Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center


SECURITY FEATURES OF ATM

Related Papers
International Journal of Advance Research in Computer Science and Management Studies [IJARCSMS] ijarcsms.com
Authentication is an important part of any secrete operation and concept is applicable for trustworthy Automatic Teller Machine which ensures that, only individuals with corroborated identities can log on to the system or access system resources. In this paper, I survey the literature to describe the ways that ATMs have influenced these aspects of security, and conclude with suggestions for further research.
IOSR Journals
Automated Teller Machine (ATM) services are more popular because of their flexibility and easiness for banking systems. People are widely using their ATM cards for immediate money transfer, cash withdrawal, shopping etc. On most modern ATMs, the ATM card used by the customer for each bank account which is a plastic ATM card with a magnetic stripe or a plastic smart card with a chip. However, password PIN which is the main authentication for ATM transactions represent the weakest link in the computer security chain. In the proposed Multi Account Embedded ATM card, we embed more than one bank account into a single ATM card so that the customer can carry out the financial transactions for multiple bank accounts. The user need not carry multiple ATM cards and remember multiple passwords. To provide high security we introduced fingerprint based customer authentication. It reduces the cost of interbanking transactions as interfacing different bank databases is a resource consuming thing.
ajer research
ABSTRACT: This paper deals with the solutions related to the ATM (Automated Teller Machine) security. Today, ATMs and Credit cards are used for the purpose of money transactions which play a vital role in the nature of trade. The weaknesses of existing authentication scheme such as password and PIN number caused the leakage of information stored in ATM smartcard which lead to the lost of money in bank account and private information misuses. To overcome this shortcoming of piracy in money transactions, we propose the idea of using fingerprints of customers as password included with traditional PIN number. After authorized verification, the customer will be able to proceed for transaction else after three successive wrong attempts, the ATM card will be blocked for 24 hours and a message will be sent to the registered mobile number. Fingerprint biometric of every person is unique and unchangeable as well as one of the famous techniques for smart card security.
Ahmar Uddin
The Omani Banking sector is undergoing significant changes and growth. This study investigated the experiences of Bank Muscat (BM) and Bank Dhofar (BD) (hereafter BM and BD) customers with automatic teller machines (ATMs) in the Dhofar region of Oman. Primary data was collected from by a random sample of 200 ATM users by means of a semi-structured questionnaire. The data were analyzed using descriptive statistics and t-test. The study found that most of the users were male in the age group of 36-45 having a government job or doing their own business. The study also revealed that the main problems faced by the ATM users are machine out of order, long queue and poor visibility of statement. As regards to the differences between the two banks the study found that significant difference in the mean customer satisfaction between customers of BM and BD for the factor " Machine out of order. " Management of these banks must take into account these factors while designing and implementing ATM based policy reforms.
cheks nwasor
Engineering Research Publication and IJEAS
Abstract— The transactions of money play an important role in the present society. ATMs and Credit cards are mainly used for transactions. ATM machine uses ATM Card and PIN (Personal Identification Number) as authentication mechanisms. Today intruders produce duplicate ATM card and make fraudulent transactions by fixing ATM Card scanners in ATM Machine to obtain encrypted data from ATM Card. So the authentication provided by card and PIN is not so secure. The fingerprints of customers can be used as a password instead traditional PIN to overcome this disadvantage. Fingerprints of each human being are unique and unchangeable. Hence it provides more security and authentication than the current systems.
International Journal of Scientific & Engineering Research
Muhammad Yasir Imam , Nabila Jannat , Ayesha Rehman
The main aim of this article presents a new idea of OTP (one-time password) and giving brief details of the close by ATM machine and the amount of cash presently now available in the close by ATM machine if there is a shortage of cash in ATM we are presently using for transactions. Other than that, we also have a deposit slot in our research paper through which the user can transfer money to their account in very short time. The amount of cash being withdrawn from the ATM machine is limited. As all of you know that the limitation of Rs.25,000 is withdrawn at one time, which is being allow for one transaction only. Our research enables us to withdraw a handsome amount of cash within a time period of five minutes utilizing OTP which is counted as for one transaction and the customer can use this service for handsome amount of cash being withdrawn per day. There is a limit of transaction every day in different banks.
Loading Preview
Sorry, preview is currently unavailable. You can download the paper by clicking the button above.
RELATED PAPERS
Issahaku Haruna
International Journal of Scientific Research in Science and Technology IJSRST , Lusekelo Kibona
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
- Protein Kinases
- Transferases
- Biological Science
- Biochemistry
- phosphotransferases
- Protein-Serine-Threonine Kinases
Towards understanding ATM security - A field study of real world ATM use
- Conference: Proceedings of the Sixth Symposium on Usable Privacy and Security, SOUPS 2010, Redmond, Washington, USA, July 14-16, 2010

- Ludwig-Maximilians-University of Munich
- This person is not on ResearchGate, or hasn't claimed this research yet.

