984, Hackers: Heroes of the Computer Revolution , New York: Anchor Press.
- Lin P., 2010, “Ethical Blowback from Emerging Technologies”, Journal of Military Ethics , 9(4): 313–331.
- Lin, P., K. Abney, and R. Jenkins, 2017, Robot Ethics 2.0: From Autonomous Cars to Artificial Intelligence , Oxford: Oxford University Press.
- Lin, P., K. Abney, and G. Bekey, 2012, Robot Ethics: The Ethical and Social Implications of Robotics , Cambridge, MA: MIT Press.
- –––2013, “Ethics, War, and Robots”, Ethics and Emerging Technologies , London: Palgrave–Macmillan.
- Lin, P., G. Bekey, and K. Abney, 2008, Autonomous Military Robotics: Risk, Ethics, and Design , Washington, DC: U.S. Department of the Navy, Office of Naval Research. [ available online ]
- Lovely, E., 2010, “Cyberattacks explode in Congress,” Politico , March 5, 2010. [ available online ]
- Lü, Yao-Hui, 2005, “Privacy and Data Privacy Issues in Contemporary China,” Ethics and Information Technology , 7(1): 7–15
- Ludlow, P. and M. Wallace, 2007, The Second Life Herald: The Virtual Tabloid that Witnessed the Dawn of the Metaverse , Cambridge, MA: MIT Press.
- Luck, M., 2009, “The gamer’s dilemma: An analysis of the arguments for the moral distinction between virtual murder and virtual paedophilia,” Ethics and Information Technology , 11(1): 31–36.
- Luppicini, R. and R. Adell (eds.), 2009, Handbook of Research on Technoethics , Idea Group Inc. (IGI).
- Magnani, L., 2007, Morality in a Technological World: Knowledge as Duty, Cambridge, Cambridge University Press.
- Mason, R. O., 1986, Four ethical issues of the information age. MIS Quarterly , 10(1): 5–12.
- Markoff, J., 2005, What the Dormouse Said: How the 60s Counterculture Shaped the Personal Computer Industry , New York: Penguin.
- Manion, M. and A. Goodrum, 2007, “Terrorism or Civil Disobedience: Toward a Hacktivist Ethic,” in Himma 2007a, pp. 49–59.
- McAfee, 2018, Economic Impact of Cybercrime: No Slowing Down, Report [ available online ]
- McMahon, J. M. and R. Cohen, 2009, “Lost in cyberspace: ethical decision making in the online environment,” Ethics and Information technology , 11(1): 1–17.
- Midgley, M., 1992, Science as Salvation: a modern myth and its meaning , London: Routledge.
- Moor, J. H., 1985, “What is Computer Ethics?” Metaphilosophy , 16(4): 266–275.
- –––, 2005, “Why We Need Better Ethics for Emerging Technologies,” Ethics and Information Technology , 7(3): 111–119. Reprinted in van den Hoven and Weckert 2008, pp. 26–39.
- Moore, Gordon E. 1965. “Cramming more components onto integrated circuits”. Electronics , 38(8): 114–117. [ available online ]
- Neumann, P. G., 2004, “Computer security and human values,” Computer Ethics and Professional Responsibility , Malden, MA: Blackwell
- Nissenbaum, H., 1997. “Toward an Approach to Privacy in Public: Challenges of Information Technology,” Ethics and Behavior , 7(3): 207–219. [ available online ]
- –––, 1998. “Values in the Design of Computer Systems,” Computers and Society , March: pp. 38–39. [ available online ]
- –––, 1999, “The Meaning of Anonymity in an Information Age,” The Information Society , 15: 141–144.
- –––, 2009, Privacy in Context: Technology, Policy, and the Integrity of Social Life , Stanford Law Books: Stanford University Press.
- Northcutt, S. and C. Madden, 2004, IT Ethics Handbook: Right and Wrong for IT Professionals , Syngress.
- O’Neil, O., 2002, “Trust is the first casualty of the cult of transparency,” The Telegraph , 24 April, available online .
- O’Reilly, T., 2007 [2005], “What is Web 2.0: Design Patterns and Business Models for the Next Generation of Software,” Communications & Strategies , 65(1): 17–37; available online . [The earlier, 2005 version, is linked into the Other Internet Resources section below.]