Abstract and Figures

Discover the world's research
- 25+ million members
- 160+ million publication pages
- 2.3+ billion citations
No full-text available
To read the full-text of this research, you can request a copy directly from the authors.
- Joseph O'Hagan

- Kieran Watson

- Jonah Stegman

- Lect Notes Comput Sci
- Teddy Seyed

- Anthony Tang

- Saranga Komanduri

- Rahul Telang

- Saule Nurymova

- Azimkhan A. Satybaldin
- Karoline Busse

- Katharina Krombholz

- Sarah Prange

- Sushil Kulkarni

- Sunpreet S. Arora

- Patrizia Willi

- COMPUT STAND INTER

- SCI ENG ETHICS

- M. Swaminathan
- Jaavaji Ashok

- Crime Prev Community Saf Int J
- Matthew P. J. Ashby

- Shweta Sankhwar

- Liron Nehmadi

- S. O. S. O.
- Ildar Muslukhov

- Thomas Palazzolo

- Keerthana Prasanth

- Abdulrauph Babatunde

- Akintoye Abraham Onamade
- Bunmi Janet Bambi

- Shreyans Jain
- Shristi Dabola
- Shikhar Binjola
- Rajni Jindal

- T Aishwarya

- M. Priyanka

- Shaik Saidulu
- Rasmi Ranjan

- Youngbae Song
- Geumhwan Cho
- Seongyeol Oh
- Morin Ostkamp
- Sven Heitmann
- Christian Kray

- Hirokazu Sasamoto

- Paul Dunphy

- Peter Peltonen

- Rachna Dhamija
- Adrian Perrig

- Collin Jackson

- Desney S. Tan

- Alma Whitten
- J. D. Tygar
- Paul C. van Oorschot
- Volker Roth

- Rene Freidinger

- Martin Denzel
- Elaine M. Huang
- Anna Koster
- Jan Borchers
- Susan Wiedenbeck
- Leonardo Sobrado
- Jean-Camille Birget
- Recruit researchers
- Join for free
- Login Email Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google Welcome back! Please log in. Email · Hint Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google No account? Sign up
A Multimodal Biometrics Secured ATM
- Conference paper
- First Online: 25 January 2023
- Cite this conference paper

- Tumelo Presley Nkgapele 13 ,
- Chunling Tu 13 &
- Moses Olaifa 13
Part of the book series: Lecture Notes in Networks and Systems ((LNNS,volume 579))
594 Accesses
Security is crucial in financial institutions to protect clients from financial losses which can occur due to identity theft and ineffective authorization measures. Biometrics techniques are commonly used in these security systems to prevent thieves from stealing people’s identity and using it for financial gains. However, the risk of identity theft has increased over the years due to the development of technology, especially the Internet of Things (IoT) and social media. To secure financial access, various systems and methods have been developed, such as the radio frequency identification (RFID)-based and the biometrics-based automated teller machine (ATM). The RFID-based devices have a dependency on the RFID cards which can be stolen, lost, misplaced or hacked. Existing biometric-based devices also have some drawbacks, with reliability and accuracy as the most common ones. The purpose of this research is to prevent identity theft by using multimodal biometrics technology for financial authorization and authentication. The biometric features used in this paper are the fingerprint and face due to their high accuracy when combined. A more reliable access granting system is developed with the low possibility to be spoofed. The proposed method also avoids the need to carry an ATM card, therefore, reducing the cases of it being stolen or misplaced.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
Similar content being viewed by others

Sentinel: An Enhanced Multimodal Biometric Access Control System

Enhanced ATM Security Using Facial Recognition, Fingerprint Authentication, and WEB Application

New Approach for Multimodal Biometric Recognition
Tran, L.B., Le, T.: Person authentication using Relevance Vector Machine (RVM) for face and fingerprint. Int. J. Modern Educ. Comp. Sci. 7 , 8–15 (2015)
Article Google Scholar
Melin, P., Kacprzyk, J., Pedrycz, W.: Bio-inspired hybrid intelligent systems for image analysis and pattern recognition, pp. 123–140. Springer, Berlin (2009)
Book Google Scholar
Dasgupta, D.: Biometrics and its use: Viewpoint. Biostatistics Biometrics Open Access J. 7 (2018)
Google Scholar
Bhanushali, N., Chapaneria, M., Mehta, K., Rathod, M.: Fingerprint based ATM System. J. Res. 2 (12), 31–34 (2017)
Dutta, M., Psyche, K., Yasmin, S.: ATM transaction security using fingerprint recognition. American J. Eng. Res. (AJER) 6 (8), 41–45 (2017)
Rajput, S., Patne, A., Varma, A., Vishe, G.: Enhanced fingerprint recognition and OTP to improve ATM security. Int. J. Adv. Res. Ideas Innov. Technol. 5 (2), 1263–1266 (2019)
Joshi, S.: Face recognition system with HOG in ATMs. Int. Res. J. Eng. Tech. (IRJET) 6 (6), 2134–2136 (2019)
Manikandan, B., Kishore, R., Saran, K., Suriya, S., Vivek, K.: Enhanced security for ATM machine with OTP and facial. Int. Res. J. Multidis. Tech. (IRJMT) 1 (2), 106–110 (2019)
Mohite, A., Gamare, S., More, K., Patil, N.: Deep learning based card-less ATM using fingerprint and face recognition techniques. Int. Res. J. Eng. Tech. 6 (3), 3504–3509 (2019)
Surjith, S., Mohan, A., Alexander, A., Mohanan, A.: Face recognition and finger print based enhanced security system for ATM transaction. Int. J. Innov. Res. Elect. Electr. Instrument Cont. Eng. 1 (2), 317–321 (2018)
Magdin, M., Koprda, Š, Ferenczy, L.: Biometrics authentication of fingerprint with using fingerprint reader and microcontroller Arduino. TELKOMNIKA 16 (2), 755–765 (2018)
Shetty, A.B., Bhoomika, D., Rebeiro, J., Ramyashree: Facial recognition using Haar cascade and LBP classifiers. In: Global Transitions Proceedings , 330–335 (2021)
Download references
Author information
Authors and affiliations.
Department of Computer Systems Engineering, Tshwane University of Technology, Pretoria, 0001, South Africa
Tumelo Presley Nkgapele, Chunling Tu & Moses Olaifa
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Tumelo Presley Nkgapele .
Editor information
Editors and affiliations.
School of Mathematics, Computer Science and Engineering, Liverpool Hope University, Liverpool, UK
Atulya K. Nagar
Namibia University of Science and Technology, Windhoek, Namibia
Dharm Singh Jat
Department of Computer Science and Engineering, Sri Aurobindo Institute of Technology, Indore, Madhya Pradesh, India
Durgesh Kumar Mishra
Global Knowledge Research Foundation, Ahmedabad, Gujarat, India
Rights and permissions
Reprints and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper.
Nkgapele, T.P., Tu, C., Olaifa, M. (2023). A Multimodal Biometrics Secured ATM. In: Nagar, A.K., Singh Jat, D., Mishra, D.K., Joshi, A. (eds) Intelligent Sustainable Systems. Lecture Notes in Networks and Systems, vol 579. Springer, Singapore. https://doi.org/10.1007/978-981-19-7663-6_34
Download citation
DOI : https://doi.org/10.1007/978-981-19-7663-6_34
Published : 25 January 2023
Publisher Name : Springer, Singapore
Print ISBN : 978-981-19-7662-9
Online ISBN : 978-981-19-7663-6
eBook Packages : Intelligent Technologies and Robotics Intelligent Technologies and Robotics (R0)
Share this paper
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
- Skip to main content
- Skip to search
- Skip to footer
Products and Services
Live stream splunk's user conference for free.
Global broadcast | June 11–12, 2024