- Parrish, J., 2010, “PAPA knows best: Principles for the ethical sharing of information on social networking sites,” Ethics and Information Technology , 12(2): 187–193.
- Pettit, P., 2009, “Trust, Reliance, and the Internet,” In van den Hoven and Weckert 2008.
- Plaw, A. 2013, “Counting the Dead: The Proportionality of Predation in Pakistan,” In Strawser 2013.
- Planned Parenthood, 2017, “New Study Shows Virtual Reality Can Move People’s Views on Abortion and Clinic Harassment,” [ available online ]
- Plato, “Phaederus,” in Plato: The Collected Dialogues , E. Hamilton and H. Cairns (eds.), Princeton: Princeton University Press, pp. 475–525.
- Poushter J., 2016, “Smartphone Ownership and Internet Usage Continues to Climb in Emerging Economies: But advanced economies still have higher rates of technology use,” Pew Research Center , 22 February 2018 [ available online ]
- Powers, T., 2011, “Prospects for a Kantian Machine,” in Anderson and Anderson 2011.
- Purcell, M., 2008, “Pernicious virtual communities: Identity, polarisation and the Web 2.0,” Ethics and Information Technology , 10(1): 41–56.
- Reynolds, G., 2009, Ethics in Information Technology , (3 rd ed.), Course Technology.
- Russell, S. and P. Norvig, 2010, Artificial Intelligence: A Modern Approach , (3 rd ed.), Massachusetts: Prentice Hall.
- Schmidt, C. T. A., 2007, “Children, Robots and… the Parental Role,” 17(3): 273–286.
- Schulzke, M., 2010, “Defending the Morality of Violent Video Games,” Ethics and Information Technology , 12(2): 127–138.
- Searle, J., 1980, “Minds, Brains, and Programs,” Behavioral and Brain Sciences , 3: 417–57.
- Shannon, C.E., 1948, “A Mathematical Theory of Communication”, Bell System Technical Journal , 27(July, October): 379–423, 623–656. [ available online ]
- Shannon, C. E. and W. Weaver, 1949, The Mathematical Theory of Communication , University of Illinois Press.
- Sharkey, N.E. 2011, “The automation and proliferation of military drones and the protection of civilians,” Journal of Law, Innovation and Technology , 3(2): 229–240.
- Singer, P. W., 2009, Wired for War:The Robotics Revolution and Conflict in the 21 st Century , Penguin (Non-Classics); Reprint edition.
- Siraj-Blatchford, J., 2010, “Analysis: ‘Computers Benefit Children’,” Nursery World , October 6. [ available online ]
- Soukup, C., 2007, “Mastering the Game: Gender and the Entelechial Motivational System of Video Games,” Women’s Studies in Communication , 30(2): 157–178.
- Søraker, Johnny Hartz, 2012, “How Shall I Compare Thee? Comparing the Prudential Value of Actual Virtual Friendship,” Ethics and Information technology , 14(3): 209–219. doi:10.1007/s10676-012-9294-x [ available online ]
- Spafford, E.H., 1992, “Are computer hacker break-ins ethical?” Journal of Systems and Software 17(1):41–47.
- –––, 2007, “Are Computer Hacker Break-ins Ethical?” in Himma 2007a, pp. 49–59.
- Spinello, R. A., 2001, Cyberethics , Sudbury, MA: Jones and Bartlett Publishers. (2nd ed., 2003; 3 rd ed., 2006; 4 th ed., 2010).
- –––, 2002, Case Studies in Information Technology Ethics , Prentice Hall. (2 nd ed.).
- Sprenger P., 1999, “Sun on Privacy: ‘Get Over It’,” Wired , January 26, 1999. [ available online ]
- Statista, 2018, “Number of social media users worldwide from 2010 to 2021 (in billions)”, [ available online ].
- Strawser, B.J., 2013, Killing by Remorte Control: The Ethics of an Unmanned Military , Oxford: Oxford University Press.
- Sullins, J. P., 2000, “Transcending the meat: immersive technologies and computer mediated bodies,” Journal of Experimental and Theoretical Artificial Intelligence , 12(1): 13–22.
- –––, 2005, “Ethics and Artificial life: From Modeling to Moral Agents,” Ethics and Information technology , 7(3): 139–148. [ available online ]
- –––, 2006, “When Is a Robot a Moral Agent?” International Review of Information Ethics , 6(12): 23–30. [ available online ]
- –––, 2009a, “Artificial Moral Agency in Technoethics,” in Luppicini and Adell 2009.
- –––, 2009b, “Telerobotic weapons systems and the ethical conduct of war,” APA Newsletter on Philosophy and Computers , P. Boltuc (ed.) 8(2): 21.
- –––, 2010, “Rights and Computer Ethics,” in Floridi 2010a.
- –––, forthcoming, “Deception and Virtue in Robotic and Cyber Warfare,” Presentation for the Workshop on The Ethics of Informational Warfare, at University of Hertfordhire, UK, July 1–2 2011
- Symantec, 2018, Internet Security Threat Report (ISTR), Symantec Security Response, [ available online ]
- Tavani, H. T., 2007, “The Conceptual and Moral Landscape of Computer Security,” in Himma 2007a, pp. 29–45.
- –––, 2010, Ethics and Technology: Controversies, Questions, and Strategies for Ethical Computing , (3 rd ed.), Wiley.
- Tavani, H. and J. Moor, 2004, “Privacy Protection, Control of Information, and Privacy-Enhancing Technologies,” in Readings in Cyberethics, second edition , Spinello, R. and Tavani, H. (eds.), Sudsbury: Jones and Bartlett.
- Taylor, N., J. Jensona, and S. de Castellb, 2009. “Cheerleaders/booth babes/ Halo hoes: pro-gaming, gender and jobs for the boys,” Digital Creativity , 20(4): 239–252.
- Turing, A. M., 1948, “Machine Intelligence”, in B. Jack Copeland, The Essential Turing: The ideas that gave birth to the computer age , Oxford: Oxford University Press.
- –––, 1950, “Computing Machinery and Intelligence”, Mind , 59(236): 433–460. doi:10.1093/mind/LIX.236.433
- Vallor, S., 2010, “Social Networking Technology and the Virtues,” Ethics and Information Technology , 12(2, Jan. 6): 157–170.
- –––, 2011, “Flourishing on Facebook: Virtue Friendship and New Social Media,” Ethics and Information technology , 1388–1957, pp. 1–15, Netherlands: Springer.
- –––, 2016, Technology and the Virtues: A Philosophical Guide to a Future worth Wanting , Oxford: Oxford University Press.
- Van den Hoven, J. and J. Weckert (eds), 2008, Information Technology and Moral Philosophy , Cambridge: Cambridge University Press.
- Von Neumann, J., 1966, Theory of Self Reproducing Automata , edited and completed by A. Burks, Urbana-Champaign: University of Illinois Press.
- Wallach, W., 2011. From Robots to Techno Sapiens: Ethics, Law and Public Policy in the Development of Robotics and Neurotechnologies, Law, Innovation and Technology , 3(2): 185–207.
- Wallach, W. and C. Allen, 2010, Moral Machines: Teaching Robots Right from Wrong , Oxford: Oxford University Press.
- Warschauer, M., 2003, Technology and Social Inclusion: Rethinking the Digital Divide , Cambridge: MIT Press.
- Weckert, John, 2007, “Giving and Taking Offence in a Global Context,” International Journal of Technology and Human Interaction , 3(3): 25–35.
- Westin, A., 1967, Privacy and Freedom , New York: Atheneum.
- Wiener, N., 1950, The Human Use of Human Beings , Cambridge, MA: The Riverside Press (Houghton Mifflin Co.).
- –––, 1961, Cybernetics: Or Control and Communication in the Animal and the Machine , 2nd revised ed., Cambridge: MIT Press. First edition, 1948.
- Woodbury, M. C., 2010, Computer and Information Ethics , 2 nd edition; 1 st edition, 2003, Champaign, IL: Stipes Publishing LLC.
How to cite this entry . Preview the PDF version of this entry at the Friends of the SEP Society . Look up topics and thinkers related to this entry at the Internet Philosophy Ontology Project (InPhO). Enhanced bibliography for this entry at PhilPapers , with links to its database.
- Clarke, R., 2000, “ Information wants to be Free… ”, unpublished manuscript.
- O’Reilly, T., 2005, “ What is Web 2.0: Design Patterns and Business Models for the Next Generation of Software ”.
- IEEE, 2018, “ The IEEE Global Initiative on Ethics of Autonomous and Intelligent Systems ”.