Making AI work for you
Cisco AI is where the AI hype ends and meaningful help begins.
Certifications
Cisco Validated
Announced at Cisco Live
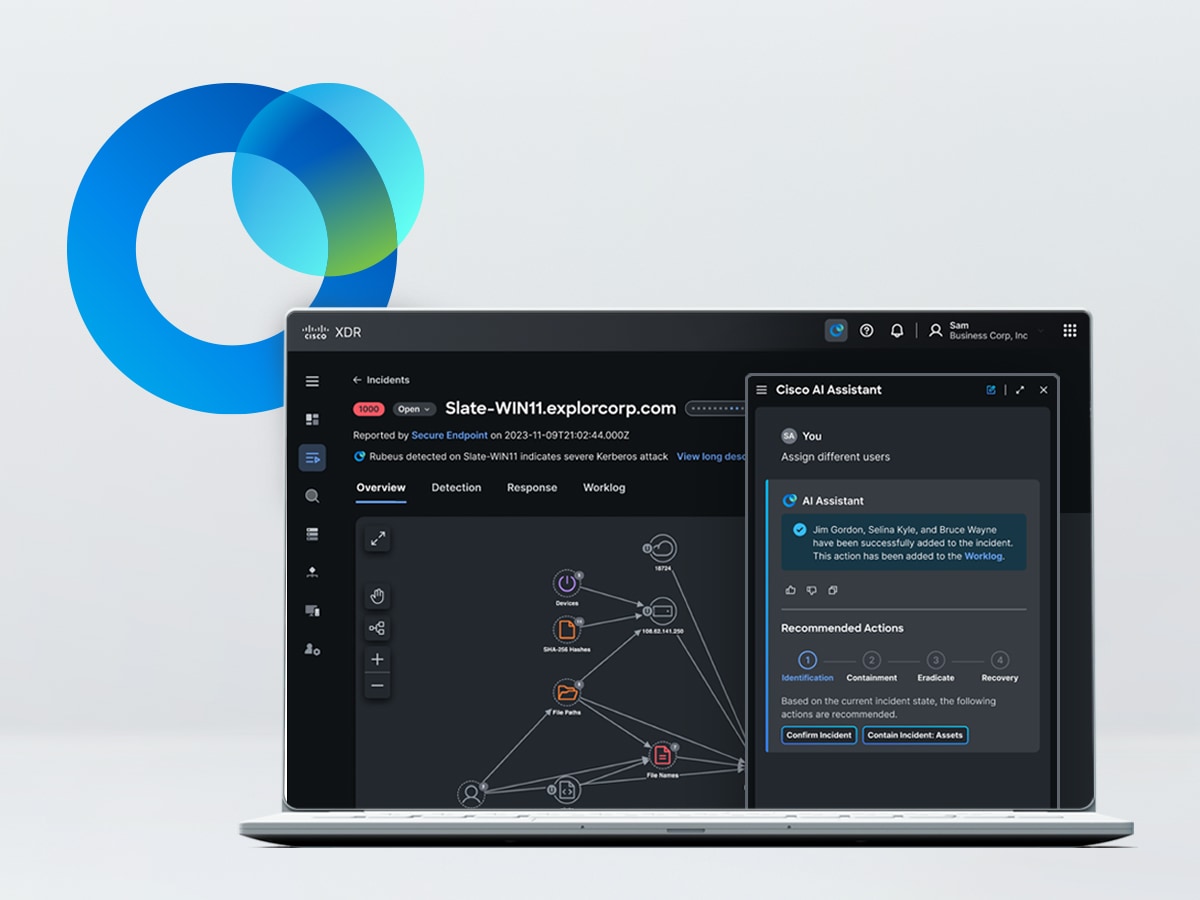

Cisco XDR with AI Assistant
Remediate the highest-priority incidents with an AI-first XDR solution.

Cisco Networking Cloud
One platform experience. Assured, secured, and simplified.

Secure Firewall 1200 Series
Compact, all-in-one SD-WAN firewall for your distributed enterprise branch.
Catch up on what you missed
Keynote: Vision for the Future
CEO Chuck Robbins addresses how to connect and protect your business in the AI era.
Keynote: Go Beyond
Learn about Cisco, Splunk, and reaping the benefits of the AI revolution.
Deep dive sessions
See tech announcements and strategic direction from Cisco's senior tech leaders.
View keynotes and tech sessions in the on-demand library.
Press release
Cisco Live puts AI center stage and more.
Cisco launches $1B global AI investment fund.