Aristotle, General Topics: ethics | artificial intelligence: logic-based | computing: and moral responsibility | Dewey, John: political philosophy | ethics, biomedical: theory | evil: problem of | information technology: phenomenological approaches to ethics and | life | pornography: and censorship | property: intellectual | Turing test
Copyright © 2018 by John Sullins < john . sullins @ sonoma . edu >
- Accessibility
Support SEP
Mirror sites.
View this site from another server:
- Info about mirror sites
The Stanford Encyclopedia of Philosophy is copyright © 2023 by The Metaphysics Research Lab , Department of Philosophy, Stanford University
Library of Congress Catalog Data: ISSN 1095-5054
- Future Students
- Current Students
- Faculty/Staff

News and Media
- News & Media Home
- Research Stories
- School's In
- In the Media
You are here
How technology is reinventing education.

New advances in technology are upending education, from the recent debut of new artificial intelligence (AI) chatbots like ChatGPT to the growing accessibility of virtual-reality tools that expand the boundaries of the classroom. For educators, at the heart of it all is the hope that every learner gets an equal chance to develop the skills they need to succeed. But that promise is not without its pitfalls.
“Technology is a game-changer for education – it offers the prospect of universal access to high-quality learning experiences, and it creates fundamentally new ways of teaching,” said Dan Schwartz, dean of Stanford Graduate School of Education (GSE), who is also a professor of educational technology at the GSE and faculty director of the Stanford Accelerator for Learning . “But there are a lot of ways we teach that aren’t great, and a big fear with AI in particular is that we just get more efficient at teaching badly. This is a moment to pay attention, to do things differently.”
For K-12 schools, this year also marks the end of the Elementary and Secondary School Emergency Relief (ESSER) funding program, which has provided pandemic recovery funds that many districts used to invest in educational software and systems. With these funds running out in September 2024, schools are trying to determine their best use of technology as they face the prospect of diminishing resources.
Here, Schwartz and other Stanford education scholars weigh in on some of the technology trends taking center stage in the classroom this year.
AI in the classroom
In 2023, the big story in technology and education was generative AI, following the introduction of ChatGPT and other chatbots that produce text seemingly written by a human in response to a question or prompt. Educators immediately worried that students would use the chatbot to cheat by trying to pass its writing off as their own. As schools move to adopt policies around students’ use of the tool, many are also beginning to explore potential opportunities – for example, to generate reading assignments or coach students during the writing process.
AI can also help automate tasks like grading and lesson planning, freeing teachers to do the human work that drew them into the profession in the first place, said Victor Lee, an associate professor at the GSE and faculty lead for the AI + Education initiative at the Stanford Accelerator for Learning. “I’m heartened to see some movement toward creating AI tools that make teachers’ lives better – not to replace them, but to give them the time to do the work that only teachers are able to do,” he said. “I hope to see more on that front.”
He also emphasized the need to teach students now to begin questioning and critiquing the development and use of AI. “AI is not going away,” said Lee, who is also director of CRAFT (Classroom-Ready Resources about AI for Teaching), which provides free resources to help teach AI literacy to high school students across subject areas. “We need to teach students how to understand and think critically about this technology.”
Immersive environments
The use of immersive technologies like augmented reality, virtual reality, and mixed reality is also expected to surge in the classroom, especially as new high-profile devices integrating these realities hit the marketplace in 2024.
The educational possibilities now go beyond putting on a headset and experiencing life in a distant location. With new technologies, students can create their own local interactive 360-degree scenarios, using just a cell phone or inexpensive camera and simple online tools.
“This is an area that’s really going to explode over the next couple of years,” said Kristen Pilner Blair, director of research for the Digital Learning initiative at the Stanford Accelerator for Learning, which runs a program exploring the use of virtual field trips to promote learning. “Students can learn about the effects of climate change, say, by virtually experiencing the impact on a particular environment. But they can also become creators, documenting and sharing immersive media that shows the effects where they live.”
Integrating AI into virtual simulations could also soon take the experience to another level, Schwartz said. “If your VR experience brings me to a redwood tree, you could have a window pop up that allows me to ask questions about the tree, and AI can deliver the answers.”
Gamification
Another trend expected to intensify this year is the gamification of learning activities, often featuring dynamic videos with interactive elements to engage and hold students’ attention.
“Gamification is a good motivator, because one key aspect is reward, which is very powerful,” said Schwartz. The downside? Rewards are specific to the activity at hand, which may not extend to learning more generally. “If I get rewarded for doing math in a space-age video game, it doesn’t mean I’m going to be motivated to do math anywhere else.”
Gamification sometimes tries to make “chocolate-covered broccoli,” Schwartz said, by adding art and rewards to make speeded response tasks involving single-answer, factual questions more fun. He hopes to see more creative play patterns that give students points for rethinking an approach or adapting their strategy, rather than only rewarding them for quickly producing a correct response.
Data-gathering and analysis
The growing use of technology in schools is producing massive amounts of data on students’ activities in the classroom and online. “We’re now able to capture moment-to-moment data, every keystroke a kid makes,” said Schwartz – data that can reveal areas of struggle and different learning opportunities, from solving a math problem to approaching a writing assignment.
But outside of research settings, he said, that type of granular data – now owned by tech companies – is more likely used to refine the design of the software than to provide teachers with actionable information.
The promise of personalized learning is being able to generate content aligned with students’ interests and skill levels, and making lessons more accessible for multilingual learners and students with disabilities. Realizing that promise requires that educators can make sense of the data that’s being collected, said Schwartz – and while advances in AI are making it easier to identify patterns and findings, the data also needs to be in a system and form educators can access and analyze for decision-making. Developing a usable infrastructure for that data, Schwartz said, is an important next step.
With the accumulation of student data comes privacy concerns: How is the data being collected? Are there regulations or guidelines around its use in decision-making? What steps are being taken to prevent unauthorized access? In 2023 K-12 schools experienced a rise in cyberattacks, underscoring the need to implement strong systems to safeguard student data.
Technology is “requiring people to check their assumptions about education,” said Schwartz, noting that AI in particular is very efficient at replicating biases and automating the way things have been done in the past, including poor models of instruction. “But it’s also opening up new possibilities for students producing material, and for being able to identify children who are not average so we can customize toward them. It’s an opportunity to think of entirely new ways of teaching – this is the path I hope to see.”
More Stories

⟵ Go to all Research Stories
Get the Educator
Subscribe to our monthly newsletter.
Stanford Graduate School of Education
482 Galvez Mall Stanford, CA 94305-3096 Tel: (650) 723-2109
- Contact Admissions
- GSE Leadership
- Site Feedback
- Web Accessibility
- Career Resources
- Faculty Open Positions
- Explore Courses
- Academic Calendar
- Office of the Registrar
- Cubberley Library
- StanfordWho
- StanfordYou
Improving lives through learning
- Stanford Home
- Maps & Directions
- Search Stanford
- Emergency Info
- Terms of Use
- Non-Discrimination
- Accessibility
© Stanford University , Stanford , California 94305 .

IMAGES
VIDEO
COMMENTS
Reassessment is in progress-reassessment. of the systems changes educational technology brings about and of the human values to be imposed on its use to preserve. our dominion over it. Since schools and colleges are institutions of their society, they necessarily reflect society's values. Up to and through.
Co-design is an approach to human-centered design (HCD). Co-design is acknowledged as a novel design field which sees the user as a valuable contributor to counterbalance the values of the 'hero-designer.'. Co-design can be applied as a pedagogy in design and technology education.
Science, Technology, & Human Values 2018, Vol. 43(6) 1066-1097 ... LTS have become central to the modern human experience, yet they puzzle researchers and "confound engineers, social scientists, historians, economists, policy planners, and political leaders" (LaPorte 1991a, 1-2).
Technology does change human lives, but my query is: does it change human selves too? On a closer look, it is observed that technology and the trail of human beings towards an authentic life (the highest desire) are central and pivotal to human living. However, most of us think of them as separate and unrelated. Technology is technical, the job of technicians, whereas queries of ...
High-level goals might include peace, excellent health care, adequate nutrition, accessible education, communication, freedom of expression, support for creative exploration, safety, and socially constructive entertainment. Computer technology can help attain these high-level goals if we clearly state measurable objectives, obtain participation ...
Technology is a key factor in enabling education to transform and upgrade, and the context of the times is an important driving force in promoting the adoption of new technologies in the education ...