Validate your AI skills with certifications
Join all Cisco U. Theater sessions live and direct from Cisco Live or replay them, access learning promos, and more. It's time to Go Beyond the basics and level up your learning.
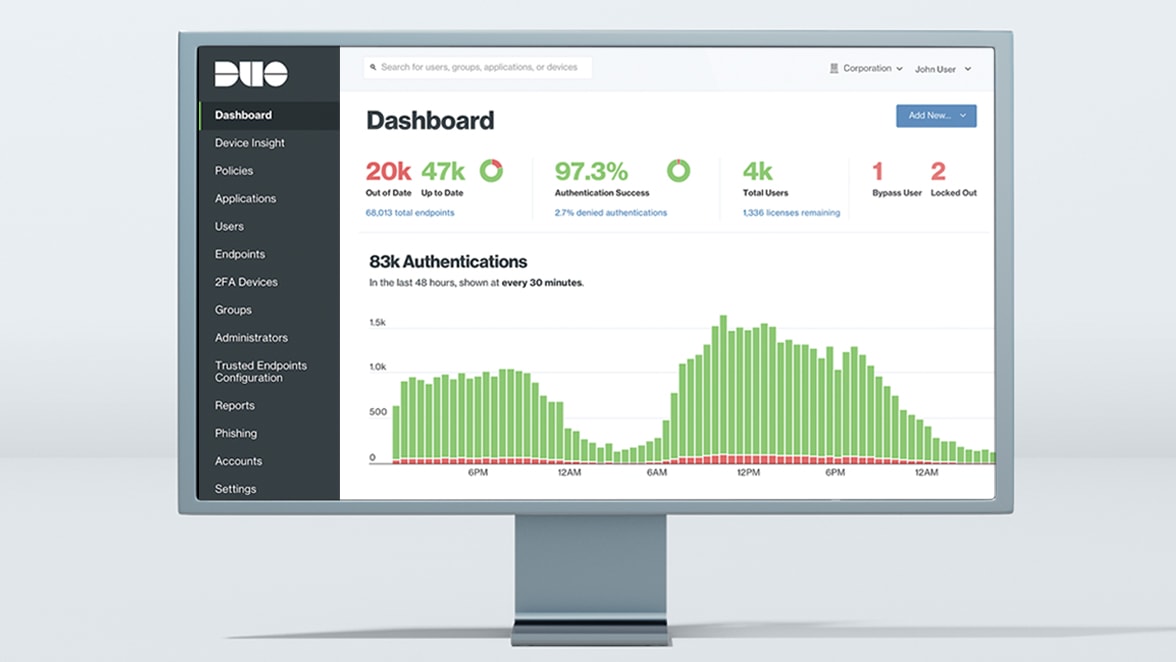
Identity is the new perimeter
Stop identity-based attacks while providing a seamless authentication experience with Cisco Duo's new Continuous Identity Security.
Inside Cisco
- More events
Cisco reveals Nexus HyperFabric
Cisco Nexus HyperFabric makes it easy for customers to deploy, manage, and monitor generative AI models and inference applications without deep IT knowledge and skills.
Cisco and Splunk launch integrated Full-Stack Observability experience
Using Cisco and Splunk observability solutions, customers can build an observability practice that meets their IT environment needs for on-premises, hybrid, and multicloud.
ThousandEyes Digital Experience Assurance shifts IT operations
New Cisco ThousandEyes capabilities and AI-native workflows in Cisco Networking Cloud will deliver Digital Experience Assurance, transforming IT operations.
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
The state of AI in 2023: Generative AI’s breakout year
You have reached a page with older survey data. please see our 2024 survey results here ..
The latest annual McKinsey Global Survey on the current state of AI confirms the explosive growth of generative AI (gen AI) tools . Less than a year after many of these tools debuted, one-third of our survey respondents say their organizations are using gen AI regularly in at least one business function. Amid recent advances, AI has risen from a topic relegated to tech employees to a focus of company leaders: nearly one-quarter of surveyed C-suite executives say they are personally using gen AI tools for work, and more than one-quarter of respondents from companies using AI say gen AI is already on their boards’ agendas. What’s more, 40 percent of respondents say their organizations will increase their investment in AI overall because of advances in gen AI. The findings show that these are still early days for managing gen AI–related risks, with less than half of respondents saying their organizations are mitigating even the risk they consider most relevant: inaccuracy.
The organizations that have already embedded AI capabilities have been the first to explore gen AI’s potential, and those seeing the most value from more traditional AI capabilities—a group we call AI high performers—are already outpacing others in their adoption of gen AI tools. 1 We define AI high performers as organizations that, according to respondents, attribute at least 20 percent of their EBIT to AI adoption.
The expected business disruption from gen AI is significant, and respondents predict meaningful changes to their workforces. They anticipate workforce cuts in certain areas and large reskilling efforts to address shifting talent needs. Yet while the use of gen AI might spur the adoption of other AI tools, we see few meaningful increases in organizations’ adoption of these technologies. The percent of organizations adopting any AI tools has held steady since 2022, and adoption remains concentrated within a small number of business functions.
Table of Contents
- It’s early days still, but use of gen AI is already widespread
- Leading companies are already ahead with gen AI
- AI-related talent needs shift, and AI’s workforce effects are expected to be substantial
- With all eyes on gen AI, AI adoption and impact remain steady
About the research
1. it’s early days still, but use of gen ai is already widespread.
The findings from the survey—which was in the field in mid-April 2023—show that, despite gen AI’s nascent public availability, experimentation with the tools is already relatively common, and respondents expect the new capabilities to transform their industries. Gen AI has captured interest across the business population: individuals across regions, industries, and seniority levels are using gen AI for work and outside of work. Seventy-nine percent of all respondents say they’ve had at least some exposure to gen AI, either for work or outside of work, and 22 percent say they are regularly using it in their own work. While reported use is quite similar across seniority levels, it is highest among respondents working in the technology sector and those in North America.
Organizations, too, are now commonly using gen AI. One-third of all respondents say their organizations are already regularly using generative AI in at least one function—meaning that 60 percent of organizations with reported AI adoption are using gen AI. What’s more, 40 percent of those reporting AI adoption at their organizations say their companies expect to invest more in AI overall thanks to generative AI, and 28 percent say generative AI use is already on their board’s agenda. The most commonly reported business functions using these newer tools are the same as those in which AI use is most common overall: marketing and sales, product and service development, and service operations, such as customer care and back-office support. This suggests that organizations are pursuing these new tools where the most value is. In our previous research , these three areas, along with software engineering, showed the potential to deliver about 75 percent of the total annual value from generative AI use cases.
In these early days, expectations for gen AI’s impact are high : three-quarters of all respondents expect gen AI to cause significant or disruptive change in the nature of their industry’s competition in the next three years. Survey respondents working in the technology and financial-services industries are the most likely to expect disruptive change from gen AI. Our previous research shows that, while all industries are indeed likely to see some degree of disruption, the level of impact is likely to vary. 2 “ The economic potential of generative AI: The next productivity frontier ,” McKinsey, June 14, 2023. Industries relying most heavily on knowledge work are likely to see more disruption—and potentially reap more value. While our estimates suggest that tech companies, unsurprisingly, are poised to see the highest impact from gen AI—adding value equivalent to as much as 9 percent of global industry revenue—knowledge-based industries such as banking (up to 5 percent), pharmaceuticals and medical products (also up to 5 percent), and education (up to 4 percent) could experience significant effects as well. By contrast, manufacturing-based industries, such as aerospace, automotives, and advanced electronics, could experience less disruptive effects. This stands in contrast to the impact of previous technology waves that affected manufacturing the most and is due to gen AI’s strengths in language-based activities, as opposed to those requiring physical labor.
Responses show many organizations not yet addressing potential risks from gen AI
According to the survey, few companies seem fully prepared for the widespread use of gen AI—or the business risks these tools may bring. Just 21 percent of respondents reporting AI adoption say their organizations have established policies governing employees’ use of gen AI technologies in their work. And when we asked specifically about the risks of adopting gen AI, few respondents say their companies are mitigating the most commonly cited risk with gen AI: inaccuracy. Respondents cite inaccuracy more frequently than both cybersecurity and regulatory compliance, which were the most common risks from AI overall in previous surveys. Just 32 percent say they’re mitigating inaccuracy, a smaller percentage than the 38 percent who say they mitigate cybersecurity risks. Interestingly, this figure is significantly lower than the percentage of respondents who reported mitigating AI-related cybersecurity last year (51 percent). Overall, much as we’ve seen in previous years, most respondents say their organizations are not addressing AI-related risks.
2. Leading companies are already ahead with gen AI
The survey results show that AI high performers—that is, organizations where respondents say at least 20 percent of EBIT in 2022 was attributable to AI use—are going all in on artificial intelligence, both with gen AI and more traditional AI capabilities. These organizations that achieve significant value from AI are already using gen AI in more business functions than other organizations do, especially in product and service development and risk and supply chain management. When looking at all AI capabilities—including more traditional machine learning capabilities, robotic process automation, and chatbots—AI high performers also are much more likely than others to use AI in product and service development, for uses such as product-development-cycle optimization, adding new features to existing products, and creating new AI-based products. These organizations also are using AI more often than other organizations in risk modeling and for uses within HR such as performance management and organization design and workforce deployment optimization.
AI high performers are much more likely than others to use AI in product and service development.
Another difference from their peers: high performers’ gen AI efforts are less oriented toward cost reduction, which is a top priority at other organizations. Respondents from AI high performers are twice as likely as others to say their organizations’ top objective for gen AI is to create entirely new businesses or sources of revenue—and they’re most likely to cite the increase in the value of existing offerings through new AI-based features.
As we’ve seen in previous years , these high-performing organizations invest much more than others in AI: respondents from AI high performers are more than five times more likely than others to say they spend more than 20 percent of their digital budgets on AI. They also use AI capabilities more broadly throughout the organization. Respondents from high performers are much more likely than others to say that their organizations have adopted AI in four or more business functions and that they have embedded a higher number of AI capabilities. For example, respondents from high performers more often report embedding knowledge graphs in at least one product or business function process, in addition to gen AI and related natural-language capabilities.
While AI high performers are not immune to the challenges of capturing value from AI, the results suggest that the difficulties they face reflect their relative AI maturity, while others struggle with the more foundational, strategic elements of AI adoption. Respondents at AI high performers most often point to models and tools, such as monitoring model performance in production and retraining models as needed over time, as their top challenge. By comparison, other respondents cite strategy issues, such as setting a clearly defined AI vision that is linked with business value or finding sufficient resources.
The findings offer further evidence that even high performers haven’t mastered best practices regarding AI adoption, such as machine-learning-operations (MLOps) approaches, though they are much more likely than others to do so. For example, just 35 percent of respondents at AI high performers report that where possible, their organizations assemble existing components, rather than reinvent them, but that’s a much larger share than the 19 percent of respondents from other organizations who report that practice.