Understandings of NoT provide a much-needed critical framework—and currently missing body of knowledge—to examine how technology interacts with individuals, society, culture, institutions, and economy (Waight and Abd-El-Khalick 2012).The NoT framework is significant for science education because it provides a lens to interrogate the artifact, its interactions, and the role of culture and ...
Prime (1993) on the basis of Schwartz's (1992) interpretation of values argues that values have both cognitive and affective components: "developing values through technology education must … address the cognitive component, by exposing children to all the relevant knowledge, as well as engaging their feelings by placing technology in a human ...
technology today plays a constitutive role in the way the whole of this universe operates. In Ian Barbour's [3] views, modern technology is appraised from three major perspectives: First, technology is understood as a liberating force primarily during the industrial revolution and in the post-world-war period by relieving people from hunger ...
Thus, human values can play a significant role in achieving sustainability. Recent discoveries in quantum physics and neuroscience have revealed that these human values are intrinsic to human beings and are hardwired in our brains. Education in human values is a program designed to bring out these values and guide our behavior and attitudes.
While contemporary academic philosophers and theorists of technology from different schools widely reject VNT, 1 it remains unclear whether claims about values in technology are more than just a figure of speech, namely, whether they are nontrivial empirical claims with genuine factual content and real-world implications. This challenge has been most thoroughly developed by Joseph Pitt, who ...
Hans Oberdiek, Mary Tiles. Published 1995. Philosophy, Sociology, Computer Science. TLDR. Living in a Technological Culture challenges traditionally held assumptions about the relationship between 'man-and-machine' and argues that contemporary science does not shape technology but is shaped by it. Expand.
Technology and Cultural Values: On the Edge of the Third Millennium on JSTOR. JSTOR is part of , a not-for-profit organization helping the academic community use digital technologies to preserve the scholarly record and to advance research and teaching in sustainable ways. ©2000-2024 ITHAKA.
PDF | On Aug 13, 2020, Zhuldizay T. Kulzhanova and others published Impact of Technology on Modern Society—A Philosophical Analysis of the Formation of Technogenic Environment | Find, read and ...
At the micro-level, and most relevant to science education, PoT engages the inherent nature of technology along a number of key dimensions: role of culture and values, notions of technological ...
Technology is a human construct. Consequently, technologies are shaped by human interests and values, and open to human choice. This view can already be found in some of the works of earlier philosophers of technology like Lewis Mumford (e.g. Mumford, 1934/1963) and Langdon Winner (e.g. Winner, 1977, 1986).
The human values and the modern technological education follow an inverse relationship. With the advancement in the technology, the emotions are getting washed away. The technological advancement into the field of education has brought about a drastic deterioration in humanitarian behaviours and human values. Factors could be many,
Within the general field of technology design and human-computer interaction, the issue of value alignment has been explicitly and systematically addressed by value-sensitive design (VSD), "a theoretically grounded approach to the design of technology that accounts for human values in a principled and systematic manner throughout the design ...
Since 1972, Science, Technology, & Human Values has provided a forum for cutting-edge research and debate in the field of Science and Technology Studies (STS). This is a collectively edited, peer-reviewed, transnational, interdisciplinary journal containing research, analyses and commentary on the development and dynamics of science and ...
Nanotechnology has made a heavy impact on human values and human development by. narrowing the rich-poor divide and if the new technologies are diverted to this end, a new era. of universalism ...
For more than 50 years, Science, Technology, & Human Values has provided a forum for cutting-edge research and debate in the field of Science and Technology Studies (STS). This is a collectively edited, peer-reviewed, transnational, interdisciplinary journal containing research, analyses and commentary on the development and dynamics of science and technology, with a focus on their ...
Information Technology and Moral Values. First published Tue Jun 12, 2012; substantive revision Fri Nov 9, 2018. Every action we take leaves a trail of information that could, in principle, be recorded and stored for future use. For instance, one might use the older forms of information technologies of pen and paper and keep a detailed diary ...
New advances in technology are upending education, from the recent debut of new artificial intelligence (AI) chatbots like ChatGPT to the growing accessibility of virtual-reality tools that expand the boundaries of the classroom. For educators, at the heart of it all is the hope that every learner gets an equal chance to develop the skills they need to succeed.
As generative artificial intelligence (AI) technologies become widely available as writing aids, the Modern Language Association and the Conference on College Composition and Communication, a chartered conference of the National Council of Teachers of English, affirm our common values as organizations serving professional educators.