Many specialized MLOps technologies and practices may be needed to adopt some of the more transformative uses cases that gen AI applications can deliver—and do so as safely as possible. Live-model operations is one such area, where monitoring systems and setting up instant alerts to enable rapid issue resolution can keep gen AI systems in check. High performers stand out in this respect but have room to grow: one-quarter of respondents from these organizations say their entire system is monitored and equipped with instant alerts, compared with just 12 percent of other respondents.
3. AI-related talent needs shift, and AI’s workforce effects are expected to be substantial
Our latest survey results show changes in the roles that organizations are filling to support their AI ambitions. In the past year, organizations using AI most often hired data engineers, machine learning engineers, and Al data scientists—all roles that respondents commonly reported hiring in the previous survey. But a much smaller share of respondents report hiring AI-related-software engineers—the most-hired role last year—than in the previous survey (28 percent in the latest survey, down from 39 percent). Roles in prompt engineering have recently emerged, as the need for that skill set rises alongside gen AI adoption, with 7 percent of respondents whose organizations have adopted AI reporting those hires in the past year.
The findings suggest that hiring for AI-related roles remains a challenge but has become somewhat easier over the past year, which could reflect the spate of layoffs at technology companies from late 2022 through the first half of 2023. Smaller shares of respondents than in the previous survey report difficulty hiring for roles such as AI data scientists, data engineers, and data-visualization specialists, though responses suggest that hiring machine learning engineers and AI product owners remains as much of a challenge as in the previous year.
Looking ahead to the next three years, respondents predict that the adoption of AI will reshape many roles in the workforce. Generally, they expect more employees to be reskilled than to be separated. Nearly four in ten respondents reporting AI adoption expect more than 20 percent of their companies’ workforces will be reskilled, whereas 8 percent of respondents say the size of their workforces will decrease by more than 20 percent.
Looking specifically at gen AI’s predicted impact, service operations is the only function in which most respondents expect to see a decrease in workforce size at their organizations. This finding generally aligns with what our recent research suggests: while the emergence of gen AI increased our estimate of the percentage of worker activities that could be automated (60 to 70 percent, up from 50 percent), this doesn’t necessarily translate into the automation of an entire role.
AI high performers are expected to conduct much higher levels of reskilling than other companies are. Respondents at these organizations are over three times more likely than others to say their organizations will reskill more than 30 percent of their workforces over the next three years as a result of AI adoption.
4. With all eyes on gen AI, AI adoption and impact remain steady
While the use of gen AI tools is spreading rapidly, the survey data doesn’t show that these newer tools are propelling organizations’ overall AI adoption. The share of organizations that have adopted AI overall remains steady, at least for the moment, with 55 percent of respondents reporting that their organizations have adopted AI. Less than a third of respondents continue to say that their organizations have adopted AI in more than one business function, suggesting that AI use remains limited in scope. Product and service development and service operations continue to be the two business functions in which respondents most often report AI adoption, as was true in the previous four surveys. And overall, just 23 percent of respondents say at least 5 percent of their organizations’ EBIT last year was attributable to their use of AI—essentially flat with the previous survey—suggesting there is much more room to capture value.
Organizations continue to see returns in the business areas in which they are using AI, and they plan to increase investment in the years ahead. We see a majority of respondents reporting AI-related revenue increases within each business function using AI. And looking ahead, more than two-thirds expect their organizations to increase their AI investment over the next three years.
The online survey was in the field April 11 to 21, 2023, and garnered responses from 1,684 participants representing the full range of regions, industries, company sizes, functional specialties, and tenures. Of those respondents, 913 said their organizations had adopted AI in at least one function and were asked questions about their organizations’ AI use. To adjust for differences in response rates, the data are weighted by the contribution of each respondent’s nation to global GDP.
The survey content and analysis were developed by Michael Chui , a partner at the McKinsey Global Institute and a partner in McKinsey’s Bay Area office, where Lareina Yee is a senior partner; Bryce Hall , an associate partner in the Washington, DC, office; and senior partners Alex Singla and Alexander Sukharevsky , global leaders of QuantumBlack, AI by McKinsey, based in the Chicago and London offices, respectively.
They wish to thank Shivani Gupta, Abhisek Jena, Begum Ortaoglu, Barr Seitz, and Li Zhang for their contributions to this work.
This article was edited by Heather Hanselman, an editor in the Atlanta office.
Explore a career with us
Related articles.

The economic potential of generative AI: The next productivity frontier
What is generative AI?

Exploring opportunities in the generative AI value chain

IMAGES
VIDEO
COMMENTS
This paper is the continuation of a previous work conducted in the past [2, 3], where we found the close relation that exists between Usability and Security when someone is using an ATM [4] and ...
The purpose of this paper is to reinforce security of the conventional ATM model. We have posited a new concept that enhances the overall experience, usability and convenience of the transaction at the ATM. Features like face recognition and One-Time Password (OTP) are used for the enhancement of security of accounts and privacy of users.
27 th - 28 th November 2019, ISBN: 978-955627-189-8. administrations for shielding individuals' money and different stuffs from. burglaries and fraud. The aim of this study is to analyze the ...
Abstract. This paper provides you with a description of this new approach for the security of ATM transactions for its subscribers. Looking towards the banking sector, ensuring the safety and security in Automatic Teller Machine (ATM) is a critical factor for ATM transactions. This paper gives a review in brief about the existing literature ...
An enhanced ATM security system is proposed using RFID (Radio Frequency Identification), facial recognition, fingerprint authorization, and web development. ... to prevent the ATM threats a multistep security system that is hard to bypass is proposed and developed in this paper. The proposed security system uses computer vision, fingerprint ...
Key Features of an Effective ATM Network Security Platform To adequately protect ATMs, branches, and the corporate network, an automated and integrated security architecture should ... The gh lobaAo Mm rkt iogehAs WHITE PAPER. Perimeter and host-level NGFWs Every bank needs business-grade NGFWs at the network perimeter to keep malware out. The ...
strengthen security features such as automatic sliding doors, op-to coupler sen-sors, and a switch to alert the bank authorities in case any mishappening like threats or tempering on ATM took place. In paper [3], Authors Navin Kumar et al. discuss the weak points and imper-fections of the current ATM security system and propose a system that ...
The main objective of this paper is to provide maximum layer of ATM security [10] by reducing security issues in ATM counter and machine. This paper also aims to introduce the technological advancement in banking fields. The proposed system makes sure that even if one layer of security is compromised the other will prevent the attack, and
Research Paper Open Access w w w . a j e r . o r g Page 41 ATM Transaction Security Using Fingerprint Recognition Mithun Dutta1, Kangkhita Keam Psyche2 and Shamima ... measure to enhance the security features of the ATM for effective banking [2]. REFERENCES [1]. Sowmya Ravikumar, Sandhya Vaidyanathan, B. Thamotharan, S. Ramakrishnan, A new ...
229. II) LITERATURE REVIEW We studied five research papers of each technique and a short survey of these techniques is discussed in this literature paper. Also we discussed some limitations of each technique. 1)SECURE ATM USING BIOMETRIC TECHNIQUE. A) Iris recognition B) Fingerprint recognition C) Face recognition.
8. The customer inputs his or her PIN. Sabbir Hosen,Dept . of CSE,RRIT,2017 2 | P a g e fSECURITY FEATURES OF ATM 9. If the card is a valid card which can be processed by the machine then control transfer to next stages and prompts the user to either transfer, deposit or withdrawal of cash. 10.
ATMs (Automated Teller Machines) have become a vital component of people's everyday lives all around the world. However, ATM security is a serious problem because these devices are subject to fraud and theft. To address this issue, confront In ATM systems, recognition technology has been included as an extra layer of protection.
The crucial prerequisite in these days is to get rid of various forms of attacks. Nowadays, for financial transaction, automated teller machines (ATMs) are the mostly used gadgets in which personal identification numbers (PINs) are generally used for transaction. But personal identification numbers (PINs) are not secured from many types of threats (spoofing, eavesdropping, man-in-the middle ...
This paper provide design and Implementation of Theft Detection System (TDS) is to provide security and safety for ATM (Automatic Teller Machine) because In India number of ATM centers are rapidly increased. In a real-time scenario, it is practically very difficult to monitor every action done in an ATM. Nowadays Most of the people in the world use the ATM machine to withdraw money. In many ...
The number of ATM's a bank has can be a factor in considering the strength of a bank. As there is increase in the number of ATM's, there is also increase in the fraudulent activities in the ATM. The main motivation of this project is to increase the security feature of the use of ATM. The current method uses static key (PIN) for security.
International Journal of Scientific and Research Publications, Volume 6, Issue 4, April 2016 159 ISSN 2250-3153 www.ijsrp.org ATM Security Kavita Hooda Abstract- ATM is an automated teller machine which is a computerized telecommunications device that provides the ... This paper focuses on security of ATM system i.e., how to augment
PThe increase of automated teller machine (ATM) frauds has actuated the development of new authentication mechanisms to overcome security problems of personal identification numbers (PIN). These ...
The technology is increasing in leaps and bounds in the present era. With many technical developments and advances taking place, there has been an advancing trend in the techniques of handling money, money transaction and exchange methods. The Automatic Teller Machine (ATM) is the most widely used method to withdraw money and get bank statements. In the era where there are a wide range of ...
The biometric features used in this paper are the fingerprint and face due to their high accuracy when combined. ... multimodal biometric security solution was presented using fingerprint and face recognition to increase and improve security . On the research, ATM withdrawals are made possible without the need for a bank card and allowed two ...
New Cisco ThousandEyes capabilities and AI-native workflows in Cisco Networking Cloud will deliver Digital Experience Assurance, transforming IT operations. Read press release. Cisco is a worldwide technology leader. Our purpose is to power an inclusive future for all through software, networking, security, computing, and more solutions.
Nowadays, people often withdraw money from Automated Teller Machines (ATMs). Every user receives a unique card and personal identification code to perform all transactions secretly and anonymously. Developing an ATM crime prevention system is crucial to avoid theft. The proposed solution uses an embedded system using a Raspberry Pi to process the real-time data collected by the vibration ...
The latest annual McKinsey Global Survey on the current state of AI confirms the explosive growth of generative AI (gen AI) tools. Less than a year after many of these tools debuted, one-third of our survey respondents say their organizations are using gen AI regularly in at least one business function. Amid recent advances, AI has risen from a ...